See Licker Beta and the U-8 Boss on this level of RE. See the playthrough for Resident Evil 5: Chapter 5-1, Underground Garden in this three-part video. The ruins appear to be adjacent to a large facility. Perhaps the answers Chris and Sheva seek can be found inside?

Is someone threatening, following, or preventing you from carrying on a normal, healthy safe life? Protect yourself from the threat of injury or physical harm by filing a restraining order. In this video, learn what steps are needed to file a restraining order.

Crafts are easily completed once you learn how to quickly thread a sewing machine. You Will Need

If your personal food pyramid replaces “Grains” with “Pizza” and “Fruits and Vegetables” with “Taco Sauce,” it’s time to make some changes.

When running for more than 30 minutes, you'd better hydrate along the way. For every 1% dehydrated you get, your performance can suffer up to 5%.

This is for everyone who has ever been frustrated by this mightiest of puzzles. Solving the Rubik's Cube.

We're living in uncertain times. The sudden outbreak of the novel coronavirus and subsequent self-isolation of roughly half the world's population has led to a massive reorganization of the economy, countless layoffs, compromised security networks, and a variety of other significant disruptions that will forever alter the landscape of our daily lives.

Ride-sharing firm Lyft says it will continue to rely on drivers in the near and long term even as it replaces them with driverless cars, Taggart Matthiesen, Lyft's director of product, said during a Podcast with Recode.

A promising new antibiotic has been discovered in, of all things, another bacteria. Burkholderia bacteria live in diverse habitats, including soil, plants, and humans where they thrive by knocking out other microbes that compete with them for resources or threaten their existence. Scientists have discovered they accomplish this by producing a very effective antibiotic.

As the world goes into a frenzy over the latest strain of WannaCry ransomware, it might be a good time to remember to update all your devices. Yes, those little reminders your phone and computer throw at you every now and then to update your junk can be really annoying, but not without merit.

Your Android phone could be listening to ultrasonic ad beacons behind your back. The unwelcome news comes year after app developer SilverPush promised to quit using its (creepy!) eavesdropping software.

When you think ticks, one of the first things to come to mind is Lyme disease. However, as terrible as Lyme disease is, there's another threat from ticks rising in rank in Connecticut and the Northeast — one that is spreading and that hospitals are not prepared for — the Powassan virus.

Download a popular, legit app from the Google Play Store. Decompile it. Add malicious code. Repackage the app. Distribute the now trojan-ized app through third-party Android app sites. This is how advertising malware Ewind, what Palo Alto Networks calls "adware in applications' clothing," infects Android users.

US blood banks have assured the American public that they have the tools to prevent a Zika contamination, despite the rapid spread of the disease.

Chrysaor, a zero-day spyware believed to have been created by the Israeli "cyber war" group NSO, is an even greater threat to Android phones than it ever was to iOS.

The latest Google Play Services update has somehow broken major functionality in both Titanium Backup and Substratum. Titanium Backup has suddenly become stuck at zero percent while restoring, and Substratum simply fails to apply themes anymore. Both of these apps do require root, but they've slowly become essential to rooted users, especially since apps like these come into play when you're deciding what your next phone should be.

With the recent news that New York County's District Attorney's office is trying to get into over 400 locked iPhones for use in criminal investigations, you can see why it's important to keep other people away from your personal data. The fact that it can and will be used against you in a court of law is just one reason to protect your phone, because even if you make sure to stay above the fray, identity theft and bank fraud are still very real threats.

Cable TV providers were dealt a pretty significant blow on Thursday, February 18th, 2016, when the Federal Communications Commission decided that customers should have a choice in what type of device they use to watch cable, instead of being forced to rent a set-top box.

The increasingly important world of white hat or "ethical" hacking is getting competitive. Thanks to growing salaries and opportunities for talented and trained coding pros who can infiltrate servers and safeguard networks against digital threats, demand for intrepid cyber warriors is through the roof, and it shows no signs of slowing down any time soon.

There are countless ways in which a talented and trained programmer and tech pro can earn a lucrative living in an increasingly data-driven age — from writing and creating apps and games to working for a cybersecurity firm or even the federal government.

Sharing pictures from Google Photos by sending a link saves time because you don't have to download the image from Google, then reupload it somewhere else. But anyone who has your link can access your pictures, and baked into every file is metadata that you may not want prying eyes to know about.

Over the past two years, Apple's Worldwide Developers Conference (WWDC) has become a showcase for new ARKit capabilities. This year, it could offer more information related to Apple's long rumored augmented reality wearable.

Next to Game of Thrones, Harry Potter is one of the most beloved franchises in entertainment today, and now we have another peek at its dive into augmented reality.

Location services company Mapbox has added new capabilities to its location-based gaming tool to fend off Google's challenge for the same mobile app category.

Hyundai Motor Company says it will launch its driverless tech ahead of schedule, but the Korean carmaker will remain behind mainstream rivals, including General Motors (GM), Nissan, and Honda.

Apple announced upcoming changes today to prevent third-party tracking of users and prevent autoplay, on Safari. Safari will prevent the recording (by anyone other than Apple) of users' browsing behavior, and by doing so prevent advertisers from targeting ads based on individuals' history.

It wasn't too long ago that Uber threatened to fire star engineer Anthony Levandowski. Eleven days to be exact. If Levandowski didn't turn over the documentation he allegedly stole from Google's autonomous car division, Uber informed Levandowski that they would take "adverse employment action." Today, The New York Times reported the ride-sharing firm has delivered on that threat. In a memo sent to employees Tuesday morning, Uber announced Lewandowski's official departure from the company "eff...

Google Home now helps users to discover new music with an added "Listen" tab in the app. The feature offers suggestions based on the Cast-enabled apps on a phone, while offering other apps to download if you'd like to broaden your musical horizons. The playlists are curated to your individual taste and will adjust for different artists and activities, which is a pretty nifty feature. This means that Google Home can cater to your momentary mood change with music, which is a welcome addition to...

infosecinstitute posted a handy article about what to expect in the new year for cyber security, along with highlighting major game changers from 2015; 2016 Cyber Security Predictions: From Extortion to Nation-state Attacks - InfoSec Resources.

I don’t buy socks—I get a pack from my parents on Christmas Day, so I’ve got to make sure they last all year. Other than losing them mysteriously in the dryer, the biggest threat to my limited sock collection is a stretched out cuff. Nothing's more frustrating than a loose sock sliding down into your shoe.

While websites may run smoothly without any noticeable vulnerabilities, there's always the looming threat that any background weakness in the site can be exploited by hackers. Once a site is compromised, it can be difficult to get it fixed without the proper help. Google has recently launched a new series entitled "Webmasters help for hacked sites”, which teaches web developers and site owners how to avoid getting hacked and how to recover their website if it gets compromised in any way.

If you have a Mac running Mountain Lion, I'm sorry to tell you that all it takes to crash almost any app on it is eight little characters. This strange bug seems to only affect Mountain Lion and doesn't cause your computer any harm. Apparently, it even crashes the error reporter. On its own, the bug doesn't really pose a threat—just don't type it.

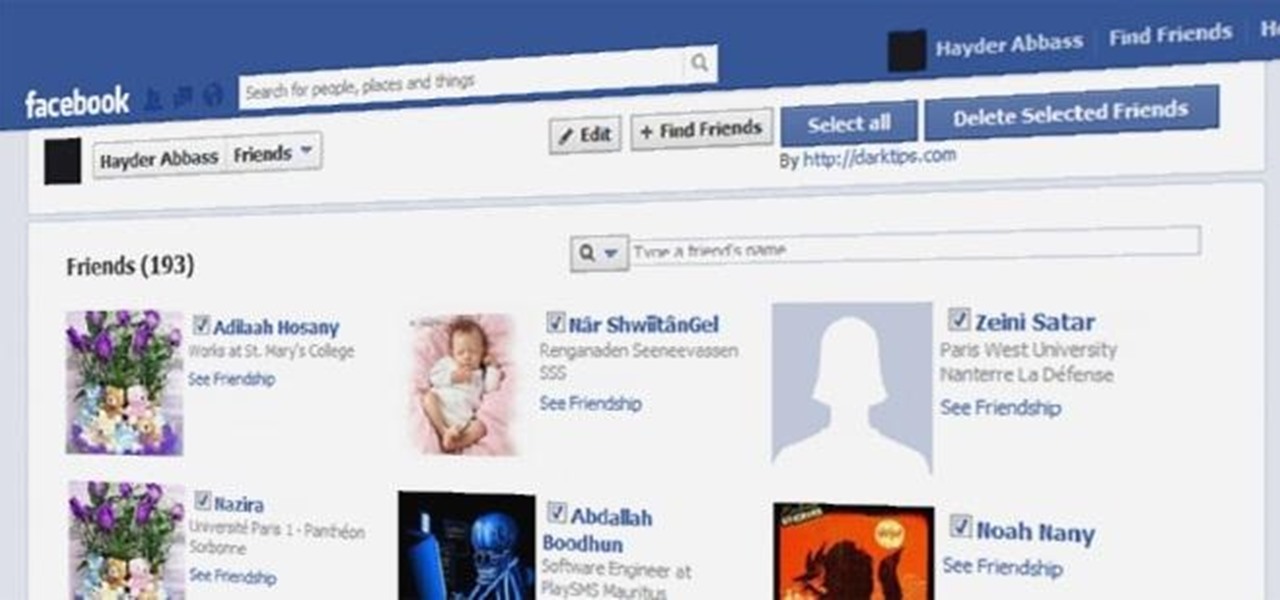
Facebook makes it extremely easy to keep in touch with family and friends, while maintaining those relationships with little to no face-to-face contact. It's the perfect tool for recluses.

It seems like every other day there's a new security threat or data leak in the news. Whether it's your credit card PIN or your smartphone's apps leaking your email address, no one wants their personal information out there, especially passwords. And if you use the same email address and/or password for more than one site, the effects of someone getting hold of your credentials can be catastrophic.

Security researcher Nadim Kobeissi has discovered that the Windows 8 SmartScreen feature, meant to screen downloads for malicious software, actually reports the data about which applications users are installing to Microsoft. He also says that "the Microsoft server is configured to support SSLv2 which is known to be insecure and susceptible to interception." The two main concerns are the ability of law enforcement to subpoena Microsoft for the information and of hackers to intercept user data...

Security researcher and iPhone hacker pod2g has brought attention to a flaw in Apple's iOS that allows the user to change the reply address of an SMS message. This bug has been a part of the iPhone's SMS since the first iPhone in 2007, but Apple has yet to address it. Basically, there's a section in the text payload called User Data Heading (UDH) that controls some advanced features, one of which is the reply address. By changing the reply address of a text message, you can make someone send ...

Dropbox announced Tuesday that a recent security breach compromised a list that included the email addresses of certain Dropbox users. To avoid future complications, the service announced that it would be implementing two-factor authentication, and even more useful, a security page that lets you monitor all activity on your account. In light of this and other recent web security threats, you might also want to know that services like Gmail, Facebook, and Yahoo! Mail have similar pages where y...

Some of us use our smartphones for almost everything. Manufacturers know this, so they try to make their devices as convenient as possible to use, but sometimes that convenience comes with a cost to security. The very same technology that allows you to easily share music with friends and make purchases can also put you at risk. Photo by sam_churchill

We need to take our privacy and security much more seriously. Whether it's malware-infected apps or the mishandling of our data by companies like Facebook, there are threats all around us in this digital world. Fortunately, some smartphones are simply designed to protect us better.

When it comes to your security, you want the best of the best. Why settle for mediocre service with something as valuable as your protection? Malware continues to make its way onto the Play Store, leaving millions of devices vulnerable. You need an app that will shield your devices from both the latest malware threats and threats nearby. And when it comes to antivirus apps, there is only one choice.