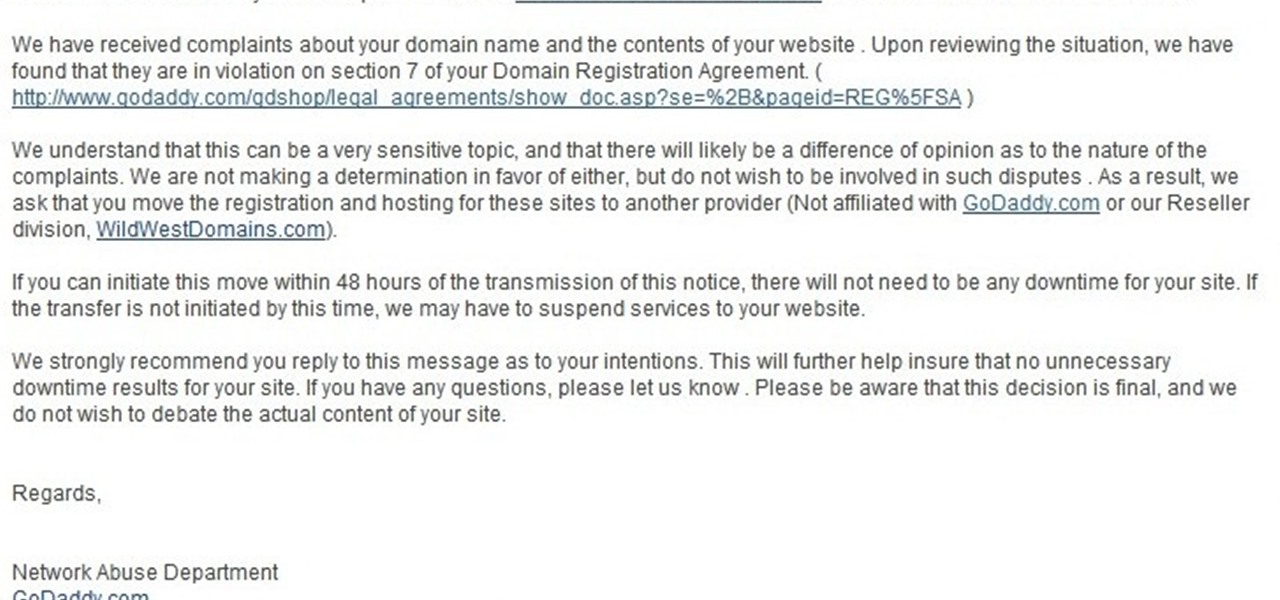
» ‘Obama Truth Team’ Orders GoDaddy To Shut Down Website. A political website that contained stinging criticism of the Obama administration and its handling of the Fast and Furious scandal was ordered to be shut down by the Obama campaign’s ‘Truth Team’. » Former Bush Attorney General Alberto Gonzales Confronted On Torture.

Most DIY freaks do-it-themselves because they love it. Because they're curious, creative, and like to take the long road (or figure out an ingenious short cut).

Hey wizards! I've compiled a list of all the Sun, Moon and Star spells you can learn, who to learn it from and what level is required to use it. Sorry, no pics. Scroll down to the bottom for links.Solar Spell List Enchantments

Last week's social engineering phone calls were a blast. We made some friends, and even some enemies. We scored cheap food for some buddies, made some phone bills disappear, and even got a few people some free pizzas. So overall, it was a very successful night. In light of its success, I figured we'd all do another one!

This is the first official announcement for a new weekly activity on Null Byte for the community to participate in. Starting next week, depending on how much traffic we get doing it, we are going to start doing live social engineering calls via Skype. I've made a list below so that you can get a feel for some of things we'll try to accomplish in these calls.

Null Byte is looking for moderators. More threats to computers exist every day. Not only do we have computer viruses and malware, but we have rootkits and other nasty pieces of code that can log your keyboard strokes or even add your computer to a botnet to attack other websites. Your computer can be infected even if you have anti-virus software installed. I can't stress enough how easy it is for a hacker to write a piece of code that gets around every piece of anti-virus software.

Here at Null Byte, we've spoken a lot about securing and anonymizing traffic. This is a big deal. With all of today's business taking place electronically via computers, we need to be secure when on-the-go. A lot of businesses don't even train their employees to secure their computers to protect from various threats. Here are a few things that should always happen when doing business on computers:

Generally, summer is a slow time for video games, but not when it comes to Xbox Live Arcade where it's harvest season! In the last month, there have been at least four great games released on XBLA, with Bastion getting the lion's share of the attention. But the remaining three are pretty awesome, as well, and should help you while away the time spent indoors away from the brain frying heat sweeping the U.S.

Join the Pilot program and learn how to fly! But you're not going to be flying airplanes in this Pilot program, you'll be trying your hands at Google's first laptop computer.

People sometimes ask me about the IT industry here in the states. These folks are usually either trying to get into a certain field, or looking to switch or move into another one. Right now, you may currently be a Computer Science major that will be graduating shortly and are interested in the current state of IT security.

We had a blast during last week's social engineering calls. One of our attending social engineers was so clever that she convinced several people on Craigslist that lost items were hers, even if it seemed she couldn't be trusted. But females are better social engineers, naturally. Some say that females have a special knack for manipulating men, but I think that's preposterous. I can't see why that would be true in a million years (note my sarcasm).

Ah, turducken. The fondest of all portmanteau words and the tastiest of all Thanksgiving day meals. Turducken is a turkey stuffed with a duck stuffed with a chicken—three glorious poultry meats molded into one marvelous, boneless hunk of flesh that any sane carnivore wouldn't dare resist. It's slapped together with pork sausage stuffing, sometimes even three different kinds, and caked with Cajun seasonings.

Facebook has been "improving" their interface in several different ways in attempt to combat the threat of Google+. One big change is the introduction of a news ticker in the top right corner that constantly feeds updates from friends and organizations you are connected with on Facebook. Not only do some people find the ticker annoying due to the constant stream of text flowing across it, but many felt unnerved by the fact that every “Like” or comment on a profile could instantly be seen acro...

World of Warcraft has been on top of the world for seven years. No other MMO has come close to challenging its dominance of the genre, and it has generated billions of dollars for Blizzard. They have spent a lot of money adding more and more content, to the extent where the full game with all the expansion packs takes up 65 GB of hard drive space. It is a beautiful game; well balanced, and a milestone in the history of the medium.

Do you ever wonder if the files you're trashing on your Mac are actually trash? Let's say there are 80 million computer owners running Mac OS. If each user trashes at least 10 files each day, that's 800 million deleted files that cease to exist every 24 hours. If that doesn't sound like a lot to you, a month would equal 24 billion junked files, a year—nearly 1 trillion.

Dactyloscopy isn’t going anywhere. Forensic science has much relied on fingerprinting as a means of identification, largely because of the massive amount of fingerprints stored in the FBI’s biometric database (IAFIS), which houses over 150,000 million prints. And thanks to the departure of messy ink-stained fingertips, biometric analysis isn’t just for solving crimes anymore.

You're walking down the street, minding your own business. Then you see it—a large, bright fireball in the near distance. A tremendous heat wave speeds towards you at one thousand miles an hour, and before you can think, before you can even blink, the extremely heated wind pushes right through you. Your skin melts, your eyes liquefy—your face disappears into the wind. Before you know it, your pancreas collide with what’s left of the person next to you, your duodenum is dissolving faster than ...

While a lot of internet threats are rather over-hyped, there are some serious things to be cautious of when going online. Probably the biggest risk to the average internet user is malicious software. Commonly knows as "malware," this term refers to any program that exists solely to do harm. This may include damaging your computer or accessing your data without you knowing. Viruses, trojans, and spyware are all forms of malware. Now, malware can seriously mess up your system, and the idea of s...

Deadly natural disasters can happen at any moment— earthquakes, hurricanes, tsunamis, floods, fires and especially tornadoes. That's why you have to be prepared.

someone runs into a airport and is wearing a fake bushey beard, turban, and robe and you are carrying a fake bomb. so you run in and say Alicabad then softly you say just kidding then hold up the fake bomb. then the airport secruity will jump on you and cuff you then take you away.Thats it!Warnings

The most recent viral video on YouTube is just that. A viral video. After seeing all the hype and 'support' that the 'movement' is getting, I want to tell you that this is a misleading video and somewhat of a propaganda campaign. These are strong accusations against such a 'humanitarian' cause, but I'm here to show you why.

Oh yeah, this is a big topic, at-least for me. All the frequent flyers will/should be interested in this topic. I'm sure all of you have heard at-least something about the TSA, and most of it should have been bad. Complaints, lawsuits and general disgust surround this organization. Is there a reason, or are the 'extremist liberals' at it again? Let's find out!

Much of the press around the launch of Google+ has pitted it squarely against Facebook. This was highlighted painfully for Facebook with their (misguidedly dubbed) "awesome" announcements yesterday. Their launch of a new design, video calling, and group chat might have been exciting, had not Google announced its Hangout feature for Google+ a week earlier (and by the way, introduced their own 1-on-1 video calling inside of Gmail way back in 2008). Hangouts took video calling a step further and...

It's really a shame that it is so hard for people to make money on the internet these days. The dot com bubble has receded and scams are plentiful on the web. There are, however, a couple of legitimate ways to make a few extra bucks online, Amazon Mechanical Turk, or MTurk for short, is one of them. The idea of MTurk is to hook up programmers with people that do tasks that computers can not, these tasks are called HITs (Human Intelligence Task). These tasks include article creation, creative ...

Finally! Gardening! Many have been waiting for ages for this invention to come true, and now it has! Come experience it for yourselves in the Test Realm (instructions on getting there will be added)! When you enter, go the Moolinda Wu and she will teach you how to start gardening. Easy as that! You can plant many things, and monsters drop seeds, too. You can plant indoors or outdoors. Garden now on the Test Realm!Here's the complete article Professor Moolinda Wu wrote:
There's gonna be a rumble.... For this week's GJ article, I thought I would jump right into talking about a mortal-lock favourite of mine: West Side Story. If you haven't seen it (and a lot of folks havent - dudes especially) and you want a lesson in filmmaking craft from a bonafide master then you kind of owe it to yourself to rent this undisputed gem.

Kurt Harris, MD, writes about paleolithic nutrition at his highly recommended blog, www.paleonu.com.

How do we really come to the decisions that we make? Is it just flip a coin and hope for the best or is there some underlying procedure that we go through, consciously or unconsciously, that guides our course of action?

There are no spoilers in this writing, read without worry. Finished Episode 3 of Alan Wake yesterday, impressed by different reasons. I originally bought the game for the possibility of great story, dialogue, and voice acting. That part of the game has been disappointing. What has stood out from playing episodes 1 to 3 is the level design and game play.

If you follow the Anonymous, Occupy, and IT security scenes, you have no doubt heard about a dox release. What is it? How can it hurt you? And most importantly, how can you protect yourself from it? Some of these steps might seem common sense, while others will be an ah-ha! moment. Your private info is both your biggest weakness and your biggest weapon in your battle to remain anonymous. You must learn how to use it as both.

In my recent Darknet series, I attempted to connect the dots on the Deep Web. I covered the two largest anonymity networks on the Internet today, Tor and I2P. While my initial four articles were meant as an introduction, I ended up receiving a lot of interesting comments and messages asking the technical differences between the two. I'd like to thank all of you for letting me know what was on your minds, as you should always!

Many windows users, if not all, run into a virus infection once in a while. This is unavoidable when using Microsoft's operating system. Without digressing too much, the fact that Windows is such a popular OS with no controlled software sources makes it easy for viruses and malware to spread. And while there's a plethora of antivirus tools for Windows, sometimes infections (such as certain scareware) can disable the install and/or use of antivirus systems and render your OS unusable until cle...

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. Part 5 in Minecraft World's Ultimate Survival Guide is, for me, the longest article to write. Since I squeezed out a lot of information from other areas to put into survivability, its going to be a fairly long read. Of course, you can just skip to your topic of choice.

Problem: You're a PC gamer who absolutely loves The Elder Scrolls series and were eagerly anticipating the release of the newest game, Skyrim. But as much as you'd like to pick up the new game, money is tight. What do you do?

Welcome to the Google+ Insider's Guide to all things Google+. We're dedicated to keeping you updated with all the latest news, tips and tricks on Google+, and this official index will serve as a one-stop catalog of all our How-To articles, as well as all the news & updates we've covered over time.

Minecart rides primarily serve two different functions—transportation or entertainment. We rarely see minecart-based transportation systems in Minecraft these days because most servers support warps or allow users to set multiple homes that they can simply teleport to. That leaves the primary purpose of entertainment.

Wireless networks. Nowadays, everyone uses 'em, but most don't secure 'em. On average, I can drive up and down any block in my city and find at least one or two open or semi-open networks on any given day. With some changed MAC addresses for good measure, an attacker can use your network as a spring board for who knows what. When the police come a few days after, they are coming to your door—and not to talk about how nice your lawn is. Don't be that guy.

ACTION MOVIES The Hunger Games (2012)







































