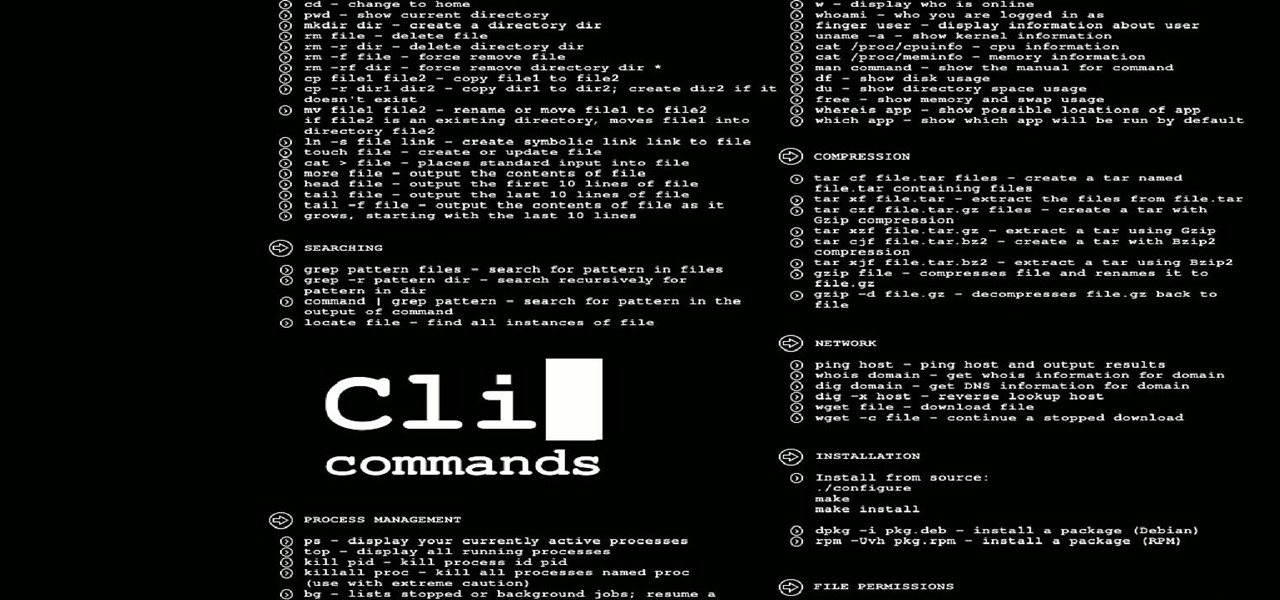
How To: Useful Lesser Known Commands for Linux
Hello everyone on null byte this is my first tutorial This Tutorial Is on Useful Lesser Known Commands on Linux


Hello everyone on null byte this is my first tutorial This Tutorial Is on Useful Lesser Known Commands on Linux

Almost everyone uploads their very personal photos in facebook trusting facebook's privacy settings. But question is - is facebook's privacy settings really that trustworthy? Few months ago, while browsing facebook, I found that one can easily access your private photos using the same browser you used to browse facebook.

Whether it's heated competition during trivia night at the bar, board game night with the family, or just another weekday in front of the TV watching Jeopardy, it seems like a natural human condition to want to test our intelligence.
How do you call 9-1-1 when you need to remain silent or can't speak? It's a great question that will finally be answered on May 15th.

If you're reading this, chances are you're utilizing Xposed Framework to apply unique customizations to your device . We've covered various Xposed mods, like how to how to unlock KitKat's full screen capabilty and make your battery percentage easier to read on the Nexus 7, but today, we're showing you an Xposed module for Xposed. In order to access the modules on your device, you typically enter the Xposed Installer, go to Modules, then select your mod. Easy enough, right? Well, things just g...
In this how-to I will show you how to get Google Music in Canada (or any other country) without a VPN or Proxy. And it will only take 5 minutes

Good posture is more important than pleasing your mother. A lifetime of bad posture basically ensures spine complications, back pain, muscle aches, and other not-so-pleasant physical health problems.

The stock weather widget preloaded on your Samsung Galaxy S4 is really great, but there's one thing that's missing—options. The weather widget shows just the right amount of information at a glance, and it's not too shabby looking either, but for us softModders, it'd be really nice to have more options. Well, today I'm going to provide you with a couple. Interestingly enough, this is a topic I first covered on the Samsung Galaxy S3.

What Is Dimensional Analysis? Dimensional analysis is used to convert units. It's the process of analyzing units to decide which conversion factor to use. It's used by multiplying units by conversion factors, rates equal to 1.

If you've got a Samsung Galaxy S3 or Galaxy Note 2, you probably either love or hate the Social Tag feature. Using facial recognition, much like Facebook does, it scans your photos and lets you tag a name to a face. If your device recognizes the face by itself, it will automatically tag it for you. If the person is in your contacts, it will give you the option of calling, texting, or emailing them. While it's a great feature for some, it doesn't always work perfectly. If the flash from the ca...

A vast number of studies ranging across time, continents, cultures, political systems, and religions show that when evaluating potential mates, women place significantly greater emphasis than men on material wealth, and that men tend to both display and exaggerate their financial status and prospects when around women.

Security researcher Ravi Borgaonkar from Berlin has discovered that hackers can hide an 11-digit code in a webpage that can wipe out all of the information on your smartphone—contacts, photographs, music, applications, and anything else of importance. The attack takes no more than a few seconds and nothing can be done about it. NOTHING. This begs the question—are you susceptible?

In an effort to help posters see the various ways that people discover their posts, Q&A site, Quora has decided to make who views each post, public, along with information on how each viewer came to see the question (ex: through an email, a followed tag, or other public stream). This would probably be an interesting, helpful, and universally liked feature, except for one thing...

A press release should be about news. It should have a sense of urgency about it and grab the reader’s attention from the outset. A good press release must quickly answer the journalist’s immediate questions:

Have someone shave all the hair on their head, but make sure to do it badly. Intentionally miss patches of hair on the eyebrows and head, and make sure to try to get some razorburn for that obviously-just-shaved look. You could also use an electric hair trimmer to leave a little bit of hair and make it even more obvious. Leave the hair on your arms or wherever else as if you forgot to shave it. The point is to be completely unconvincing.

Hotly contested video. The question remains, is the science behind the potato fire bonafide or bogus? We have yet to try it over here at WonderHowTo, and the comments thus far haven't indicated a solid verdict. Try it out and let us know! Is this a hoax? Or can you truly start a fire with a potato, salt and toothpaste?

Do you wanna be that person who stands out in a crowd? Our society dictates our fashion sense. We believe we all must look like who ever is the "most popular" in the media (TV, film, magazines etc.). Our choice to express our self is very limited because of the stigma of what patterns, styles and colors belong to which gender. I have found by adding just a hint of feminine flair to my person that I am able to catch peoples eye's faster than a supermodel walking onto a runway.
Introduction This is one of the things I am asked the most and there are so many different answers. It is hard to just tell you without know your computer's current speed or what type of hardware it has. So here I will talk about how to speed up a slow computer and how to keep your computer running fast.

Ever since high school, I've been preparing my own taxes. Each year it gets more and more complicated, which results in me filing later and later, avoiding it until I have the time or just can't wait any longer. I even resorted to using TurboTax online to help do some of the grunt work for me these past couple years, but that hasn't stopped me from being lazy about it. I have yet to file my 2010 taxes, but I will very soon. Tomorrow, in fact—before TurboTax raises their prices.

Create some form of shocking underpants Get multiple people to play a game of jeopardy

The ComCoachVideo Tutorial is an online learning environment designed to help students improve their oral presentation skills. The website contains video clips illustrating effective and ineffective public speaking practices, as well as an interactive feedback component designed to foster students' ability to critically evaluate presentation segments.

Ever wanted to display text in Minecraft? It's actually not overly difficult. In this tutorial, I will endeavor to guide you through the process between storing and displaying text from memory. To do this, we will examine two different methods of displaying and storing text in memory.

We've talked about the deep web before, but we never really covered the details of what's out there. It occurred to me that a nice list of resources would be very helpful to all of you anons out there. Think of this like a helpful brochure to the hidden web.

This morning, I received a message from a friend who was reading a hack log, and she had some questions about the commands used. This got me thinking, as Linux has a ton of commands and some can be archaic, yet useful. We are going to go over everything you need to know to read a hack log and hopefully implant the steps in your head for future use.

Industrial espionage, social engineering and no-tech hacking are all very real and there are simple precautions that you can take to protect yourself, which this article will discuss. Whether you are a high-profile businessman or a housewife (or husband), keeping information you want to keep private, private, should be important to you.

Over the past couple of weeks, there have been a series of high-profile hacks and leaks. From the rooting of CombinedSystems, to a secret FBI conference call leak, all the way to the distributed denial-of-service (DDoS) attacks on U.S. government sites—with a lot in-between. As governments move to close their long fingers around the free speech that exposes their secrets, this shadowy collective of loose-knit, but like-minded individuals are hell bent on preventing them. Or are they?

With the mass arrests of 25 anons in Europe and South America, and the rumors of an FBI sweep on the east coast of America floating around, times look dicey for hackers. Over the past few days, a lot of questions have been posed to me about removing sensitive data from hard drives. Ideas seem to range from magnets to microwaves and a lot of things in-between. So, I'd like to explain a little bit about data forensics, how it works, and the steps you can take to be safe.

In this article I’m going to talk about specific issues about optimizing your website, making it more clear to Google and other search engines exactly what your website is about. As I've discussed in previous articles this is very important for people when they are searching. We're going to talk first about keyword phrases and how they fit into search engine optimization. You are going to be using keyword phrases in a number of different ways. First you have to figure out what your keyword ph...

Today's article serves as a general guide to keeping Windows 7 and Vista clean. The goal is to clean up your messy computer and have it running at maximum performance in no time. The question at hand is—what is your computer's performance like?
Sergio Peralta Advisor: Jessica Davis

WonderHowTo is made up niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

WonderHowTo is made up niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

Welcome to WonderHowTo's first Weekly Community Roundup! Each week we will be featuring the best projects from the community, as well as ongoing challenges and activities you can partake in. WonderHowTo is made up niche communities called Worlds, so if you've yet to join one, get a taste of what's been happening this week in the highlighted Worlds below...

One of the primary goals of a social network is for you to share what you find interesting with your followers and friends, but on Google+, sharing has so many layers that it can be confusing for most people to really take advantage of it properly. Some of the tools in place that enable you do deal with spam and manage your privacy aren't very clear, so this week's round up is all about how you can share what you want with who you want on Google+.

On Google+, one of the very first creative projects using the popular hangout feature revolved around cooking. Foodies +Lee Allison and +Eric McKee decided to start their own "G+ Cooking School", which has now expanded into the Social Skillet. Although neither have formal training, they're both quite accomplished cooks and skilled instructors. Using hangouts, they've taught their students how to create dishes like margherita pizzas and chicken marsala.

Stuck in a relationship that is going nowhere? Do you wake up and it's nine years later and nothing has changed? Do you also dream of sheep? You know, in the non erotic sense? Well welcome to Catherine, a puzzle game of non-commitment and text messaging.

Hangouts are one of the most fun features in Google+. As long as you have a webcam and a microphone, you can "hangout" with up to 10 of your buddies on Google+ and do just about anything. Of course, sometimes it can get kind of awkward when you are hanging out and you don't really have anything to say. This problem can be mitigated if you host hangouts with a plan.

People ask me all the time, "Nick, what are the best blinds for my home in terms of Wood vs. Faux Wood?" Well the answer to that question is not so cut and dry. However, I can help steer you in the right direction. In this post, we will examine the pros and cons of both wood and faux wood blinds to help you make your decision.

Guiding internet users to useful content is one of the most lucrative businesses in the world. This process is called aggregation. Google and other search engines form the top of the food chain, aggregating all of the content on the web in response to queries. There are all sorts of other important aggregators though, and you probably use at least one every day: Fark and Reddit for web content, Rotten Tomatoes for movie reviews, and Metacritic for a variety of media, but most importantly, vid...
Dear Miss and Mrs. H, I love your blog! Its nice to get two completley different opinions on one subject. I have a couple questions for you both and then need some advice.