Hello everyone! I hope you are having a great day so far. Today, instead of caring about networks we are going to talk about subnetting based on host requirements as promised in my first article about subnetting. Just like in the previous articles we will jump right into the examples because that's the best way to learn.

Hello everyone! How's subnetting going? Did you practice a lot? I hope you did, but even if you didn't we will go through some more examples so you can be feeling confident after reading this article. It's all about that bad boy binary!

If you have a local Trader Joe's, you know first-hand how enchanting the frozen aisles are—almost every item offers the promise of a delicious meal or dessert. (We're always tempted to open the package and eat the cookie butter cheesecake, stat.)

It seems like everything old is new again these days where food is concerned, and that includes the recent renaissance of babka. The name of this rich, rolled yeast bread, with roots in both the Jewish and non-Semitic Eastern European communities, means "little grandmother" in Ukrainian, Russian, and Yiddish.

Instead of suffering through long, dull meetings with your supervisors and coworkers, you can turn those office table sessions into your very own psychological experiment.

I've never had a problem with veggies—we've always been the best of friends—but I do have a lot of other people in my life that have been less than enamored with this basic food group in the past. Some cite the bitter flavor associated with veggies like Brussels sprouts, while others dislike the various consistencies that come with boiling or steaming vegetables such as broccoli or eggplant.

My daughter moved into her first apartment last year, a huge rite of passage in any young person's life. With a mother and two grandmothers who are good cooks (to say the least, in the case of the latter), it's not surprising that she turned to us for some advice about how to improve her own skills in the kitchen. Without question, the single best piece of advice we have given her is to employ mise en place each and every time she prepares a meal.

Smartphones have been a hot button issue around school campuses for several years now—some schools allow them, others confiscate them on sight. But the fact of the matter is, when used correctly, a smartphone can be just as much of a learning tool as a textbook or school-issued laptop.

In recent weeks, some people have been shunned from the Null Byte community because they expressed "black hat" aspirations. This is because Null Byte is the "white hat" hacker training/playground. Although most of us think we know what that means, it does beg the question; "Who and what is a white hat hacker?"

Welcome, in this tutorial we shall we looking at creating a safe(r) way to back up your important files. The contents we will be covering are as follows;

If your iPhone can't last a full day without being recharged multiple times, something's wrong—but it might just be working harder than it needs to.

Your freezer is no one-trick pony. While it does excel at keeping your food fresh for as long as possible, it has a few secret talents it doesn't want you to know about. Like making soda slushies and pyro-friendly smoke mix, as well as reviving dead hard drives. Even better—it can help you do laundry.

Whether you're just getting your first Android, or are already on your fifth annual cycle of picking up the latest flagship, there is always the question of what to do after booting up your device for the first time.

I am very new to Null Byte but I find much of its content and community incredibly interesting. I spent quite a bit of time just chronologically going through the posts and I noticed a common theme in many of the beginner posts. Many people seem to want to know the 'secret' or a paragraph on "How to Hack" and become a hacker in a few minutes. I started off this post as a reply to a question from a beginner but thought it might be beneficial to have for those stumbling across this site.

Welcome back, my rookie hackers!

Firstly let me start by giving credit to Lucid for their guide on Evilzone which inspired this idea, as well as the recent talk of anonymity on here.

With only a few days until Apple Watch preorders begin, and just a couple of weeks until its official release, the biggest question in Apple Land seems to be: "Are you going to get an Apple Watch?"

Welcome back, my rookie hackers! "How can I travel and communicate over the Internet without being tracked or spied on by anyone?" It's a question many Null Byteans have asked me, so I have decided to write a comprehensive article addressing this issue.

Holidays are a time for good food and good drink, but more often than not, we substitute good drink for, well, cheap drink. However, cheap wine doesn't have to be bad.

Audiobooks are great because they require little-to-no effort on your behalf. When driving in traffic, why not listen to George R.R. Martin's lengthy A Feast for Crows instead of repetitive, commercial-laden radio? Maybe it harks back to prepubescent bedtime readings, but having things read to me is a very satisfying experience.

Welcome back, my budding hackers. So many of you are interested in hacking Wi-Fi that I have decided to revisit my Wi-Fi Hacking series with some updated and more in-depth material. I strongly suggest that you look at some of my earlier posts, such as "Getting Started with Terms and Technologies" and "Getting Started with the Aircrack-ng Suite of Wi-Fi Hacking Tools," before continuing here. If you're ready, you can also check out our updated 2017 buying guide here.

Biting into a perfectly ripened piece of fruit is enough to convince you to give up baked goods and plant your own garden. The combination of flavor, juice, and sweetness in a ripe mango, apple, plum, or berry is the stuff of life itself.

As I've explained before, black app backgrounds save you a bit of battery life on your Samsung Galaxy S5. This is because the AMOLED display on your S5 does not have to power pixels or a backlight for portions of the screen that are black.

Hard as it is to imagine, there are people out there who loathe garlic and onions. Some might have allergies or medical conditions like IBS, or are supertasters (i.e. people who carry a certain gene that makes them extremely sensitive to how certain foods taste). Others might just be picky eaters.

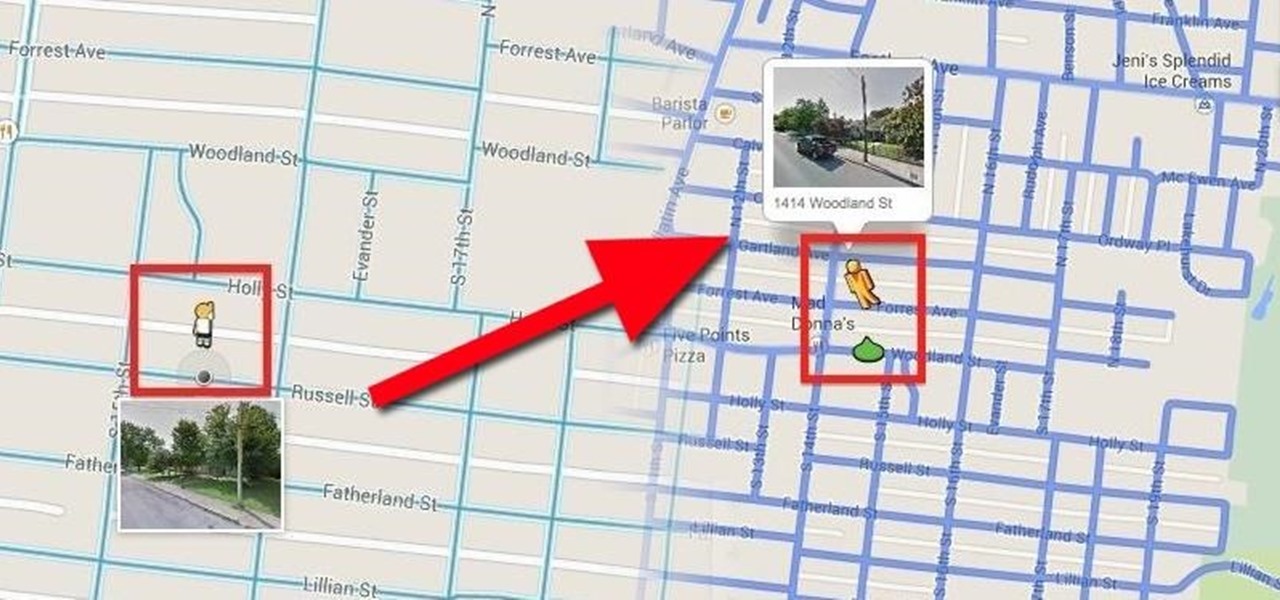
When the Google Maps web app got a massive redesign earlier this year, I was pretty excited to try it out, but it was a fairly disappointing update for me. The slower load times, confusing street view, and bicyclist neglect are just a few of the reasons I don't enjoy it over the old classic Google Maps. The brand new drag-and-drop measuring tool released this week is actually pretty useful, but not enough to change my mind.

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

What separates the work habits of the ultra-productive from us mere mortals struggling to check items off our never ending to-do lists? While the answer to that question is by no means simple, one undeniable factor in their success is a clearly defined, highly organized workflow.

The point of ice in your cocktail is to make it cold, right? Yes and no.

Welcome back, my hackers novitiates! As you read my various hacking tutorials, you're probably asking yourself, "What are the chances that this hack will be detected and that I'll land behind bars, disappointing my dear mother who already thinks I'm a loser?"

The holiday season is almost over, bringing the year to an end, and what better way to end it than with some tonsil hockey from the dime across the room on New Year's Eve?

The Nexus 5 is the current Google flagship packed with the latest and greatest of all things Android, but what if you never made the leap from your Nexus 4 smartphone?

With all of the new features and third-party apps out there making Android better and faster every day, it's quite frustrating to me that keyboard advancements remain relatively static.

One little known feature on Android devices is TalkBack, which provides you with spoken feedback and vibrations in order to help you navigate your device. Obviously, if you're not blind or visually impaired, this isn't a feature you're likely to use.

The iPod changed the music and electronics industries when it was first introduced way back in 2001. It is credited with ushering in the age of "connected devices," and has held a huge market share of around 70% for years. At the height of its popularity, the iPod made up almost 50% of Apple's revenue. Now that the smartphones and tablets we use every day have the ability to store and play music, the iPod's glory days are over. Nevertheless, there are millions of people who still use them, an...

Facebook just released its new "home on Android" last Friday, appropriately called Facebook Home. Taking a cue from Amazon's Kindle, Home serves as an "operating system" that runs over Android.

TouchDevelop is a browser-based programming tool that allows anyone to build your own Windows 8 apps directly from any touchscreen device, including iPad, iPhone, Windows Phone, Android, PC and Macs. Once the script is created and the app proves to work, it can be placed in the Windows Store for free or purchase.

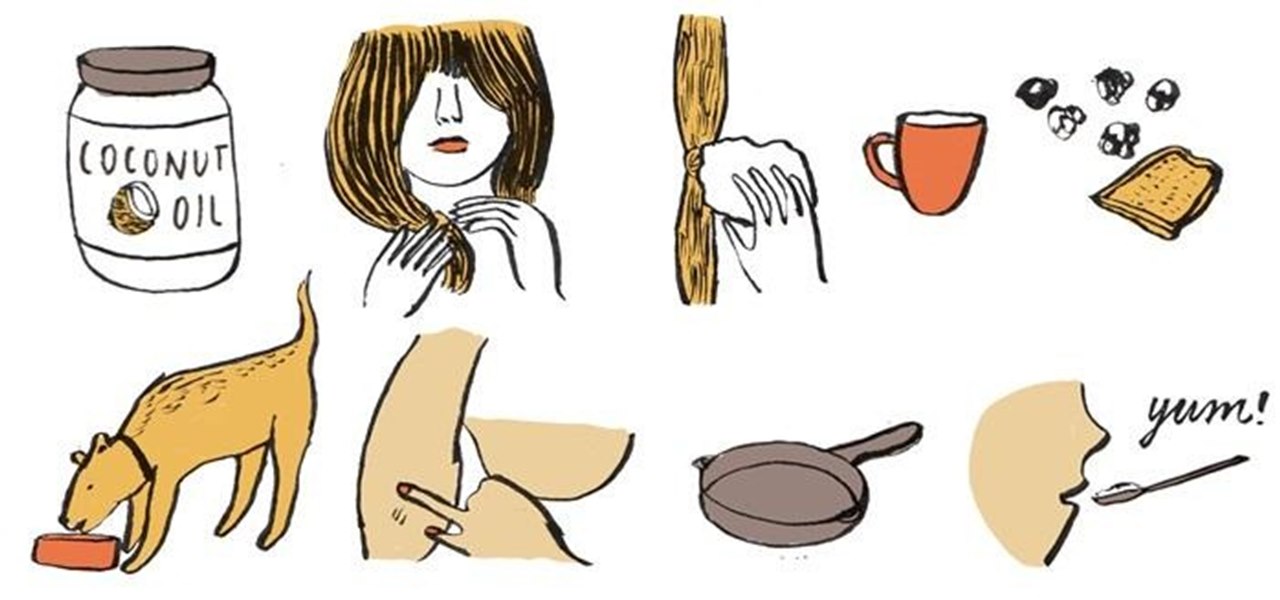
What can't coconut oil do? This edible oil, extracted from the copra or meat of a coconut, has done what most other food, beauty, and health trends have not: demonstrated real lasting power. Indeed, the "superfood" continues to make headlines, with its many uses the subject of debate, study, and fervent support. From the obvious (cooking) to the less so (home improvement), there are likely many coconut oil uses you're not yet aware of.

Steampunk is a tremendously interesting phenomenon because of its reliance on science fiction, and fiction in general. Steampunk can arguably be broken down into two categories: the fiction, and the aesthetic. Sometimes these categories cross over, but they're often more distinct than most people suspect; that said, the aesthetic is firmly based in works of fiction.

It's September 1st, 1859, and the Earth looks more or less like something out of an apocalyptic movie or Sci-Fi novel. All communications have failed, it's so bright outside at midnight that people are getting up and making breakfast, and people all over the world are seeing auroras. The solar storm that produced the electromagnetic pulse and caused all this mayhem is known as the Carrington Event, and storms like it happen about about once every century.

There are lots of people who want to stay anonymous online, and lots of reasons they want to do this. Staying anonymous on the internet isn't easy, and it's probably possible to trace almost anyone with enough time and resources. A lot of people think that they're completely secure with just one method of cover. For example, a lot of people thought anyone using the Tor network was nearly untraceable, but then things like this often cast doubt on just how secure these networks are. Unless you ...