It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept.

A peek inside the code of the Snapchat app has revealed that the company is expanding the search capabilities of its augmented reality camera to include visual search that may link to items within Amazon's massive online store.

Database technology has vastly improved the way we handle vast amounts of data, and almost every modern application utilizes it in one way or another. But the widespread use of databases naturally invites a slew of vulnerabilities and attacks to occur. SQL injection has been around for awhile, and as such, there are many defense methods in place to safeguard against these types of attacks.

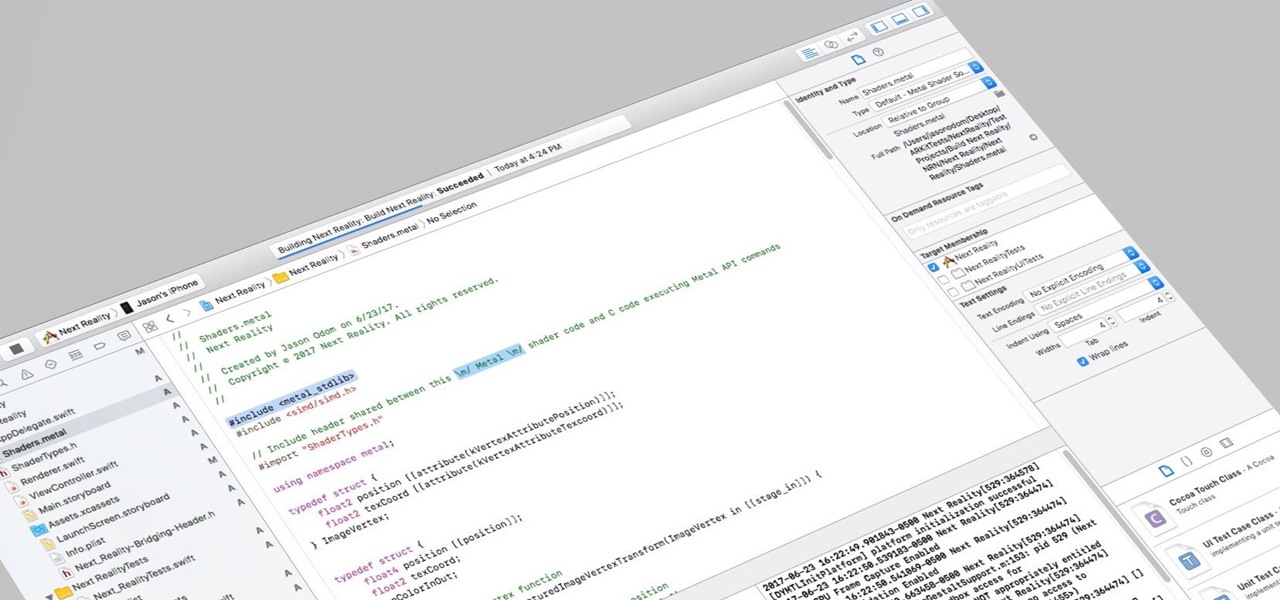
So after setting everything up, creating the system, working with focus and gaze, creating our bounding box and UI elements, unlocking the menu movement, as well as jumping through hoops refactoring a few parts of the system itself, we have finally made it to the point in our series on dynamic user interfaces for HoloLens where we get some real interaction.

In our previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when an MS Word document is opened. Because Microsoft built DDE into all of its Office products as a way to transfer data one time or continuously between applications, we can do the same thing in Excel to create a spreadsheet that runs malicious code when opened. The best part is, it will do so without requiring macros to be enabled.

Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.

I currently am and have always been what one might call a PC/Android guy. Many that know me well would likely even go so far as to say I am anti-Apple. About an hour after seeing the ARKit demo during the day-one keynote at WWDC, I became the owner of a brand new Mac.

There are a lot of exciting improvements in store for Siri in iOS 11. Apple showed off some of the highlights at WWDC, but there are five changes in particular that you don't want to miss.

One of the most exciting features in iOS 11 was the fully revamped Control Center, which improved the overall interface visually, made it one page only, and finally made it possible to customize what controls actually appear within it. Customizable controls was previously only available to jailbreakers, but now it's available to anyone running iOS 11 or iOS 12.

Google added a new feature to its mobile app that pairs your searches for events with direct summaries of activities from sites like Eventbrite and Meetup. If you see an event you like, then you can tap on it to check it out for more fun details or book your ticket directly through the providing website.

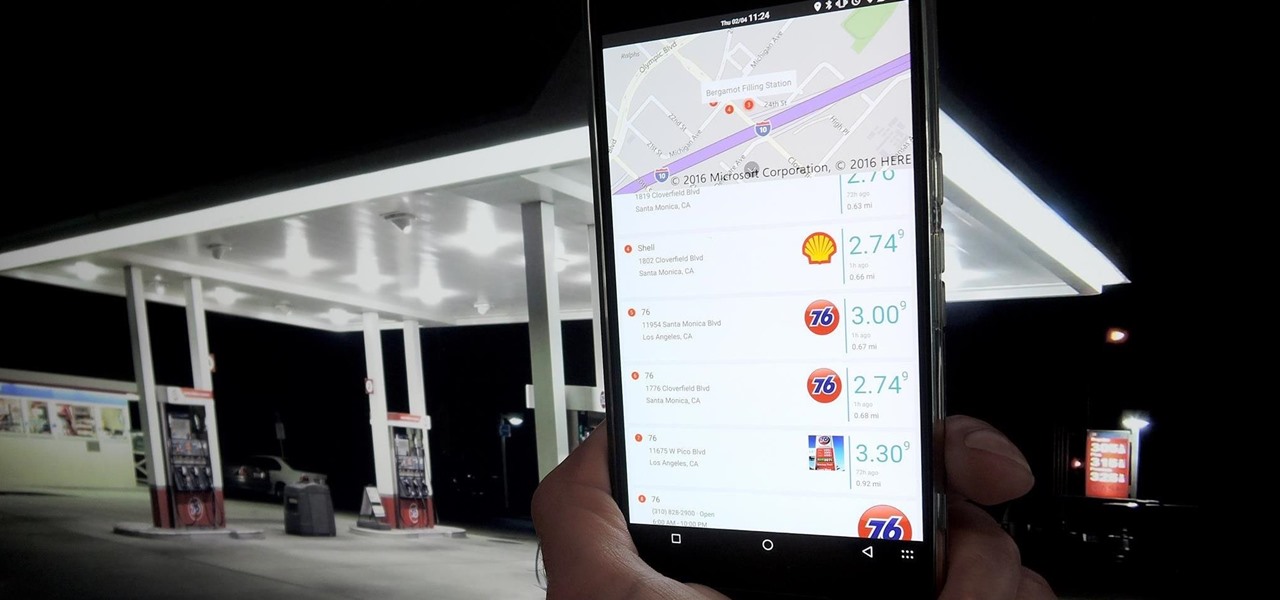
Whether you're a professional mechanic, a hobbyist, or someone who just wants to know why their check engine light came on, your Android device and an OBD-II adapter can provide insight as to what's going on with your car. Most adapters sell for less than $10, and once you plug it into your vehicle, you'll just need a good app to help you make sense of all the data it can gather.

While it remains unknown how exactly augmented reality will make its way into the mainstream (the Microsoft HoloLens sitting at $3,000 isn't exactly accessible), many brands have been trying to integrate the tech into their mobile apps, mimicking the success of Snapchat and its popular AR filters. One of those brands going all in on augmented reality is Shazam.

A market research report, posted on February 27, 2017, forecasts that the image recognition market will grow to nearly $40 billion worldwide by 2021. The market, which includes augmented reality applications, hardware, and technology, generated an estimated $15.95 billion in 2016. The report estimates the market to grow by a compound annual growth rate of 19.5% over the next five years.
In this Tutorial I will show you how you can use the frequency of letters to decrypt the famous Caesar cipher. I hope it is easy to understand and helpful for getting in touch with basic cryptanalysis. If you find any mistakes or have questions feel free to ask me. Finally I ask you to give me feedback which I will take into account for the next part.
Fugu - a simple virus in bash. I once told a friend of mine I'd written a virus in bash and he scoffed - "You can't write a virus in bash!" - he sniggered, like an ignorant idiot.

Microsoft is working hard to make Bing a good alternative to Google for more than just looking up images of the "human anatomy" that Google and a lot of other search engines filter out of their results.

Researchers have discovered a "severe vulnerability" that allows attackers to use eBay to distribute malware, and the online auction company has no plans to fix the problem.

Welcome to a tutorial on XOR encryption. We'll be looking at what XOR is and how we can use it to encrypt or decrypt data.

Hey guys, in this tutorial, we are going to learn about the heap segment and how to use it for storing data in our programs. We will also go into the details of its use in conjunction with the char pointer and struct data types.

Welcome fellow Null-Byters! Sorry for the delay, this time of the year can be hectic for all of us. Hopefully this will not happen again. In this "tutorial" we will go over more styling and make our page look even better!

Welcome back to another tutorial on functions. Last time, we looked inside memory to see what functions looked like in the flesh and all that Assembly was pretty nasty. At least you have some exposure to it. This time, we will be examining how functions work with the stack.

Welcome back to control structures, part two featuring the three types of loops. Here we go! What Is a Loop?

Hello null_byters, after some time out here we are again with another tutorial, continuing our beautiful series, today we will write our first real world bash script.

Welcome to the Part 2 of the series 'Cryptocurrency'. It has been late because of some errors, where all I typed was lost.

Welcome back, rookie hackers! We recently began an exploration of ways to hack using the Bluetooth protocol. As you know, Bluetooth is a protocol that connects near field devices such as headsets, speakers, and keyboards. Its minimum range is a 10-meter radius (~33 feet) and maximum is at 100 meters (~328 feet).

For those unwilling to wait until the Fall for the official release of Apple's latest Mac OS X, El Capitan, you can sign up for the public beta today and get it sometime this summer. If that's still not soon enough for you, there is a way to get it on your Mac right now.

At last, what you all finally waited for! Hi! Fire Crackers,

Welcome back, my fledgling hackers! With this first article, I am initiating a new series intended to convey to my readers the skills necessary to develop your own exploits.

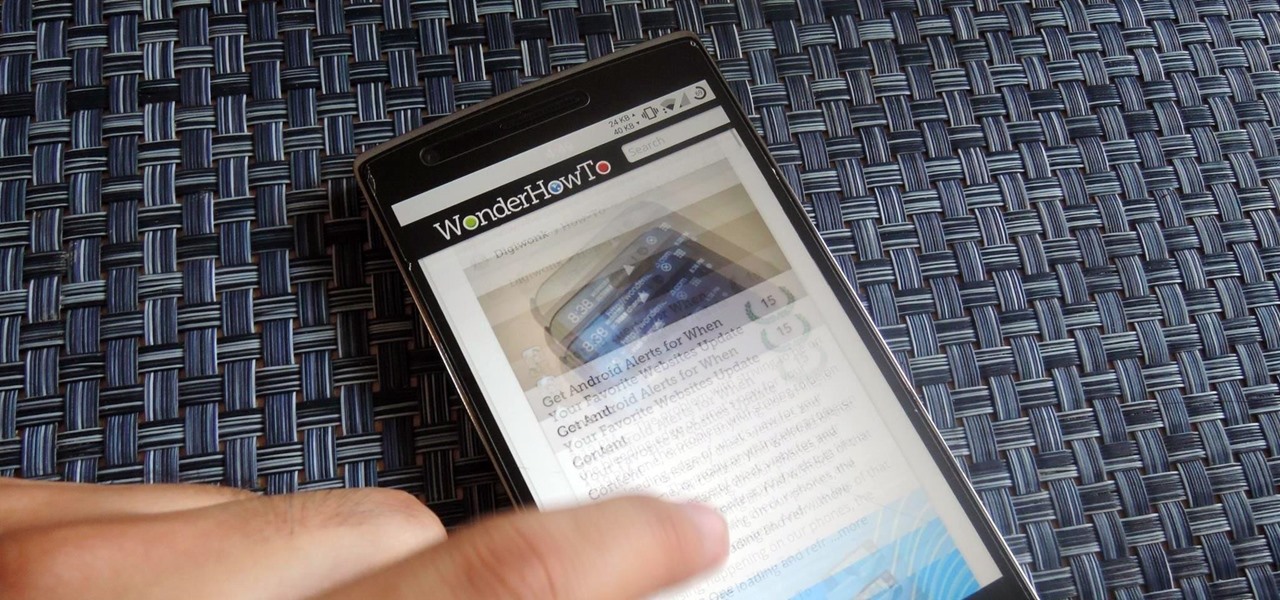
The hardware running your One is nothing short of powerful, but the people at OnePlus can't control how developers choose to utilize that power—or rather, not utilize it. Most popular developers have removed all signs of lag from their apps, but others still have archaic lines of code that can make your shiny, new device feel like a first-generation smartphone.

While most of us don't think twice about dragging a pattern or using Touch ID to open our phones, or entering a password in for our email and bank accounts, these features are there to protect some of our most private information. Only problem is, they don't do a good job of it.

If you're trying to get a new iPhone 6 or 6 Plus, we know you've been struggling to find one, and we're here to help. With Apple's preorder numbers topping 4 million in the first 24 hours, it was nearly impossible to get one during the first wave.

This past year, Facebook spent $19 billion purchasing the popular messaging app WhatsApp, and for good reason. Mark Zuckerberg isn't going to spend that type of money on just any application. WhatsApp is widely popular and frequently used by more than 500 million users worldwide, which is almost twenty percent of the Earth's population.

A friend of mine has a crazy amount of Reddit karma and gold, and yesterday he let me in on his secret. This person, who will remain unnamed for obvious reasons, created a Python script called Reddit Karma Crawler that finds rising posts before they get too popular.

I love Android, and I think its apps are great—the polish that came with the Ice Cream Sandwich update truly put Android design on the map. That being said, one of the more frequent complaints from iOS fans continues to be that apps just "run smoother" and "look better" on iOS than they do Android.

As with most OEMs, HTC would like you to think that you can do virtually anything with your new HTC One M8, but as a softModder, you know that isn't true. To actually unleash the full potential of that device, you need access to the whole system, not just the parts that HTC deems okay for you to mess with.

Locking up your iPhone with a passcode prevents mischievous friends from looking at your pics and emails, and makes it harder for thieves to access your data before you get around to wiping it. For even more security, there's the password option, which gives you more than just 4 lonely digits.

Unless you like paying exorbitant prices for out-of-contract phones, most of us are stuck with the one we already have for two or more years. The tech industry moves fast, and as new phones are released seemingly every month, your Samsung Galaxy S4 might start looking older by the week.

For the most part, transferring files from your computer to your Nexus 7 (and vice versa) is a simple process. Just hook up your tablet to your computer with the USB cable and transfer. However, most of the time you'll need additional software on your computer to do this, and then, of course, you need the USB cable.