A burner number isn't just for criminals and cheating spouses. In this digital world, with many of our interactions being conducted online, a throwaway phone number acts as a buffer — it lets you enjoy the web without having to give out your personal information, such as real name or phone number.

It doesn't matter how cool or groundbreaking a particular technology is, if it doesn't offer the promise of big returns on investments, you'll have trouble drawing interest from both Silicon Valley and Wall Street. That's why we're increasingly seeing existing augmented reality players doing everything they can to focus in on revenue generation, which was the message coming from Snap Inc. this week.

In case you missed it, you don't have to chat one-on-one anymore in Snapchat. The company added group chats back in 2016, and they are increasingly gaining new features such as video and audio chats, so communicating Snapchat-style with all your friends at once is better than it's ever been.

If you've ever connected your iPhone to a computer before, you know iOS prompts you to "Trust" the computer and enter your passcode to confirm. According to Apple, trusted computers can "sync with your iOS device, create backups, and access your device's photos, videos, contacts, and other content." That's a lot of permissions to hand off, especially if the computer's not your main laptop or desktop.

While some of our group chats should probably remain private and closed off, others will only get better with more people. Whether you're organizing an event and need a headcount or you want to share a funny YouTube video with a large crowd, you can add all the friends you wish to on Facebook Messenger by sending them a unique link.

One of the biggest improvements with the Galaxy S9 and S9+ is the redesigned camera, with the latter scoring an impressive 99 overall on DxOMark. But with an abundance of features and enhancements, tweaking the camera's settings for optimal performance can be a little confusing.

Magic Leap's recent flurry of patent applications prompted us to look around for any trademark movements from the company, and it turns out that the Florida-based company has been quite busy.

BlackBerry has formally unveiled its latest flagship, the KEY2, during an exclusive event in New York. The Android-powered KEY2 retains its distinctive BlackBerry aesthetics with a physical QWERTY keyboard. Here's all the juicy details regarding Blackberry's followup to the venerable KEYone.

While the Twitch app for iOS came out way back in 2011, livestreaming iPhone games was a rarity until Apple recently updated its ReplayKit in iOS 11. However, Twitch hasn't jumped on the bandwagon yet, but that doesn't mean you can't livestream your iPhone games to Twitch right now.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

While it's easy enough to ask websites not to track your browsing activity in Safari, they do not have to honor your request. Plus, some of the third-party content providers that websites use can actually invasively track you across other websites. Thankfully, iOS 11 includes a way to minimize companies from tracking you across the web on your iPhone.

ARKit is a marketer's dream. By providing tools for creating augmented reality experiences on mobile devices, AR apps can now be deployed easily alongside just about any campaign. As expected, we now have ARKit apps pushing wares ranging from automobiles to tequila.

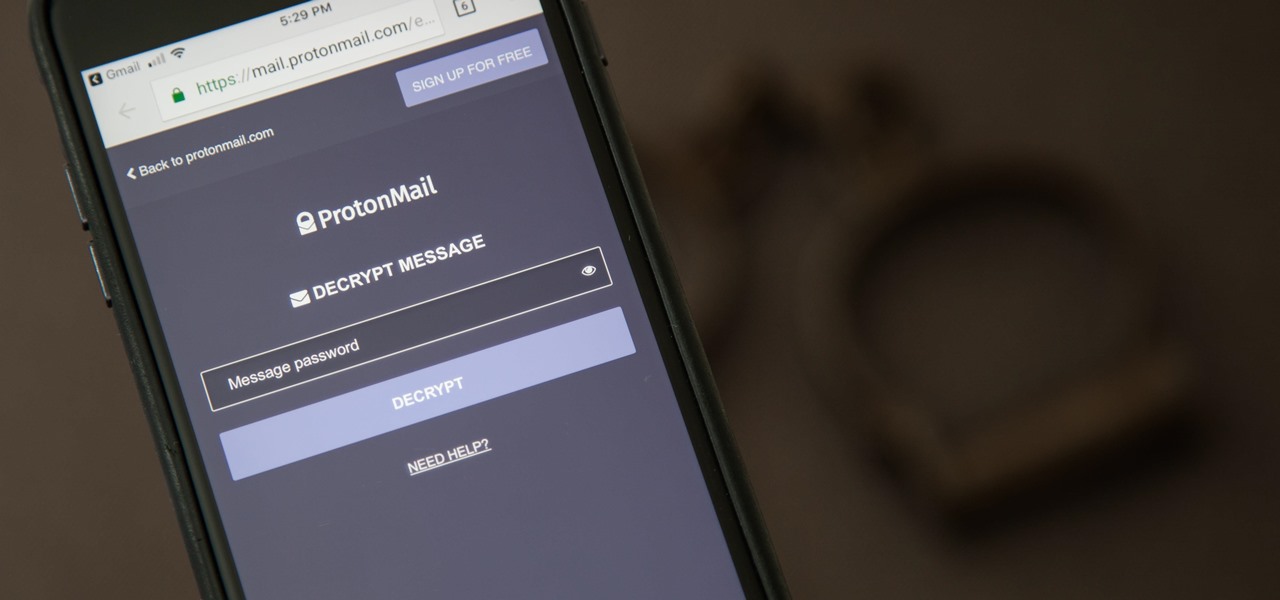
It can be hard to get all of your friends, family, coworkers, and acquaintances to jump on board with the more-secure email system ProtonMail, but that doesn't mean you can't still send them encrypted emails. Best of all, they won't even have to install any other apps or extensions to read or reply to the messages.

For as long as 14,000 years, the First Nations people of the Heitsuk Nation have made their home along the Central Coast of the Canadian province of British Columbia. Among the territory's inlets, islands, rivers, and valleys lie a clay deposit on the north side of Kisameet Bay, near King Island. For as long as most can remember, the tribe has used the clay as medicine. Now science says microbes that live in that clay may have important antibacterial properties.

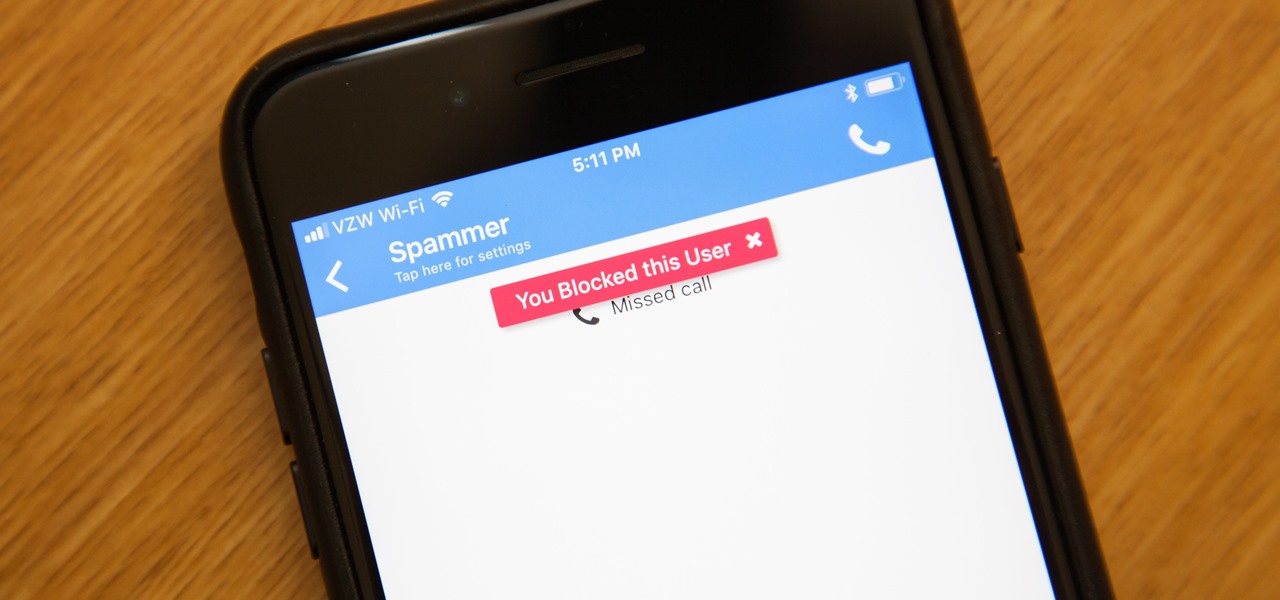
While it's a more secure platform for messages and calls, Signal's job isn't to prevent unknown users from contacting you, so you run into the same issues you would with a regular phone number. People you know that you don't want to talk to may try to strike up a conversation and you'll still get spam messages. Luckily, it's easy to block these suckers.

Wherever there are people, the party is sure to follow. Well, a party of microbes, at least. That is what scientists at NASA's Jet Propulsion Laboratory have found after a 30-day microbial observation of the inflatable lunar/Mars analog habitat (IMAH).

So, Nintendo's never really been good at the whole online thing. Most of the time, we forgive them, because they are masters at creating games meant for solo play or local multiplayer. Sometimes, though, that doesn't fly. Take a game like Splatoon, for instance. Although it redefines the genre, it is still, at its core, a shooter. Shooters are meant to be played online, with your friends, yelling at each other over voice chat.

For a company more associated with debugging computer programs, Google's parent company, Alphabet, is making a name for itself by taking on the real thing — mosquitoes.

Bitmojis are not only a good way to personalize your Snapchat account, but also a really fun Snap addition to play around with. A bitmoji is basically like your little avatar, letting you design your mini-self whichever way that you desire.

What makes YouTube such a special platform is that anyone and everyone can upload their own content. Big players upload their videos to the same site that the little guy does.

Brace yourselves, because Siri has a trick up its sleeve that iPhone users have wanted for some time. Yep, that's right, I'm talking about the ability to use Siri without having to talk out loud for the whole world to hear. It's great for privacy, Siri-ing on the down-low when you're not supposed to, or ... you know ... if you have a speech disorder.

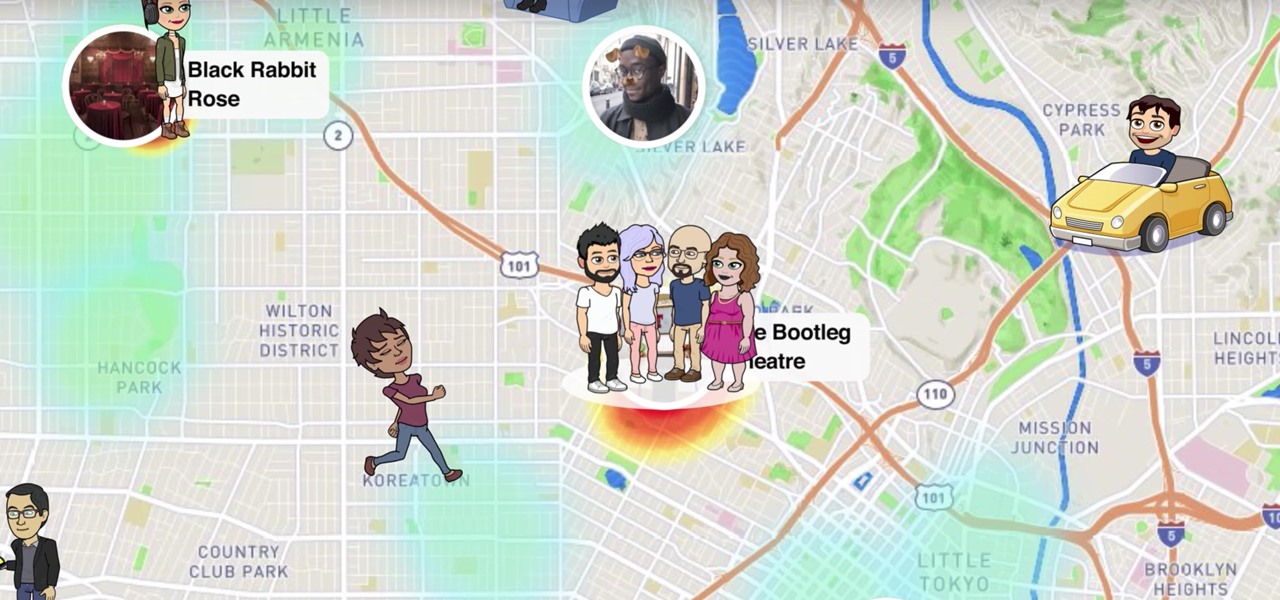
Snapchat recently updated their Android and iPhone apps with a new feature called Snap Map which lets you share your current location with other Snapchatters, as well as see their current locations. It may sound like an interesting new feature, but sharing your exact location with all of your Snapchat followers is dangerous, to say the least. Luckily, it's easy to turn this feature off.

There are a lot of exciting improvements in store for Siri in iOS 11. Apple showed off some of the highlights at WWDC, but there are five changes in particular that you don't want to miss.

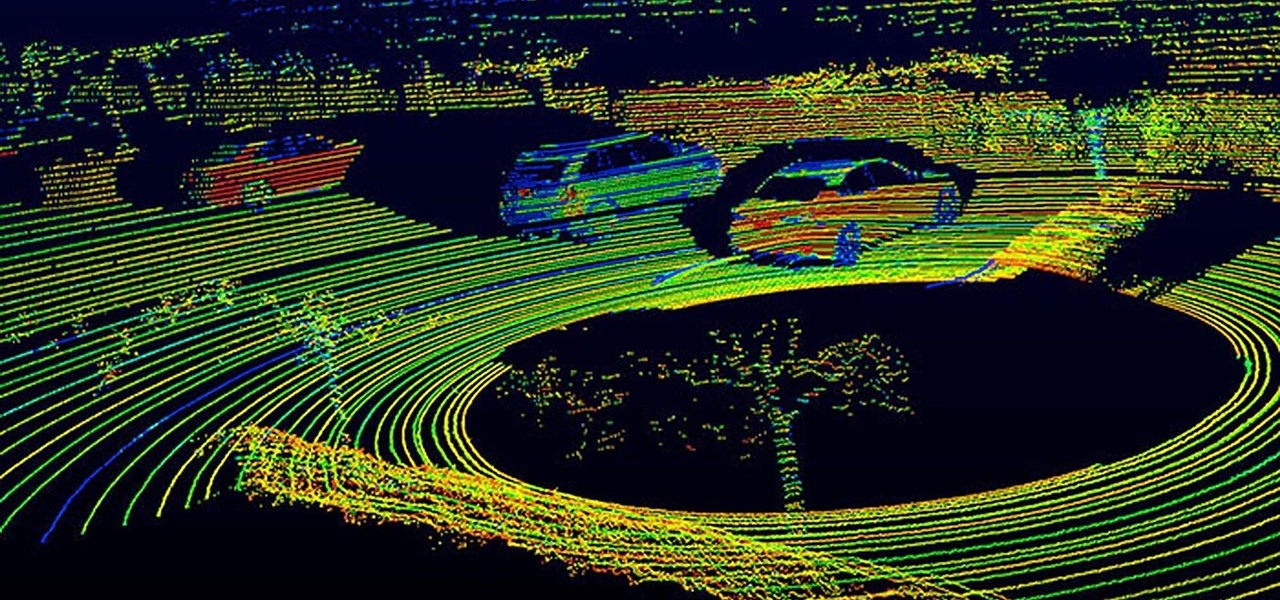
Solid-state LiDAR is cheap, robust, and compact in size — this is why the device is seen as the LiDAR of choice for future high-volume production of level 3 and level 4 cars.

As much as you try to safeguard your personal information, you may have made a small mistake by giving your phone number to the wrong entity, and now you're being bombarded with dozens of spam calls every day. To help parse your call log and reject the proper numbers without answering or trudging through voicemail, a good reverse phone lookup app is needed.

New statements from Apple make it clear that they do not believe a hacker, or group of hackers, breached any of their systems. This comes after a recent report from Motherboard that a hacker gang called the "Turkish Crime Family" is threatening to remotely wipe up to 559 million iPhones by April 7.

Somewhere around 600–800 million people in the world are infected with whipworm (Trichuris trichiura), an infection they got from ingesting soil or water contaminated with feces of infected animals or people containing the parasite's eggs.

Disengagement report numbers for self-driving car testing in 2016 on public roads in California were just released, and the biggest point we can make about them is that Waymo is very far ahead of their competitors in almost every metric.

You might feel the bite, you might not, but an infected mosquito has injected you with a parasite named Plasmodium falciparum, a single-cell protozoa that quickly takes up residence in your body.

Alphabet's moonshot factory, X (formerly "Google X"), is a secretive place, but it seems that when they are close to graduating a project, then they need to staff it up quickly. Watching for these job ads is one easy way to know they're close to budding off a baby.

When you do an internet search, you'll see ads that are relevant to your query mixed in with the rest of your results. Nothing surprising there—it's how the internet is funded. But then, when you click one of the search results, you'll also see ads that are related to your initial search. Now that's a bit creepy, because it demonstrates that one webpage knows what you typed into a different webpage.

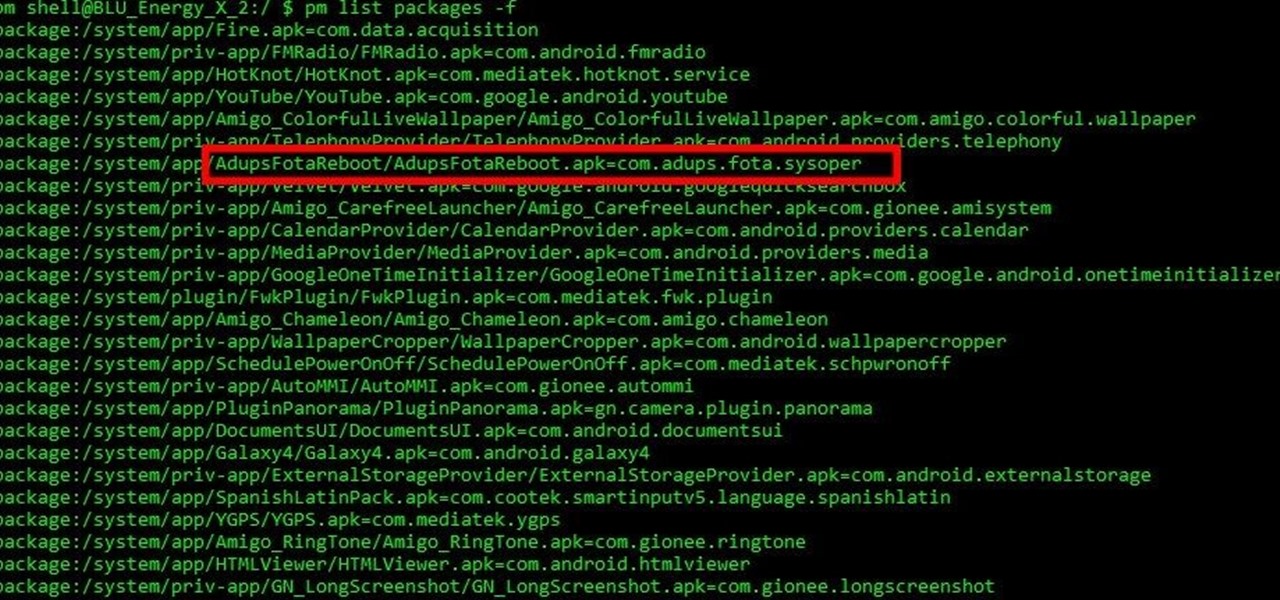
Mobile security researchers at Kryptowire recently uncovered spyware preinstalled on hundreds of thousands of Android smartphones by FOTA provider Adups which was gathering personally identifiable information (PII) such as call logs, app usage data, and even the full contents of text messages and sending these to a third-party server—all without the users' knowledge.

In this first part of my series on getting started with Windows Holographic, we are going to cover everything you need to get set up for developing HoloLens apps. There are many pieces coming together to make one single application, but once you get used to them all, you won't even notice. Now there are different approaches you can take to make applications for HoloLens, but this way is simply the fastest.

We haven't had a working jailbreak method since October of last year, and that only worked for about a month until iOS 9.2 came out and shut down the loophole it was using. So all of those cool Cydia tweaks have been out of the question for quite a while now, unless you downgraded your firmware to keep jailbreak compatibility.

Starting with the Priv, BlackBerry's become an Android manufacturer. This move gives BlackBerry's phones access to Google's sizable app store, but it also presents several hurdles to keeping the security brand they've built intact.

Counter-Strike is one of the most popular first-person shooters of all time, and deservedly so. What originally started out as a third-party Half-Life mod garnered such a cult following that Valve had to hire the developers and purchase the intellectual property to make it an official standalone release.

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

As many of you know, I have been running a couple of series here on Null Byte about digital forensics called Digital Forensics for the Aspiring Hacker and Digital Forensics Using Kali. Although many readers have seemed to enjoy these series, just as many seem to be pondering, "Why should I study digital forensics?"

Last month, it was revealed that Juniper Networks' routers/firewalls were hacked. It was reported that a backdoor was implanted in the operating system of their routers/firewalls and that attackers could listen in on all encrypted communication. There are now fears that all confidential communications by U.S. government agencies and officials could have been compromised over the last three years.