They're finally here. Apple announced three new iPhone models at their "Gather Round" event in Cupertino, and they're all absolutely gorgeous phones. With bezel-less screens and polished titanium edges, the iPhone XS, XS Max, and XR are truly marvels of engineering — but perhaps the most impressive design feat Apple pulled off is the fact that two of these models are rated IP68 under the IEC standard 60529.

Facing mixed reviews for the Magic Leap One, Magic Leap has already returned to the lab to improve on the device's successor.

After a $20 million funding round fell through, augmented reality headset maker Meta Company has been forced to furlough (or place on temporary leave of absence) approximately 65% of its workforce for 30 days.

Better known among consumers for its virtual reality apps, Jaunt is now pivoting toward solutions for augmented reality developers.

If you want the best two-factor authentication app out there, our pick is Authy. A close second is LastPass Authenticator. If neither of those is to your liking, try Duo Mobile or Microsoft Authenticator. But if you're fine with missing out on great features, then and only then should you look at using Google Authenticator.

The fortunes of ARKit and ARCore are still in the hands of developers, who have been increasing the number of mobile augmented reality apps on the market, but perhaps not as fast as companies like Apple might have expected. But one new product is looking to literally kickstart mobile AR gaming by introducing a few key components that harness the traditional board game model.

As we predicted earlier this week, the focus has already begun to move from Magic Leap back onto Apple's rumored augmented reality smartglasses. The latest credible whispers come from none other than longtime Apple-focused analyst Ming-Chi Kuo.

When Magic Leap One owners unbox their new devices over the next few months (or, if they are lucky, days), they will have some familiar augmented reality news content to consume.

Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. We'll use Wireshark to discover a Wi-Fi attack in progress and determine which tool the attacker is using.

In the lead up to the Magic Leap One launch, Magic Leap has been coy about what the actual field of view (FoV) is for its first commercial product.

On Tuesday, Unity released the latest version of its 3D engine, which brings improvements to the Scriptable Render Pipeline that the company introduced earlier this year.

You've protected your Ubuntu system from physical attacks, annoyed network hackers, and sandboxed potentially malicious applications. Great! Now, the next logical steps to locking down your OS include thoroughly auditing Ubuntu for weak points, using antivirus software that respects your privacy, and monitoring system logs like a boss.

If you ever want to root your OnePlus 6, install TWRP, get Magisk and Xposed, or flash a custom ROM, the first thing you'll need to do is unlock your bootloader.

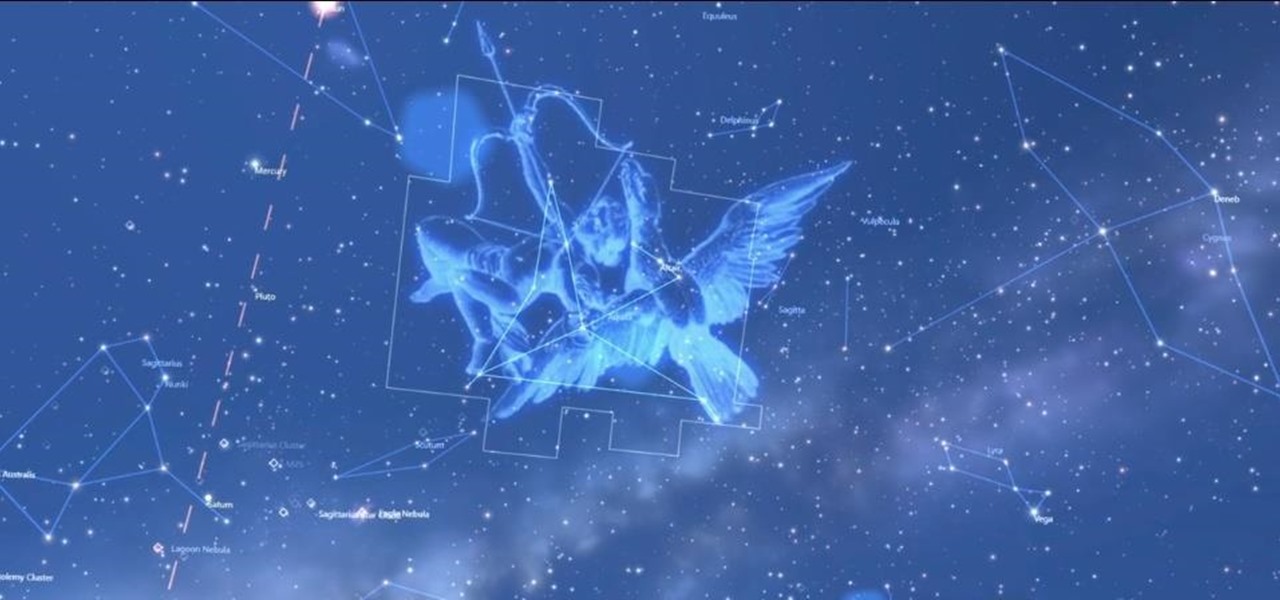
On June 23, National Geographic will begin welcoming visitors to the world's first outdoor planetarium in Quebec, Canada, where an augmented reality experience overlaid on the night sky will replace the projection systems of traditional facilities.

The addition of a new research mode for Microsoft HoloLens will enable researchers and developers to tap into a wider range of data collected by the device's sensors.

With all the talk about the impending release of the Magic Leap One, some have forgotten a very important, competing release on the near horizon: the HoloLens 2.0. Well, now we have new information that tells us when (roughly) the device will be released, as well as a few other exciting tidbits.

Even in augmented reality, Wile E. Coyote still can't catch the Road Runner. The latest AR experiment from developer Abhishek Singh brings the classic Looney Tunes duo into the real world.

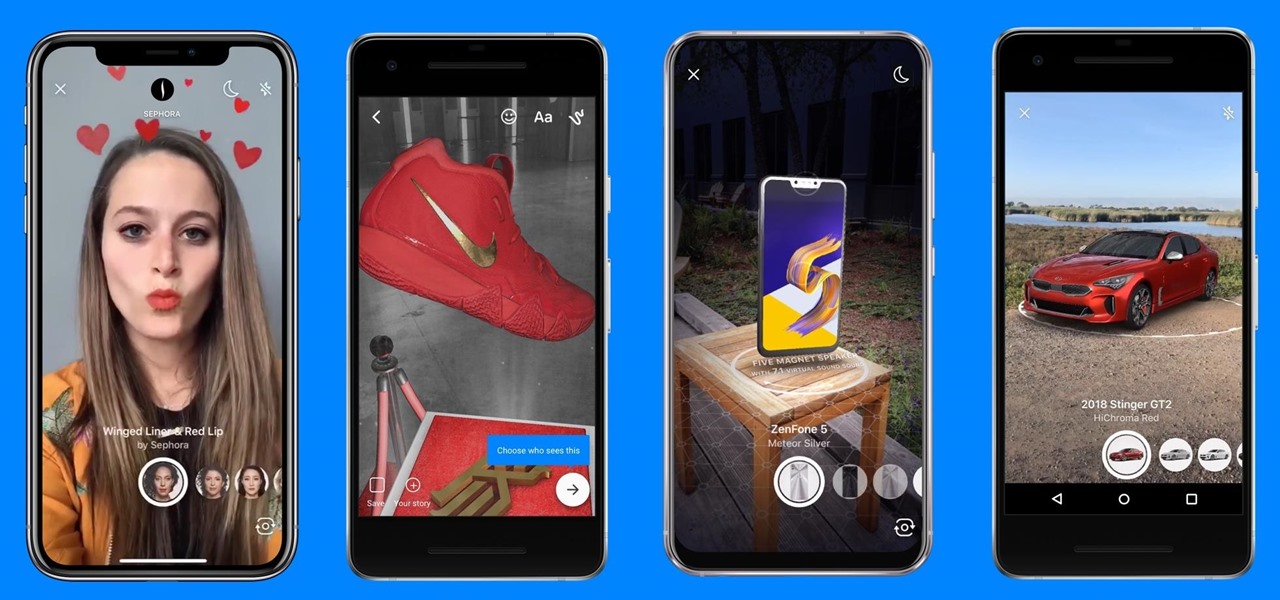
On Tuesday, on the one-year anniversary of the announcement of its AR Camera platform, Facebook founder and CEO Mark Zuckerburg revealed at the company's F8 developers conference that the platform will be extended to the company's Instagram and Messenger apps.

For social media platforms like Facebook, augmented reality represents a whole new art form with which users can express themselves online. Now, Facebook is giving those users a new brush.

The augmented reality and VR arm of Verizon, Envrmnt, wants to make it really easy for anyone to create AR apps.

Netflix currently lets parents block content based on maturity rating, but it isn't a perfect system. Not all titles rated PG-13 are equal, for instance. That's why it's good news that Netflix is adding more controls for parents, by allowing account holders to bar individual movies and TV shows they deem inappropriate.

Eventually, even the most private company has to file its patents and unveil its tightly-held secrets, and Magic Leap is no exception.

Oreo, the latest and greatest Android OS, lets you enjoy a ton of new features such as app shortcuts and an improved keyboard. But thanks to a feature that's required of all phones that ship with Android Oreo out of the box, your S9 may be the first Galaxy phone to finally receive timely software updates.

The day has finally arrived — Samsung has unveiled the Galaxy S9 and S9+. Apart from minor upgrades, the two might not appear to be much different from last year's S8 and S8+, but that's not necessarily a bad thing. One feature that hasn't changed is the Galaxy's IP68 water-resistance rating. That's a great score, but it begs the question — what does that number really mean?

If you're an Android user, you're very likely jealous of your iPhone friends who have access to the wide, wonderful world of augmented reality thanks to ARKit.

Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website was viewed. There's no doubt Coinhive, an innovative mining method, is being abused and exploited by hackers in the wild.

By default, images embedded using external links will not automatically load in any emails that you get with ProtonMail. This is a security mechanism that can prevent malicious code from being executed on your system, but it can also be fairly annoying to have to manually load images in email after email.

One of the most overlooked components of talking about augmented reality and virtual reality is getting people to actually use the hardware and software associated with these platforms.

With iOS 11.2's introduction of Apple Pay Cash, you can send and receive money to others directly through iMessage, using the convenience and security Apple Pay is known for. However, if you want to make sure your efforts go uninterrupted, you'll want to make sure you verify your identity with Apple.

OpenBSD implements security in its development in a way that no other operating system on the planet does. Learning to use the Unix-like operating system can help a hacker understand secure development, create better servers, and improve their understanding of the BSD operating system. Using VirtualBox, the OS can be installed within a host to create a full-featured test environment.

A mention of the deep web can bring to mind images of drugs, hackers, and other criminal activity. Despite the presence of these elements, the Tor network is a valuable tool for preserving privacy and anonymity. And browsing the deep web and any hidden services can be as simple as downloading the Tor Browser.

When Google announced its ARCore augmented reality toolkit for Android as its answer to Apple's ARKit for iPhones and iPads, the question from many observers was, "What about Tango?"

Armis Labs has revealed eight vulnerabilities, called "BlueBorne", which put 5.3 billion Android, iOS, Windows, and Linux devices that use Bluetooth at risk. With it, hackers can control devices, access data, and spread malware to other vulnerable devices through networks. In this post, we will learn about the vulnerabilities, then look at how to find devices that have them.

Augmented reality software maker Upskill has released the latest version of their Skylight platform, adding a number of new tools to ease implementation and improve functionality for enterprises, including a new application builder.

Avegant Corporation has begun shipping display development kits based on its light field technology that other companies can use in their augmented and mixed reality devices.

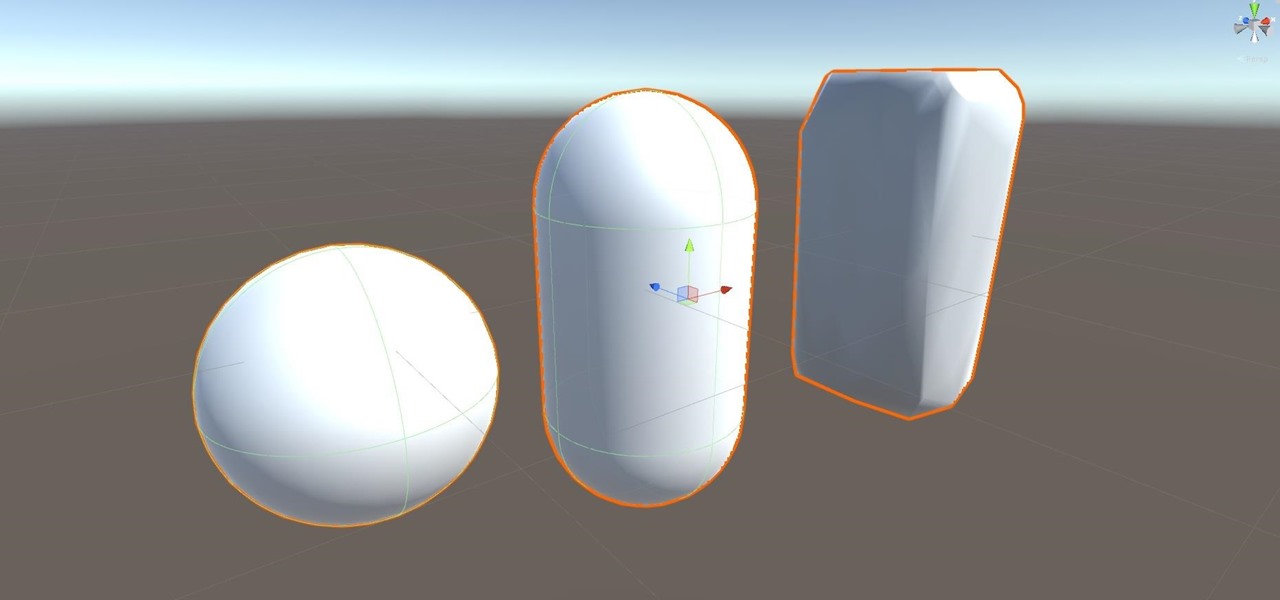
Alright, calm down and take a breath! I know the object creation chapter was a lot of code. I will give you all a slight reprieve; this section should be a nice and simple, at least in comparison.

As we have seen previously with the likes of SethBling's Mar I/O videos and other examples, video games seem to be a great source for training AI neural networks. Augmented reality and machine learning are part of a collection of technologies that seem to be growing toward a point of maturity, and that will likely cause them to be intertwined for the foreseeable future. As developers, machine learning will definitely change the way we create software in the coming future. Instead of going lin...

Every time you make a call or send a text, you're giving the recipient your phone number. This can be quite the security vulnerability, opening yourself up to scammers, spammers, and the feds. In this how-to, we'll look at what a burner phone is, why you might want one, and how to get started using a free second phone number on your regular smartphone.

Alright, let's dig into this and get the simple stuff out of the way. We have a journey ahead of us. A rather long journey at that. We will learn topics ranging from creating object filtering systems to help us tell when a new object has come into a scene to building and texturing objects from code.

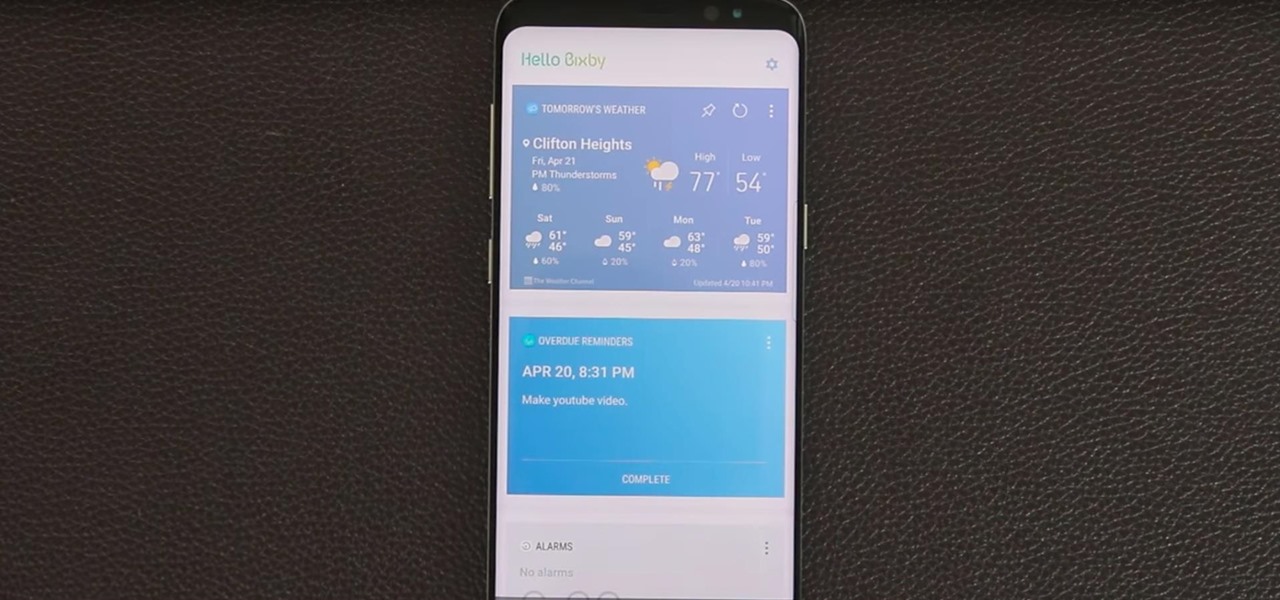
Bixby — Samsung's voice-activated digital assistant — has been delayed again because the software still can't recognize English. Although Samsung claims Bixby can execute 15,000 tasks, it appears it's inability to master English is a major obstacle that's preventing its full release in the United States.