Hello fellows nullbyters, first of i will start saying that im addicted to this community, i feel the challenge growing up so fast, all the newbies, amateurs,advanced and professionals hackers around trying their best to help the community, badly but we got some script-kids too but anyway, today we are going to learn how to install and use clanAV in kali linux.. INTRODUCTION

In this tutorial, we learn how to manage a fever in children. When your child has a fever, this means their body is fighting an infection. The fever will vary depending on what it is, but it will usually peak at 106 degrees. Don't bring the fever down with Tylenol, because it could make the cold last for a longer amount of time. This can be a greater threat to health than the illness was in the first place. If the child starts to get a higher fever, this is a good sign that the body is killin...

Learn how to do the Kobe Bryant pump fake & pivot! This is another Nike Signature Move from NBA Laker MVP Kobe Bryant. Get in triple threat position. Jab step, drive by, pump fake and then pivot. This is a mid-range game for when you have an aggressive defender. Show him the ball, step through for a drive. If the defender is close left pivot around in a pirouette. Take the shot or you've got the teammate.

Growing a garden isn't a walk in the park. Besides watering the plants and choosing the right kind of soil, one of the biggest threats is also one of the smallest. Bugs can be a major factor when planting certain fruits or veggies in a garden and should be taken care of as soon as possible.
In order to keep your PC safe from annoying or potentially dangerous threats on the Internet, a properly-configured firewall is a crucial item in helping prevent your system from becoming compromised. The Windows Firewall in Windows Vista™ is the first line of defense in helping to keep your computer safe. By preventing your computer from being infected by malware, Windows Firewall is designed to be easy to use and is automatically enabled to protect your computer as soon as Windows starts. T...
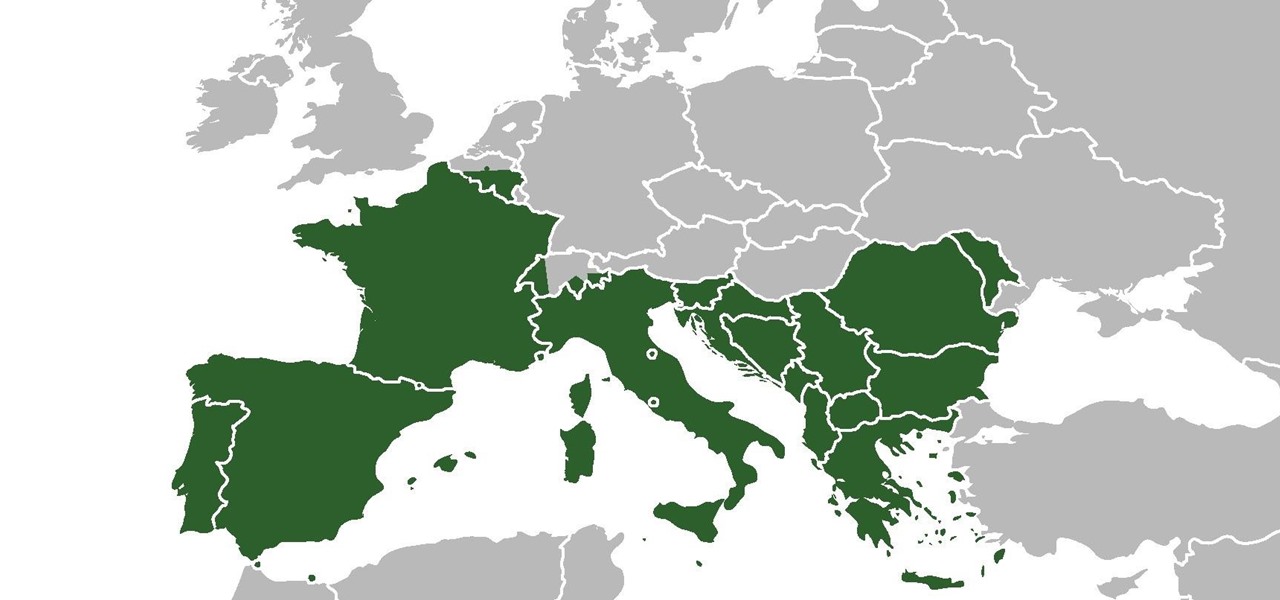
The beauty of southern Europe won't protect it from invasions of disease-carrying ticks and mosquitoes—in fact, the Mediterranean climate and landscape may be part of the reason the bloodsuckers are expanding there, bringing unique and terrifying diseases in their wake.

These days we're used to triple threat stars who, for instance, act, dance, and sing. But stars that excell at all three are as difficult to find as a needle in a haystack.

You may or may not know it, but getting rid of old batteries is a problem nowadays. Buying alkaline batteries from the store can be bad news, since these cannot be reused or even recycled. They end up in land fills and can pose serious toxic threats. Buying recycled batteries from the store is a better way to go, since these guys can be recycled and of course, reused. So check out this tutorial for some more adivce on properly disposing or your batteries. Good luck and enjoy!

If you've had an iPod for long enough, chances are you've had issues with iTunes recognizing it at one point or another, and the threat of having to delete all of your MP3s and other files has loomed large. Well worry no more! This video contains instructions for how to make iTunes recognize the device again without having to delete all of your files! All you need to do is gain access to your hidden folders, get into the iPod's folder, and replace the firmware. Brilliant!

This video tutorial from ballader1 shows how to remove viruses, trojans, adware, spyware from your computer.

James Marey teaches how to test whether your Anti virus is still working perfectly. First right-click anywhere on your desktop, go to 'New' and select 'Text Document' to open a new document. Now find some text containing a virus from the internet or you copy the text from the video. After entering the text, go to file and save the document. Now if your anti virus is working perfectly it will pop out a virus threat indicating the file you just saved. Finally select the appropriate option to re...

In this video the instructor shows how to get rid of fleas. He starts telling about how infectious the fleas can be and how much trouble they can cause. He gives a step by step procedure on how to get rid of them. He says that you should eliminate the threat first by removing eggs, larvae and other germs from the area. He shows how to quarantine the infected area and how to wash them in warm water to kill them. He shows how to use vacuum cleaner to clean all the carpets and other furniture. N...

This is a Cheat Engine guide on how to hack this flash game - B29 Assault. Kongregate Acheatment shows you how to hack B29 Assault with Cheat Engine (09/23/09). This B29 Assault cheat will give you infinite nukes and an invincible hack.

In this episode, Brandon Jackson shows how to merge two images with the Photoshop gradient tool to create a banner montage. Doug Grammar joins D.Lee Beard again, this time to explain spyware, adware, and keylogging. They explain what these threats to your privacy & computer speed are as well as how to prevent and get rid of them. Speaking of security, Jason Rybicki shows one way to tell if your privacy is being compromised on a Mac using a free widget.

What happens if you unknowingly connect a malicious USB drive and it starts infecting your entire office network? Instead of having a panic attack and working all night to find a fix, you can just put on a mixed reality headset like Microsoft's HoloLens and point.
Your company is deciding on starting new projects but there is a lot you need to do to make sure these projects are right for your company and will be financially rewarding to the bottom line. Before you begin you and your project management team will need to go through a Project Evaluation Process.

Dull knives in the kitchen are not only slow, but possibly the most dangerous threat in your home. In this entertaining and informative video, Bruce Trettor teaches how to properly sharpen your own knives with a hand-held sharpener. He explains how to test the sharpness of your knives, the common indicators of improperly sharpened knives, and some great tips on chopping and slicing that will drastically improve your cooking skills. He also covers the different techniques necessary to hone you...

Wiping our shoes off as we enter the home reduces the amount of contaminated dirt tracked in. Large mats, that cover two or three strides, will ensure that even those that refuse to wipe will leave most of the dirt clinging to their shoes on the mat rather than your carpet.

Gonorrhea infections reached a peak in 1975, then decreased until 2009, when infection rate started rising and has increased each year since. With the rise of antibiotic resistance, those numbers are only going to get worse — unless we find new treatments against the bacteria.

Antibiotics are one of our main weapons against infections. The problem is that many bacteria are becoming resistant to most of the antibiotics we use to treat them, and those 'superbugs' have created an urgent threat to our global health. A research group found a new way to hit a well known bacterial target and have developed a drug to hit it.

When the mosquito that carries the malaria parasite (Plasmodium falciparum) bites someone, the parasite must travel to the liver where it undergoes part of its lifecycle before infecting red blood cells and spreading to its next host. Until now, the first step of how the parasite gets to the liver hasn't been clear.

Although this century is still young, with little fanfare we may have just witnessed the "Hack of the Century." AV software developer Kaspersky of Russia recently announced that they found that some hackers have stolen over $1 billion from banks around the world!

You encounter this problem many times, when you plug your flash drive, and suddenly you find that all your data has become shortcuts everywhere!!!

Yellow fever has emerged again in Brazil, causing death and disease to people unprepared for this mosquito-borne illness.

There are countless ways in which you can turn your love of tech and coding into a full-fledged career — from developing apps and websites as a freelancer to working in the IT departments of small startups or major tech companies. But one of the best ways that you can put your programming skills to good use is to join the increasingly important world of cybersecurity.

Cruise Automation, General Motors' (GM) driverless car arm, has hired two hackers who were once seen by many as a safety threat to help find vulnerabilities in its self-drive car network.

A New York creamery was forced to recall items after a fatal disease outbreak stemming from their soft cheese products.

A recent security risk exposed by software engineer Szymon Sidor has raised a few eyebrows amongst the Android community.

Good day to everyone, today I will present some basic and advanced concepts that targets sophisticated attacks on the social basis, also I will write about some steps that can prevent this attacks from occuring, basically we will examine Social Engineering from the angle of attacker and victim, some people who are interested in security and work for middle-sized companys can learn and use something interesting from this post.

Null Byte users have often requested video content, but the question has always been what format would best serve our community. This week, we partnered with Null Space Labs, a hackerspace in Los Angeles, to test the waters by hosting a series of talks on ethical hacking for students in Pasadena Computer Science Club. We invited students and Null Byte writers to deliver talks on Wi-Fi hacking, MITM attacks, and rogue devices like the USB Rubber Ducky.

Antibiotics used to prevent diseases in livestock are creating a world of hurt for humans and the soil we depend on for food. Bacterial resistance to antibiotics is a global health issue. The overuse, underuse, and poor use of these life-saving drugs is rapidly removing them as a treatment option for serious infections in humans—plus bacteria are naturally adaptive.

Former Vice President Dick Cheney was so fearful of attacks, he had his heart defibrillator re-calibrated to block incoming wireless signals so that highly skilled hackers couldn't send him into cardiac arrest.

This will show you how to do the Lebron James Signature Move from Nike series on NBA superstars bball skills.

Today is the day before Thanksgiving. It's also the BIGGEST travel day in North America. Everyone is taking flights home to their family and friends for a nice Thanksgiving dinner. But this holiday will be one to remember thanks to the TSA.

Kill in the Defender Shadow Arena Challenge in the Drowned Pass on the Xbox 360 game Darksiders. You need to enter the Shadow Realm and defeat four portals to free Vulgrim.

Learn how to organize your kitchen. You might cook more if your kitchen weren’t so cluttered. Okay, maybe not. But, still—wouldn’t it be nice to have an organized cooking space?

People like Ralphige and The Jerky Boys have elevated prank phone calls to an art. Here’s how you can get in on the fun.

This is how to do the Manu Ginobili step back jumper! NBA hot shot show's us how to pull the step back jumpshot, one of his Signature Moves on Nike's series. First the long step and catch your balance. Then setup for the rim. Go behind the back and then see what you have in front of you.

You may have seen news reports over the last two days detailing a major security flaw in virtually all smartphones. The devices that are at risk are not limited to either iPhone or Android — all of us are affected. If you want to make sure your smartphone and its data stay secure, there are a few steps you can take.
Welcome back Hackers\Newbies!