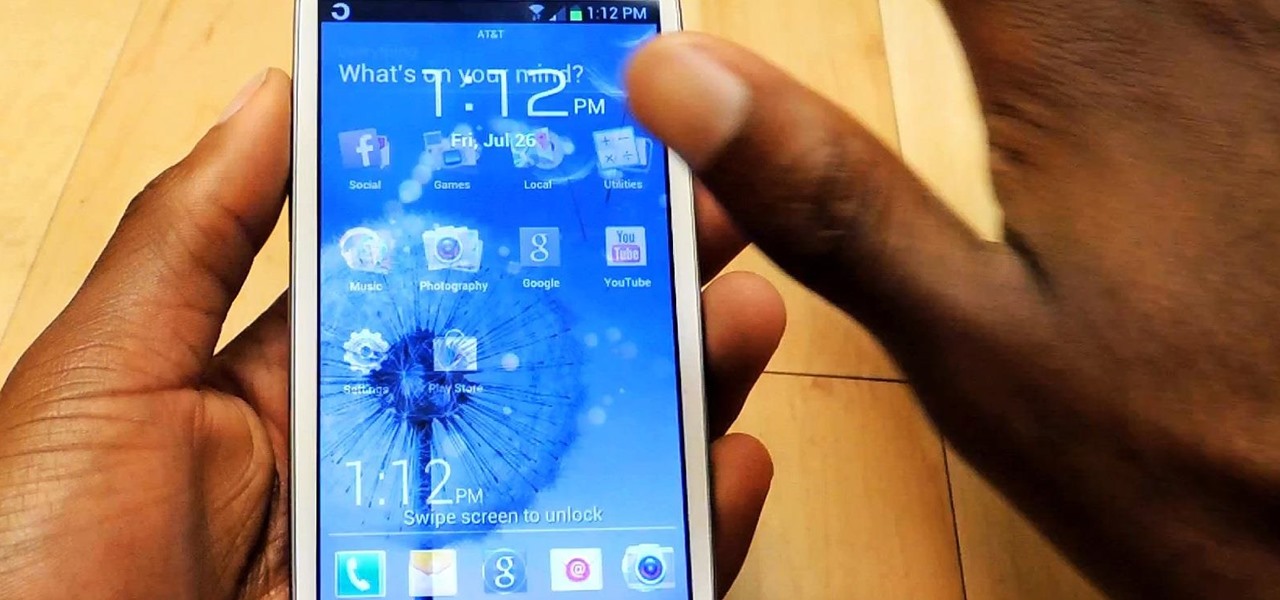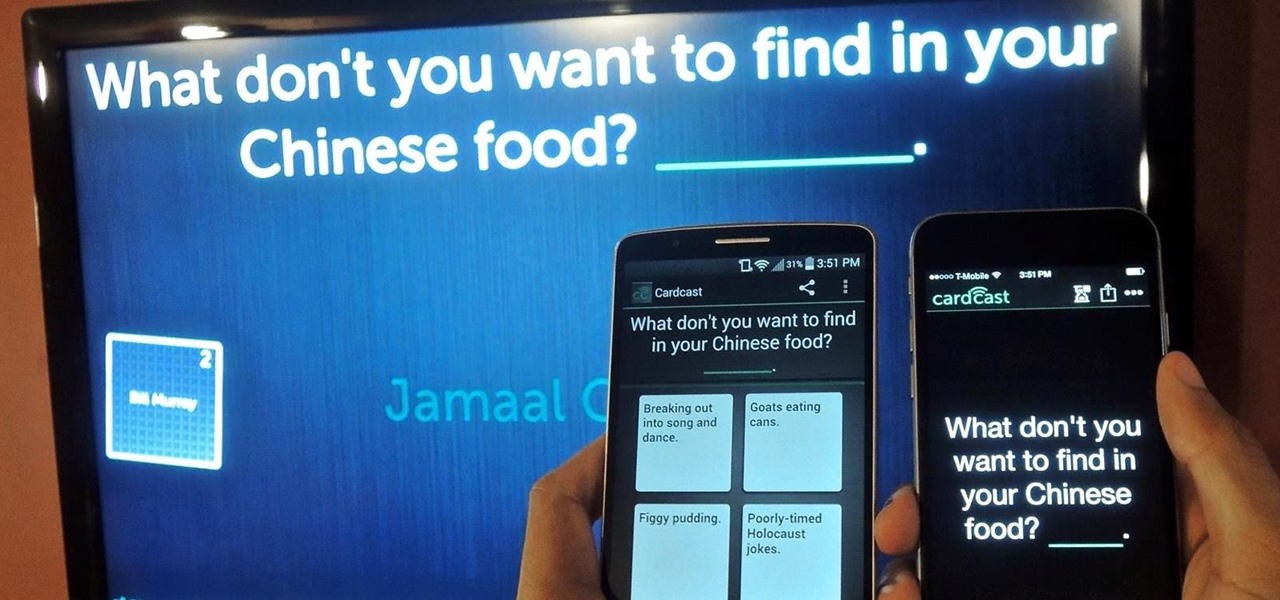
The future of game night is digital. Your Chromecast is great for watching Netflix or YouTube, but get more use out of it by making it the centerpiece for your next fun get-together.

Want to get even this Halloween? Want to scare somebody with nothing but a few lines of code? Here's how it can be done...

I have never been a morning person, and that's a trait that I don't think is going away. Combine my distaste for early hours with being a heavy sleeper, and it adds up to a lot of alarms being dismissed in a haze, with no real intention of ever waking up.

Ah, the age-old problem of sharing pictures with friends and family. Ten years ago, the best method available to us was passing around duplicate photos printed out at the local drug store. As easy as smartphones have made this act, you'd think we'd be satisfied by now.

Tired of playing old-school Game Boy Advance, Game Boy Color, Nintendo, and Nintendo DS games on your iPhone? We've got another retro video game system for you to add to your arsenal of emulators—Super Nintendo.
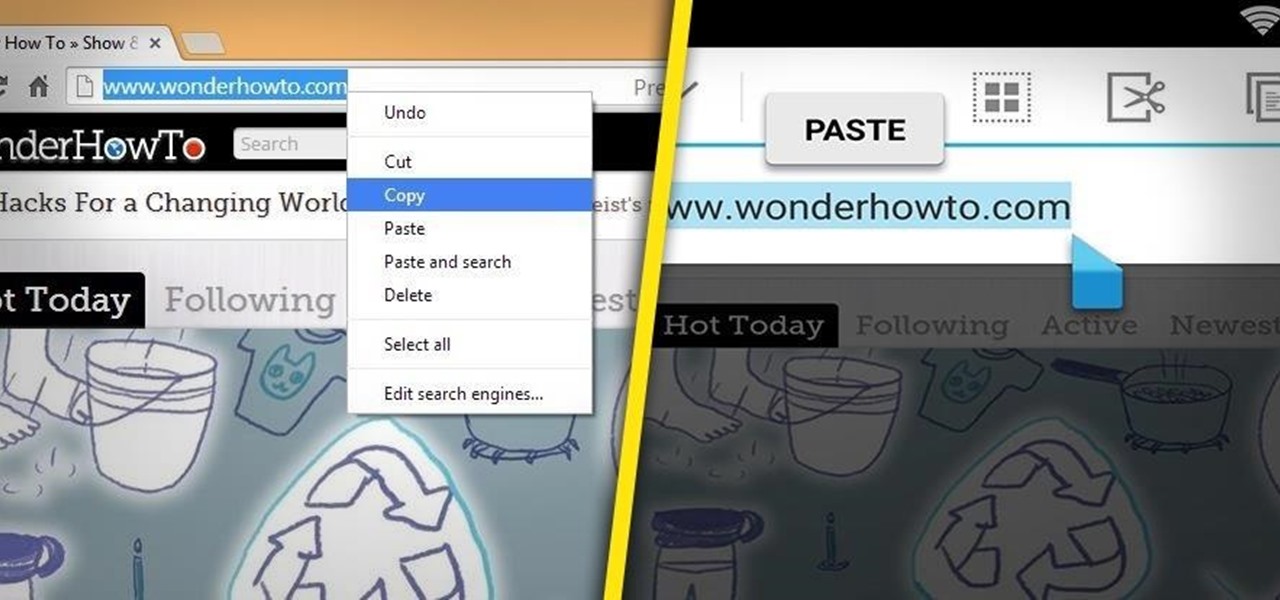
Pushbullet is one of those apps that helps separate Android from its competition. By pushing the boundaries of cross-platform data syncing and file sharing, the service truly demonstrates how flexible and robust the world's leading mobile operating system can be.

Remember when MITMing people to pentest webapps and log-ins you had to fire Ettercap,Arpspoof, SSLstrip, then look for credentials in the captured packets?

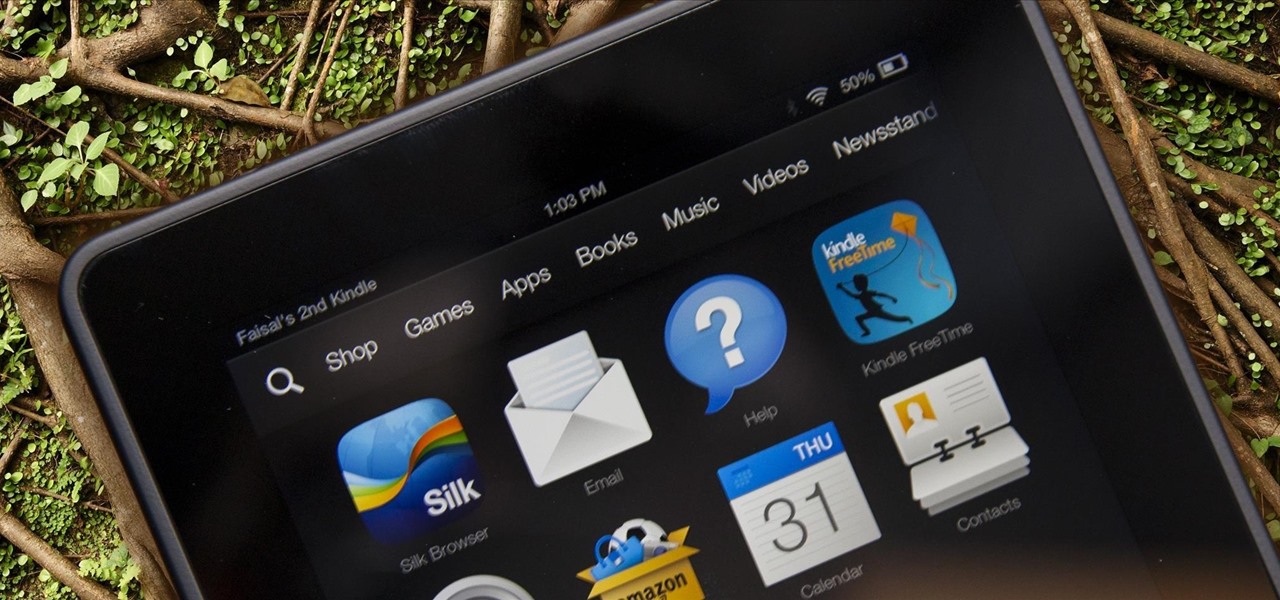
Amazon released the Kindle Fire HDX back in late-2013, and if you picked one up or received one as a gift, you've probably had a good amount of time to get to know your tablet.

Most variants of the Galaxy S5 come with the gesture-based Swype keyboard preinstalled. If you're into gesture typing, you probably already switched to this input method from the default Samsung keyboard (whose gesture service is nice, but it's no Swype).

Let's be real, browser histories are virtually useless. Trying to find something you passed up a week ago is like, pardon the cliché, finding a needle in a haystack.

Recipes are invaluable to cooks who are just starting out, but what if you want to get to the next level? Then it's time you learn how to apply simple math to food. In other words, learn how to cook using ratios, not recipes.

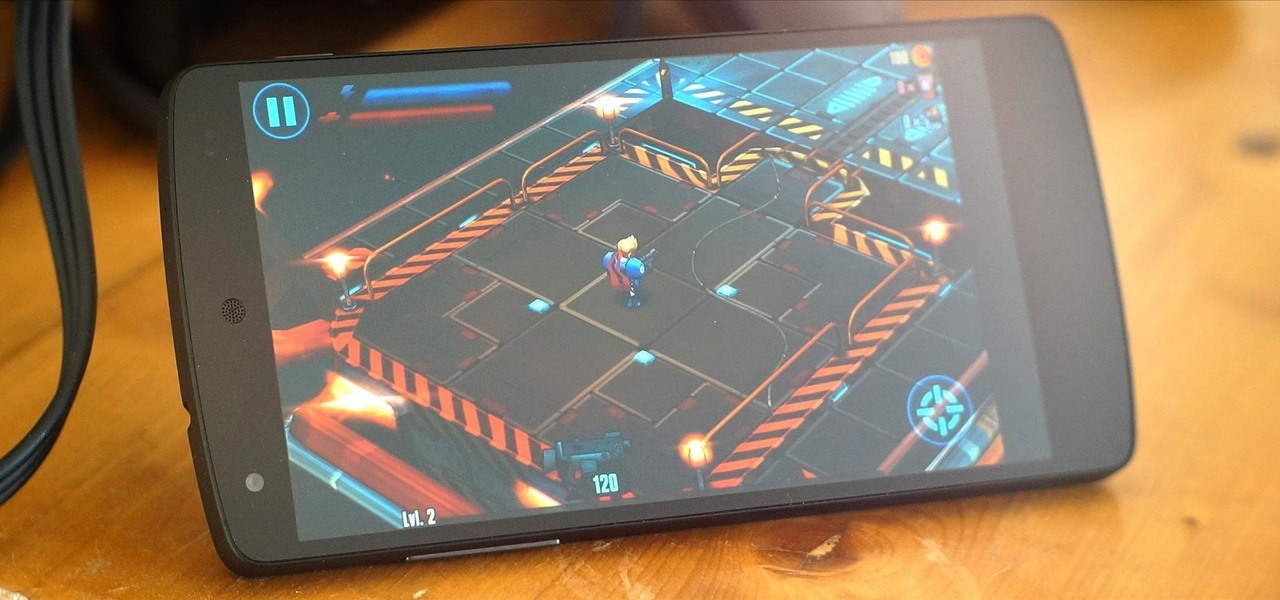
Aside from the newer HTC One M8 and Samsung Galaxy S5, the Nexus 5 still has one of the fastest processors on the market today. However, despite its superpowers, some graphically intensive games can still have a bit of lag to them during gameplay.

It started in Australia, and now seems to have made its way statewide—hackers are remotely locking iOS and Mac devices, holding them for a $100 ransom. Users awoke to the loud "lost iPhone" ringtone, with a message on their lock screen stating that "Oleg Pliss" has hacked their device, and that "they" will unlock it after being sent $100 through PayPal.

There's a lot of personal information residing on your phone, possibly even more than on your computer, so it's only a matter of time before someone tries to access it.

Welcome back, my greenhorn hackers!

Samsung's exclusive music streaming service, Milk Music, has been making waves across the web thanks to its peculiar name and ad-free stations.

The status bar is where we get all of the important need-to-know information for our phones. At a quick glance, you can see what time it is on your Samsung Galaxy S3, how much battery power you have remaining, your current signal strength, and more. But after a while, things can feel a little stale up there.

If you've been keeping up with anything Android these days, you've no doubt heard about a little dandy called Xposed Framework kicking around. Xposed, by XDA developer rovo89, is a framework for Android devices that lets you easily modify your stock or custom ROM.

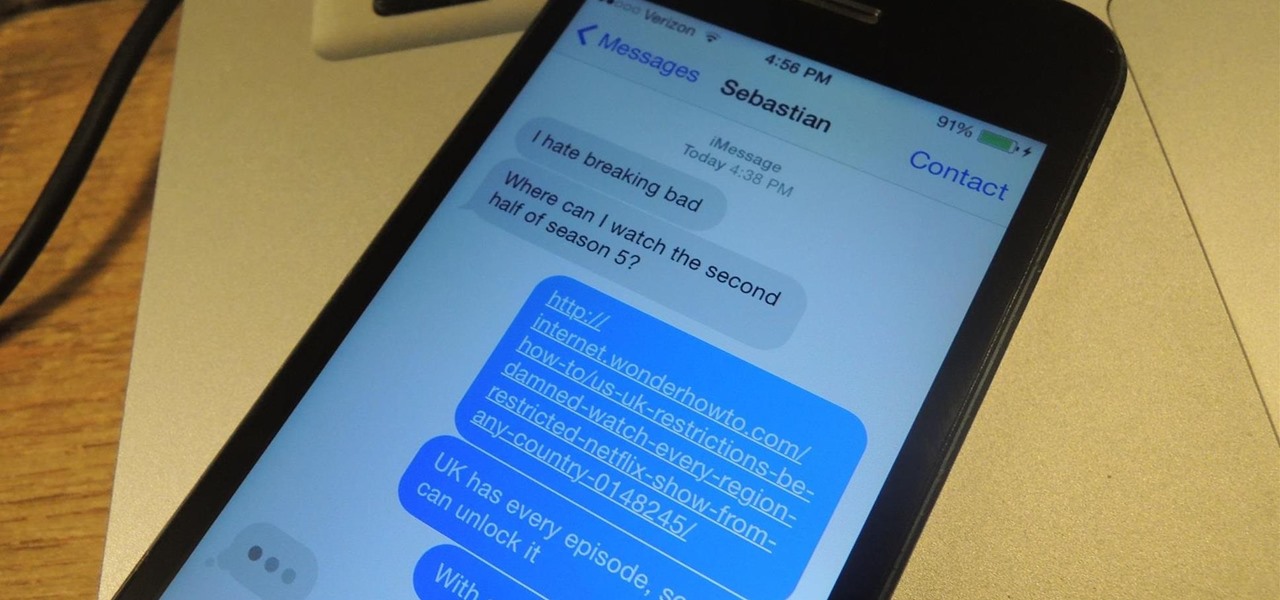
NSA aside, Apple makes it difficult for users to extract and download text messages from their iPhones onto a computer. For whatever reason (legal, devious, neurotic, etc), we've all found a time where we'd like to save backups of certain meaningful, important, or perhaps incriminating conversations (including all MMS or iMessage pictures and videos). While there are a handful of third-party applications that can help with this process, the majority of them cost money and implement certain te...

One of the best-selling video game consoles of all time is the Nintendo Entertainment System, better known by its acronym, NES. However, cartridge-based gaming consoles are a pain now when compared to the newer download-and-play alternatives.

If there's one way to get a visceral response from someone, it's bringing up the DMV. Regardless of the reason, whether it's the long lines, disgruntled employees, or just general inefficiency, I have yet to meet a single person who doesn't mind the trip. Just look at all those happy faces.

David Blaine has made millions off his magic tricks and mind-bending illusions, so why shouldn't we get in on the action, too? Well, your Samsung Galaxy S3 can do all kinds of things, but magic isn't one of them...yet.

Unlocking your Samsung Galaxy S4 so you can use a different SIM card isn't the easiest thing in the world. In the states, unlocking cell phones was actually illegal, despite the White House's disapproval, though, a recent bill has making its way to the House floor and has made it legal again.

A few weeks ago, Bluebox Security uncovered a bug that could potentially effect 99% of Android devices. Bug 8219321, dubbed the Master Key bug, works by allowing applications with modified code to pass Android's signature verification system, thereby bypassing security measures that normally wouldn't allow these apps to be installed.

Don't always believe the marketing hype. "PlayStation Certified" does not mean anything to a softModder. All this indicates is that a smartphone or tablet labeled as "PlayStation Certified" has met the guidelines and hardware requirements issued by Sony to display PlayStation Mobile (PSM) content from the PlayStation Mobile Store correctly. No Nexus 7 here.

I've never understood gift cards. Aside from being severely restricted as to where you can use them, they're also a strange gift, especially if you don't shop at that particular store. Some even have expiration dates and service fees.

Sense appears on over forty Android devices, but HTC's notorious GUI was actually designed with a completely different mobile OS in mind—Windows.

Rooting a mobile device may not be a big deal these days, but not being able to root definitely is. Even the Library of Congress, National Telecommunications and Information Administration, and White House can agree on that.

How to find a stud in the wall. How would you like to be able to find a stud in a plaster wall / drywall wall, easily and every time without an expensive stud finder? Let's look at how to find a wall stud using three conventional methods then l'll explain my foolproof method of how to find a stud in the wall without a stud finder.

Cinema is a matter of what's in the frame and what's out, according to director Martin Scorsese, who asserted that when describing his life's work. Getting the perfect shot can turn an otherwise ordinary scene into something great, both on and off screen.

In the Harry Potter world, there was a character by the name of Beedle the Bard, who told a story about witnessing the three Peverell brothers building a bridge out of magic and successfully crossing a very dangerous river that had claimed many lives.

The number of passwords I have for different websites and emails is easily in the triple digits. And if I had to actually remember all of those individual passwords, I would be locked out of accounts on a daily basis.

The beauty of free apps is that, well, they're free. But as we all know, there is no such thing as a free lunch. Sometimes these "free" applications are only feature-limited mini versions, or they're so littered with ads that opting to pay for it is the only way to actually enjoy it.

There is nothing more irritating than having a nice jam session interrupted by an ad selling B vitamins, and that's exactly what Spotify does to you if you don't pay up.

Every year, Black Friday gets a little more insane. People get up at ungodly hours, wait in lines forever, and get into some of the most ridiculous fights you've ever seen. All in the name of saving some cash. Everyone loves saving money, but without a game plan, you could end up missing all the good deals and going home with nothing. Luckily, the Internet is here to take some of the stress out of holiday shopping. With these sites and apps, you can find out about all the best deals before yo...

There's really nothing safe about transmitting sensitive information electronically, but even if it gets there safely without being seen by prying eyes, there's no guarantee what happens to it once it reaches its destination. And let's face it, there are some things that you just don't want floating out there forever. So what can you do? Whether you want to send an email, a text, or a link, there are ways to send messages that self-destruct so that once they're read, they immediately vanish. ...

All of my hacks up to this point have been operating system hacks. In other words, we have exploited a vulnerability usually in an operating system service (SMB, RPC, etc.) that all allow us to install a command shell or other code in the target system.

Getting two sticky-pistons to pull eachother, a piston-train, isn't anything new but the pistons and their timing in 1.3 are and there has been alot of QQ-ing on the Minecraft-forums about how bad they are and that Jeb should bring back the old pistons we all know. I, for one, not only welcome out new 1.3-pistons but have also made a small mini-game out of them. A two-player tug-o-war. The players stand on the diamond or emerald area and press a button to make the piston-train take one step t...

Okay, you can't really become the king of the world by stacking three pistons. For that, you have to stack four pistons.

A flaw in WPS, or WiFi Protected Setup, known about for over a year by TNS, was finally exploited with proof of concept code. Both TNS, the discoverers of the exploit and Stefan at .braindump have created their respective "reaver" and "wpscrack" programs to exploit the WPS vulnerability. From this exploit, the WPA password can be recovered almost instantly in plain-text once the attack on the access point WPS is initiated, which normally takes 2-10 hours (depending on which program you use).