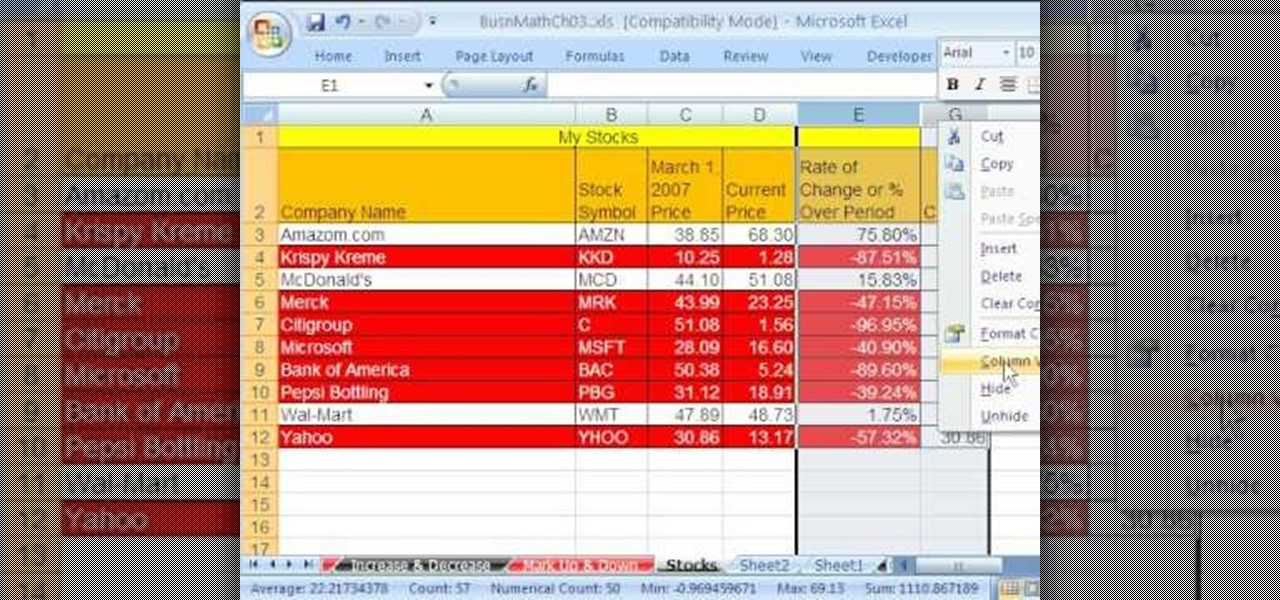
As you might guess, one of the domains in which Microsoft Excel really excels is business math. Brush up on the stuff for your next or current job with this how-to. In this tutorial from everyone's favorite digital spreadsheet guru, YouTube's ExcelIsFun, the 33rd installment in his "Excel Business Math" series of free video lessons, you'll learn how to add current stock prices to a stock analysis table in Excel using a web query.
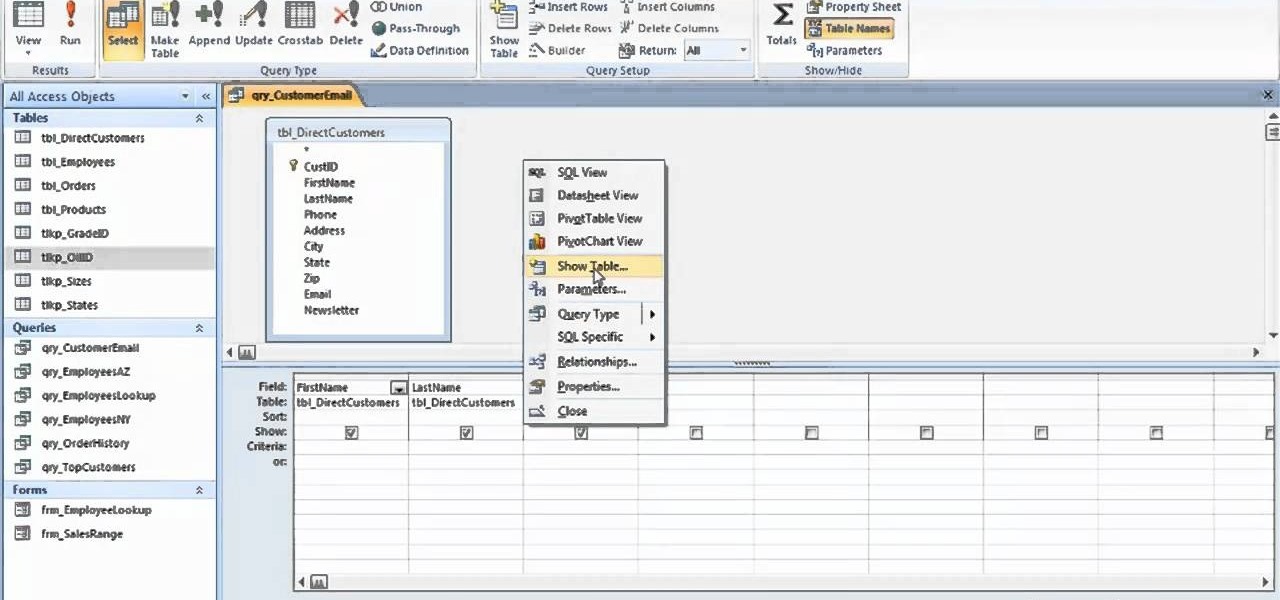
In this clip, you'll learn how to take advantage of the Microsoft Access QBE interface. Whether you're new to Microsoft's popular data management application or a seasoned MS Office professional just looking to better acquaint yourself with the Access 2007 workflow, you're sure to be well served by this video tutorial. For more information, including step-by-step instructions, watch this free video guide.
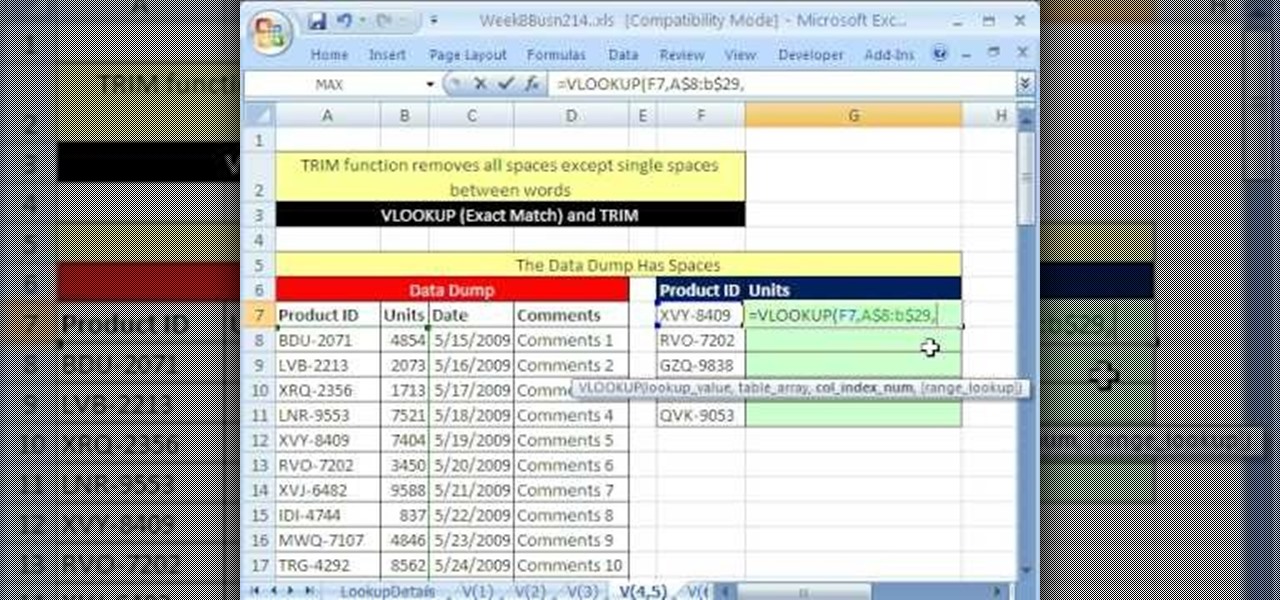
Whether you're interested in learning Microsoft Excel from the bottom up or just looking to pick up a few tips and tricks, you're in the right place. In this tutorial from everyone's favorite digital spreadsheet guru, ExcelIsFun, the 40th installment in his "Highline Excel Class" series of free video Excel lessons, you'll learn how to perform eleven VLOOKUP tricks including how to use VLOOKUP with the TRIM function to remove spaces from first column of lookup value.
Brand new to Microsoft Office Access? This seven-minute free video lessson, which presents a general orientation to using the popular database program, will see that that you're well versed in all of the fundamentals. Learn how to create databases and forms, how to run queries and more. For the specifics, watch this free MS Access video tutorial.

New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 469th installment in their series of digital spreadsheet magic tricks, you'll learn how to use a VLOOKUP query to lookup values for horsepower calculation.
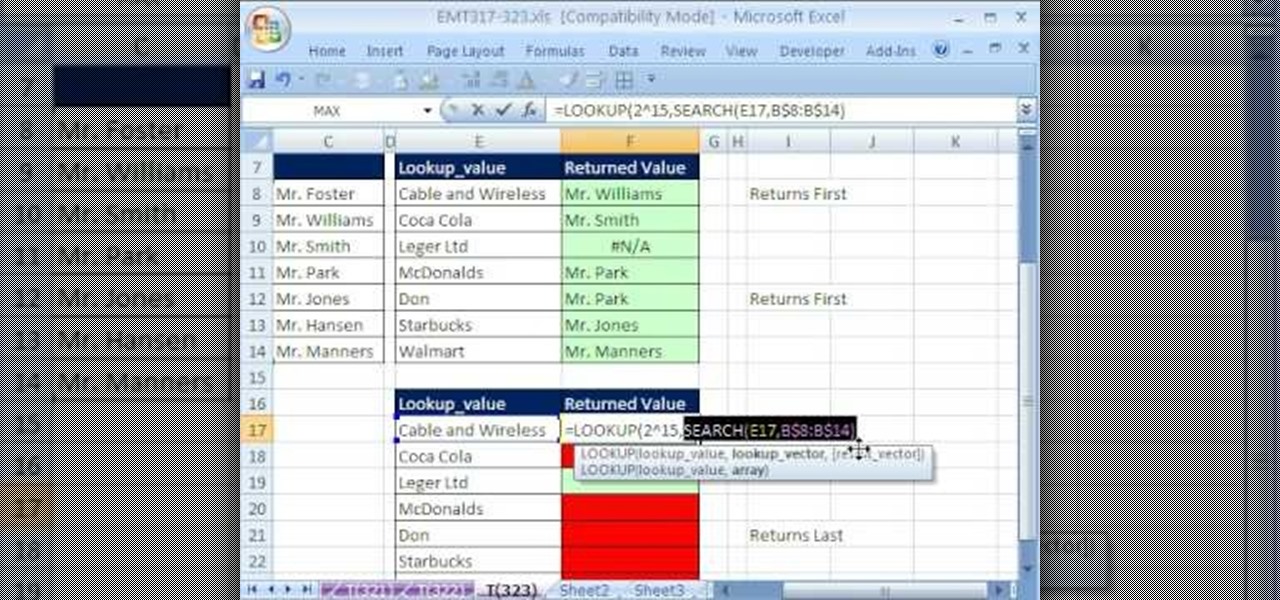
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 323rd installment in their series of digital spreadsheet magic tricks, you'll learn how to run a partial text lookup query using a VLOOKUP function with wild card criteria.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

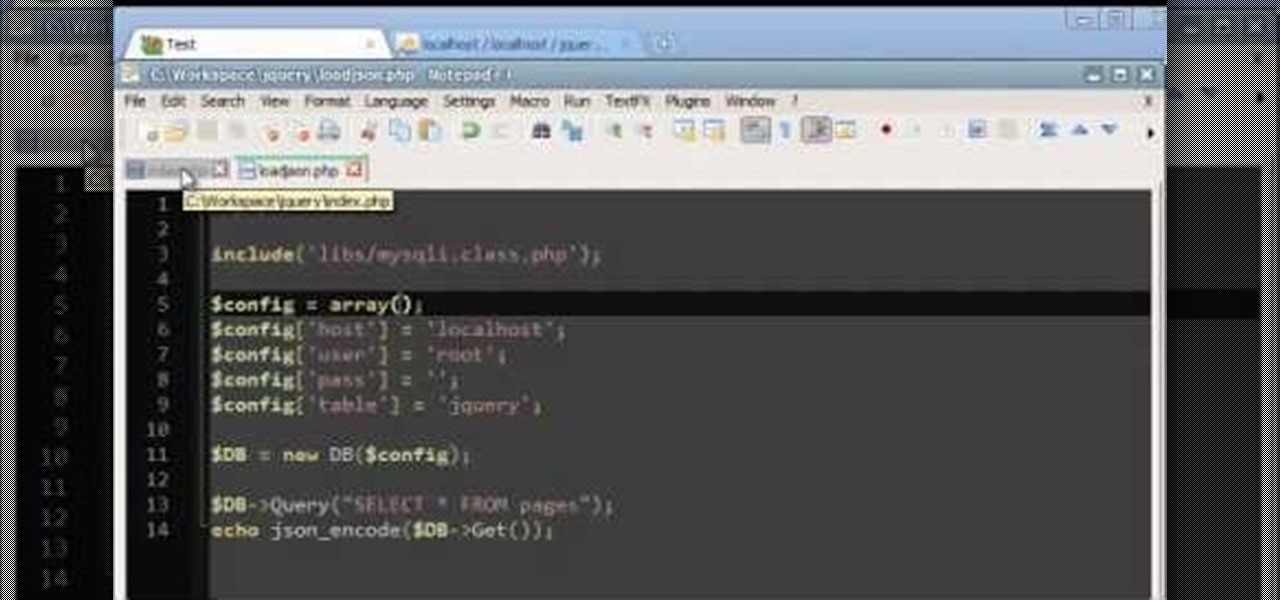
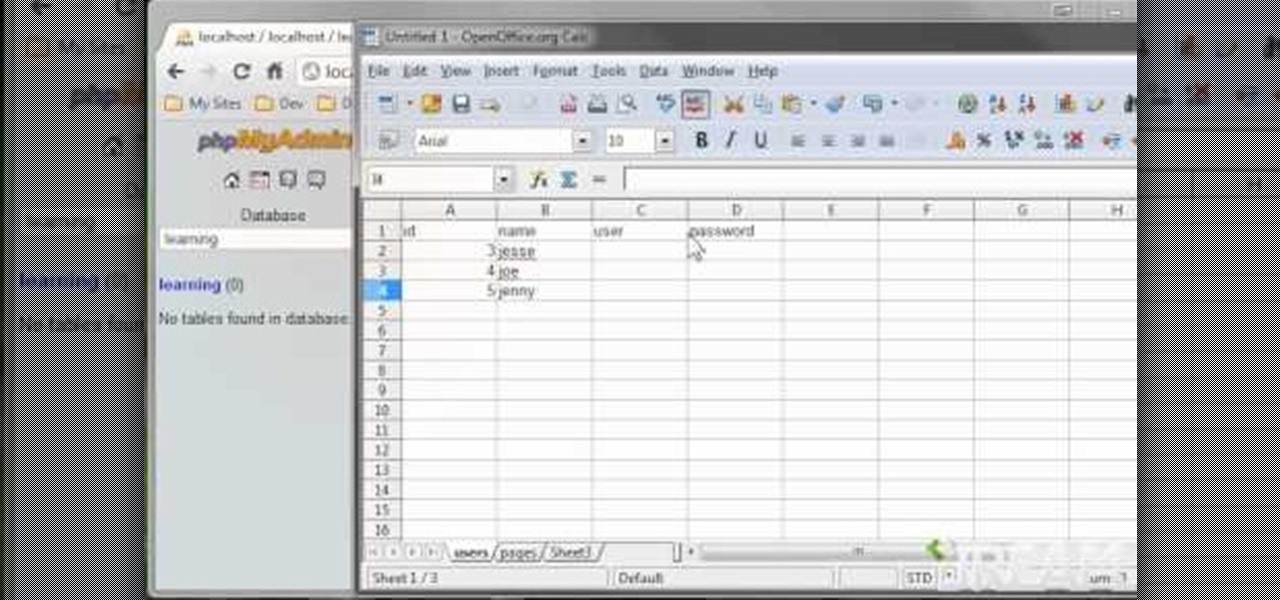
Load JSON (JavaScript Object Notation) data from an existing database file into jQuery by following along with this informative and illustrative video tutorial from JREAMdesign. Here, a database query is used and the results are returned to jQuery via AJAX formatted in JSON.

MySQL is a structured query language (hence the 'sql'), and is an open source language published by Oracle. If you want to learn how to manipulate and use databases (such as customer lists or membership rosters), you will need to learn MySQL.

Looking for an easy way to protect your privacy when using Google Search? With the right habits, it's easy. So easy, in fact, that this home-computing how-to from the folks at CNET can present a complete overview of the process in just over a minute. For more information, including detailed, step-by-step instructions, take a look.

Interested in submitting up to four different Google queries all at once? Let this video be your guide. With GoogleGoogleGoogleGoogle.com, it's easy and this clip presents a complete, step-by-step overview of the process. For more information, including detailed instructions, and to get started using this trick yourself, take a look.

Looking for a primer on how to create and work with lookup queries in Microsoft Office Excel? You've come to the right place. In this free video tutorial from everyone's favorite MS Excel guru, YouTube's ExcelIsFun, the very first installment in his series of Excel lookup formula series, you'll learn how to use the VLOOKUP function to deliver a value to cell.

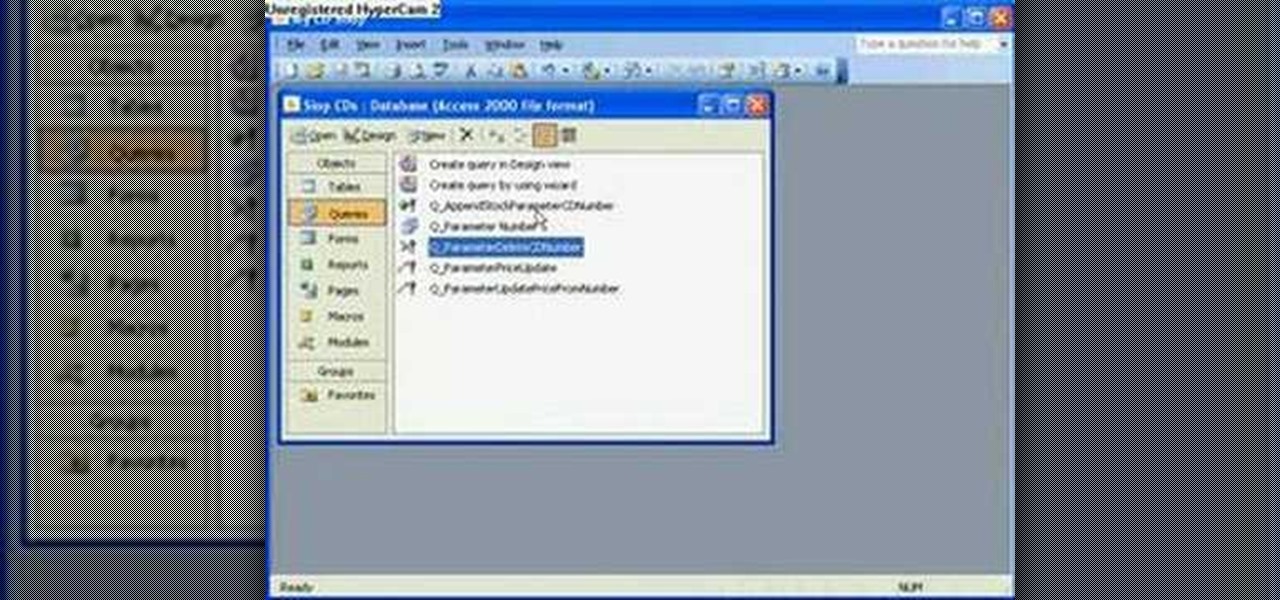
The Microsoft Office Access 2007 relational database manager enables information workers to quickly track and report information with ease thanks to its interactive design capabilities that do not require deep database knowledge. In this Microsoft Access video tutorial, you'll learn about using an append and delete query sequentially using a macro. For more on archiving data in Microsoft office, take a look.

If you're looking to increase the ranking of your website in Google, and so increase your traffic, you'd do well to at least a rudimentary understanding of what Google looks at when considering the relevance of a web page to a given query. This SEO tutorial offers a cursory explanation of how the Google search robot sees, or spiders, your website. Drive more traffic your website with this SEO how-to.

Check out this SEO video tutorial on Google's supplemental index. What could cause your webpage to fall into the supplemental index? There's duplicated content, content taken from other sites, too many query strings in the URL, etc. See what you can do to get them out of Google's supplemental index, with some good search engine optimization.

YouTube Hack! Youtube now uses a new gdata format and doesn't require a developer key. It also added a whole bunch more variables you can attach to the query string making things possible that weren't before.

The key to becoming a competent white hat is knowing how the technology that you are trying to exploit actually works. SQL injection is one of the most common methods of attack used today and also one of the easiest to learn. In order to understand how this attack works, you need to have a solid grasp of ... you've guessed it ... SQL.

Welcome to the first coding tutorial on SQL here on Null Byte. Typo:

Have you tried searching for 4K HDR videos on YouTube, only to get 1080p videos just because the uploader used "4k" or "HDR" in the description? Or have you tried looking for a video about something that just happened, except YouTube's algorithm surfaces established videos first by default, so all the results you get are older than a month? Well, there's a better way.

In this six-part video tutorial, learn how to create an access database. The following six parts go over the following:

Every now and then, we are stuck with a situation when all we have is the perfect lipstick shade, but in gloss! So what can we do to make this lipstick matte instantly? Check out this video to know the process - the results will thoroughly amaze you!

Attention aspiring screenwriters! In this tutorial, learn how to sell that script. You may have written the next Hollywood blockbuster – but unless you can finance the film yourself, you’ll need to sell the screenplay to a producer who can make it come to life.

I have been on Null Byte for a long time, a very long time and. I havent always had an account here, ive like many of you also have, been looking and decided to make a profile to contribute.

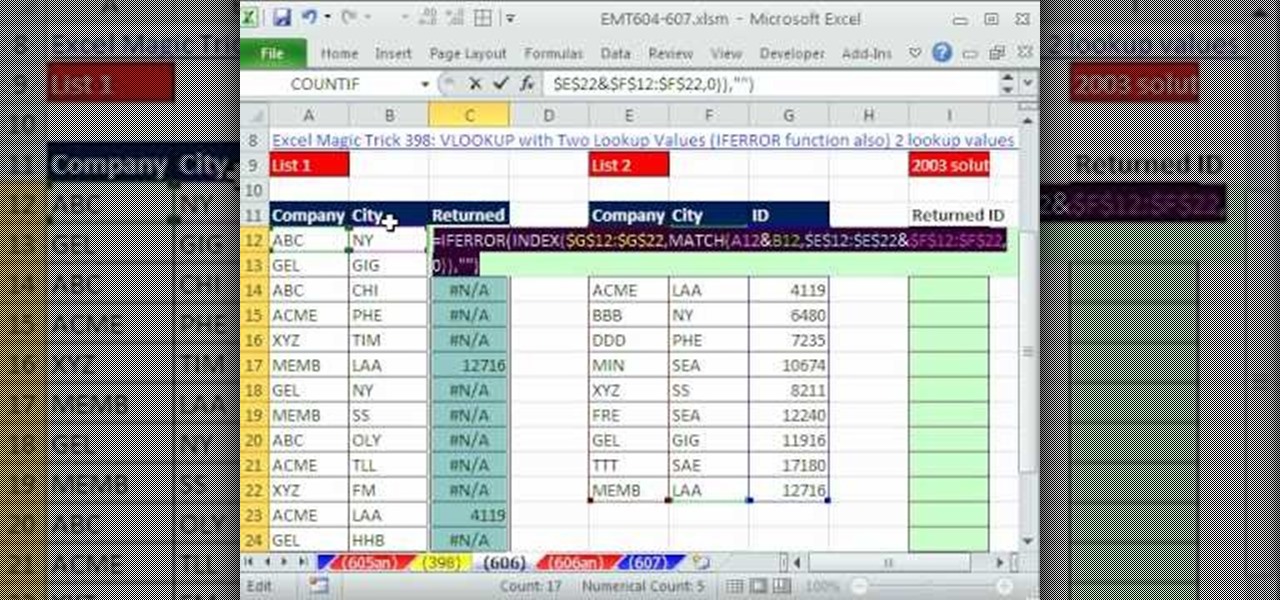
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 606th installment in their series of digital spreadsheet magic tricks, you'll learn how to write a formula that can look up two 2 lookup values using the INDEX & MATCH functions and concatenated (joined) columns for the lookup value and lookup table.

One of the cool things in Windows 7 is the new start menu. It is now possible to add an internet search area to your Start Menu. Instead of searching your computer, you can select a separate option called Search the Internet.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

The Gmail app on both Android and iOS has a powerful search engine that helps you find any email with a few keywords. Even more impressive is Gmail's ability to remember previous search queries for future reference. However, this list of past searches can become extensively long and needs to be reset from time to time.

In my last how-to, we built a man-in-the-middle tool. The aforementioned script only established a man-in-the-middle. Today we'll be building a tool to utilize it. We'll be building a DNS packet sniffer. In a nutshell, this listens for DNS queries from the victim and shows them to us. This allows us to track the victims activity and perform some useful recon.

Now that we have our vulnerable server, it's time to start up BeEF. Getting Started

Privacy features have become quite the hot commodity, emerging from the aftermath of the NSA scandals that rocked the United States this past year. While the NSA has the means to gather information on all of us (regardless of any security software we implement), it doesn't mean that they're the only ones looking.

For Infinity Exists Full Disclosure's first Website Hacking episode, we demonstrate how to exploit a security vulnerability occurring in a website's database to extract password hashes. Sql (Structured Query Language) is a computer language designed for the retrieval and management of data in a system's database. The Attack, known as Sql Injection, manipulates Sql statements before they are sent to the Sql Server, allowing the Attacker to create, change, or retrieve data stored in the database.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and seeing all that glorious data displayed right in the browser. This is when more advanced techniques are needed.

Searching YouTube is tough, because there's a plethora of content, so sometimes i's best to do an advanced search. This is not to be confused with the "search options" available during a YouTube search query, because those are limited to key features of YouTube, but not specific search terms. Much like Google, you can search YouTube via search operators. Many of the same search operators that work on Google work on YouTube also. Filter your results the way you want, not the way they want. You...

SEO is the name of the game. If you want your business or brand to succeed, ranking on the front page of Google is a boon. Getting to the front page of search engines takes work, but it's not impossible when you master SEO best practices.

Microsoft Excel is one of the most powerful programs for modern businesses. By allowing you to manage, sort, and analyze large collections of data, Excel provides an essential service for any company interested in using the power of data science to its advantage.

The Operative Framework is a powerful Python-based open-source intelligence (OSINT) tool that can be used to find domains registered by the same email address, as well as many other investigative functions. This reconnaissance tool provides insight about your target through examining relationships in the domains they own.

Aside from identifying songs with Shazam and using the "Hey Siri" feature while driving, Apple's personal assistant isn't something I regularly use on my iPhone.

Yosemite brought a new, Alfred-like Spotlight search to our Macs, but at times I still find myself wanting more out of it. However, after stumbling upon Flashlight by developer Nate Parrot, I am now able to perform Google searches, look up weather, and even enter Terminal commands straight from Spotlight's search bar.

Welcome back, my hacker apprentices! Although there is a multitude of different hacker types, the one target they all share is the database. I often refer to the database as the hacker's Holy Grail, or the ultimate prize for an effective hack.