
How To: Post to Null Byte [4.10.15 Revision]
Hello readers, and welcome to Null Byte. Before we start, for those of you who may not know me, my name is ghost_; I'm a relatively active member of our community and have been around for a while.


Hello readers, and welcome to Null Byte. Before we start, for those of you who may not know me, my name is ghost_; I'm a relatively active member of our community and have been around for a while.

Have a super secret spy communication you'd like to send out, but don't have the funds to hire your own trusted operatives to deliver the message? Then stick to what you're used to—email it. SafeGmail is a browser extension that allows you to send encrypted emails right through your regular Gmail account. While this may seem a bit unnecessary for most messages, encrypting your email can definitely be useful.

Amazon Web Services (AWS) offers over 200 services, including networking, computing, storage, analytics, blockchain, mobile, and developer tools. Not surprisingly, numerous companies rely on AWS's massive infrastructure. Instead of building their own server farms, they rent space and computing power from AWS's secure and robust system.

Who's ready to let future Facebook augmented reality smartglasses read their brain? Well, ready or not, the tech giant is making progress in the area of brain control interfaces (BCI) by funding research.
With the reveal of Magic Leap's developer documentation last week, many questions have been answered—and several new ones have been raised as well. But since the Magic Leap One (ML1) isn't simply called the "Leap One," these are questions that the company probably has no interest (at least for now) in answering. Understandably, Magic Leap wants to keep some of the "magic" under wraps.

If you've never played Cards Against Humanity, it's time to get initiated. Originally funded through Kickstarter, the free to download card game is basically an obscene version of Apples to Apples.

Mystery is a tricky thing. Used correctly, it can give onlookers the impression that wondrous and perhaps valuable things are afoot. However, once the veil of suspension of disbelief is removed in any significant way, that same mystery can quickly turn into not just skepticism, but outright anger at what may have seemed like an attempt to dupe trusting onlookers.

Look, tests are no fun, and doing poorly on them is rarely an option. Whether you're studious or a slacker, everyone needs a little boost now and again. While students have found ways to cheat as long as tests have existed, the invention of smartphones has greatly enhanced the potential to get ... creative.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

If you've been to a convention of any sort before, you know that there are good and bad panels, and that their inherent goodness or badness often has little to do with the actual content being discussed. That's because giving a panel is a skill that not everyone has. However, it is a skill that everyone could have! In this article, I'll tell you how to give a good panel on practically any subject. Image by Shannon Cottrell

Now this is a spell! In The Elder Scrolls V: Skyrim, there exists a spell that turns iron into silver, and silver into gold. That's the best thing! And it's pretty easy to get, too.

Kids love sports drinks, but are they healthy for them? This video answers that question, and dissects all of the information pertaining to the diet, nutrition and metabolism of a child playing sports. Healthy eating is important for any sports player, but there are some special considerations for young children. Variety is important, but you need about 40 different nutrients to keep the kid playing well. And believe it or not, chocolate milk is actually one of the best recovery foods.
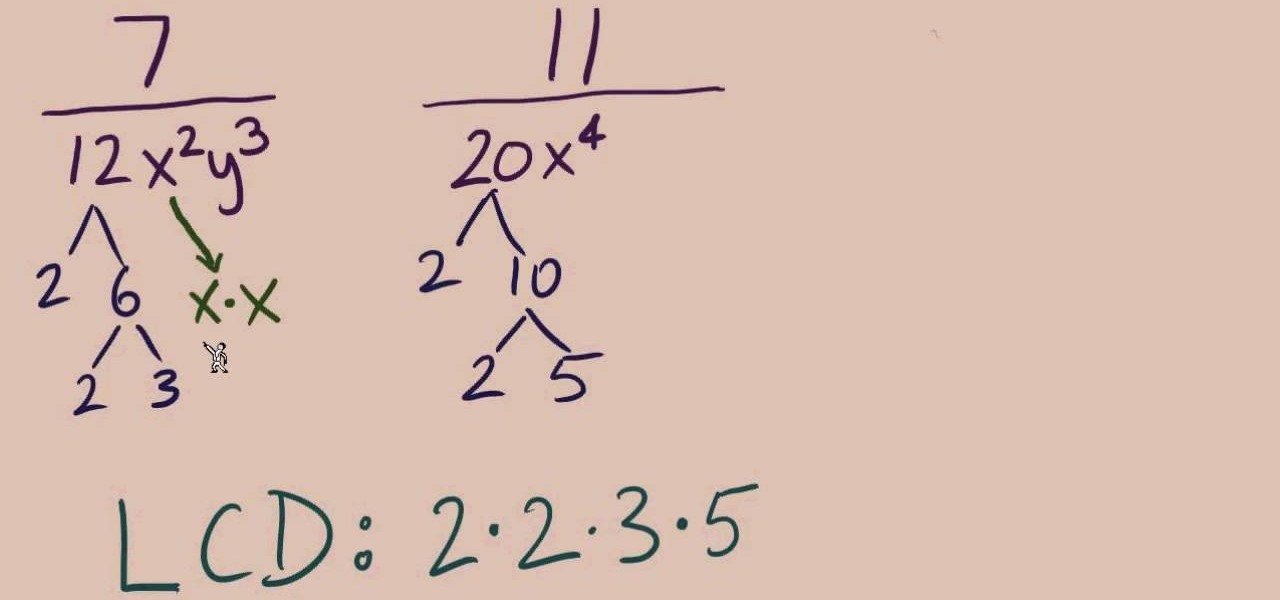
This series walks you through the steps of finding the least common multiple in rational expressions. This excellent video shows you a clean board, with the instructors voice showing exactly what to do. Don't fret, any question you may have, will be answered. Watching this video will make you feel like your back in the classroom but rather comfortably from your home.

This video walks you through the steps of multiply and divide rational expressions. This excellent video shows you a clean board, with the instructors voice showing exactly what to do. Don't fret, any question you may have, will be answered. Watching this video will make you feel like your back in the classroom but rather comfortably from your home.

This series walks you through the steps of adding and subtracting rational expressions. This excellent video shows you a clean board, with the instructors voice showing exactly what to do. Don't fret, any question you may have, will be answered. Watching this video will make you feel like your back in the classroom but rather comfortably from your home.
Here is the answer to the question that a lot of people have asked lately, "How does one install Linux Ubuntu on Windows without causing any modifications in the original boot record of the PC?" Software wiz-kid Matt Hartley walks the viewer through a step-by-step process of installing Ubuntu on a Windows-driven computer. The secret is to download Ubuntu to a CD instead of downloading and installing it directly on the hard drive of one's PC. This also ensures that the Ubuntu is easy to delete...
This technique can be used to write answers for a question asked in the exam or can be used to write a paragraph while applying for a scholarship or while writing a brief letter. The main thing to be considered while writing the paragraph is having an outline, all we need to do is prepare an outline before starting the paragraph. First write the "main idea" that is to be delivered, then the main idea should be supported with additional details, there can be two to three additional points to s...

Filmmakers beware... or more importantly, cinematographers beware... boring setups and unpleasing camera tricks can ruin a movie. Check out this helpful video tip from Focal Point Technologies on how to use zoom and dolly effects in your film.

You'd kill to sleep, but even a quick rest is out of the question when you're on the job. If your performance is affected by lack of ZZZs, check out these ways to relax while you are working without falling asleep on the job.

How to talk to women is a question that every man faces at one time or another. Men are looking for an inside on communicating to women. Whether you are looking for a date or just a friendship, just be yourself.

Learn how to upgrade your RAM memory for a typical laptop or notebook computer. In this example, we show you how to install memory in a Compaq Presario laptop. Upgrading your laptop memory is easy to do and an inexpensive way to improve the performance of your laptop.

Learn how to add memory (RAM) to a typical desktop computer. In this example, we show you how to install memory in a eMachines Desktop. Upgrading your desktop computer memory is easy to do and an inexpensive way to improve the performance of your desktop.

Watch this video sequence and learn how to ask someone if they dislike or like something and also how to respond to such a question.

Grilled or breaded? When asked this question at most fast food joints or restaurants most of us would answer "breaded" because of the oil-soaked, fluffy goodness, but in truth grilled chicken is a LOT healthier for you.

While there is a lot to love about Apple's latest suite of iPhone models, the real draw comes down to the cameras. The iPhone 11, 11 Pro, and 11 Pro Max all have killer rear camera systems, but the front camera was also improved. Apple claims Face ID works at more angles than before in these models, which begs the question: can you unlock your iPhone when it's flat on a table?

In just a few weeks, on May 29, the annual AWE (Augmented World Expo) conference will take place once again in Silicon Valley (Santa Clara, California, to be exact).

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.
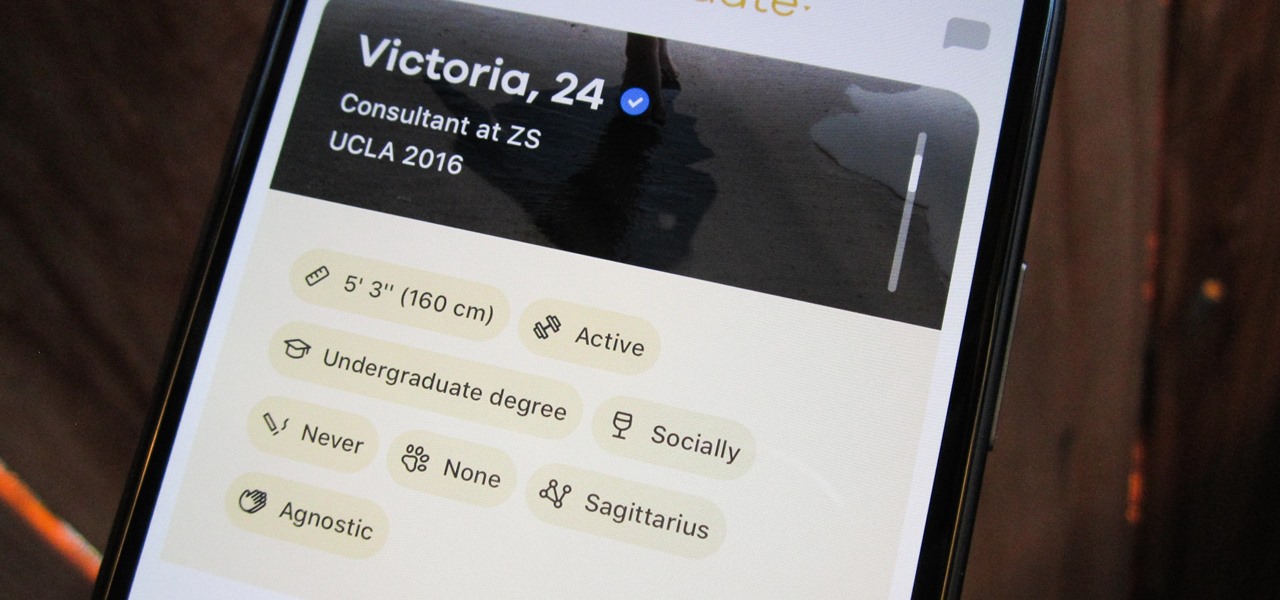
Despite Tinder's tremendous popularity, Bumble has carved out a billion-dollar business by focusing on women (they message first), simplicity (ice breakers less wordy than OkCupid), and relationships past romance (friends and prospective jobs). Now they're diving into customization, with filters that allow you to pore over prospective matches by height, religion, education, politics, and more.
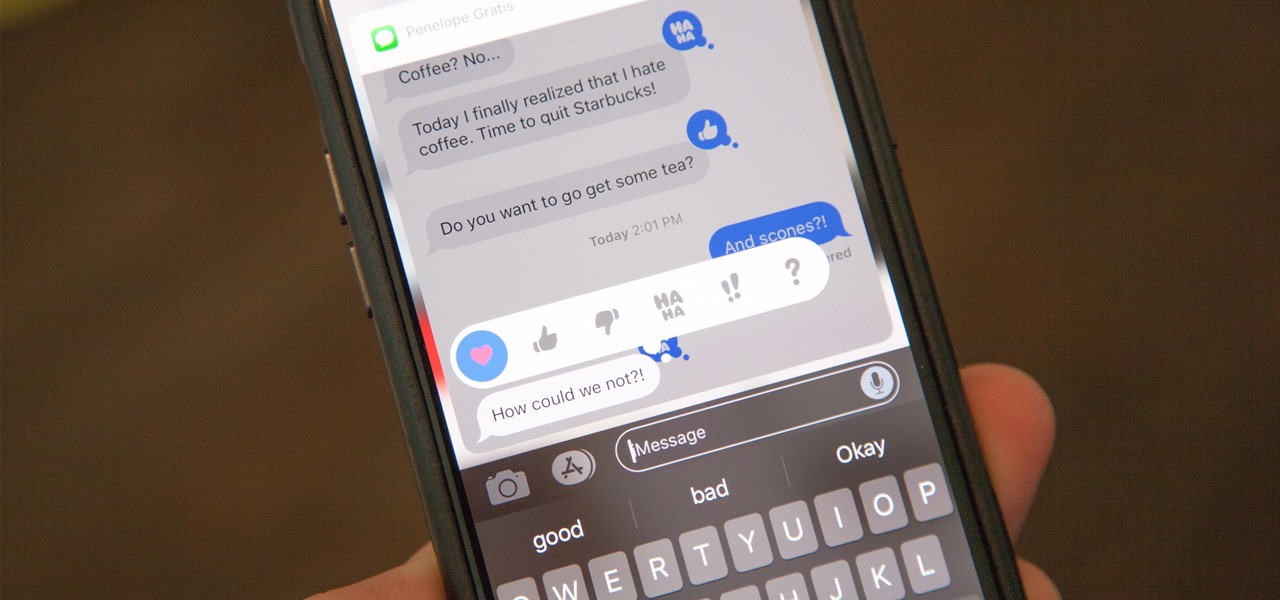
Ever since iOS 8, Apple's quick reply feature had made it easy to respond to messages without leaving the lock screen or whatever app you're currently in, but you can't utilize all of Messages features when responding this way. You can't add photos, use iMessage apps, record audio, choose effects, or send handwritten messages. You also couldn't use Tapback, but iOS 12 just changed this.
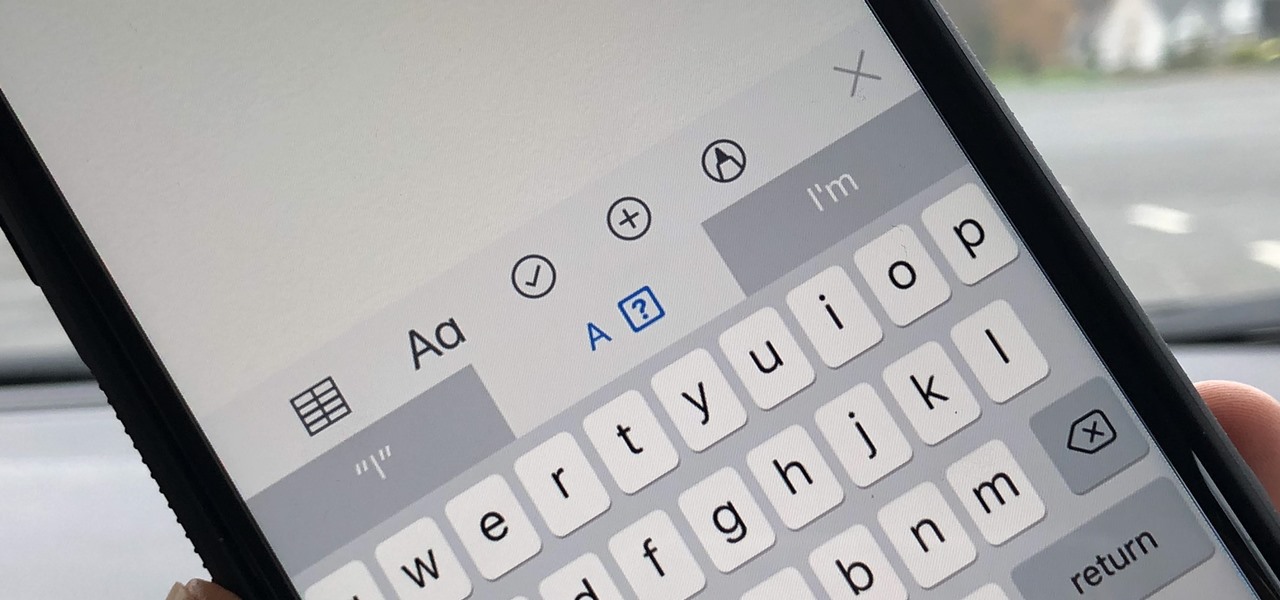
There's an annoying bug in Apple's latest operating system for iPhone, iOS 11, that autocorrects the lowercase letter "i" by itself (which usually turns into a capital "I" pronoun) into a capital "A" followed by a strange question mark in a box "[?]" symbol. There is now an official patch for this bug, as well as a workaround fix if you don't want to update yet.

When will the drama end? The lawsuit between Waymo and Uber is back in the news with no signs of stopping. Today the court denied yet another request from Uber to shield itself with the fifth amendemnent, securing a small victory for Waymo.

Samsung and Apple are back in court, but this time it's not just money at stake. The Supreme Court's decision could have a far reaching effect on patent law and innovation in design.

If you like having Siri available to answer a quick question every now and again but don't want everyone who picks up your iPhone to also have access to your personal assistant, there's an easy way to disable her from working on your iPhone's lock screen. This is also something you can do if you're always activating Siri accidentally in your pocket.

With Passover soon upon us, many Jews are dreading a week (or eight days for Conservative and Orthodox Jews) of making matzo, the staple of their diet. Matzo is also known as "the bread of affliction," and I'm pretty sure it's because by day three or so you're convinced that matzo is the 11th plague.

My first ever post on here was 'Keeping your hacking identity secret' and it did very well, and its not something I see here on null byte. So read along.

Welcome back to control structures, part two featuring the three types of loops. Here we go! What Is a Loop?

!!!WARNING!!! !!!Because of misleading informations please wait for the new post about this same argument instead of reading this post!!!
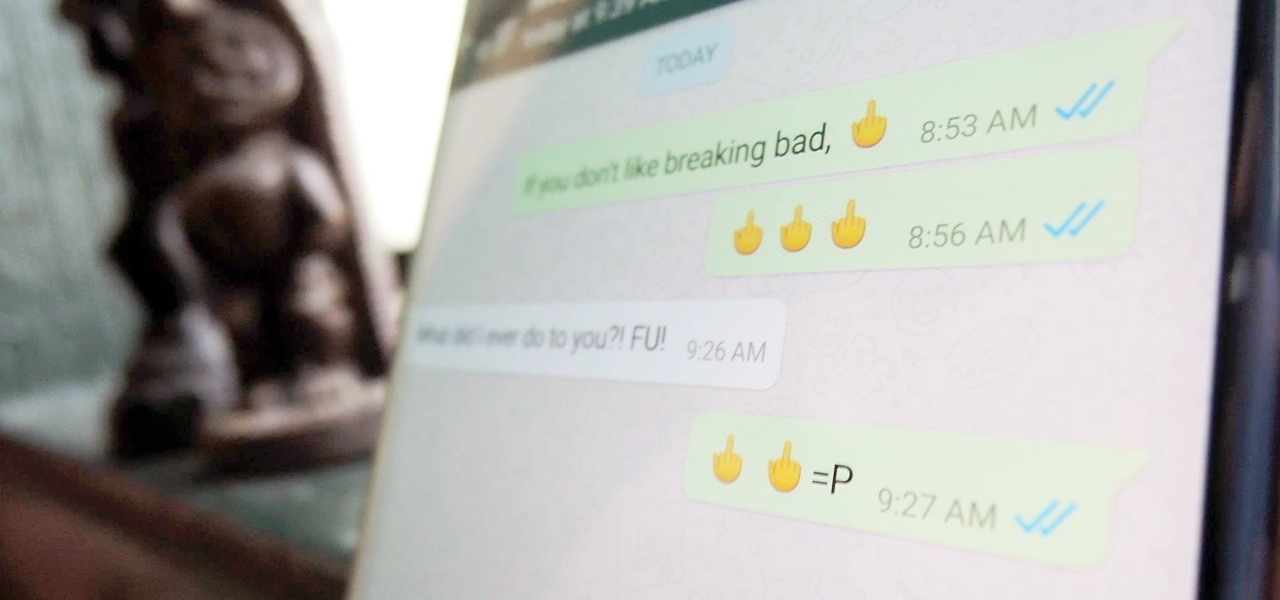
Hidden deep in WhatsApp's emoji database is a middle finger emoji, and there's a really easy way to use it. Much like Spock's "live long and proper" Vulcan salute, this one can be used simply by copying and pasting the emoji from our tweet. Note that the emoji, for now, does not display properly on iOS devices, but it can still be sent. So if you're in a conversation with an Android or computer user, they'll see it just fine.

If you lend someone your phone, even if it's just for a second, there's a chance they can enter an app and see something you'd rather they didn't. Whether it's a personal email or a private photo, there are plenty of reasons why you'd want to keep snoops out of certain apps.

My friends can be pretty shitty sometimes, but they're my friends nonetheless. On various occasions, they've secretly taken my device and made me look foolish by posting crude and embarrassing posts to Facebook, Instagram, or Twitter. With friends like these, who needs enemies, right? And it's because of these types of friends that we need to substantially upgrade the app security on our devices.