Investing is like exercise—we all know we should be doing more of it, but we often just can't find the time. I mean, really, who's got the hours, inclination, and skill to pour through volumes of data and put together a balanced yet sophisticated portfolio of investment vehicles tailored specifically to optimize their returns while mitigating potential risks. Not me, that's for sure.

Guardians of the Galaxy wowed moviegoers this summer with its sassy, strong team of intergalactic superheroes. From Groot, the ever-growing tree, to Rocket, the rough-around-the-edges raccoon, the film had an unending supply of unique characters—but no one stood out as much as Gamora.

Considered a huge gamble on the part of Marvel and Disney due to its seemingly small fan base, Guardians of the Galaxy turned out to be well worth the risk, nearing $800 million in world-wide box office numbers. Many may not have known about the comic book prior to the movie, but you can definitely count on plenty of Guardians of the Galaxy costumes this Halloween.

In today's world of ordering food from your PC or hailing a cab with an app, it almost seems archaic when we have to actually use our vocal cords to contact a local business. It sure would be nice if we didn't have to use our smartphones as, well, you know...phones.

Quickly jotting down grocery lists, recommended books, phone numbers, and addresses, among other things, has been a pretty straightforward process on an iPad or iPhone. Through the Notes app, you can enter information and have it seamlessly synced across all of your iOS devices, making access to them simple, quick, and universal.

If you've already read the first part exploring what geniuses actually eat as opposed to what the rest of us are told to eat for brain health, you've noticed that there are some big discrepancies. Instead of favoring healthy, wholesome foods high in antioxidants, lots of high-achieving types tend to go for caffeine, sugar, and processed foods. One notable health habit practiced by many: eating breakfast.

Certain files contain sensitive data that you don't want being shared with just anybody. Even still, it would be nice to be able to send such a file to a certain confidante without fear of it falling into the wrong hands.

You hand your iPhone to a friend to show them a picture. What happens? They swipe. Left, right, it doesn't matter. You don't remember what lies in either direction of the photo in question, and you don't want anything compromising exposed to the unassuming viewer. Luckily, Apple includes a safety net in iOS to prevent this scenario from ever happening, so long as you set it up ahead of time.

There are a lot of manipulative people out there, but you don't have to let all of them push you around. It's time for the tables to turn.

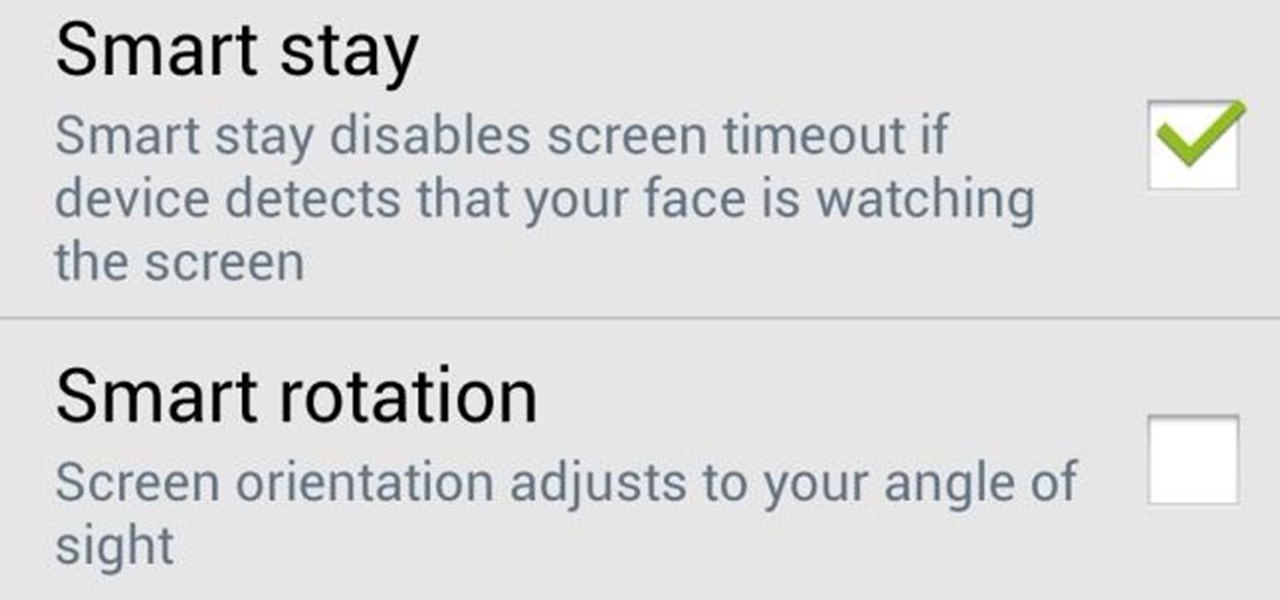
Samsung catches a lot of flak for all of the "bloatware" it preinstalls on its Galaxy line of devices. Many users complain that "TouchWiz," Samsung's custom Android skin, causes lag with its overabundance of features. But some of these features can actually be pretty handy, like Multi-Window Mode or Milk Music.

Not too long after getting a new device, you probably start installing any and all apps that seem fun and interesting. But after having used the device for a considerable period of time, those extraneous apps begin to take their toll.

Admit it, you wish Siri was on your Mac, and so do I. She stole my heart on iOS, and now every time I open up my MacBook, I feel something missing. Wouldn't it be great if we could, I dunno, hack Siri onto our Macs? Yeah, it would!

Screen timeouts serve mostly as security measures and energy savers, but they can also interrupt you when you're reading a book or editing a document. There is no built-in way to manage screen timeouts on a per-app basis, but if you've got root access, you can do just that using Never Sleep from Android dev Hamzah Malik.

Pallets, Pallets, Pallets. You have to love them! How to build an outdoor play kitchen for the kids using old pallets and recycled / reclaimed wood. I came up with the idea after seeing how my young son loved playing with the one at childcare. Pallet projects and Pallet Ideas are never far from my mind so l couldn't wait to get stuck into building my play kitchen.

Look away from this screen and try to remember the sound of your childhood hero's voice. Did you do it? Do it again, and this time pay attention to your eyes.

Facebook rolled out a new feature that lets your friends ask you about your current relationship status. This is great feature if you use Facebook for finding hookups, but if you use it mostly to connect with family and friends, a bunch of questions about your dating status can get annoying real quick.

The Galaxy S5 is a flagship-level device with some pretty advanced features, like its 4K video recording capability, water-resistant casing, fingerprint sensor, and KitKat running out of the gate.

With the emergence of rumors that Amazon, Google, and Samsung are all making their foray into the gaming console market, it's a possibility that our Android-powered mobile devices might become tools that play a central role.

Baking powder and baking soda are two staples almost everyone has around that seem to last forever. But a lot of people don't know that they eventually start to lose their potency after enough time on the shelf. If you can't remember when you bought it, it's probably time for a new box.

What kind of music do you like? It's a classic first date question that reveals so much about the person answering, but when it all comes down to it—everyone likes or listens to music. We may each have our own unique tastes and interests, but music is usually something almost anyone can get behind.

Ever since the FBI took down the Silk Road and Dread Pirate Roberts last month, many questions have been raised about whether Tor still provides anonymity or not, and if it's now broken. I'll try to address that question here today succinctly from multiple angles, keeping it as simple and plain-language as possible. The Closing of Silk Road

The Nexus 7 is a huge jump in screen size when coming from a phone, but obviously this tablet is still smaller than some of the major players such as the Nexus 10, Galaxy Tab, etc. One way to squeeze out a little more space is to eliminate the navigation and status bars.

Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.

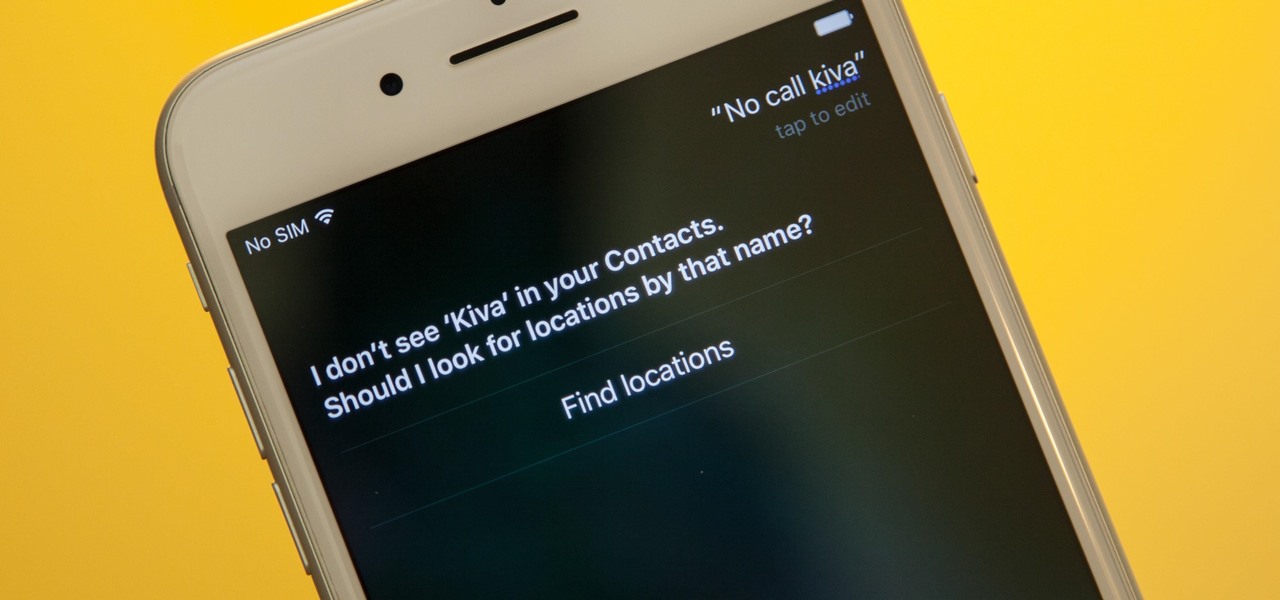
Siri makes it easy to call almost any contact on your iPhone with just a quick verbal command. I say almost because counterintuitive name pronunciations such as Caoimhe, which is actually pronounced "Keeva," will confuse the hell out of Siri. Luckily, there's a way to get Siri to understand pronunciations for the tricky names in your contact list ... it just takes a little grunt work on your part.

If you're studying human anatomy (or have ever visited a doctor's office), you're no doubt familiar with those plastic anatomical models with removable pieces meant to teach the different parts of the body. Before those, there were illustrated pop-up books. If you need to know the difference between the latissimus dorsi and the multifidus, you're probably better off sticking with your textbook diagrams. But if you prefer a more artful approach (and have a lot of time one your hands), this pap...

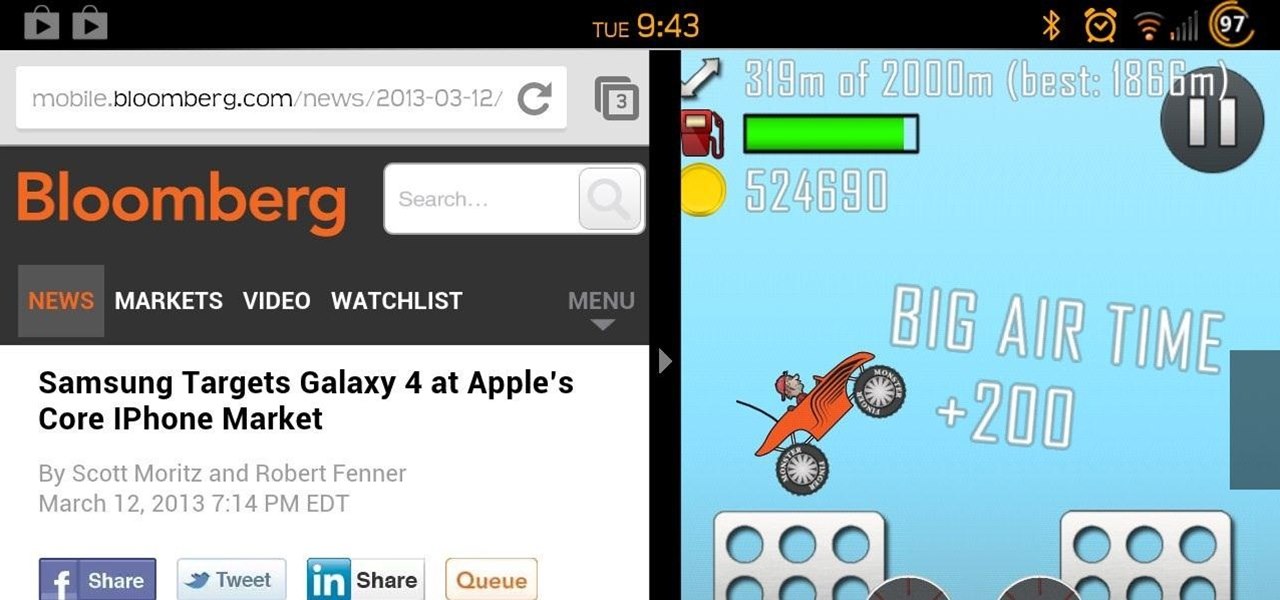
While many of the U.S. carriers have updated their Samsung Galaxy S3 devices to Android 4.1.2 already, one major absence from the upgrade is Samsung's Premium Suite. One of the coolest features from the Premium Suite is Multi-View, a function that lets you truly multitask by running two apps at the very same time—right next to each other. As you can see above in the left image, I have both Pandora and Spotify running. Why? Because why not?!? On the right, I have YouTube on top and Maps on the...

A new leak from GSM Israel on March 6th shows some telling screenshots of the U.S. variant of the upcoming Samsung Galaxy S4, some of which confirm features seen in the leaked 4.2.1 ROM for the Galaxy S3.

The lovely Kato of Steampunk Couture has gone hardcore. For those who prefer to exercise their imaginations a bit more, Voila! Veronique Chevalier in Gearhearts Steampunk Glamour Revue- click here should do... A recent kerfuffle unfolded on facebook's Steampunk Revolution group when a discussion was started by Steampunk R &D''s very own Austin Serkin on the subject of Kato's new foray into steampunk porn, which was, ahem, examined in detail. (Well, figuratively, not literally, since her websi...

As you have no doubt observed, brothers and sisters do not mate. While they may find one another attractive, they find the notion of sex with one another repulsive. This is because a child produced by siblings has a high probability of sharing the same recessive genes, and recessive genes are often harmful unless coupled with dominant genes.

When most people think of stained glass, the first thing that comes to mind is a church, but it's become more popular in home decor as well. The biggest downside is that high quality stained glass pieces can be insanely expensive—and it's not an easy project to take on yourself.

Want to secure your home? There are plenty of ways to go about it. You can make your doorbell send you a text if someone rings it while you're not home, or build a motion-triggered security camera. Even better, you can beat potential crooks at their own game by installing a door they can't even find.

The long standing popularity of 4chan has been due to the entirely anonymous setup. The site's anonymous community and culture has provoked media attention, in turn inciting larger audiences. On the other side of the spectrum is Facebook—popular for its connectivity and easily identifiable names. With the brush of keyboard stroke, you can be connected with your entire high school class in a matter of seconds.

The vast majority of people involved in Steampunk are interested in history but, like with science, there's something about history that we don't talk about very often: The holes.

In yesterday's tidbit, we learned that across the planet women seek material wealth in their mates. This stems from our hunter-gather past in which females depended on male hunters to provide them and their children the meat necessary to support their large brains.

Do you ever wonder how all these celebrities continue to have their private photos spread all over the internet? While celebrities' phones and computers are forever vulnerable to attacks, the common folk must also be wary. No matter how careful you think you were went you sent those "candid" photos to your ex, with a little effort and access to public information, your pictures can be snagged, too. Here's how.

Before lead was removed from gasoline, lead from car exhaust got into the air, was breathed in by kids, lowered their IQs, and increased crime rates (there is a very strong correlation between IQ and criminal behavior).

I seriously cannot get enough of these sweet ass emblems for Call of Duty: Black Ops 2. Thanks to the new emblem editor, there's just so many possible designs to be made.

Roughly five million years ago, humans split off from chimpanzees, who had in turn split off from gorillas five million years earlier.

'Tis the season to be jolly, and what's more jolly then unleashing a torrent of bullet fire on the opposing team using a LMG emblazoned with a Santa Claus emblem?

Everyone has a favorite superhero. It doesn't matter how old or young you are, there are probably some heroic characters out there that you wish you could be. And in Call of Duty: Black Ops 2, you can be them, as long as you've got some emblem editing skills.