Uber's driverless cabs began picking people up in Arizona in February, after its attempt at a pilot test in San Francisco. Now, one of these cars has been in an accident, and that's just the tip of the iceberg.

Rumor has it that a gang of hackers—or possibly, one lonesome individual—holds the power to remotely wipe millions of iPhones and iCloud accounts, unless Apple coughs up some ransom money by April 7.

Baidu's self-driving car unit has had a tough week. Today, the company's leading artificial intelligence (AI) expert, Andrew Ng, announced in an optimistic blog post that he would be leaving the Chinese search engine company to pursue AI research on his own.

Huawei is making a fresh attempt at launching into the US market to challenge Apple and Samsung's monopoly on premium smartphones. In its latest attempt to break into America, Huawei is trying to get its Chinese mobile chipset accredited by AT&T.
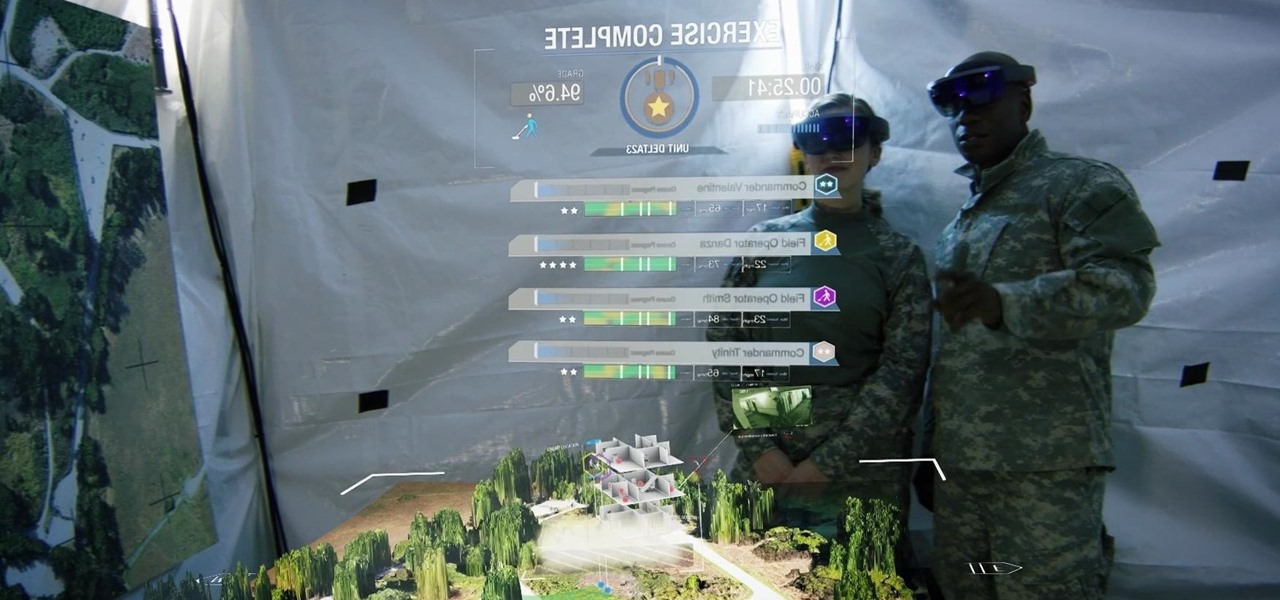
The limitless applications of 3D data visualization will enable a more efficient approach to many of life's problems. Each day, developers exploring this technology are finding new ways to solve these problems in mixed reality; 3D modeling, easier house management, spinal surgery, and forest fire management are just a few recent examples of ways 3D data visualization can benefit us all.

When Kaci Hickox, a Doctors Without Borders nurse, returned to New Jersey from working with Ebola patients in West Africa in 2014, she was surprised by her reception. Instead of a quiet return to her home in Maine after four weeks on the front line of Ebola treatment, she was quarantined by the State of New Jersey in Newark. She later filed a lawsuit in U.S. District Court for violation of her civil rights, false imprisonment, and invasion of privacy.

Virtual, mixed, and augmented reality all provide different but compellingly immersive experiences that draw us in through sight and sound. But what about our other senses? A few strange inventions are already exploring the possibilities.

In a letter dated February 16th, Apple CEO Tim Cook responded to the FBI's demand that Apple create a "backdoor" to bypass the encryption on an iPhone used by one of the perpetrators of last year's terrorist attack in San Bernardino, CA. Cook began the letter by stating that Apple has "no sympathy for terrorists" and has cooperated in giving the FBI all of the information that it has available.

If you have seen the movie Fast and Furious 7, you know what "God's Eye" is. Well this might spark interest to you.

Most of you already know that a zero-day exploit is an exploit that has not yet been revealed to the software vendor or the public. As a result, the vulnerability that enables the exploit hasn't been patched. This means that someone with a zero-day exploit can hack into any system that has that particular configuration or software, giving them free reign to steal information, identities, credit card info, and spy on victims.

Admit it: when nothing's at stake other than your boss's disapproval, you don't exactly feel the urge to get working. Finding the motivation to take on a task, whether at work or home, can be a constant struggle. Though working through your laziness might seem like the best course of action, a meaner method can make more of an impact on your productivity.

Coffee shops are a relaxing place to get work done on your laptop; there's free Wi-Fi, fresh coffee, and people generally leave you alone. Inevitably, those cups of coffee will go straight through you, resulting in a much-needed bathroom break. But while you're attending to your bodily functions, who's attending to your MacBook?

I have never been a morning person, and that's a trait that I don't think is going away. Combine my distaste for early hours with being a heavy sleeper, and it adds up to a lot of alarms being dismissed in a haze, with no real intention of ever waking up.

Most of us have some sort of malware scanner or antivirus program on our computers, but what about our smartphones? A lot of people don't realize that computers aren't the only devices that are susceptible to malicious software and apps—they can follow you on your smartphone or tablet, too.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

Do you live in a dangerous neighborhood? Even if your area isn't known to be dangerous, it could still be a target of home burglaries. Don't let the thieves have the upper hand. Make sure the only thing they're stealing is grass. To properly secure your home from external threats, you must find weaknesses potential and potential entry points and fix them.

Now the werewolf and the vampire are no longer threats, but we have heard reports of the giant spider going on drinking binges and webbing up large buildings and even entire towns in the California wine regions as well as in Kentucky bourbon country. It even left a slurred message on our answering machine about plans to step up the devastation this October 31st. We can’t protect each of you from this sticky conclusion, but we can offer a suggestion: build your own giant spider web and you wil...

Amber, emergency, and public safety alerts on an iPhone are loud — startle-you-to-death loud even. They can happen at any time, day or night, and sometimes back to back when you're in a big city. Those blaring sirens can wake you from sleep, interrupt an important meeting, or disrupt an entire movie theater mid-movie, but you can turn most of them off if you're tired of hearing them.

If you're interested in joining the increasingly popular and lucrative world of ethical or "white hat" hacking, you're far from alone. More and more coding and programming pros are turning to this field thanks to the high pay, countless opportunities, and exciting work environment.

VPNs add a protective layer between your data and your internet service provider (ISP) or bad actors (hackers), so it makes sense they've become so popular lately. Probably the most common one of these is NordVPN, so we explored its mobile app to find all the options worth checking out.

Now that more and more people are working on their personal computers and smartphones as opposed to their work computers as a result of the coronavirus outbreak, hackers are having a field day. Unencrypted home networks and public WiFi connections make it incredibly easy for cybercriminals and even government agencies to access everything from your browsing history to your banking information, and a Virtual Private Network (VPN) is the only way to stop them.

Google's feature drops for Pixel devices have added fun and useful new abilities, such as AR effects for Duo, Call Screen automation, scheduling Dark Mode, and Quick Access Wallet for Google Pay, that are exclusive to the company's line of smartphones.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

You need a break from gloomy coronavirus updates. We all do. The unrelenting stream of doom and negative news is both helpful in terms of keeping ourselves and our families safe, but it also has the unfortunate effect of increasing our anxiety. When will this end? How bad will it get? Is there reason to be hopeful?

While MacOS computers have been spared from some of the most famous malware attacks, there is no shortage of malicious programs written for them. To keep your computer safe from some of the most common types of malware, we'll check out two free tools. These tools can automatically detect ransomware encrypting your files and watch for unauthorized access to your microphone and camera.

It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to throw off any investigators is to change the file attributes to hide activity. We can do this with Metasploit's Timestomp.

It is a great time to be a mobile gamer. Not only are there millions of mobile games on the Play Store and App Store, but thanks to some recent developments, we can also even play PC games. AMD recently released an app, which, among other things, lets you play your favorite PC games on your phone.

As much funding as Magic Leap has secured, another round of funding will still catch headlines. However, the latest funding solidifies the company's strategy for succeeding in the consumer segment of AR.

Hundreds of Windows 10, macOS, and Linux vulnerabilities are disclosed every single week, many of which elude mainstream attention. Most users aren't even aware that newly found exploits and vulnerabilities exist, nor that CVEs can be located by anyone in just a few clicks from a selection of websites online.

Over the last few years, the only thing teased by Magic Leap more than the Magic Leap One itself has been the company's flagship gaming title Dr. Grordbort's Invaders. The game, developed by New Zealand studio Weta Workshop, finally got its debut last week during the L.E.A.P. conference in Los Angeles.

Not all threats to our privacy come from hackers thousands of miles away. Often, we just want to keep our data safe from those around us, who may snoop in our phones or demand we reveal our secrets. That's where BlackBerry Locker comes in.

As of 2016, there are approximately 1.85 billion Android smartphones worldwide. This growing popularity has led to an increasing number hacks and cyber attacks against the OS. Unfortunately, Android users need more protection than what is offered by Google. The good thing is that there are a number of options available.

As expected, Apple began pushing out the final version of iOS 11.2.5 to all iPads, iPhone, and iPod touches today after 41 days of beta testing. Highlights include a fix for the ChaiOS vulnerability, a persistent Now Playing bar in Music, and some signs of AirPlay 2 just in time for the HomePod launch on Feb. 9.

With so much money on the line, it's no surprise that cryptocurrency exchanges are prime targets for cybercriminals. Because of this, the importance of keeping your personal account as secure as possible cannot be overstated. Binance is one step ahead in this regard, as it requires you to enable two-factor authentication to keep your bitcoins and alt-coins safe.

The threat of an evil access point has been around for a long time, and with the rise of open public Wi-Fi, that threat is often overshadowed by how comfortable we are using third-party Wi-Fi hotspots at coffee shops and public spaces. While we've shown an evil twin attack using the Aircrack-ng suite of tools, MitmAP is a Python tool to configure custom APs for many types of wireless attacks.

Threats to your privacy and security are everywhere, so protecting your data should be the highest priority for anyone with a smartphone. However, one threat many people overlook is the company who supplies the operating system your Android phone runs — Google.

After recently being in the news for collecting PII (personally identifiable information) for analytics and after-sales support, OnePlus has another security problem. An individual going by the name Elliot Alderson discovered an app in OnePlus devices that can enable root access with one command.

Because of the way Google Play works, Android has a "bad app" problem. Google allows any developer to upload an app to the Play Store, regardless of if it works, how it looks, or whether or not it can harm users. Malware scanning happens primarily after apps are uploaded, and though Google has recently taken steps to safeguard users with its Play Protect program, you don't have to depend on them.

A recent initiative by the Cherokee Nation American Indian Tribe delivers a success story for knocking out a silent killer — Hepatitis C.

A recent study offers information that might help combat a deadly virus that affects an estimated 300,000 people each year in West Africa.