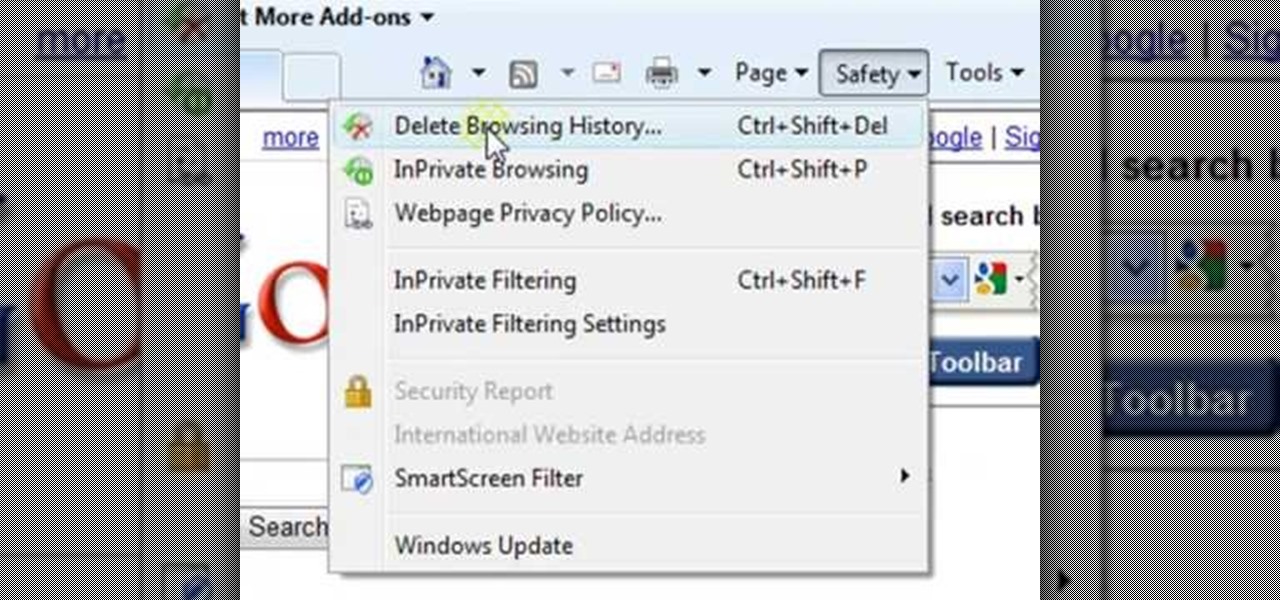
ClearTechInfo presents a how-to video on clearing Internet Explorer 8's browser history. Computer users are reminded that the only silly question is the question not asked. In the video, the viewer is shown that by clicking the button marked "Safety" in Internet Explorer 8 the "delete browser history" option is revealed. As long as each option is clicked, the history for the computer user is deleted. The browser history, cookies, cache, and passwords can all be deleted with the click of the b...
In this video the instructor shows how to remove vocals in a audio using the Adobe Audition 3 software. He says that one cannot remove vocals 100 percent but just reduce them to a minimum compared to the rest of the sound. He shows you a sample track first which contains vocals.

In this video, Dr.Travis Fox explains how you can tell if your partner is cheating through eye cues. Many people will search and hire even private investigators to find out the truth. Dr. Fox in this video says to "save your money." He tells you about certain indicators that are used to read if they are lying. For example, looking to the left or looking down might indicate that they are lying to you. He does say that it is not 100% always correct but works well in a lot of cases.

In this tutorial by Shooting Eggs, you'll learn how to create your own "ocean in a bottle". The supplies are very simple and cheap, probably stuff you've already got around the house. But the finished effect is pretty impressive.

In this AeroCast episode, Anthony Bottini discusses the Power Off Stall maneuver as performed in the Piper Warrior (PA-28-161), referencing the procedures and standards outlined in the UND Aerospace Warrior Standardization Manual. All performance tolerances are based on the performance standards set forth by the FAA Private Pilot Practical Test Standards. Power Off Stall practice is vital in increasing a pilot’s proficiency in regards to stall recognition and stall recovery techniques during ...

The ability to browse the web in coffee shops, libraries, airports, and practically anywhere else you can imagine is more than convenient, but convenience has risks. Using public Wi-Fi allows others to spy on you easily. Even your own internet service provider can see every website you've ever visited. Don't fall into the trap of protecting your identity, data, and devices after it's too late.

Smartphones have so much sensitive information attached to them. If you share your home with others, then you know the pains of trying to keep anything private. Photos are surely among the things you'd prefer to keep to yourself, so OnePlus has you covered.

After drawing attention from nostalgic Gen Xers for its Motorola Razr reboot with a foldable screen, Lenovo has a new augmented reality smartglasses concept that the company hopes will also turn some heads.

Commenting on Facebook pictures is a commonality. But you may not want to share your private and personal pictures on Facebook. Maybe you just want a select few to comment on your photos. Fear no more, you can send your pics and get private comments using Google Photos.

Thanks to its encrypted messaging, WhatsApp can be a platform for secure communication with friends and family. One drawback, however, is that the app would let anyone add you to a group chat, regardless of if you approved it or not. This lack of control over your own account is over, as WhatsApp now lets you decide who can add you to a group chat.

It's that time of year again. No, not Thanksgiving. Black Friday. There are a lot deals available this holiday weekend, many of which include flagship Android devices. Whether you are thinking of buying a phone for yourself or looking for a gift for someone else, you can find a little savings to shop smart during the holidays.

As penetration testers, we sometimes need to securely store customer data for prolonged periods. Bruteforce-resistant, vault-like containers can be created with just a few commands to protect ourselves from physical attacks and unintended data disclosures.

Two characters from the popular sci-fi animated comedy Rick and Morty have already made their way into augmented reality courtesy of ARKit experiments. Now, it's possible to become one of them on the iPhone X.

If you've received a spam message in Signal Private Messenger, you know that anyone can contact you as long as they have your linked phone number. But when it comes to the people you're actually trying to have a private conversation with, how do you know it's really them?

The photo-centric Instagram app is a great way to share "evergreen" pictures and videos when compared to Snapchat and Facebook's new Messenger Day feature. But like all social media, keeping the account secure is an essential aspect, as it restricts unwanted viewers from seeing your content and can prevent unauthorized users from accessing your account. Instagram has several methods for locking down the account including a new two-factor authentication (2FA) mechanism.

Hello people again, I wrote my last post about crypto about 10 months ago, now I will introduce something not fresh for the science, but fresh for the people who wants to learn. In my http://null-byte.wonderhowto.com/forum/cryptography-0161538/ post of crypto concepts, there is just basics, today we will see something that targets wide concepts like Symmetric crypto, Public Key Cryptography, Hashing, Keys etc...

This tutorial is for those who've purchased an account with Private Internet Access to hide your VPN and would like to set it up in Kali. Please note, you can chose to run your PIA service from your Windows computer without configuring it in linux as long as you'll be using a NAT connection. Using a NAT connection will allow your Windows machine and Kali Virtual Machine to use the same IP address, hence if your IP is hidden on one, it will be hidden on the other.

Welcome back, my rookie hackers! "How can I travel and communicate over the Internet without being tracked or spied on by anyone?" It's a question many Null Byteans have asked me, so I have decided to write a comprehensive article addressing this issue.

Learn insider tips for managing a private health club and the best way to manage your health club, gym, spa, or fitness center with expert health club management advice in this free online management video series.

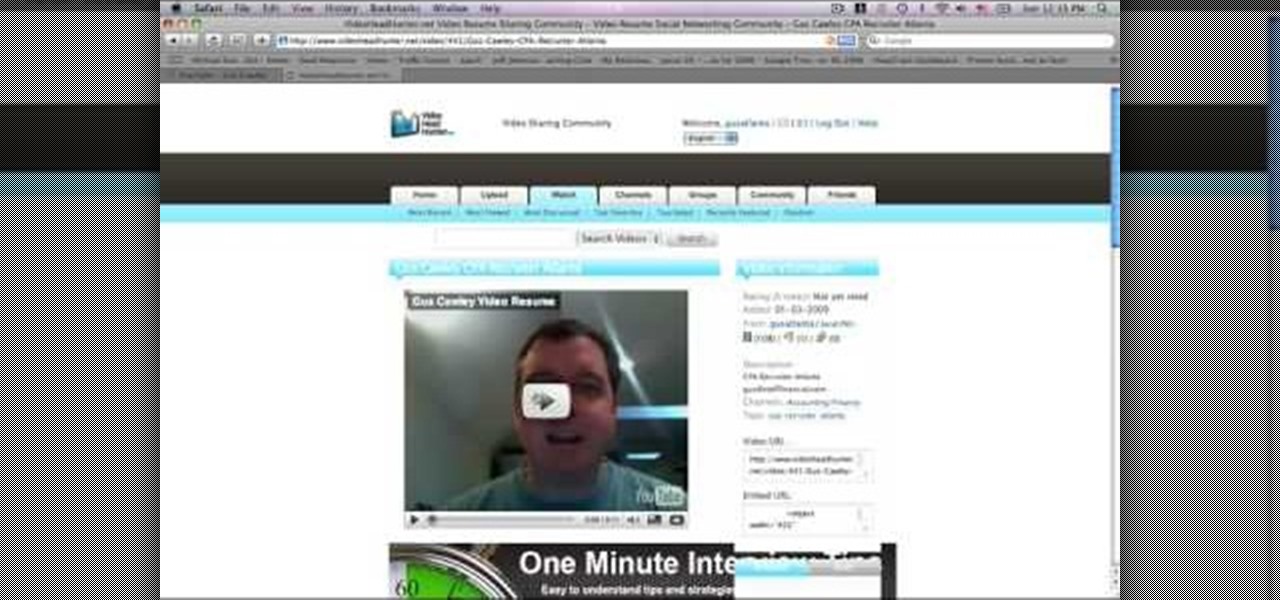
Gus Cawley shares the ways to make a video resume with the help of free online tools. 1. Log in to YouTube. 2. Click upload and select quick capture. 3. Click the record button (be sure to have good lighting, good background and a high quality microphone for a more effective recording) 4. State the information of your resume. 5. Click the red square button to stop the recording then choose publish. 6. Edit the information of the video. In the description, put your contact details and informat...

In a world increasingly regulated by computers, bugs are like real-life cheat codes. They give you the power to break the rules and do good or bad without ever leaving your seat. And government agencies around the world are discovering and stockpiling unreported bugs as cyberweapons to use against anybody they see fit.

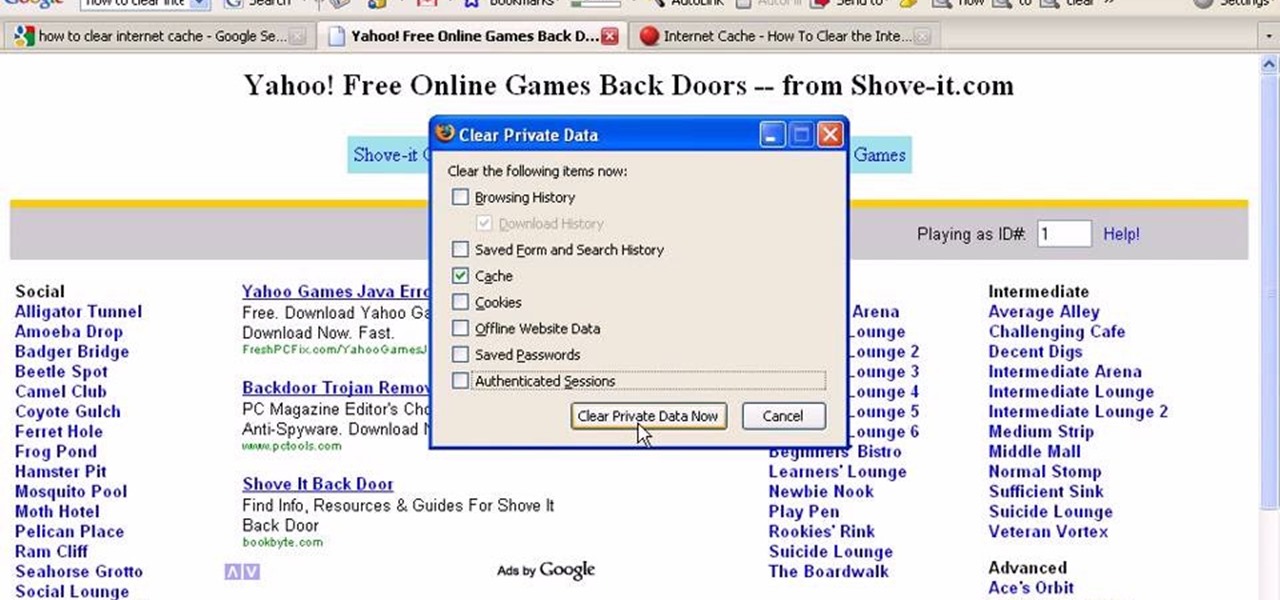
In this tutorial, we learn how to clear your internet cache using Firefox. This only takes a few minutes and can help your browser run much more quickly. First, you will need to log onto Firefox on your computer. After this, you will need to go to the tools menu and then click on 'clear private data'. A new box will pop up, when it does you will need to check the box next to 'cache'. Once you do this, click on the bottom button and then it will load and clear it out. It's just as simple as th...

In this video tutorial, viewers learn how to clear their cookies in Mozilla Firefox. Begin by opening the web browser. Then click on Tools from the top menu and select Options. In the Options window, click on the Content tab and deselect "Block pop-up windows". Click OK. Now click on Tools and go to Options once again. Click on the Privacy tab and click on Clear Now under Private Data. Make sure that Cookies and Cache are checked and click OK when finished. This video will benefit those viewe...

Learn how to make biodiesel. Maurice Vanegas is an executive for a private charter company. The biodiesel made is used in a fleet of transit buses, executive buses, and diesel trucks. The biodiesel comes from virgin soybean oil and used vegetable oil. Since July 2006, the company has produced in excess of 20,000 gallons.

This 4 part video series is a gift from me to all the other singers out there who have shown me such great love and support. It contains a full vocal warmup that will improve tone, expand range, and increase control. This is pretty much the kind of warmup that I might do with a private client, but it's for you guys - free of charge.

It is well documented that what you say and do online is tracked. Yes, private organizations do their best to protect your data from hackers, but those protections don't extend to themselves, advertisers, and law enforcement.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

In Safari for iPhone, as far back as iOS 7, you can request the full desktop version of websites. The process was streamlined starting in iOS 9, but the process remains relatively hidden and easily missed. Now, iOS 13 shines a light on it, as well as adds functionality to set the desktop view for individual websites indefinitely.

In order to increase the security and harden the integrity of an email account and its content, you'll want to use PGP on your Windows, macOS, or Linux computer. This is usually the first thing security analysts do to protect communications with encryption, and everyone else should consider it too, especially since there's an easy way to incorporate PGP that anyone can follow.

It turns out that the government of Saudi Arabia has managed to do something last month's Game Developers Conference couldn't — give us a few new glimpses of the Magic Leap One being worn by someone other than Shaq.

Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion unbeknownst to the participants. However, we don't need to communicate insecurely.

Telegram routinely boasts about its secure messaging for truly private conversations between two parties. However, default cloud chats in Telegram are only encrypted between client and server, not client and client, which means you have to be a little proactive in making sure your private conversations on Telegram are really private.

It seems like there's a cyber security scare every day. Consumers are growing increasingly concerned about the safety of their accounts, and they have reason to be. Hackers will maliciously attack you anywhere — and we mean anywhere — they can to get your private information.

Last week, the U.S. Justice Department issued criminal indictments against seven Iranian hackers. These hackers, working for private companies in Iran, are accused of orchestrating DDoS attacks against U.S. financial institutions from 2011-2013 as well as intruding into the control panel of a small dam in Rye, New York. It is thought that these attacks were a response to the U.S. tightening financial restrictions on Iran during those years and the NSA-based Stuxnet attack on their uranium enr...

After lots of anticipation and leaks, the LG G3 has been unveiled. Sporting a gorgeous 5.5" Quad HD display, the first of its class for smartphones, this flagship device is ready to put some scare into Samsung and HTC. It's currently available for purchase from AT&T and Sprint, and for preorder at T-Mobile and Verizon Wireless.

No matter how careful or decent you are, there will always be pictures or videos that you want to keep private. They say a picture is worth a thousand words, but if someone were to go through my photo gallery, only one word would be coming out of my mouth—"%@&#!!"

I want to talk about growing up with burden of acne. I frequently receive comments and private messages about kids being bullied for having acne, this is not right. Everybody is beautiful in their own way and you should never let the haters put you down! Love yourself =)

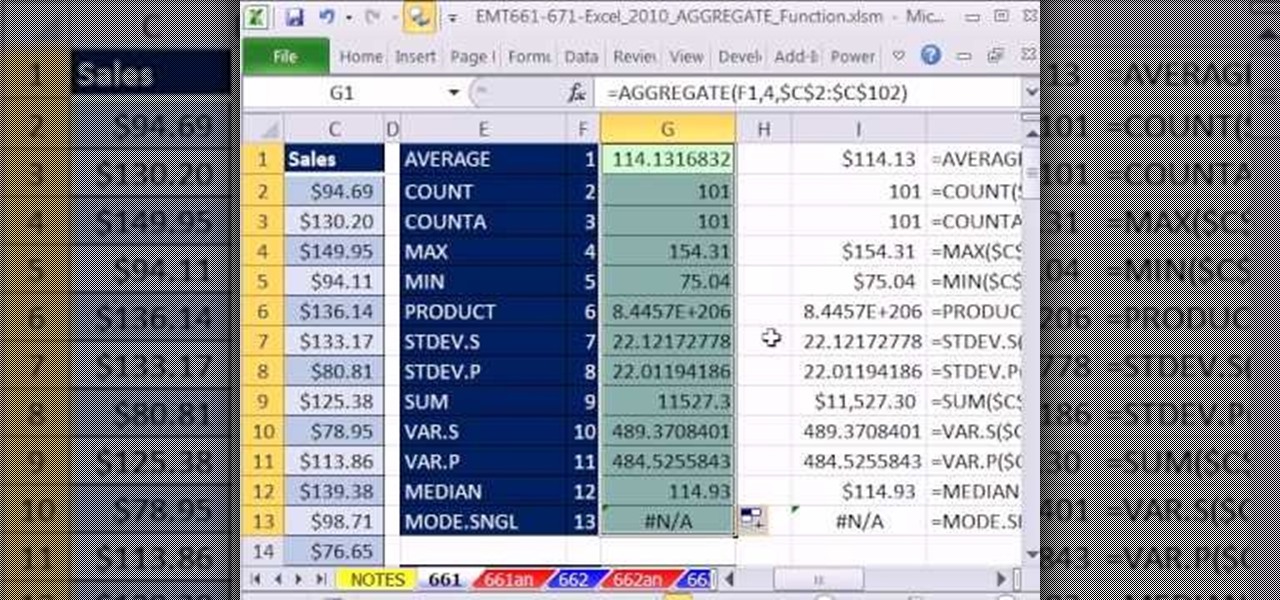
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 664th installment in their series of digital spreadsheet magic tricks, you'll learn how about how the new Excel 2010 AGGREGATE function that can calculate these 19 different functions depending on what number you put into the 1st argument of the AGGREGATE function. This is an improvement over the SUBTOTAL function wh...

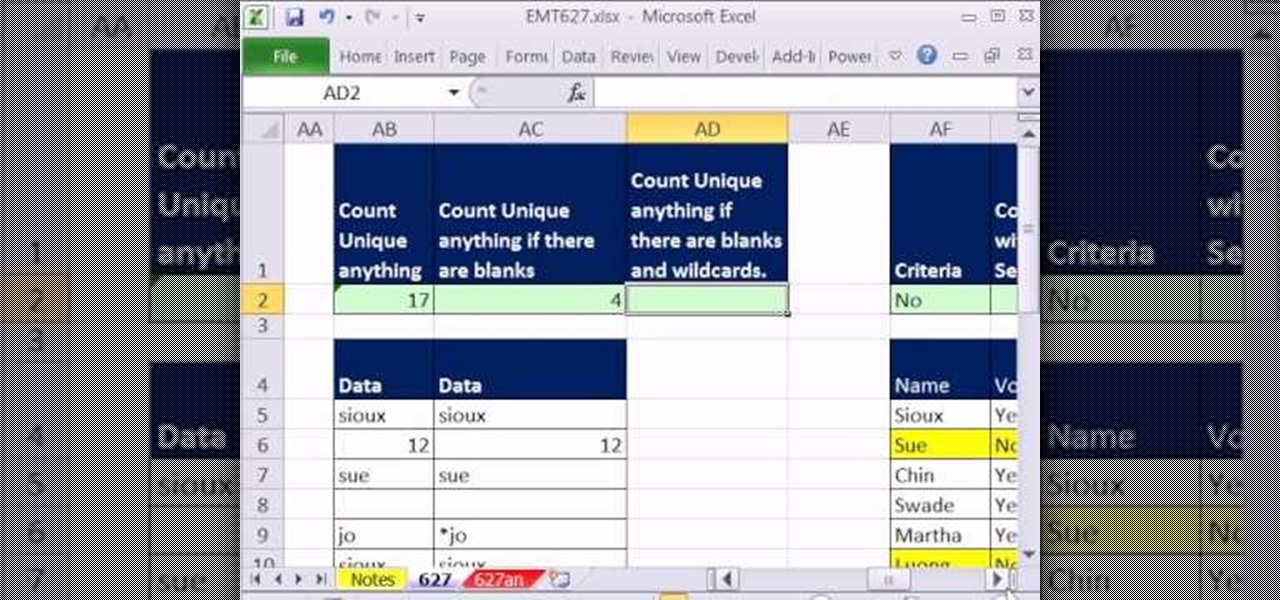
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun and Mr. Excel, the 627th installment in their joint series of digital spreadsheet magic tricks, you'll learn how to create, edit and otherwise work with FREQUENCY array functions.

Want a free meal at McDonald's restaurant? Forget those money-saving (supposedly) weekly coupons, that's nothing compared to an actual free meal. Coupons won't get you that. But this method of free food, perfect for the freegan or the poor (or maybe just the rude). This would technically be qualified as a prank or con, but hey, you got to eat, right?