Google is an incredibly useful database of indexed websites, but querying Google doesn't search for what you type literally. The algorithms behind Google's searches can lead to a lot of irrelevant results. Still, with the right operators, we can be more exact while searching for information that's time-sensitive or difficult to find.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

Traditional subdomain enumeration techniques create a lot of noise on the target server and may alert intrusion detection systems to an attacker's intentions. For a stealthier approach, there's a tool with the capability of finding hundreds of subdomains related to the target website without alarming the server administrators.

Learn how to do downhill ski series exercises. Presented by Real Jock Gay Fitness Health & Life. Benefits

Who needs a Rubik's Cube when you have a Rubik's World? See how easy it is too learn and solve. Each video is broken down into its own step.
Two books were presented as suggested reading. One was by Bob Katz: Mastering audio; art and science. The other was Bob Alginski: the Audio Mastering handbook. Mastering takes a collection of songs and makes them sound like they belong together by making certain technical changes. The project page in Studio One is where the mastering is done. Drag in your sound content that you will be working with. Make sure you have the most recently updated version. If you are using multiple tracks, you mu...

Sometimes it's necessary to format your memory card in your mobile phone or digital camera, just like you need to format a hard drive, because of virus problems or slower speeds. This video will show you the steps to formatting (or reformatting) the SD memory card for a cell phone, using a memory card reader. You'll also get details about a write protect error that could happen.

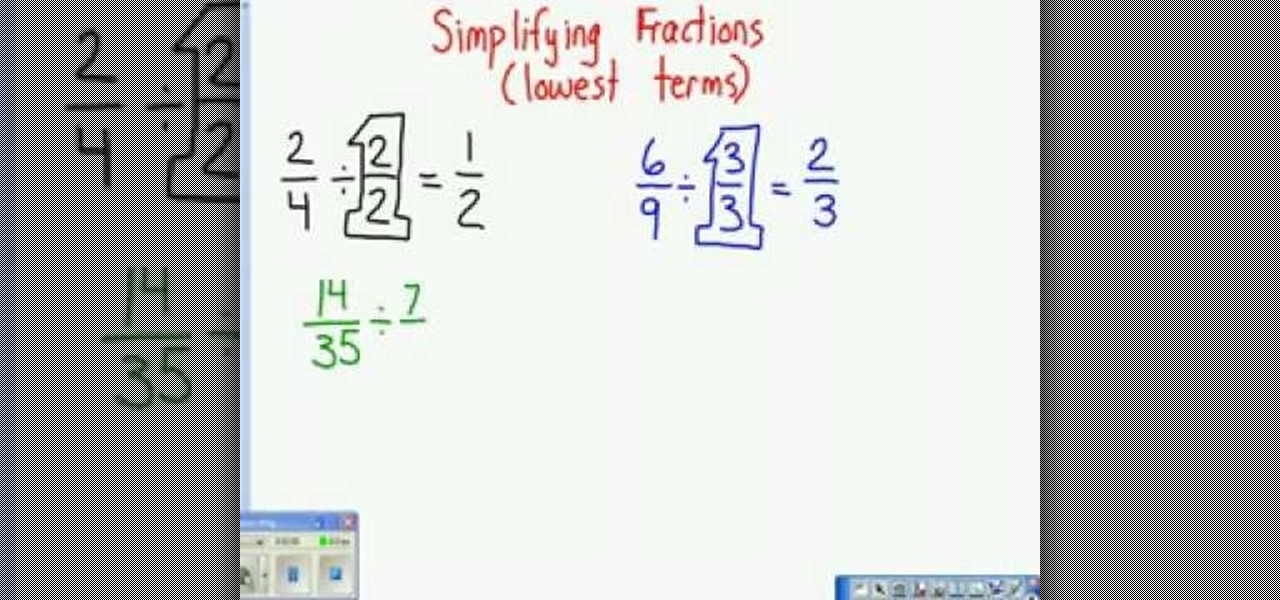
This video tutorial belongs to the Education category which is going to show you how to reduce fractions to their lowest terms. For doing any operation with fractions like addition, subtraction, multiplication or division, they need to be reduced to their lowest terms. To do this look at the numerator and the denominator and decide what number can divide both of them. Continue dividing till you can no more divide them. Now you get the lowest term of the fraction. For example, 2/4 can be divid...

This video tutorial belongs to the software category which is going to show you how to convert a Word document to a password protected PDF file with NovaPDF. Go to NovaPDF and download the program and install it. It is a paid program. Select the word document that you want to convert and select print option. Under the name of the printer you will find novaPDF option. Select this and click 'preferences'. Now click on 'security' and select high level encryption. In the document permissions, sel...

Do you need to lock the door but don't have the keys? This may happen if you are sharing your keys with someone else, staying at a friend's house, or for a variety of other reasons. Check out this video for a sneaky way to secure that door tight without even sticking a key in the lock.

Are you a magician on a budget? Impressive feats of magic don't require an assistant to saw in half, or even a rabbit to pull out of a hat. You need only the slightest sleight-of-hand to perform this impressive magic staple.

Is the Home button the main reason you haven't pulled the trigger on a new iPhone? Are you worried that you'll miss its functionality too much, or that simple things like accessing your home screen will be too hard? Well, don't worry about any of that, because Apple came up with some intuitive gestures that makes the old Home button seem clunky and outdated once you get used to things.

When it comes to finding lost things, the joke goes that it's always in the last place you look. With an assist from ARKit, Pixie can make your iPhone the first and last place you look for that missing item.

The peaceful, pastel and doily-filled world of Pinterest is my oasis. My account conveys who I want to be and what I want to accomplish, so the idea of someone hacking it and ruining my favorite escape for me is heartbreaking. Fortunately, Pinterest has updated its security, implementing three new features to hack-proof your account.

Don't Miss: The Difference Between Virtual, Augmented, & Mixed Reality

Instagram is the world's biggest photo-sharing site, narrowly edging out competitors like Imgur and Flickr. But unlike the competition, Instagram doesn't make it easy for users to download a full-resolution copy of any of the images hosted on their servers, as the site's main intention is to keep folks coming back and using the social media aspect of it all.

First of all, before we start, the modules and some of the tutorials belongs to Und3rf10w, not mine!

When people get accustomed to something, any type of change is typically met with resistance or disdain. So when Twitter decided to swap stars for hearts, the internet wasn't exactly receptive to the new aesthetic.

Ever since Sense 4, HTC phones have had no access to easy access setting toggles from the notification pane. CyanogenMod and other custom ROMs are an option, but even if your phone isn't rooted, you can still have clean, functional quick settings. Step 1: Install Power Toggles

There's something missing on your brand new Samsung Galaxy S4, and if you're a softModder like me, you know exactly what it is already. If you don't know, keep reading, because you should—anyone who wants a better Android experience should.

If you are like me and you have a old iPhone and you don't want to buy a new one, you can fake your ios version by fallowing this tutorial. Just to be safe i am not responsible for what you do with this or if you mess up and wreck your phone. Plus ios and iPhone all belong to their rightful owners.

Sure, your search history can be useful, but more often than not, it's a paper trail of privacy infringement. It's perfectly reasonable not to want to see a complete list of your YouTube queries every single time you search for a new video. Luckily, blocking YouTube from saving your search history takes only a few taps.

It's nearly impossible not to be at least somewhat familiar with Microsoft Excel. While it's needed for many office jobs and data analysis fields, hackers could also benefit from improving their spreadsheet skills. Many white hats already know some of the essential Excel hacks, such as cracking password-protected spreadsheets, but there's so much more to know from an attack standpoint.

Few things are more important than being well-versed in data analytics and interpretation when it comes to succeeding in today's increasingly data-driven world. As a data scientist, these skills are the key to a high-paying career. For hackers, there's no better way to defeat the enemy than to become the enemy.

Since its release back in 1988, Microsoft Office has been the top client and server software suite for businesses around the world. Office's domination is thanks to both Microsoft's extraordinary foresight and their continual updates and innovations to ensure that companies always get what they need.

While North has yet to add third-party app support to its Focals smartglasses, the company has been diligent as of late in its efforts to add more functionality to the bare-bones AR device.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

Mobile app publishers are using augmented reality to solve everyday measurement problems from measuring the length or height of items to previewing furniture in the home.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

Cruise Automation, General Motors' (GM) driverless car arm, has hired two hackers who were once seen by many as a safety threat to help find vulnerabilities in its self-drive car network.

Long before Nvidia figured out how to embed neural networks in its graphics processor units (GPUs) for driverless vehicles, it and other chipmakers were already making the same kinds of devices for 3D games and other apps.

Winter is here, which means we have a lot of questions about the coming season of Game of Thrones. It's hard finding someone who cares enough to listen to you rant about why Jon Snow is the rightful ruler of Westeros. It's also hard to figure out who exactly everyone is and is related to since there are over 150 major characters on the show. We're all getting a little antsy waiting for the new season, so to hold us over a new bot has rolled out 'G0TB0t' on Facebook Messenger. Specifically, it...

The $25 million development alliance Jaguar Land Rover's mobility unit InMotion has formed with US-based ride-share firm Lyft reflects how the British luxury carmaker is leaning towards a fleet service business model for its driverless offerings.

GitHub is an extremely popular site that allows developers to store source code and interact with other users about their projects. Anyone can download public, open-source files on GitHub manually or with Git, and anyone can fork off someone's project to expand or improve it into its own project. It's a really great site for programmers, developers, and even inspiring hackers.

Google has been working on its voice recognition technology ever since the days when you had to call a phone number with a Silicon Valley area code to dictate your query. As you can imagine, things have come a long way in the decade or so that has passed, to the point where we talk to our phones as if they were a person nowadays.

Hello ladies and gentlemen, welcome back to the Part 2 of our UDP & Wireshark adventure as I promised. Last time we discussed about what DNS is and how it uses UDP as its transport protocol but we left some unexplained parts behind and I'm about to investigate those with you. I would advice you to go back to Part 1 so you can have a clear understanding in case you don't feel comfortable with the topic. So our computer made its request to the DNS server and asked "Hey, I want to find out what ...

Welcome back my networking geeks. In this part we are going to keep discussing about IP Addressing and I hope after you finish reading it you will become an IP wizzard.

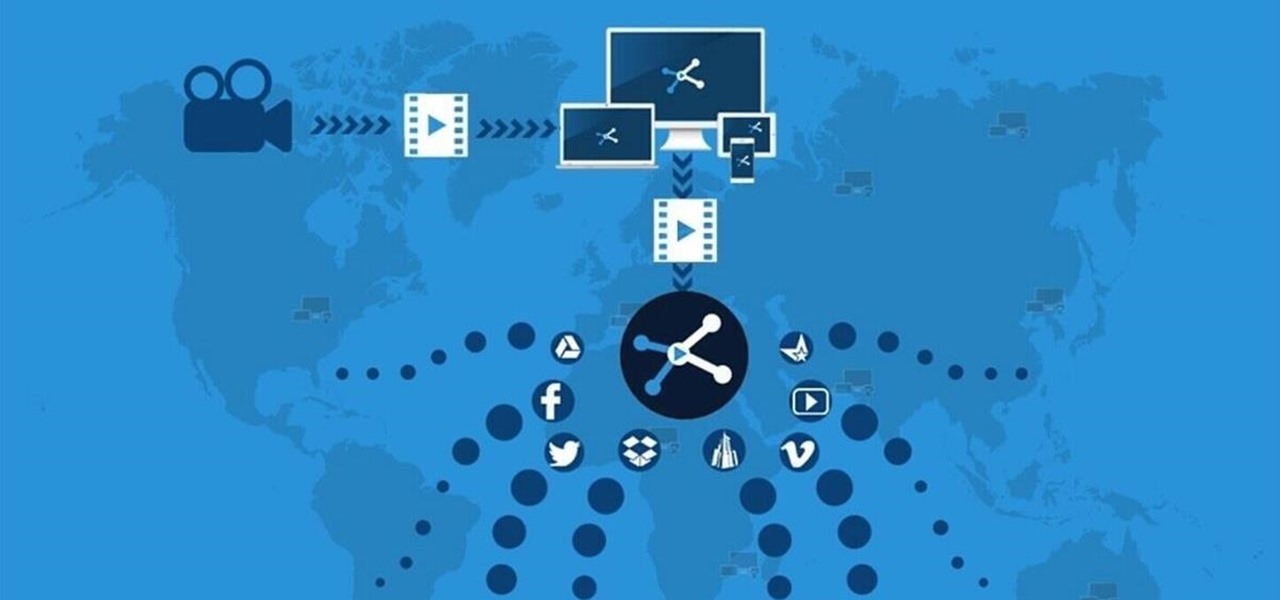
Are you tired of uploading videos to different sites separately? It's really time consuming and difficult. Finally, there is a way to upload and distribute your videos to YouTube, Facebook, Dailymotion, and many more video-hosting websites in one go. No need to upload to every site separately and one by one.

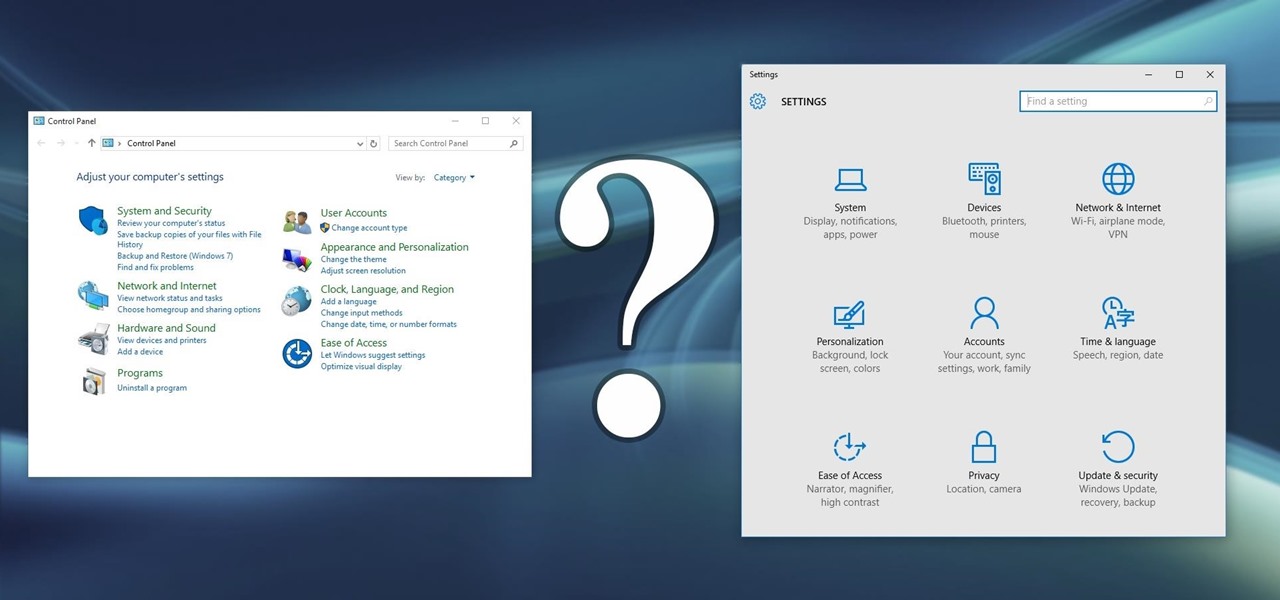
Slowly but surely, Microsoft is pushing more and more options out of the Control Panel and into a new menu simply called Settings. This new Settings menu debuted with Windows 8 and mainly focused on touchscreen-related options, but starting with Windows 10, you'll find quite a few general options residing here as well.

For all of the flak that it catches, Wikipedia is still a great source of information. Contributors take their work very seriously, so the vast majority of information is cited, and the site serves very well as a starting point to learn about a new topic.