This is a special four-part series on the human head, neck and skull. Medical students can greatly benefit from watch this anatomy video series. Dr. Gita Sinha "dissects" all of the information pertaining to the head and neck. Dr. Sinha is Assistant Professor for the Department of Anatomy & Neurobiology at Dalhouse University. Each of these videos cover a different topic:

Check out this instructional Russian language video to learn Russian as Russians speak it. This is Theme 8, Lesson 2 in the series. Practice your Russian listening skills by listening to the dialogue presented in this language video. Learn travel related words in Russian.

Microsoft Excel is one of the most powerful programs for modern businesses. By allowing you to manage, sort, and analyze large collections of data, Excel provides an essential service for any company interested in using the power of data science to its advantage.

For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and seeing all that glorious data displayed right in the browser. This is when more advanced techniques are needed.

The Operative Framework is a powerful Python-based open-source intelligence (OSINT) tool that can be used to find domains registered by the same email address, as well as many other investigative functions. This reconnaissance tool provides insight about your target through examining relationships in the domains they own.

Aside from identifying songs with Shazam and using the "Hey Siri" feature while driving, Apple's personal assistant isn't something I regularly use on my iPhone.

Yosemite brought a new, Alfred-like Spotlight search to our Macs, but at times I still find myself wanting more out of it. However, after stumbling upon Flashlight by developer Nate Parrot, I am now able to perform Google searches, look up weather, and even enter Terminal commands straight from Spotlight's search bar.

Welcome back, my hacker apprentices! Although there is a multitude of different hacker types, the one target they all share is the database. I often refer to the database as the hacker's Holy Grail, or the ultimate prize for an effective hack.

Searching YouTube is tough, because there's a plethora of content, so sometimes i's best to do an advanced search. This is not to be confused with the "search options" available during a YouTube search query, because those are limited to key features of YouTube, but not specific search terms. Much like Google, you can search YouTube via search operators. Many of the same search operators that work on Google work on YouTube also. Filter your results the way you want, not the way they want. You...

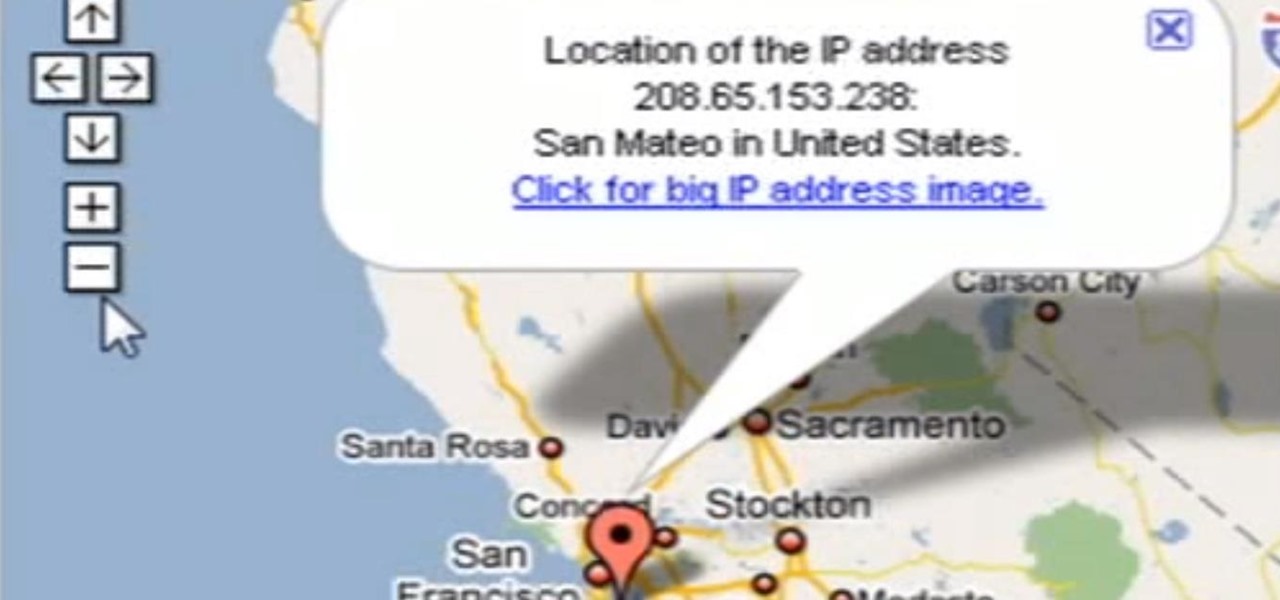
Need help tracing an IP address to a location? Well, Tinkernut has a clear and effect way to help out.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

Database technology has vastly improved the way we handle vast amounts of data, and almost every modern application utilizes it in one way or another. But the widespread use of databases naturally invites a slew of vulnerabilities and attacks to occur. SQL injection has been around for awhile, and as such, there are many defense methods in place to safeguard against these types of attacks.

Nmap is possibly the most widely used security scanner of its kind, in part because of its appearances in films such as The Matrix Reloaded and Live Free or Die Hard. Still, most of Nmap's best features are under-appreciated by hackers and pentesters, one of which will improve one's abilities to quickly identify exploits and vulnerabilities when scanning servers.

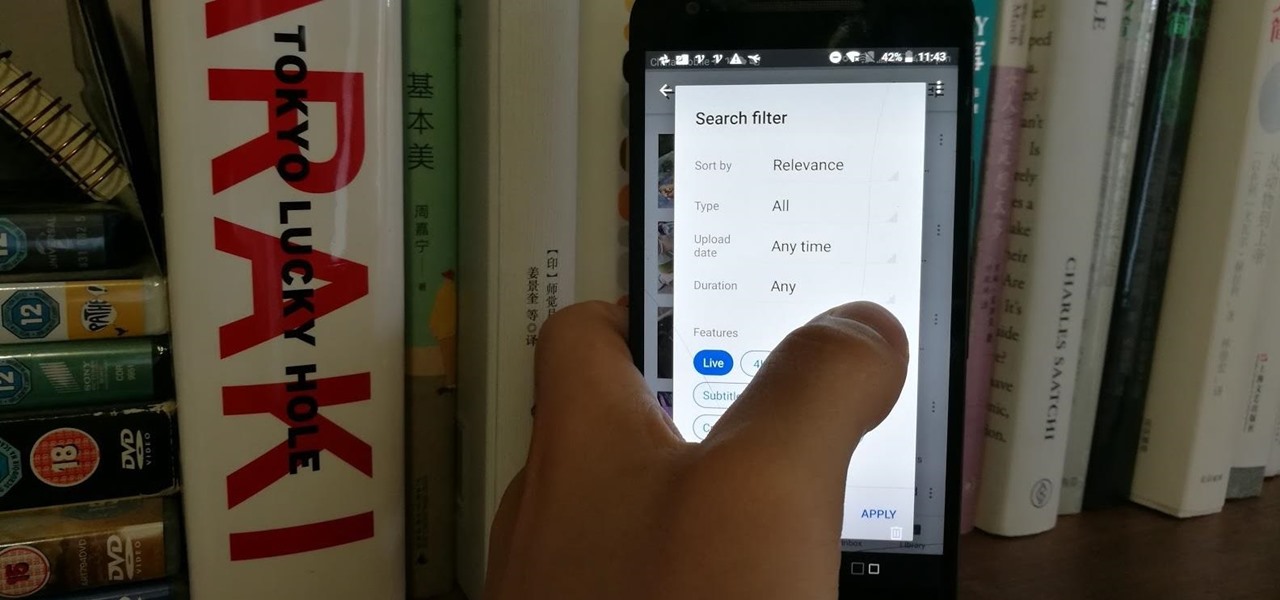
Have you tried searching for 4K HDR videos on YouTube, only to get 1080p videos just because the uploader used "4k" or "HDR" in the description? Or have you tried looking for a video about something that just happened, except YouTube's algorithm surfaces established videos first by default, so all the results you get are older than a month? Well, there's a better way.

Welcome back, my tenderfoot hackers! Have you ever wondered where the physical location of an IP address is? Maybe you want to know if that proxy server you are using is actually out of your local legal jurisdiction. Or, maybe you have the IP address of someone you are corresponding with and want to make certain they are where they say they are. Or, maybe you are a forensic investigator tracking down a suspect who wrote a threatening email or hacked someone's company.

As Microsoft unveiled their new Windows Phone 8.1 software update yesterday, undoubtedly the most memorable takeaway was their showcase of Cortana. Competing directly against Apple's Siri and Google's Now, Cortana is Microsoft's entry into the digital voice assistant fray, and the official replacement to their search app.

You've probably used Google to search for recipes, or to find out what the heck that mystery food on the ingredients list is. But with all its built-in features, there are plenty of other ways the search engine can help you out in the kitchen.

If you're new to DreamCoder for Oracle, one of the things you may want to know how to do is to is write complex SQL queries. Happily, this tutorial will walk you, step by step, through the process. To learn how to use the DreamCoder for Oracle Query Builder, press play!

SoundHound, the Shazam-like song-matching service, recently announced a new mobile app called Hound, which wants to be your one and only intelligent personal assistant.

Now that we have control over a victim's browser, we need to use some attacks to maintain the connection, or even better: upload a shell.

Family Feud is one of the longest-running game shows in American TV history. Its viewer base spans generations, and this is mostly due to the fun nature of the show. Contestants have to guess the most popular answers to survey questions that were posed to 100 random strangers, and the responses often range from silly to downright funny.

Google continues to be the most commonly-used search engine for a reason. While continuing to stay ahead of the pack with advanced semantic search functions, Google even introduced Knowledge Graph results that offer key information without ever having to click a search result.

If you're reading this, you're likely a tech-savvy coding pro whose analytical talents are mostly applied to designing apps, cracking passwords, and infiltrating networks — all of which are admirable activities for both aspiring and seasoned white hat hackers. But there are other profitable ways that you can put these types of skills to use, namely in the world of investment and trading.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

There's nothing quite like getting lost in the TikTok void. While you'll likely never run into the same video twice, the same can't be said for popular sounds and fads. Some trends get so viral, it feels like you hear the same song or track every other TikTok. Just know this: you don't have to put up with any trend you're sick of.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

Back in November, Essential opened the Android Oreo Beta Program for all users of their PH-1 flagship. We even wrote up a full guide on how to install the beta, if you're interested. They followed the Oreo beta with a Reddit AMA, where they mentioned the second beta software would arrive very soon. That update has just gone live, so you can grab it right now in a few easy steps.

If you need to scan a large number of domains for a specific web app vulnerability, Dorkbot may be the tool for you. Dorkbot uses search engines to locate dorks and then scan potentially vulnerable apps with a scanner module.

Open-source data scraping is an essential reconnaissance tool for government agencies and hackers alike, with big data turning our digital fingerprints into giant neon signs. The problem is no longer whether the right data exists, it's filtering it down to the exact answer you want. TheHarvester is a Python email scraper which does just that by searching open-source data for target email addresses.

The latest beta of the popular open-source media player VLC just hit the Windows Store, which means it not only runs on Windows 10 and Xbox One, but the HoloLens as well.

If you watched a YouTube video on your Android device today, you may may noticed something just a little different. If you haven't, go check out the app in your drawer or homepage. Google today pushed out an update to their YouTube app, but by all accounts, it was never meant to hit the public. This is labeled a dogfood build, which is a term used to describe products going through in-house testing, in effect "eating their own dogfood".

In this video you will learn how to say words pertaining to water and health in Mandarin Chinese and then see how they are used in conversation.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to track a USB device.

Data analytics is crucial to the operations of any modern business these days. This trend is going to continue: in three years, 71% of global enterprises predict a rapid increase in data analytics.

Hacking web applications can sometimes be challenging due to the sheer amount of moving parts they possess. At the core of these apps are HTTP requests and parameters, but these things are often concealed from the user, due to security reasons, convenience, or both. However, a tool called Arjun can be used to discover hidden HTTP parameters in web apps.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

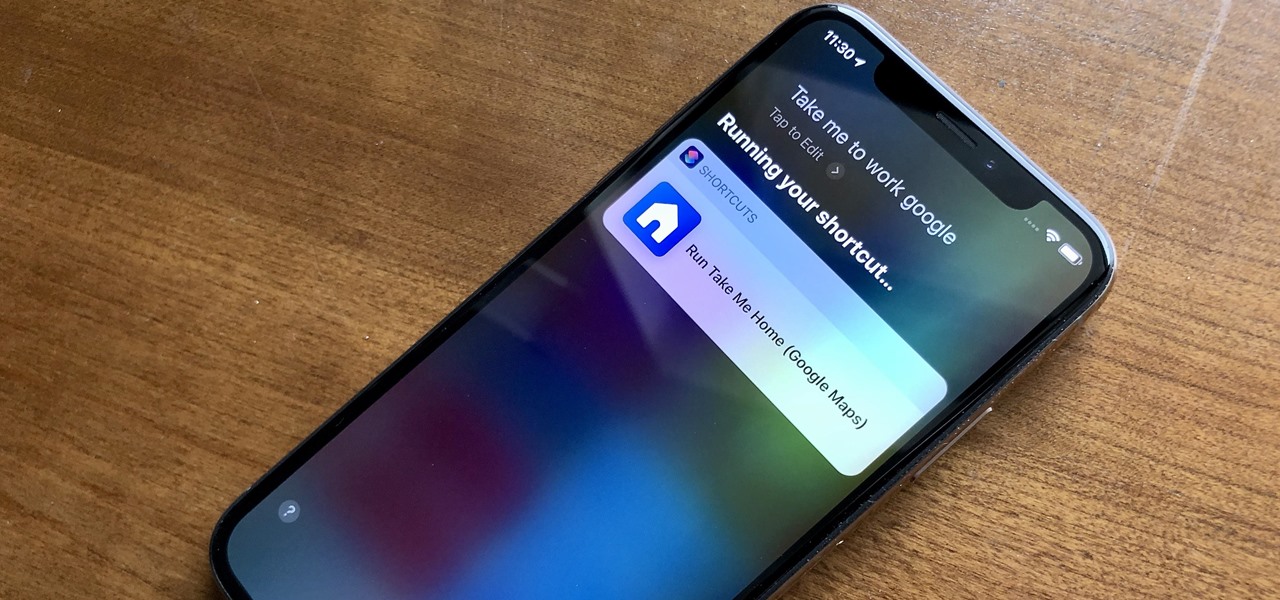
When driving, you can get directions hands-free by asking Siri. You can also make general map searches, show a location's details, call a query's phone number, and view traffic details. However, Siri defaults to Apple Maps for all those. If you prefer Google Maps, Waze, or another third-party navigation app, the map-based Siri commands won't work. But that doesn't mean you can't still use Siri.

Besides its extensive collections of add-ons for Android, Firefox's mobile browser apps have many built-in features that you won't see in other mobile browsers. One feature in particular, available for both Android and iOS versions, makes it easy to switch back and forth between search engines for any query.

At I/O 2018, Google showcased features that would make the Google Assistant easier to communicate with. While some people were impressed with (and maybe creeped out by) Google Duplex, one feature that was well received was the ability to talk to the Assistant without the constant "Hey Google" before each question.