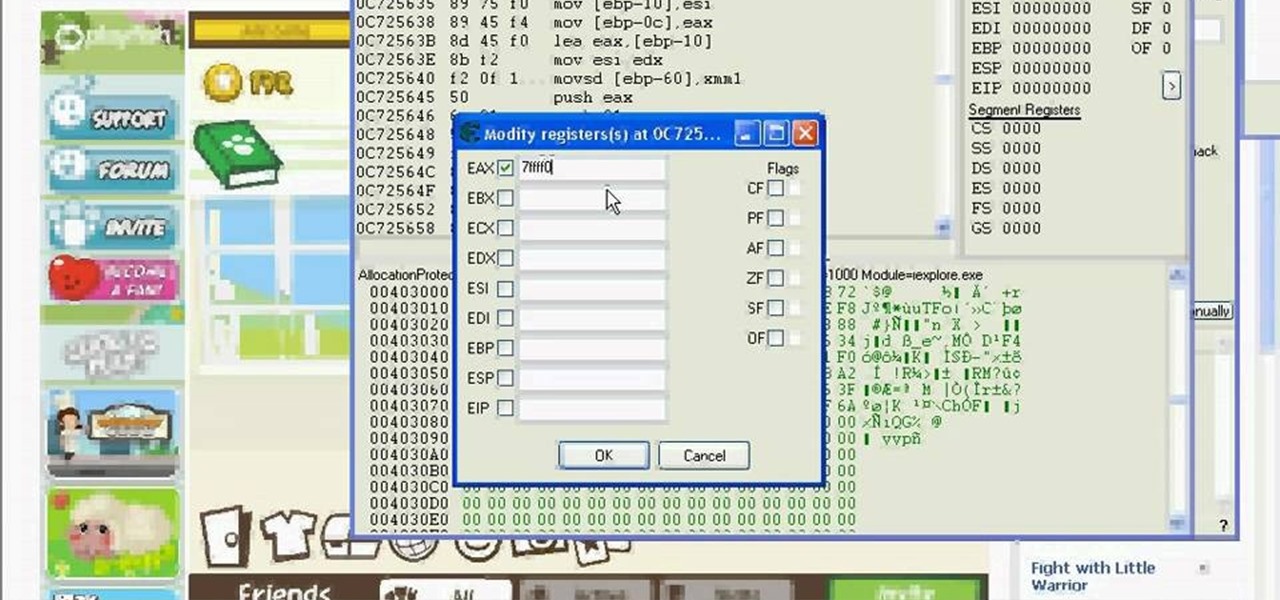
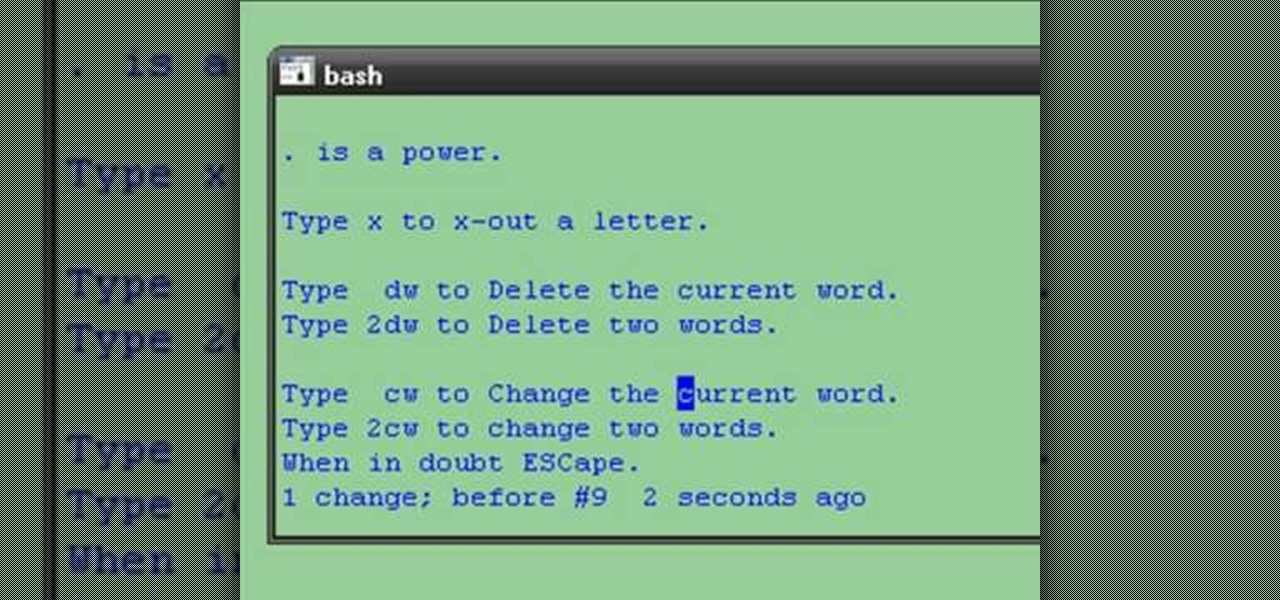
Creating a modern video game is a mammoth undertaking, especially if you are working alone. Hopefully, this video will make it a little bit easier. It will teach you how to create a custom class for your game's hero character using Flash CS4 and Actionscript 3. Doing so will make your main character react in predetermined ways to a variety of actions, which is very useful if you want the character to react consistently throughout the game.
In this video tutorial, viewers learn how to create a Face-book badge for a website or blog. Begin by going to your Face-book profile. Scroll down the page and click on Create a Profile Badge. Then click on Create Badge and select the layout, format and information that you want to display on your page. Once your finished, click on Save. Now copy the given HTML code and paste it onto your website or blog. This video will benefit those viewers who use Face-book and would like to learn how to e...

The iPad is a pretty innovative device, it looks like an iPhone, runs like a computer and is sleek and thin like a magazine. This new tool can be used for almost anything.
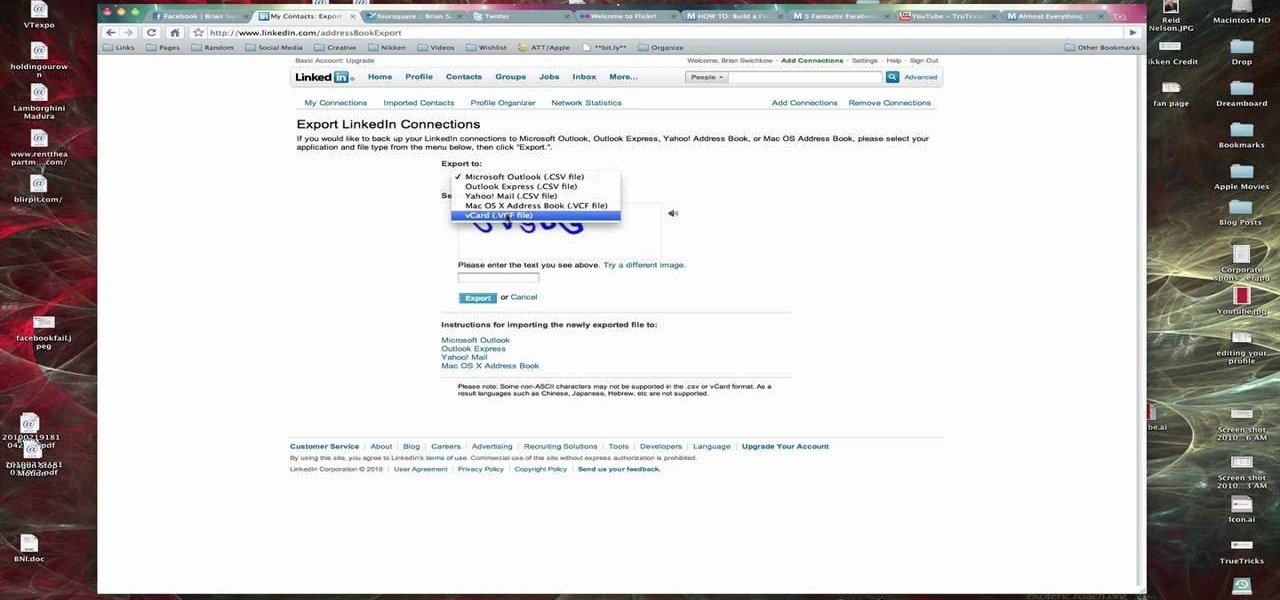
In this Computers & Programming video tutorial you are going to learn how to export LinkedIn contacts to an address book. LinkedIn is great for keeping your contacts in your professional network. To export your contacts go to home page and click on ‘contacts’. Now your full network of contacts will be displayed. On the right hand bottom, click on ‘export contacts’. On the next page select where you want to export the contacts, type in the security code and hit ‘export’ and all the contacts wi...
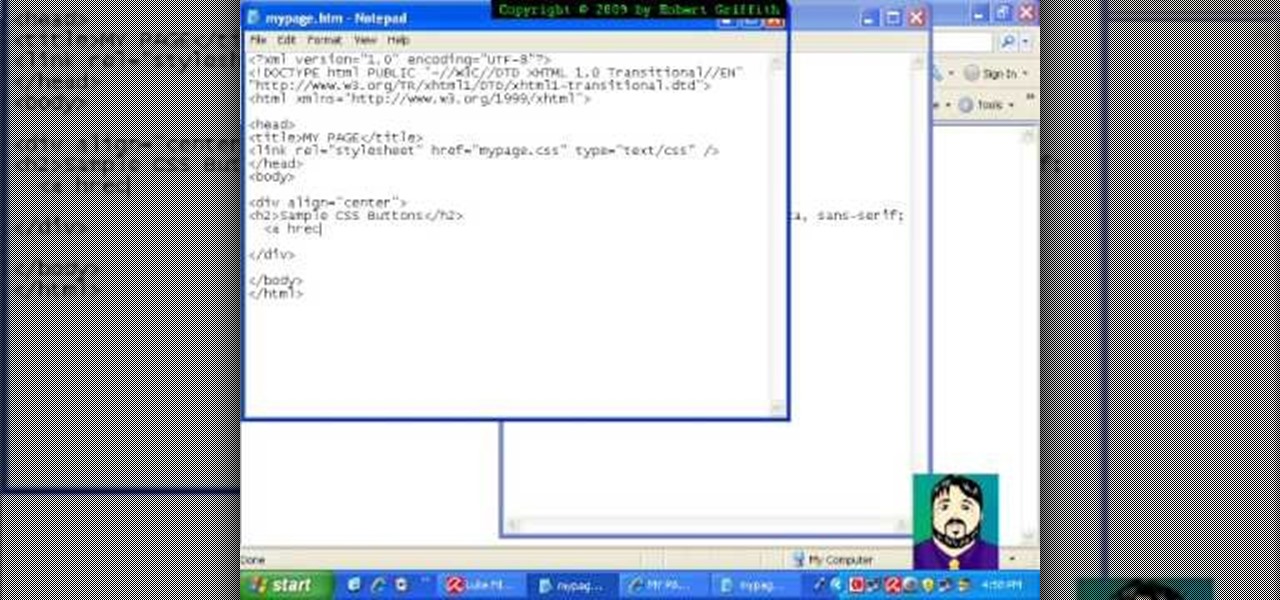
In this tutorial freetutorials teaches you how to create navigation style buttons using cascading style sheets, or CSS, in this the first in his series of "HTML Tips & Tricks". As you follow along, you will be shown how to setup and link your cascading style sheet to your HTML document, and where to place it in the document. Once you have done that, he will show you how to create a CSS, add a body and code the buttons in the CSS using notepad.
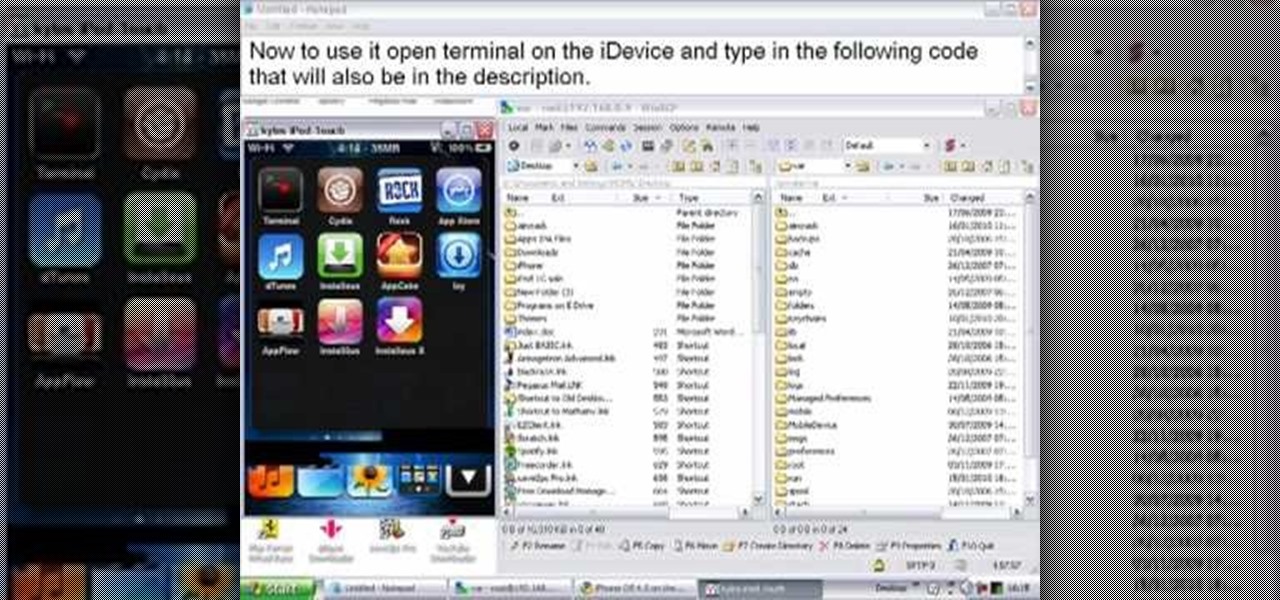
Learn how to install Aircrack on your iPhone to hack into almost any WiFi network. First download Aircrack from iHackMyi, then follow these steps:

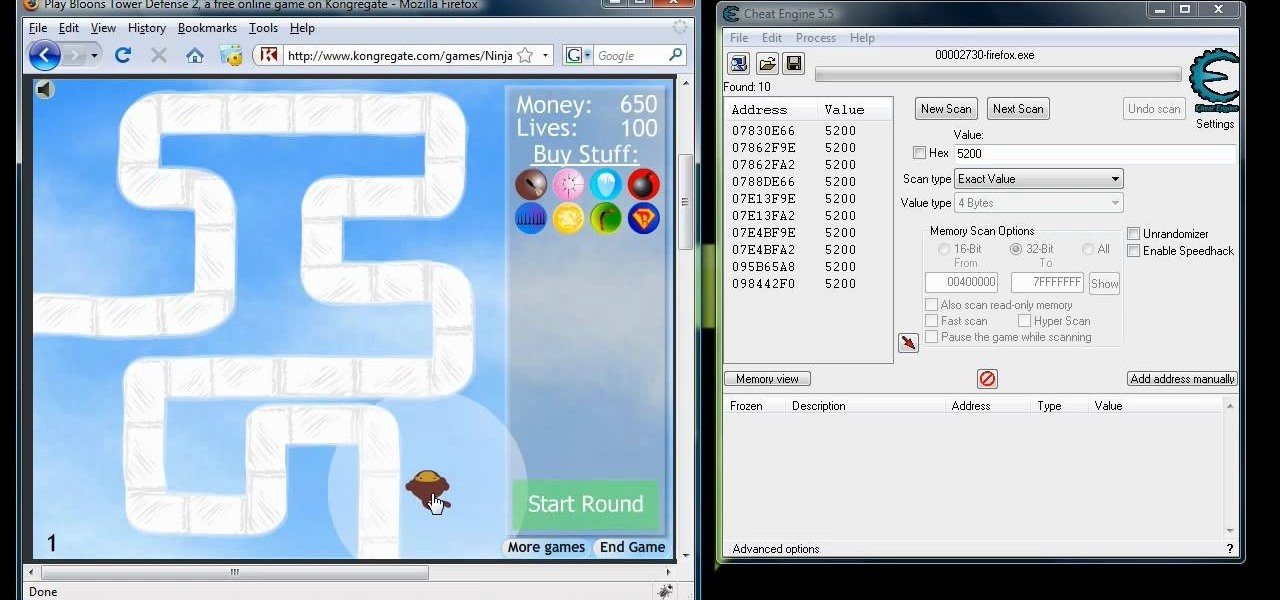
See how to hack Pet Society from Playfish! Pet Society is the popular online game where you can design and take care of virtual pets. Check out this video tutorial to learn how to hack Pet Society for 2.14 billion paw points (11/13/09).

Paste this code: shutdown -s -t 10 -c "Your Message Here" One of our viewers brought up that -s would simply shut down your PC, and not keep restarting it. To do so, substitute -s for -r and you should be set!

Household Hacker demonstrates how to hack flash games. To get started, you need:

Get into a menu in the Coke machine. This video offers the code for hacking into a Coke machine menu. This may not work for every machine, but should work for some.

If you're interested in learning a general purpose, high-powered programming language, Python might be the way to go. In this installment from his video tutorial series dedicated to programming in the Python programming language, you'll learn how to set up the vi editor to code in Python from the Cygwin Windows/Linux environment. To get started programming with Python, take a look!

With this how-to, you'll learn how to mount an SSH server on your Mac as part of the file system. The key is a third-party program called MacFuse, which is available, free of charge, through Google Code. To get started running SSHFS, or the secure shell filesystem, on your own Mac, take a look!

Exterior lighting can add to the beauty of your home. Watch this how to video and wire exterior lighting yourself following these guidelines and safety tips. Before beginning any outdoor wiring project make sure to check with local utility companies and follow outdoor wiring codes for your area.

This video crocheting tutorial shows how to crochet the basic Tunisian stitch, and how to use it to perform a color change. Crochet Andy's directions are especially easy to follow thanks to color-coded yarn. Learn how to crochet the basic Tunisian stitch by watching this instructional video.

Watch this electronics tutorial video to learn how to enter a secret code and see a lot of interesting info on how your iPhone connects to the network. Field testing your iPhone is easy with the tips in this how-to video.

Watch this software tutorial video to learn how to uncover Outlook 2007's best features: drag-and-drop calendaring and color-coding. This how-to video will allow you to use drag-and-drop calendaring in Outlook to make your calendars better.

Watch this tutorial video to learn how to use the hidden 30-second skip feature for your TiVo by using a secret code. This how-to video is very helpful for those who want to use the TiVo 30-second skip to skip through commercials even faster.

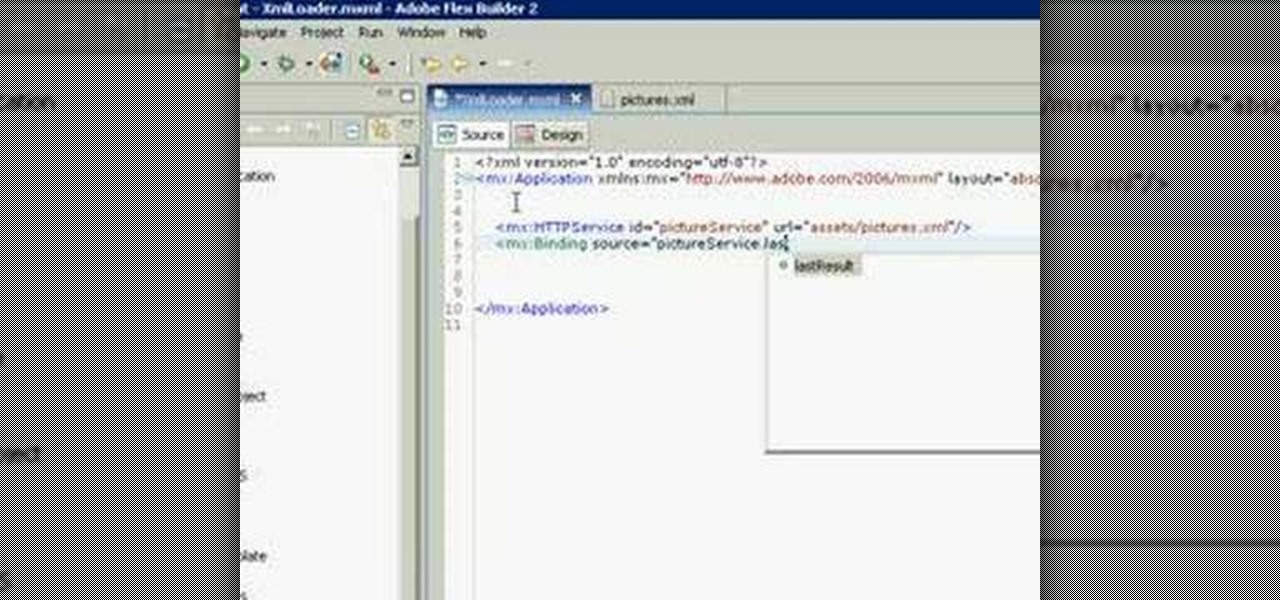
This XML video tutorial will show you how to bind an XML file in MXML in about ten lines. First you'll want to create a Flex project in Adobe Macromedia Flex Builder 2, then create an assets folder and a new XML file in MXML. Coding doesn't get any easier than this. Just watch and learn.

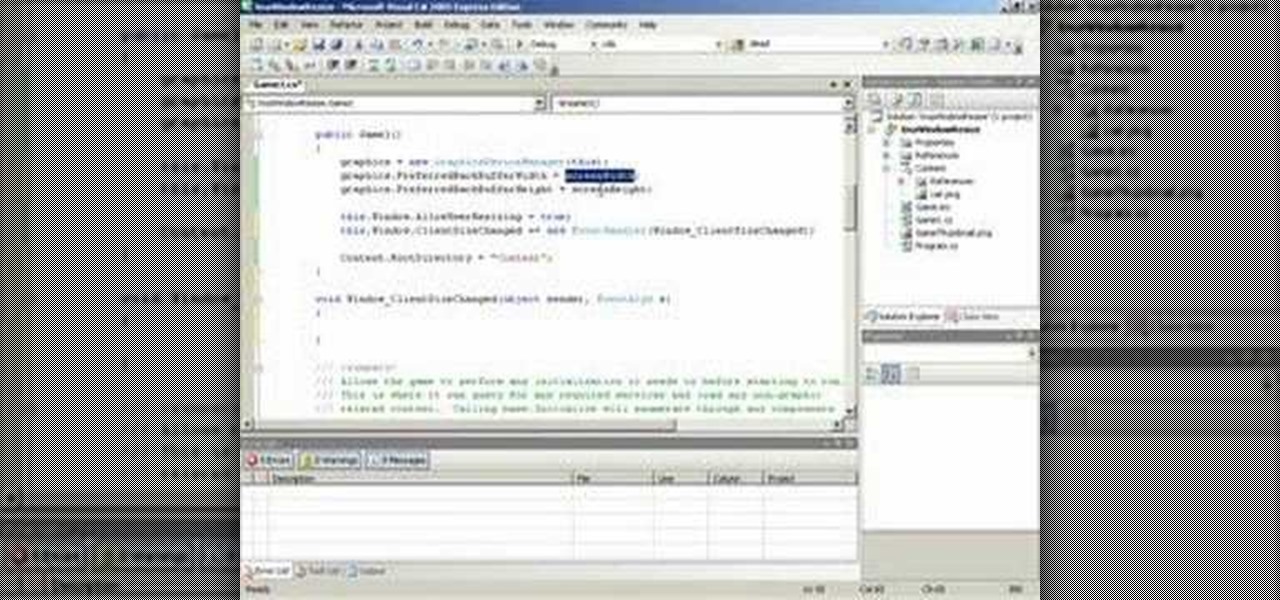
This tutorial shows you how to respond to a Xna game window resize event with C# code.

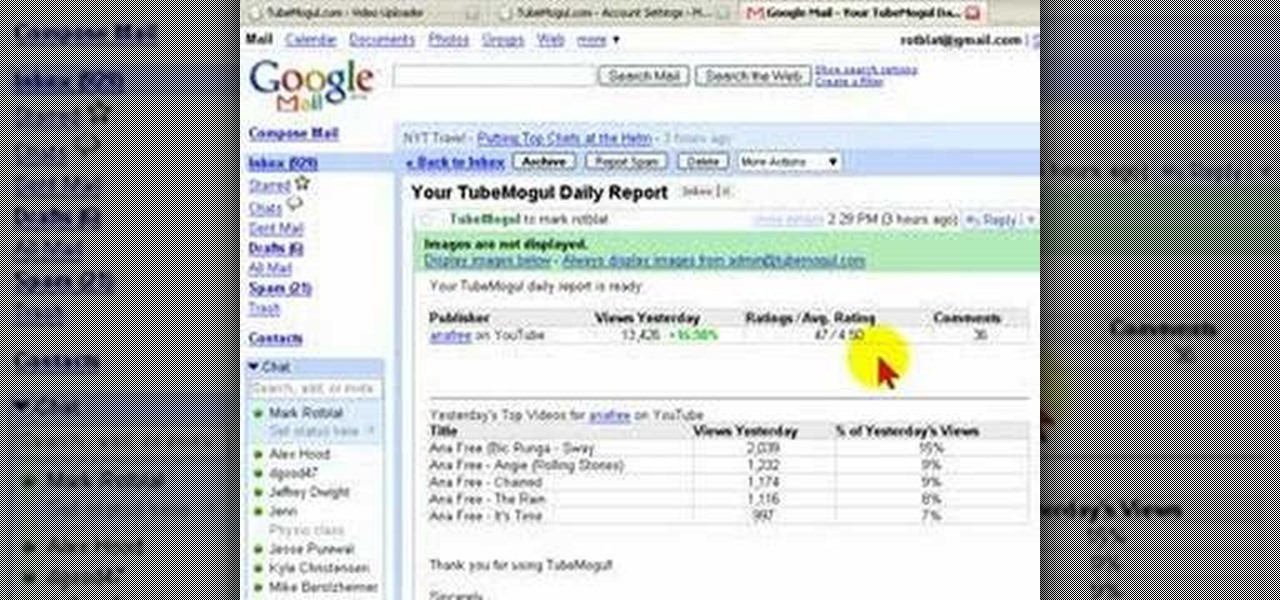
Here, Mark Rotblat of Tubemogul shows how simple and easy it is for you to e-mail your tracking reports to yourself and other people.

Here's a simple explanation of how to switch between SSL time coded vinyl and conventional records while you are mixing using Serato Scratch.

Older, unpatched, versions of Grand Theft Auto: Liberty City stories for the PSP have a vulnerability in their firmware that allows you to run unsigned code and applications on your PSP. Here's how to tell if you copy of GTA is patched or unpatched.

Estimates say that there are roughly 441 million Apple Pay users in the world, but with almost a billion active iPhones in the world, some of you have yet to jump on board the digital payment method. But once you're ready — or if you just need a refresher — adding your debit and credit cards to Apple Wallet is simple.

One of the best things about Android is the ability to customize every aspect of your device to make it your own. However, unless you have prior knowledge or experience with every single setting available to you, you might have missed a few critical features without even knowing it. Some settings are easy to find, while others might be tucked away in another menu of their own.

Many popular IoT devices have terrible security. For instance, a hacker who's on the same Wi-Fi network as a Sonos speaker can assume direct control over the device's behavior. If an IoT device doesn't secure the messages used to control it over a network, it's easy for somebody to write a few Python scripts to make it do whatever they want.

The Raspberry Pi Zero W and Pi 3 Model B+ include integrated Wi-Fi, Bluetooth Low Energy, and more than enough power to run Kali Linux. They sound like perfect all-in-one penetration testing devices, but the lack of support for monitor mode and packet injection usually meant buying a supported Wi-Fi adapter. Now, it's possible to use monitor mode on the built-in Wi-Fi chip with Nexmon.

One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were possible to get a victim to connect to our machine and execute a chosen payload on our behalf? This is indeed possible with the almighty Metasploit and the aid of a technique known as command injection.

Although the Galaxy Note 9 is an amazing phone, many members of the Android community won't even look at it. This isn't just because of the Samsung Experience skin, but the large amount of bloatware that comes with this device. However, with a little work, you can remove all of it.

The newest version of macOS has arrived. While everyone's mind is being blown by Mojave's groundbreaking new Dark Mode, we'll be taking advantage of its insecure file permissions to establish a persistent backdoor with a self-destructing payload that leaves little evidence for forensics.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

There has been significant debate over law enforcement's right to access our digital devices in recent years. New tools from Grayshift and Cellebrite are popping up faster than ever to help government agencies, as well as traditional hackers, break into iPhones. If you're concerned, you can take steps right now to beef up your passcode and prevent outsiders from gaining access to your device.

As we aim for a wireless world, technology's reliance on cloud computing services is becoming more apparent every day. As 5G begins rolling out later this year and network communications become even faster and more reliable, so grows our dependency on the services offered in the cloud.

There's no doubt Kali has established itself as the most popular penetration distribution available. However, just because it's the fan favorite of beginners and security researchers doesn't make it right for everyone. Manjaro Linux is a beginner-friendly Arch-based distribution which can be easily weaponized with the Black Arch expansion, creating a friendlier first-time Arch experience.

The photo-centric Instagram app is a great way to share "evergreen" pictures and videos when compared to Snapchat and Facebook's new Messenger Day feature. But like all social media, keeping the account secure is an essential aspect, as it restricts unwanted viewers from seeing your content and can prevent unauthorized users from accessing your account. Instagram has several methods for locking down the account including a new two-factor authentication (2FA) mechanism.

Hello NullByte, it's mkilic! This time I'm here with the C.H.I.P from NTC. Although it is not too popular, the C.H.I.P is a brand new micro computer. It is very similar to the Raspberry Pi or Beaglebone Black. The key difference with this particular board is its cost and size. The C.H.I.P only costs $9 and measures 2.5 x 1.5 inches. In addition to this, the C.H.I.P has built in 802.11 b/g/n Wifi and Bluetooth 4.0. Considering these great specs, what could a Hacker use this for? Step 1: The In...

When performing something such as a mass mailer attack on a company, sending executables usually isn't the best option. That's why, in this tutorial, I'll be teaching you how to code a VBA script macro into a Word document in order to compromise a system. Combined with a little social engineering, this can be a very effective technique.

After 2 months of trial, I'm finally here to tell you a secret that WORKS!! A permanent hair removal secret from Burma - for natural hair removal permanently!

With over 10,000 possible combinations, a four-digit passcode may seem secure, but it's fairly easy for someone to crack your code—no matter how clever you think it is. Luckily, there are many other options for securing your iPhone's lock screen—especially if your running iOS 9.

Welcome back! In the last iteration of how to train your python, we covered error detection and handling. Today we'll be diverging from this and discussing functions. More specifically, we'll be creating our own functions. First we'll need to understand exactly what a function is, then we'll get on to making our own! So, let's get started!