Security journalist Brian Krebs recently suffered a record-breaking DDoS attack to his his website, clocking in at or near a whopping 620 Gbps of traffic. Krebs' site was down for over 24 hours, and it resulted in him having to leave his CDN behind.

A little less than a year after announcing "Project Astoria," Microsoft announced Thursday, February 25th, that it will end the "Bridge," which would have brought Android apps to the Windows Store.

Alright, this will be my first tutorial in C. Note that this guide is written for Linux.

Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the victim portion of the shell. Today, we'll be building the attacker portion. This script will initialize interaction with the victim portion of the shell, send commands, and receive the output.

Hello aspiring hackers, It's been a while since I wrote a tutorial, so I figured I might just share one of the tools that I have created to help the community grow.

Welcome to the final tutorial of the series on standard C. This article will cover the linked list abstract data type (ADT). There will be a lot of abstraction to try to deliver the understanding in the most basic way for easiest interpretation of what they are and how they work, then we will get into the guts of it and learn the technical code underneath. For those who have yet to grasp the concept of pointers, it's advisable that you do that first before approaching this. Having learned thi...

Hello there Nullbytes, In my previous tutorial found here,

In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.

What's up, peeps? In this quick tutorial, we will be looking at structs, a special kind of data type.

Welcome back! In our last training session, we covered some advanced list topics. We'll be going deeper into the advanced list rabbit hole today with lambda and lambda operators! (And I'm not talking about Gordan Freeman)

Hello fellow training hackers. I do not know if many of you are familiar with ruby, but since it is a useful scripting language, that hasn't been covered too much here on Null Byte, I thought why not do some How-tos about it now and then.

One of the highest rated posts on Spotify's own community forum is titled "Add support for Google Chromecast," a clear indicator of not only how much this feature is desired, but also of Spotify's lack of care for it. Remaining consistent with statements made in the past, Spotify is firm in their decision to not pursue Chromecast support at this time—or maybe ever—thanks to a deal with Sonos and Spotify Connect.

Well, this is my first article so if it sucks tell me...lol!! Story Time

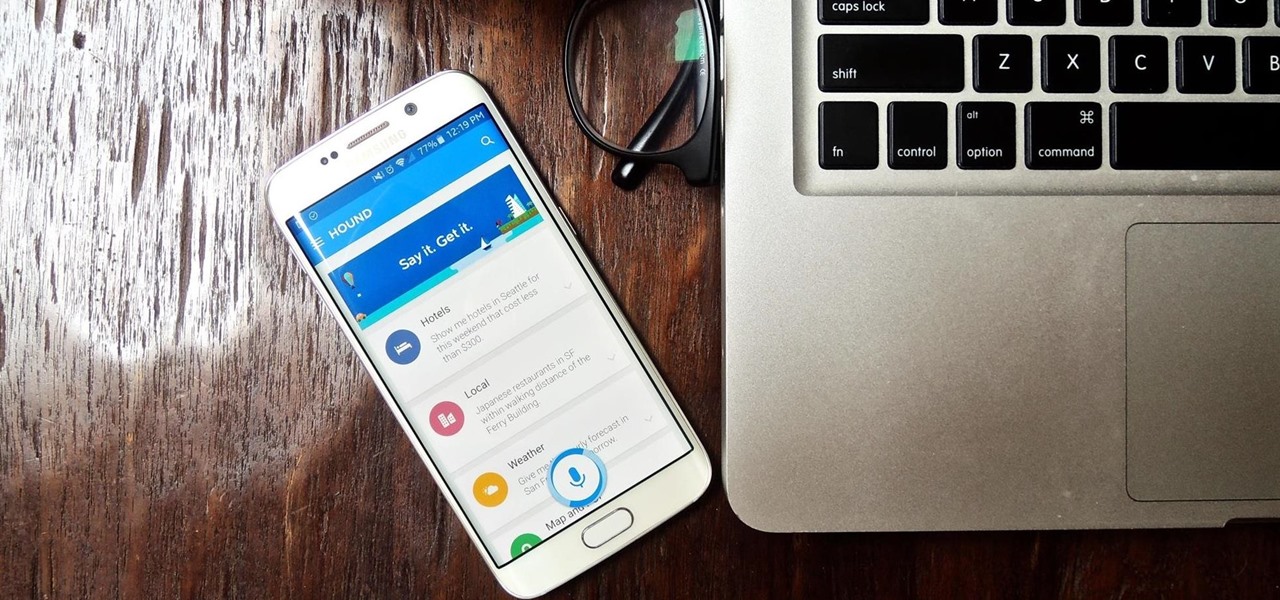
SoundHound's new virtual assistant application, Hound, is gaining a lot of buzz in the tech world—especially after a demo video showed just how awesome it works (it has amassed over 1.6 million views in under a week).

Based on OTW's encouragement in his post on "How to Find the Exact Location of Any IP Address", I decided to make a gui(graphical user interface) which would hopefully make the process easier. However, because turning a python script into a standalone executable is a right pain in the nether-regions, particularly for linux, I haven't yet completed this step(I will soon and update this). I did however, make an apk for android(you use a .apk file to install an app on your android device), which...

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

When going out to eat with friends, it's inevitable that one person takes charge at the end of the meal to split the bill. They whip out a pen and begin asking everyone what they ordered, carefully dividing, adding, and subtracting on the back of the receipt for everyone to use. Unfortunately, that never seems to work as intended. One person will end up paying a little more, while another will pay less.

Hello Elite Hackers! Welcome to my 3rd Post, which explains how to hack any account like G-mail, Facebook, etc.

There are many ways to take a screenshot in macOS (previously Mac OS X), but all of the well-known options give you a drop shadow in the picture when snapping application windows.

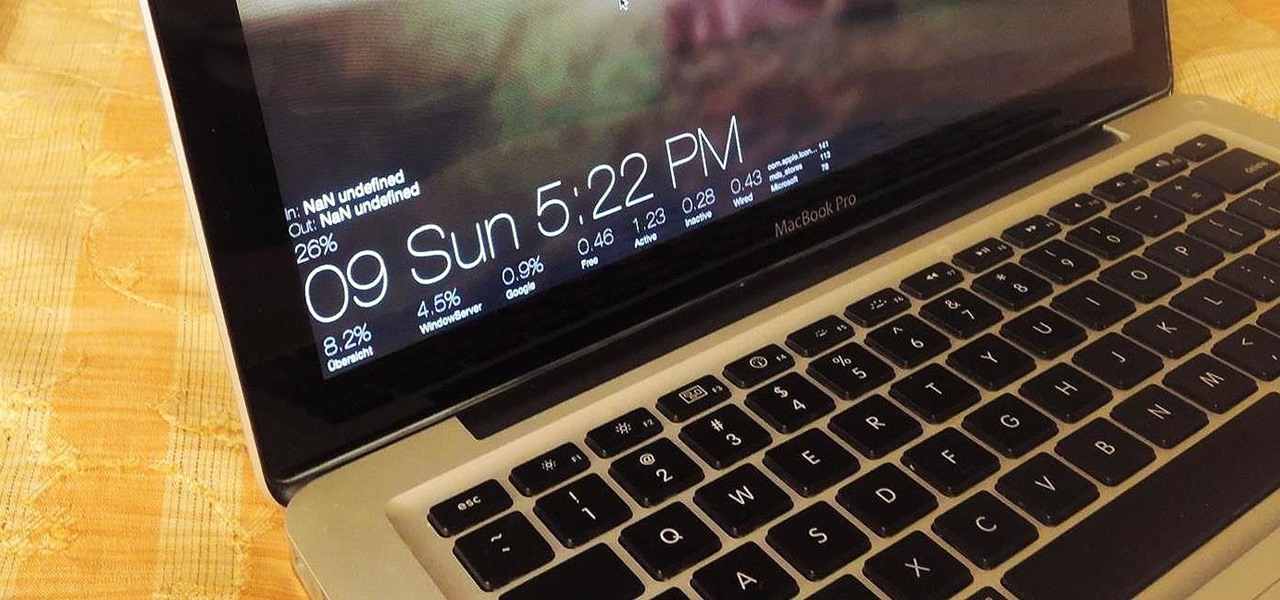
Apple hasn't been the most avid supporter of widgets over the years. Yes, they added them to the Notification Center in Yosemite, but that requires a drawer to be opened and closed whenever you want to check them. In my search for a better solution, I came across Ubersicht by developer Felix Hageloh.

When I stumble upon a new song that I'm really into, I don't just listen to it repeatedly—I share it with family and friends that I think might enjoy it just as much as I do. Now, thanks to a new iOS app called Craaave, sharing those tunes are a cinch, no matter if I'm using Spotify, SoundCloud, or any other music streaming app on my iPhone.

With GPS chips and Wi-Fi positioning systems, a modern smartphone is capable of tracking its user's location with pinpoint accuracy. This being the case, it's strange that the most common text message sent today is still "Where are you?"

Thousands of history files, cookies, other unwanted files stored in your system as logs and other formats. To manually check each one is difficult. New computers are too fast by processor behavior, after some times of working it comes to slow performance.

Even if you have the fastest internet connection in the world, it's not going to be fast if your Android device isn't optimized to use all of the bandwidth. I have pretty fast speeds at home, but every now and then my web surfing on my Nexus 7 tablet is halted in its tracks—for seemingly no reason.

Why can't I see who is stalking my Facebook profile?

Apple is widely known for keeping a tight grip on iOS, disallowing open-source and third-party downloads. While there are many reasons for this, the three most frequently referenced are quality control, malware prevention, and of course—money.

When the HTC One was announced, the fact that its IR transmitter was a side note more than a main feature made me dismiss it. When Samsung included one in the GS4, it became even less impressive. However, now that I actually have a One, I find that the "TV" app is way more than just one of Samsung's "S"-gimmicks. Step 1: Set Up Your Service Provider

The mighty Arduino microcontroller can be used to show children how robots work, it can be used to hack into hotel rooms, or it can be used to let you know when you've got a new job opportunity!

Let's say you forgot the code to your Master Lock combination padlock. What can you do besides buy another one? Well, there's a surprising abundance of ways to open a combination lock other than with just the combination, some of which will even let you reset the code. Of course, these hacks aren't limited to folks just looking to open their own locks, but let's just assume that's what you're here for.

WordPress started in 2003 with a single bit of code to enhance the typography of everyday writing and with fewer users than you can count on your fingers and toes. Since then it has grown to be the largest self-hosted blogging tool in the world, used on millions of sites and seen by tens of millions of people every day.

If you've never heard of geocaching, it's kind of a grown-up treasure hunt you play everywhere in the world. GPS coordinates are given as clues and the players must find the cache box. There is usually a log book to write your name and a small toy or present to collect.

Change object colors via ActionScript in Flash 8

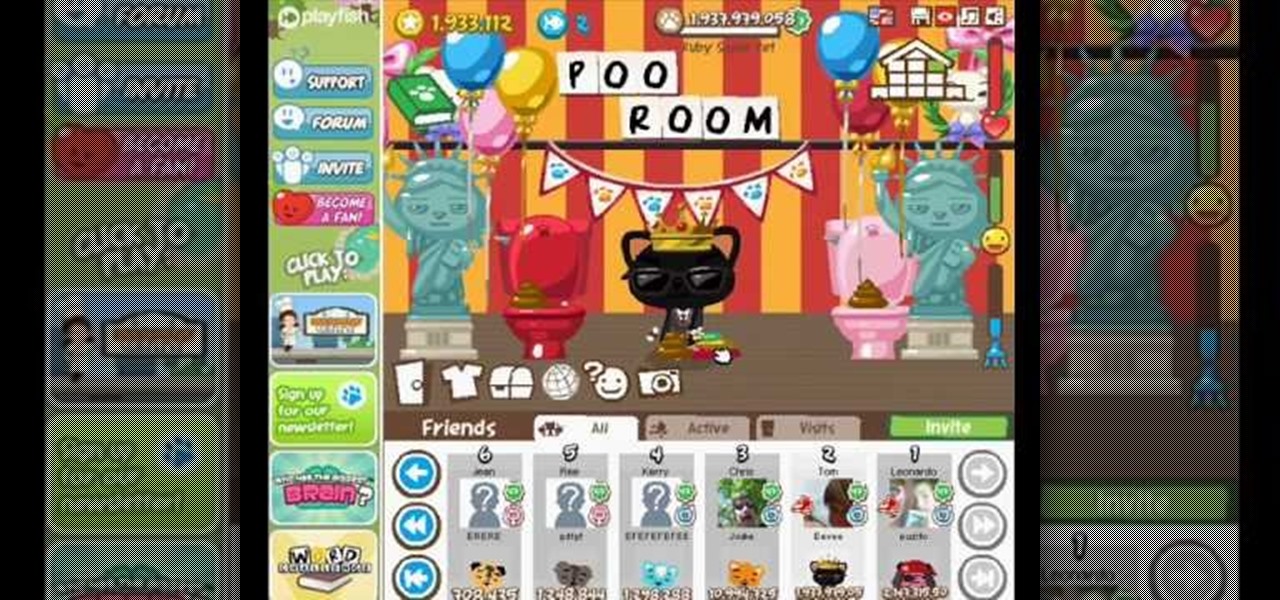
How to hack Pet Society! Pet Society cheats, tricks, hacks. Watch this video tutorial to learn how to hack poo and coins on Pet Society (09/10/09). See how to get unlimited poo: normal, gold, or rainbow! You can sell them for lots of money!

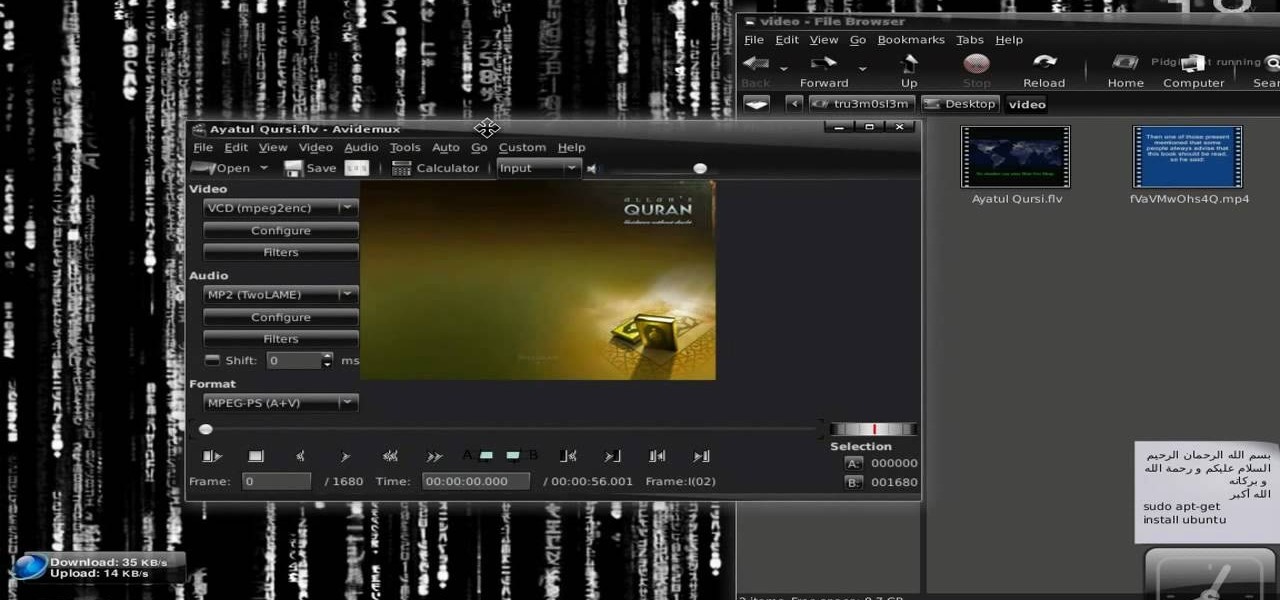
New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to convert video formats with Avidemux on Ubuntu Linux.

You know YouTube is able to host high-defintion video content online now, right? Well, how do you watch it, or make it, or embed it? Well, this video tutorial will show you how to upload, embed and watch 720p HD video on YouTube. This YouTube hack will let you watch and embed videos in true 1280x720 high definition.

They are after you from all over the globe. Looking for ways to exploit you. Ways to hurt you. Not political terrorists, but rather "info terrorists." Each month thousands of websites get hacked into and have hidden links inserted into the pages by people wanting their spam sites to rank highly in the search engines.

Since 2020, you've been free to set your preferred web browser and email app as the default on your iPhone or iPad. Now, four years later, Apple is expanding this flexibility in the U.S., allowing even more apps to be set as defaults for specific actions. Plus, there's now a centralized menu to manage all these default app settings.

Python is commonly touted as one of the best programming languages for beginners to learn, and its straightforward syntax and functionality makes that hard to argue with. But a lot of tutorials still use Python 2, which is outdated now. Python 3 introduces many new features, and it's important to be aware of them going forward, as well as the key differences between Python 3 and its predecessor.

I've covered augmented reality apps for about three years now and the most useful mobile app I've encountered over that time is Google Lens.

Overall, iOS is more impressive than ever with its stability enhancements, security tools, suite of apps and services, and intuitive user interface. With each passing update, things just get better and better for iPhone users. But don't think for a second that this is all because of Apple's genius — many of these features were at least partly inspired by tweaks made by the jailbreak community.