Nicole Mead and Vanessa Patrick had a bunch of dieters, one at a time, sit and watch a movie, each with a bowl of candy next to him. Some were told they shouldn't eat the candy, while others were told that they should hold off during the movie but could have the candy later.
Sitting in the Powell Library at UCLA was a constant thing for me. Directly after class, I would streamline my way there to study all night until my eyes shuttered to sleep. For the most part, my classes and professors managed to keep my studying online via PDFs, emails, long essays and journal entries.

When subjects are asked to watch a movie and not display emotions (say, a comedy without laughing, or a tearjerker without crying), they evidently use up glucose in particular areas of their brain in a way that subjects who are free to react however they want do not.

A hidden feature residing in Mac OS X Mountain Lion is the ability to view and also reply to your friend's tweets through the Contacts application, previously known as Address Book. The only way to do this, though, is to provide your Twitter account login data to the Contacts app. To integrate your Twitter, just go to System Preferences, then click on Mail, Contacts & Calendars and choose Twitter. Put in your Twitter login information and then click on Update Contacts. Twitter will use your e...

If you've decided to forgo the super heroes and television characters and go medieval this year for Halloween, David J. Guyton has just the thing to take your costume over the top. To promote his new book, he built this awesome gauntlet armor—and made a step-by-step tutorial. David's is made of brass because it's meant to be a prop (would work well with Steampunk), but if you wanted to make it legit, he suggests trying steel instead. He started with a paper template, which he used to trace th...

If you use apps on your smartphone, chances are you have no idea what those apps are doing with your information. Just this year, there have been several scandals involving apps transmitting user data, like Path uploading users' entire address books onto its servers, HTC's Security Flaw, and Brewster exposing users' personal information (even Ashton Kutcher's). A new service called Mobilescope wants to make sure you always know where—and to whom—your data is going. Lots of apps copy your cont...

Remember those Choose Your Own Adventure novels? If your school was anything like mine, they were so popular you were lucky to find one to check out at the library. But there's no worries now, thanks to this handy HTML5 app, which makes it easy to write and share your own 'choose your own adventure' novels. inklewriter is a free tool designed to make writing interactive stories simple. Basically, you start typing and inklewriter helps you organize your story, making it easy to add, remove and...

First off—Happy Independence Day! Since it's the 4th of July, let's make this week's roundup short and sweet, so you can all get back to your holiday festivities.

WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the communities.

What's the first thing you would do once you realized you were lost in, say, a desert? If you're like me, you would immediately pull out your cell phone and start dialing every number. But what if you have no service? What if your battery is dead?
1 Identify the child's talents, and discuss the opportunities he has to use them in productive ways. If you notice that the child you're mentoring is excellent with counting money, talk about how the child should consider a career in banking or running a business one day.

Pronunciation is key to learning any new language. Before diving into the vocabulary and basic phrases, a good approach is to listen and try and get your aural perception honed in. A new word or phrase, like "je m'appelle" in French, is awesome to learn, but it's important to learn it correctly: that starts and ends with pronunciation.

It's not brain surgery, but teeth whitening systems still hits the pocket books hard. However, there is a cheaper alternative to have the whitest teeth in the neighborhood, and it's called Photoshop. With Adobe Photoshop, you can have whiter teeth in seconds! Really. It's definitely the best tooth whitening remedy for those behind the camera lens. But remember… Photoshop is only a digital cure. You still might have to hide that smile in public… or consult a dentist.

In this how to video, you will learn how to draw an angel. First, start out with the basic sketch of the drawing. Remember, eyes go in the middle of the head. Drawing the head first will help proportion the rest of the body. Use long strokes with the wrist to draw the hair. Try to make the hands the size of the face and try to make the fingers look like fish sticks. It is easier to draw if you study anatomy books. Next, erase the sketch and start going in with further detail. Exaggerate the w...

Dante's Inferno. Most people know this as the first book to Dante Alighieri's fourteenth-century poetic epic, the "Divine Comedy", an allegory of medieval hell. But gamers can experience the torment of sin without the pages of a book. Dante's Inferno is a third-person, action-adventure game from February 2010, playable on the Xbox 360 and PlayStation 3. The story follows Dante (now a Templar knight) as he makes his trek through the nine circles of Hell. His goal: To find Lucifer and reclaim t...

If you read my article on the OSI model, you got a good overview on communications from that model's perspective, but how does that relate to TCP/IP? We're going to take it a step further, getting into the idea behind the two address concept. How does an IP address and a MAC address work together? If you want to hijack sessions and all sorts of lulz like that, you need to understand these concepts. Let's get into it, mates!

At a very early age, I would go on summer camping trips. I remember every night being handed a pack of sparklers that were my own, to swing around wildly, which gave me many valuable life lessons on cause and effect.

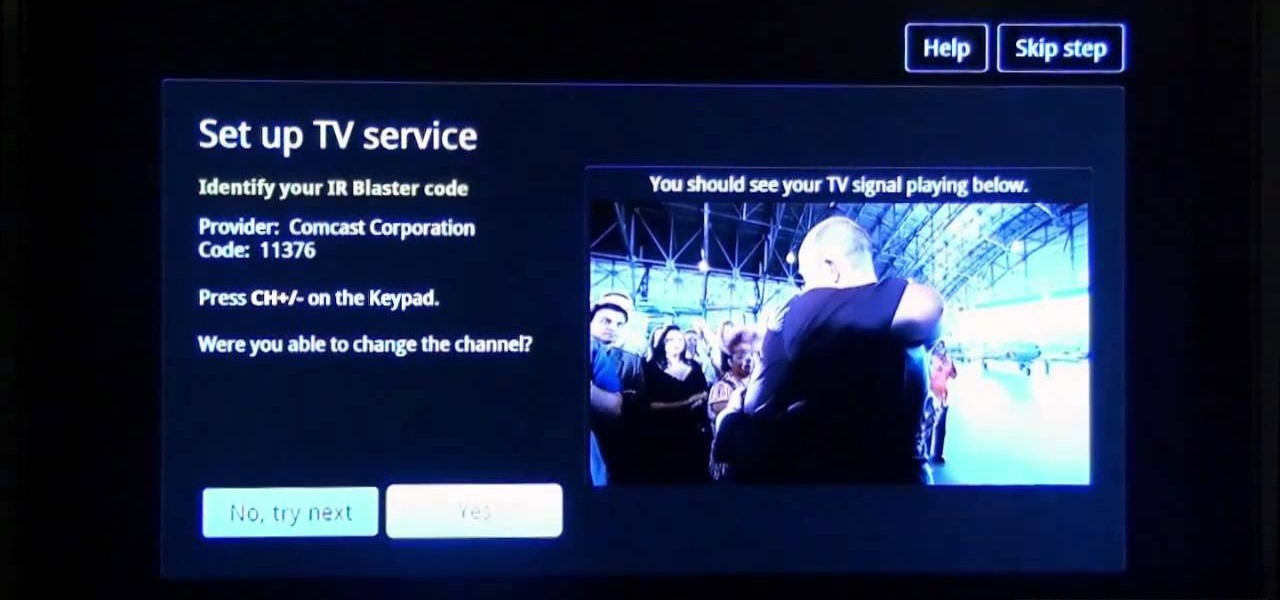
Sony's new Internet TV combines the power of Google TV and television into a neat and accessible package. And setting up your new Google TV is a cinch. This video walks you through the quick setup process for getting your Google TV system going. The player in this video is model NSZ-GT1.

The only things that will get you into a good college is persistence, a will to learn, and of course… grades. If your grades are lacking that oomph they need to impress the schools and your parents, there's a few ways to aid in improving your scores. With a little effort and focus, your next report card will sport better grades.

An easy way to view your CSS code of your website is through the Firefox plugin called Firebug. It's really helpful, especially if debugging your code. Just remember, you cannot save anything with Firebug, it's only for viewing code and adding codes for previewing webpages.

This is a humorous video with tips for young people on how to dress and act to make a good impression in a job interview. Dressing inappropriately for the interview will make the interviewer wonder what you might wear to work. Be well groomed, remove any piercings and be sure any tattoos are covered. A suit is not really necessary; a shirt with a collar and khaki pants are fine. Your appearance shows the interviewer that you are more interested in the job than in expressing your own personal ...

Striking up a conversation with a group of people you don't know can be an intimidating task. Come prepared with some interesting comments and ideas and you will be able to make new friends out of any crowd.

Is a Bridezilla driving you crazy? Whether the bride gone wild is your sister, daughter, or BFF, you can stop the insanity. Here are some tips offered on how to deal with an out-of-her-mind bride.

Paw points. Everybody loves them in Pet Society. You need them to survive. So get more of them by hacking with Cheat Engine!

Enjoy tons of money in Pet Society! But the only way to do so is by cheating… with Cheat Engine. If you've never heard of Cheat Engine, then you're missing out on tons of easy hacks.

I spent hours writing a guide on how to record a screencast, or record what is on the desktop, and convert it. I then found out that this is much simpler & faster and doesn't even involve opening the commandline.

For the avid multitasker, listening to audiobooks and podcasts is the ultimate way to passively absorb knowledge while performing other activities — but there are other options. You can turn any written text on your Android phone into speech that's read aloud to you, so there's virtually no limit on what you can soak up audibly from your headphones or speaker.

Ready to take the next step in your career and become an Amazon Web Services certified cloud practitioner in 2021? The complete AWS Certified Cloud Practitioner All In One Bundle is the easiest option to help you kill the exam — and right now, the entire bundle of courses is on sale with 91% off, for just $24.99 (regular price $300).

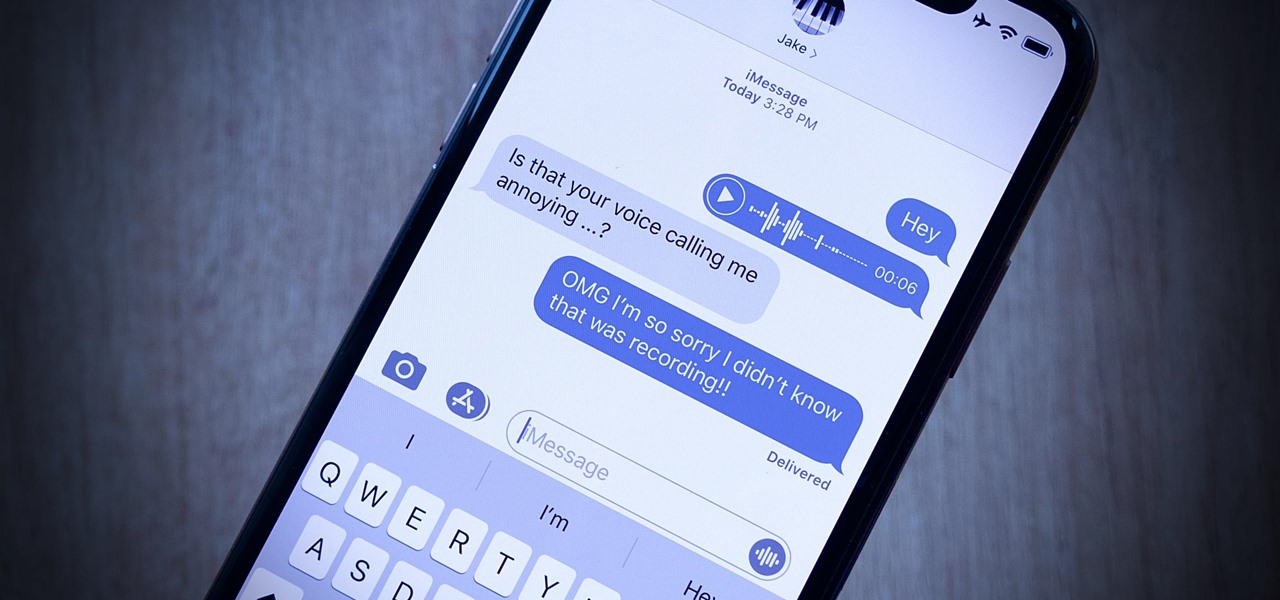
Your iPhone's audio messages may get you in trouble if they haven't done so already. It's way too easy for your iPhone to start recording without your knowledge, only to send a friend or family member a conversation you're having about them. (Awkward.) Luckily, protecting yourself takes only the flick of a switch.

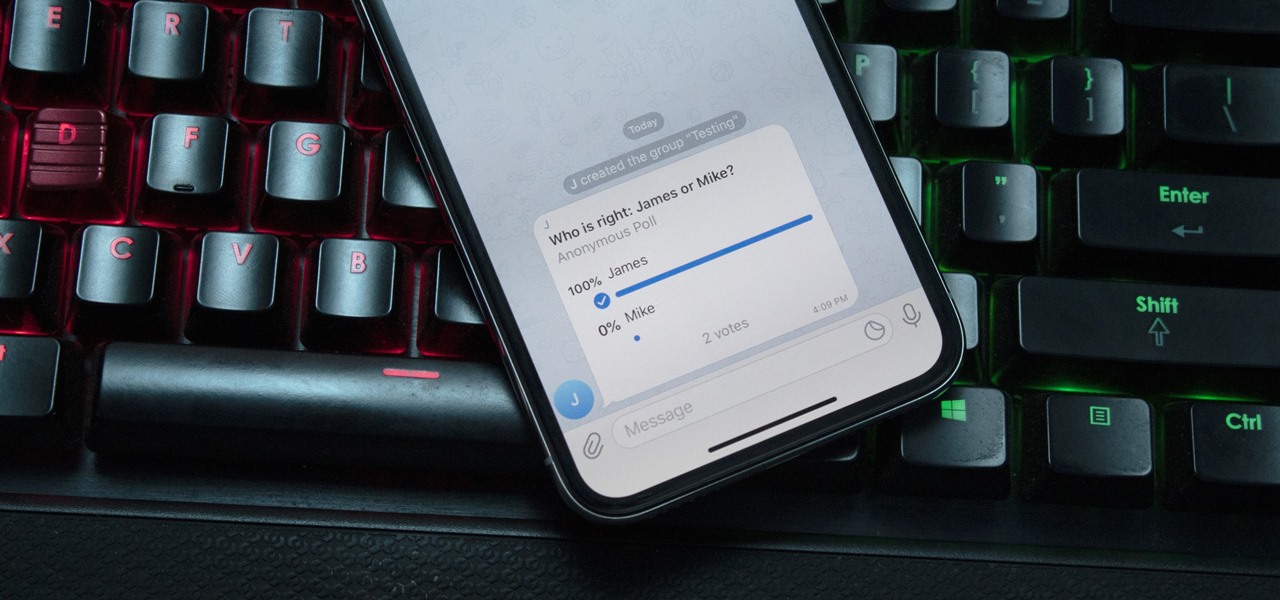
With group chats, arguments tend to devolve from a dispute between two people to a giant debate amongst all members. But before things get out of control, Telegram has a feature that can help.

Pressing the side key on your Galaxy S20 wakes or locks the device, while pressing and holding the button activates Bixby. So "side key" is an apt name — it's not really a power button anymore. That begs the question, how exactly do you restart this thing?

You get a snap from a friend, per usual, but what's this? The lens they're using is actually really cool. Of course, you want to try it out for yourself, but don't bother searching Snapchat's enormous library of lenses to find the AR effect. Instead, there's a simple way to instantly test it out, right from the original snap itself.

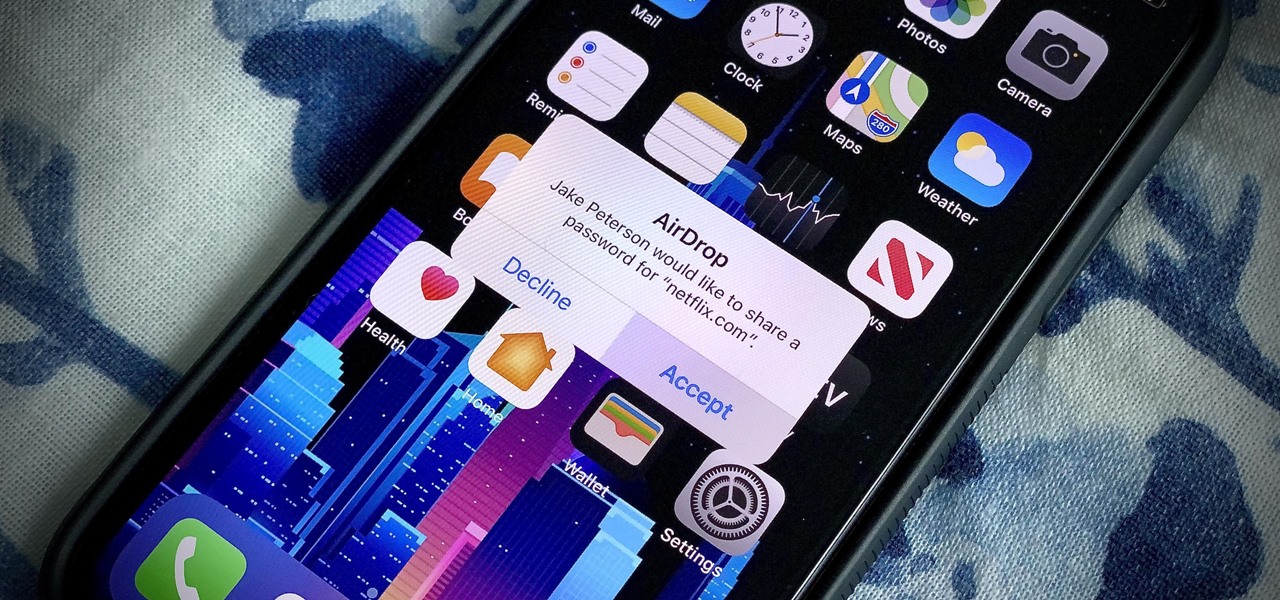
In iOS 11, Apple made it easier for you to share passwords with friends. Back then, it was just Wi-Fi passwords, which made sense. "What's the Wi-Fi?" gets old after a while. But now, whether you're running iOS 12 or 13, you can share any password you want with any iPhone around, all with one of iOS' best features: AirDrop.

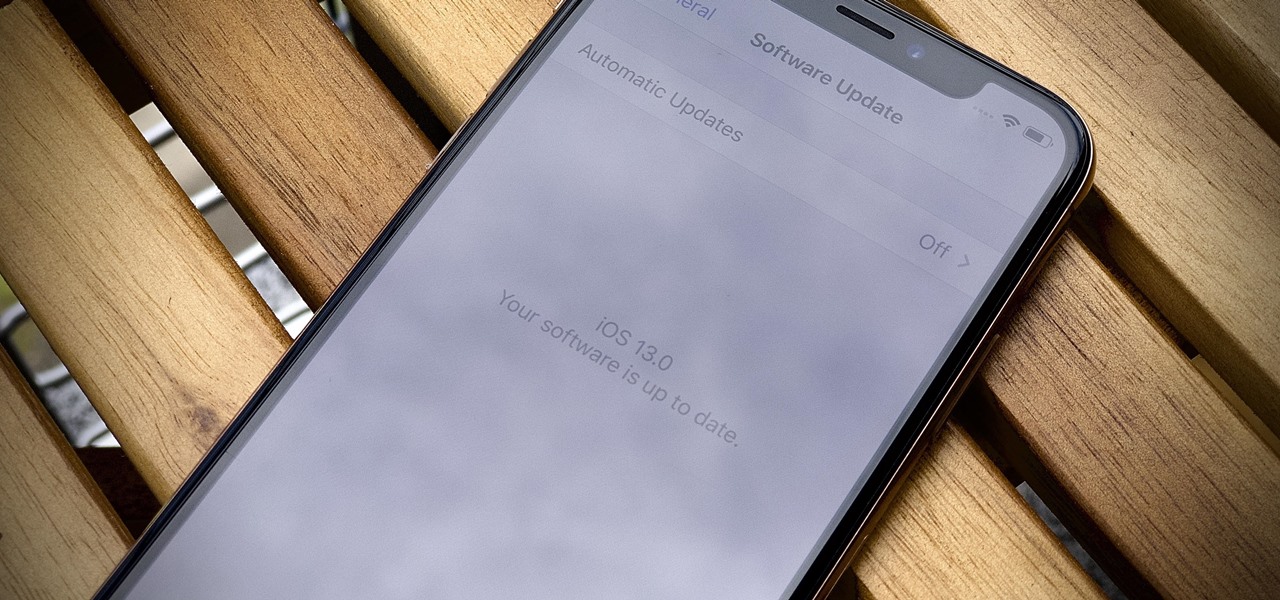
Earlier than expected, Apple just released the first public beta for iOS 13 today, June 24, three weeks after Apple first seeded the beta to developers. The general testing pool now has access to iOS 13's expansive list of new features, including system-wide dark mode, robocall prevention, adaptive charging, and more.

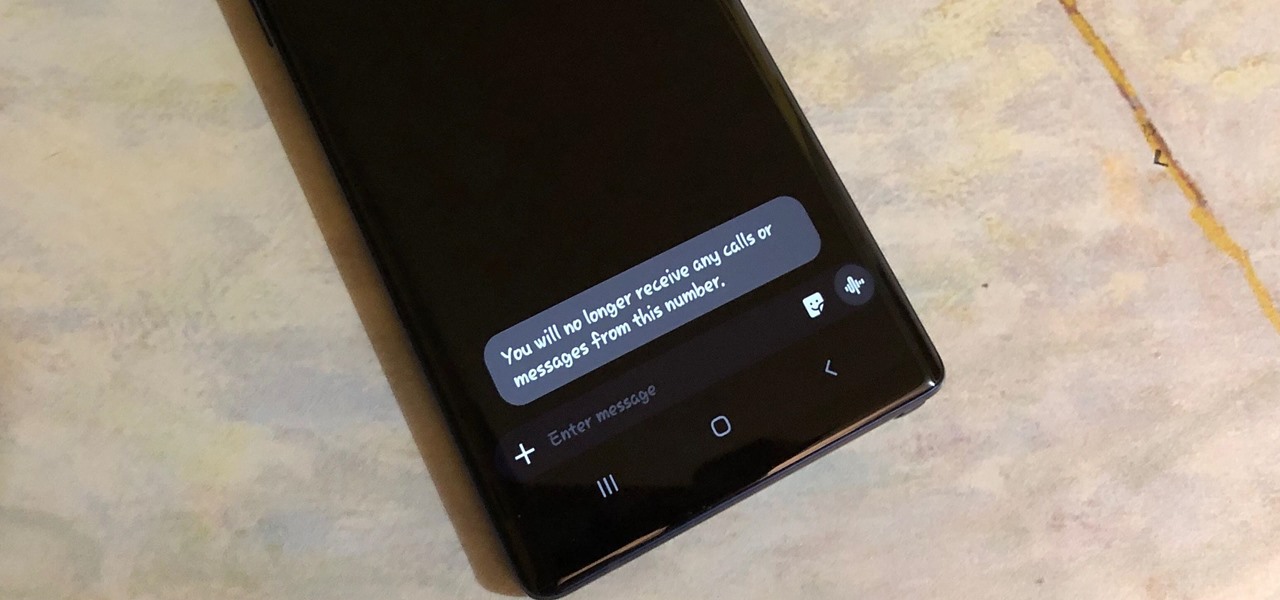
With so much of our personal data floating around the web, it's nearly impossible to get away from spam calls, texts, and emails. Unfortunately, this isn't just limited to the online world — filling in your contact information in a raffle ticket with the hope of winning that shiny new car in the mall, for instance, can often result in getting swamped with spam texts containing sketchy loan offers.

With plans to compete with Niantic and other augmented reality game developers, game developer WarDucks has closed a $3.8 million funding round.

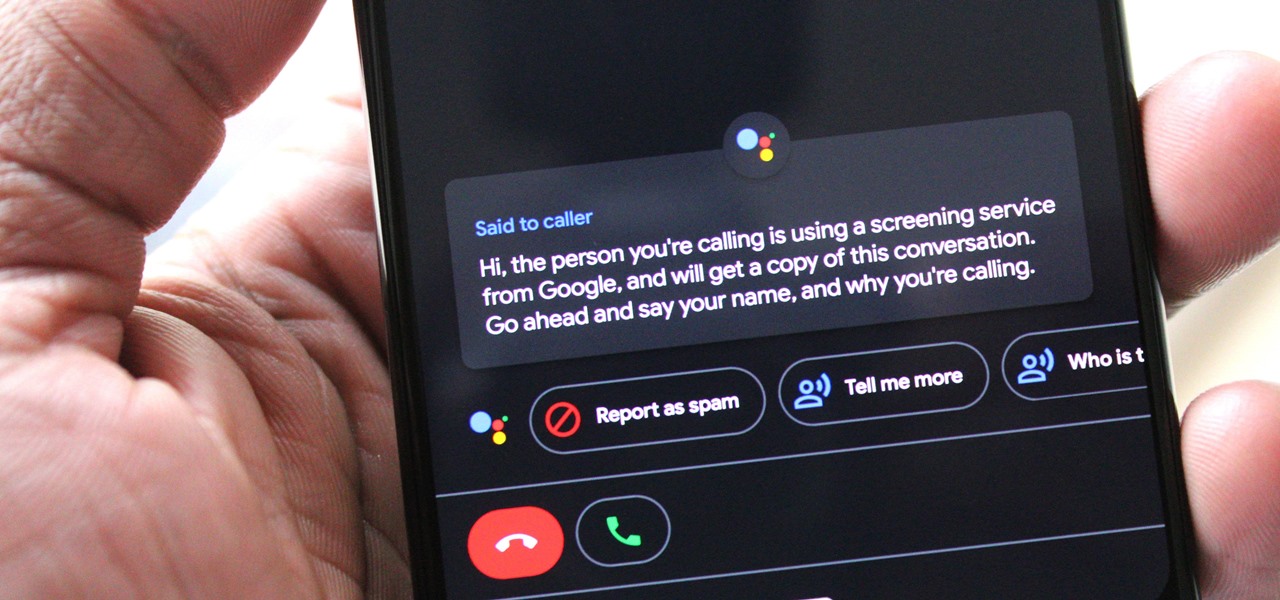
One of the best features on Pixel phones is the new call screening. Any call received on your Pixel device can now be answered by your Google Assistant, allowing you avoid spam calls, wrong numbers, or even exes. But what many don't know is that you can listen to the caller during the screening process.

From its introduction and all the way through iOS 11, FaceTime has been restricted to one-on-one calls. Apple will be changing that in a future iOS 12 update with Group FaceTime, which adds support for up to 32 people total in group audio and video calls. But that's not all we'll be getting in iOS 12 — there are more features that FaceTime has or will be getting soon that you should know about.

Something that always brings a tear to my eye is uninspired Instagram stories. When you have a bunch of like-minded friends, you end up with like-minded stories. While it may seem difficult to stand out, stickers were designed so that you can differentiate yourself from other users — and knowing everything there is to know about Instagram stickers will make you a sticker master.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.