
How To: Do Striped Valentines Day Nail Art Design
This is a very cute combination of black and white striped with red glitter and red sequins! Video: .


This is a very cute combination of black and white striped with red glitter and red sequins! Video: .

In this video I did a very simple nail design that can be worn by women and teens on valentines day or just regularly too ! It is a very easy to create design and looks not only pretty but also immensely elegant!

This is one of my personal favorite designs from last year, that I wanted to share with you all for this year's valentines day !

In this video i shall be sharing some super amazing glitter nail polish swatches of Elixir nail polish collection!

This is a very easy nail design that I tried a few days back and I couldn't believe that such a simple nail design could actually look so exciting and get me so many wonderful compliments !

In this video , I shall share with you girls a very simple and fun way to go glitter nails to get a gel like effect and a framed look for this glitter ! Check out the video and you will be surprised how easy it is to get these simple and clean lines on the nails !

This is a very easy hello kitty nail art design that I recently did using hello kitty nail art stickers! In the video given ahead, I have demonstrated in a step wise procedure how to use nail art stickers and how you can create this super cute design in less than a few minutes !
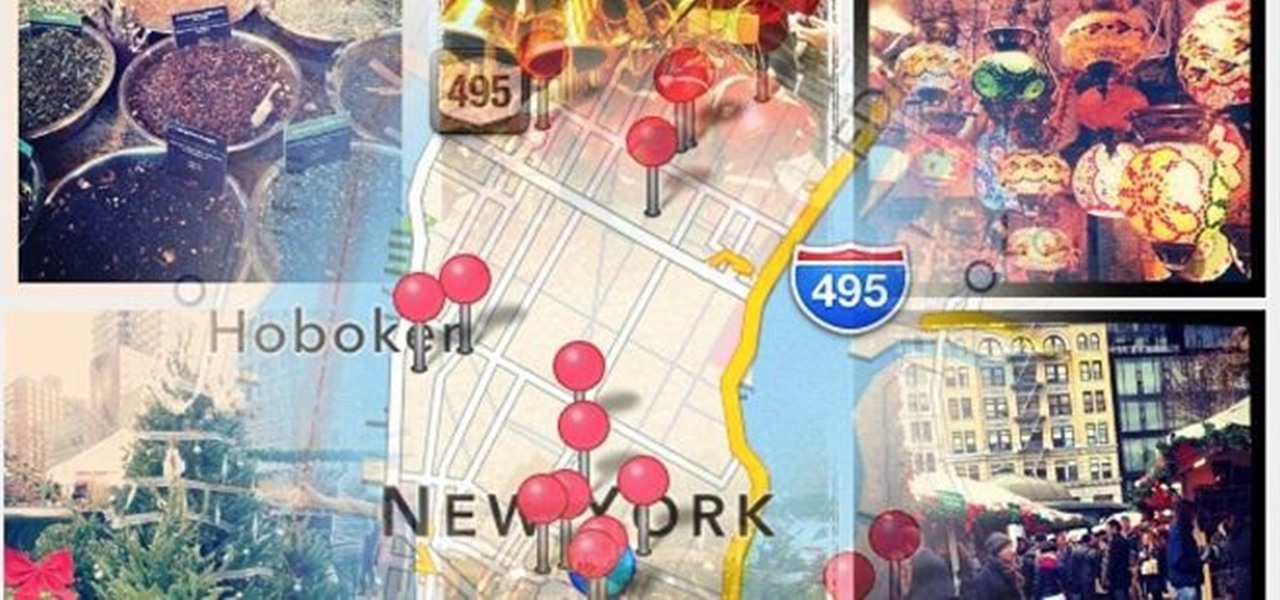
The only thing worse than not having any plans is not even knowing where to begin making them. Sure, you can check Yelp or one of countless other review sites to find a great spot, but there's no way of knowing what the vibe is like before you get there. Is it crowded? Are people having fun, or does it look pretty lame?
The long standing popularity of 4chan has been due to the entirely anonymous setup. The site's anonymous community and culture has provoked media attention, in turn inciting larger audiences. On the other side of the spectrum is Facebook—popular for its connectivity and easily identifiable names. With the brush of keyboard stroke, you can be connected with your entire high school class in a matter of seconds.

This is a very interesting puzzle nail design that I did the other day ! It is super easy to create and uses a combination of matte nail polish and glossy nail polish to create a light crisp effect !

In this video , I have done a very easy and quick sequin nail manicure ! Video: .

If you've ever taken a university course with an awesome professor, you're more than likely acquainted with the precious and all-glorious cheat sheet. Like the midterm, the professor usually allows a one-sided cheat sheet for the most important exam of the class—the dreaded final. I should work on my final, but I'd rather just sit here and be a douchebag.

Striping tapes are very popular these days , among nail enthusiasts. One of the main reasons is that not only is it super easy to use, but you can literally create hundreds of styles by using them right !

Here I have used some very smart and easy to use nail art decals to create this lovely zip nail art design !
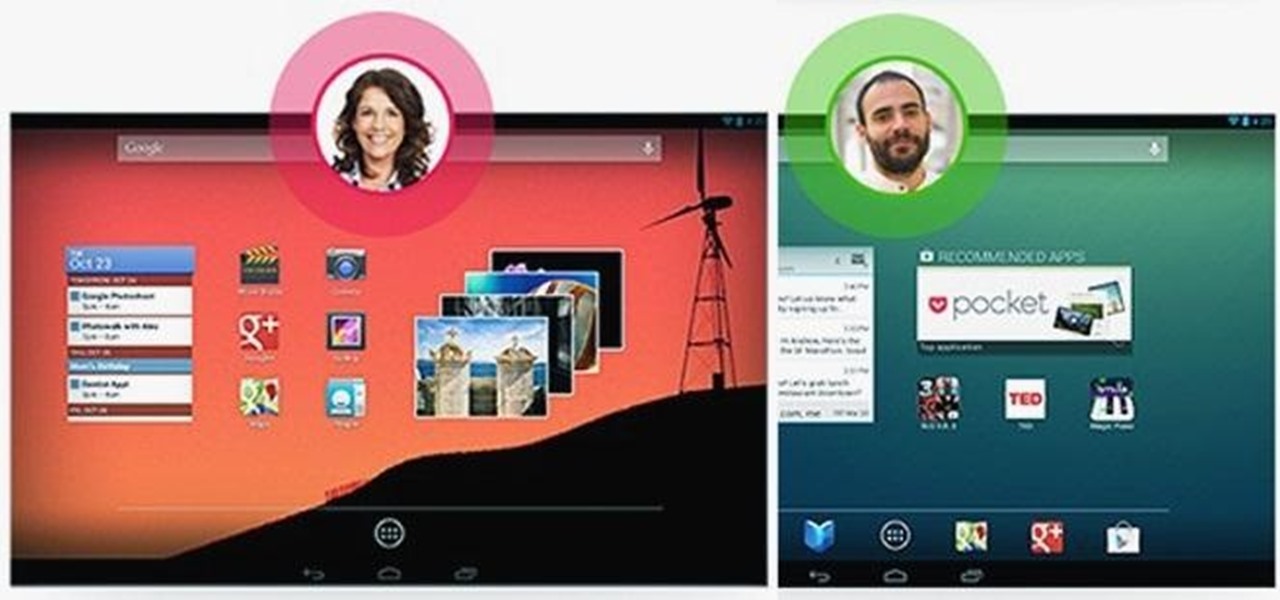
The most recent update for Android's Jelly Bean has some pretty cool new features, like better panoramic photos, gesture typing, and wireless sharing. From a security standpoint, though, the best new feature is the ability to add multiple users to one device. You can create up to 8 different accounts on Android tablets like the Nexus 7 or Nexus 10, so besides saving time hiding or protecting sensitive data, it could also save you some money. You can share a device with your family, kids, or s...
Feelings can get hurt on Twitter as fast as an update. Everything is fine and dandy because two people are mutually following each other, then out of nowhere, one person has unfollowed the other out for seemingly no reason. Twitter doesn't notify users when someone has unfollowed them, so there are millions of people out there who get used for their follow! Well, now you can find out who unfollows you on Twitter with these mobile apps.

Lucid dreaming, in which you're aware that you're dreaming, can be profoundly beneficial to us. It gives us freedom to do things we couldn't possibly do in the real world. It can show us the true potential of our brain power. You can even use lucid dreaming to question the nature of our own reality. For whatever reason, people everywhere are interested in this mysterious phenomenon...especially in achieving it. Whether it be visiting another planet or flying around, the possibilities in lucid...

If you don’t have any little children to blame for an inadvertent or misguided app, book, or music purchase from Apple, you might still have a fighting chance. Apple has a very strict return policy, specifically stating that all sales and rentals of products are final for purchases made in the iTunes Store, Mac App Store, App Store, and iBookstore. But if you play it carefully and do a little digging, a return and full refund may still be possible.

I've never really liked to type on a flat or low keyboard. Even the small flip-up stands underneath most keyboards were not good enough for me, as those little legs aren't usually more than 2 or 3 centimeters high. I'd like a minimum of 5 cm, so I decided to make this keyboard base for myself. Aside from giving me the right height and angle, this DIY keyboard base also features LEDs that light up my monitor, the table, and gives a nice background to my desktop. It's even got a built-in stand ...
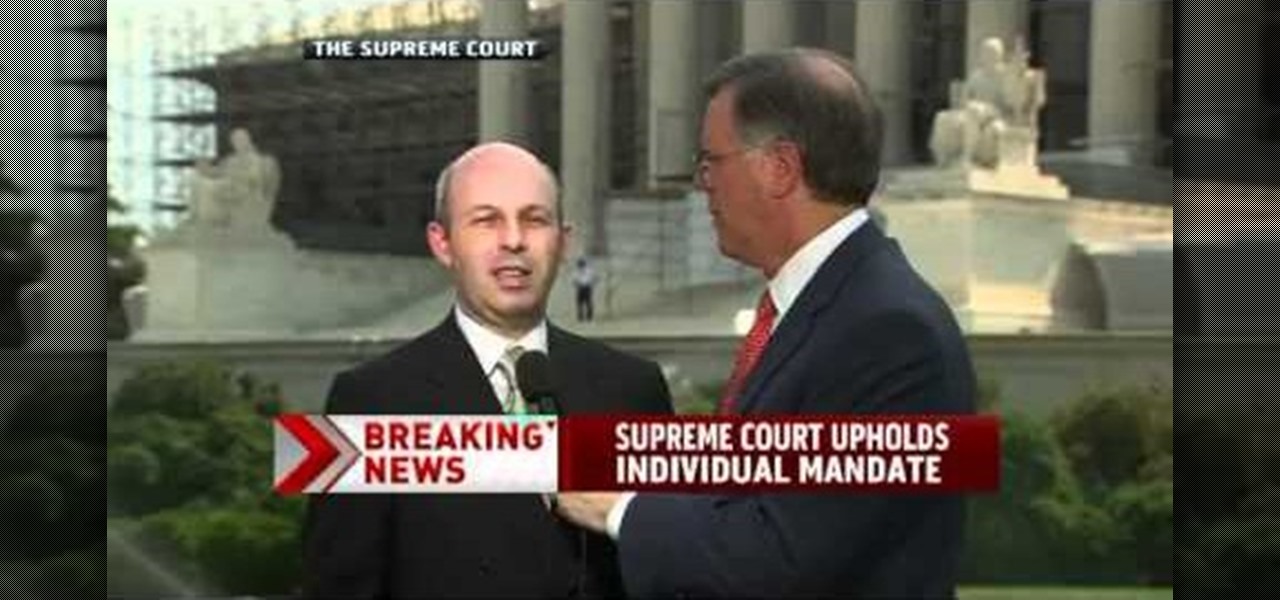
The big question this week would be the controversial Obamacare mandate. And heres the answer: Yes. Obamacare passes Congress' filters and is now an official OK. Texas college hacks drone in front of DHS — RT.

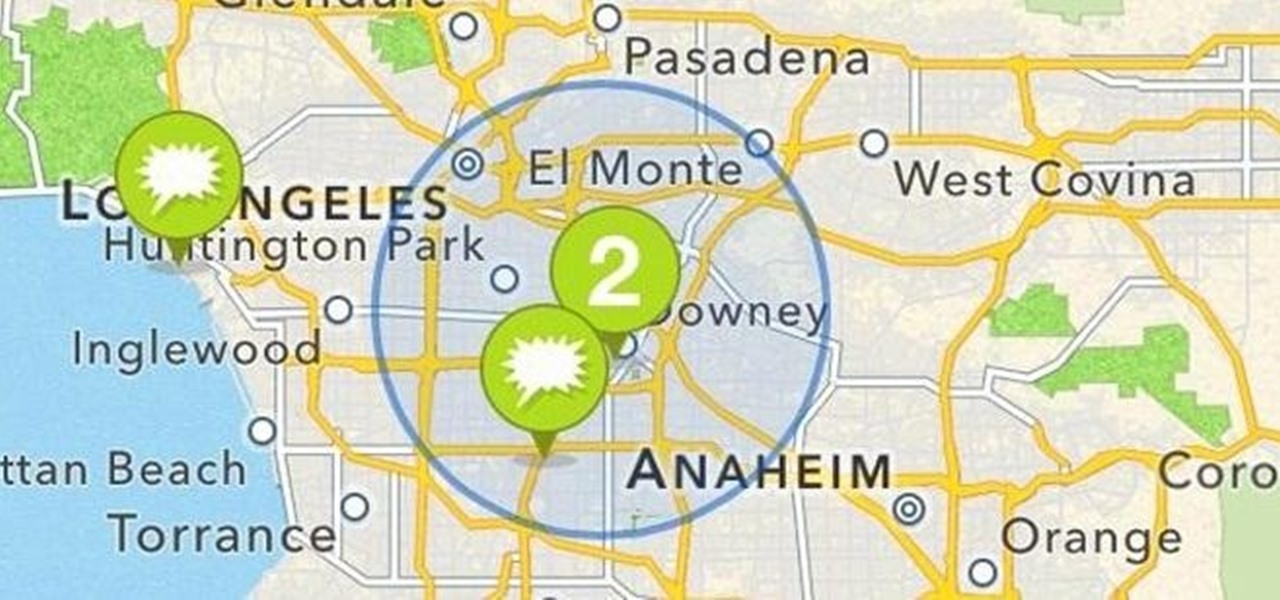
What's the first thing you would do once you realized you were lost in, say, a desert? If you're like me, you would immediately pull out your cell phone and start dialing every number. But what if you have no service? What if your battery is dead?

Pronunciation is key to learning any new language. Before diving into the vocabulary and basic phrases, a good approach is to listen and try and get your aural perception honed in. A new word or phrase, like "je m'appelle" in French, is awesome to learn, but it's important to learn it correctly: that starts and ends with pronunciation.

If you're always taking blurry and underexposed pics with your mobile device, try using some of the tips below to turn your phone into a valuable photography asset. It doesn't matter if you have an iPhone, Android smartphone, or even a first-gen camera phone... you can still take some beautiful, winning photographs.

If you do get stopped pull over to the right and make sure you are off the road. If it is at night turn your interior lights on. Keep your hands on top of the steering wheel until the officer tells you what to do. If he asks you do you know why I stopped you always answer no. He will then ask for your drivers license, registration, and insurance. If it is in your glove box or your wallet tell him what you are going to do. This shows respect for the officer. Before he goes back to his car make...

Is your French up to par with Parisians? Can your Aussie tongue mingle with the local Australian natives? What about your old-style New York accent? If you're in need of improving your accents in different languages, then Amy Walker can help you out.

This retro informative video gives a general overview of a woman's menstrual cycle. A curious young girl asks her family questions about having a period, what's normal, what isn't, who gets one, who doesn't. While this video feels a bit dated, and eschews medical terminology, it offers some basic insight to that time of the month. Check out this video and learn how to understand the feminie menstrual cycle.

Panties don't taste like fruit, unless the edible panties cocktail is the one in question. Raspberry vodka, orange vodka, cranberry juice, sweet and sour, watermelon liqueur, sour apple liqueur, and triple sec make up the edible panties cocktail. Follow along with bartender Jorge as he gives step by step directions for how to mix up this specialty alcoholic drink. Watch this video beverage making tutorial and learn how to mix the edible panties cocktail.

This tutorial covers some frequently asked questions in Sony Vegas 7.

Yossarian the Grammarian answers your questions about gerunds and gerund phrases. Great English grammar lesson for ESL students.
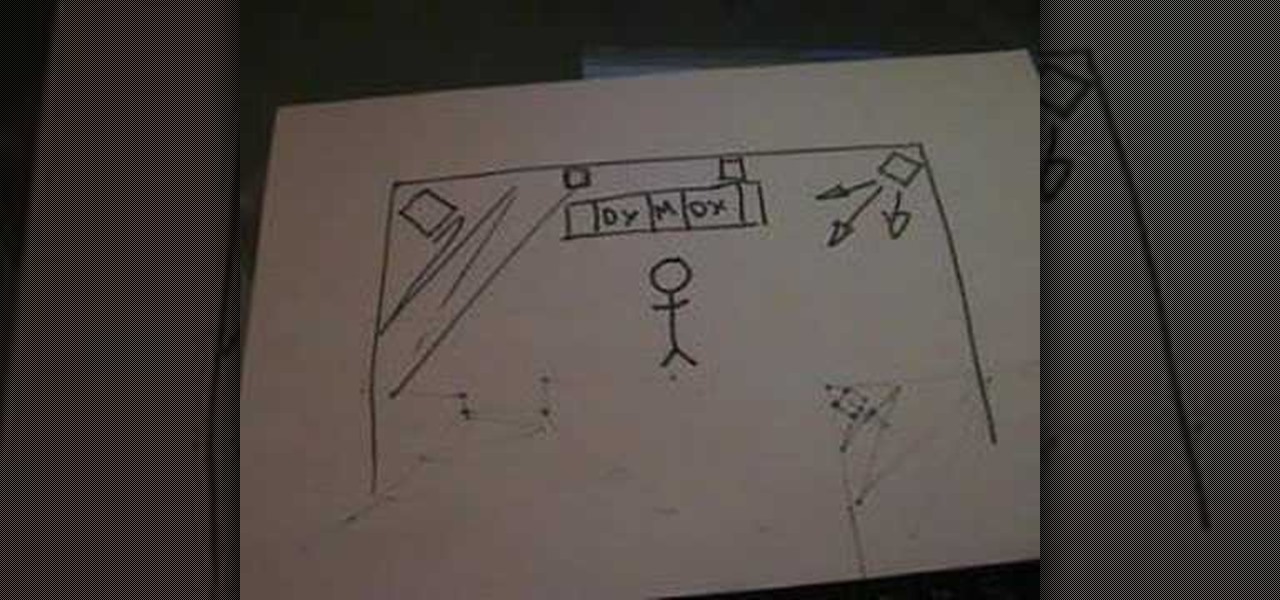
DJ Tutor answers the questions: where does the earth cable go, how do I get a good sound out of my speakers, and will I get problems if the cables cross each other.

10 phrases and questions to ask your bartender, in Spanish, is taught in this video.

You don't need to work in the accounting department of a Fortune 500 company to use and appreciate Microsoft Excel. Although primarily associated with a wide variety of functions pertaining to accounting and finance, Excel is actually an incredibly powerful and multifaceted platform that can be found at the heart of many large-scale analytics environments.

Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

The ability to stay organized and be resourceful with data gathered from recon is one of the things that separates the true hackers from the script kiddies. Metasploit contains a built-in database that allows for efficient storage of information and the ability to utilize that information to better understand the target, which ultimately leads to more successful exploitation.

Cross-site scripting can be one of the easiest vulnerabilities to discover, but to be successful with this type of attack, it is essential to learn how to get past filters. In the previous guide, we explored some ways to do this, such as abusing attributes and event handlers and tricking the application into accepting unusual characters. Now, let's take a look at more techniques used to defeat filters.

It's always a good idea to know how an attack works at the very basic level. Manual techniques for exploitation often find holes that even the most sophisticated tool cannot. Sometimes, though, using one of these tools can make things so much easier, especially if one has a solid foundation of how it works. One such tool can help us perform a cross-site request forgery with minimal difficulty.

Google, Amazon, and Facebook are always listening. But what's worse? Hackers are listening, too. Windows PCs are particularly vulnerable, but with a few simple commands, a remote attacker can even take over the microphone on someone's Mac computer, streaming audio and listening to private conversations in real time without the victim's knowledge, abusing an overlooked security consideration.
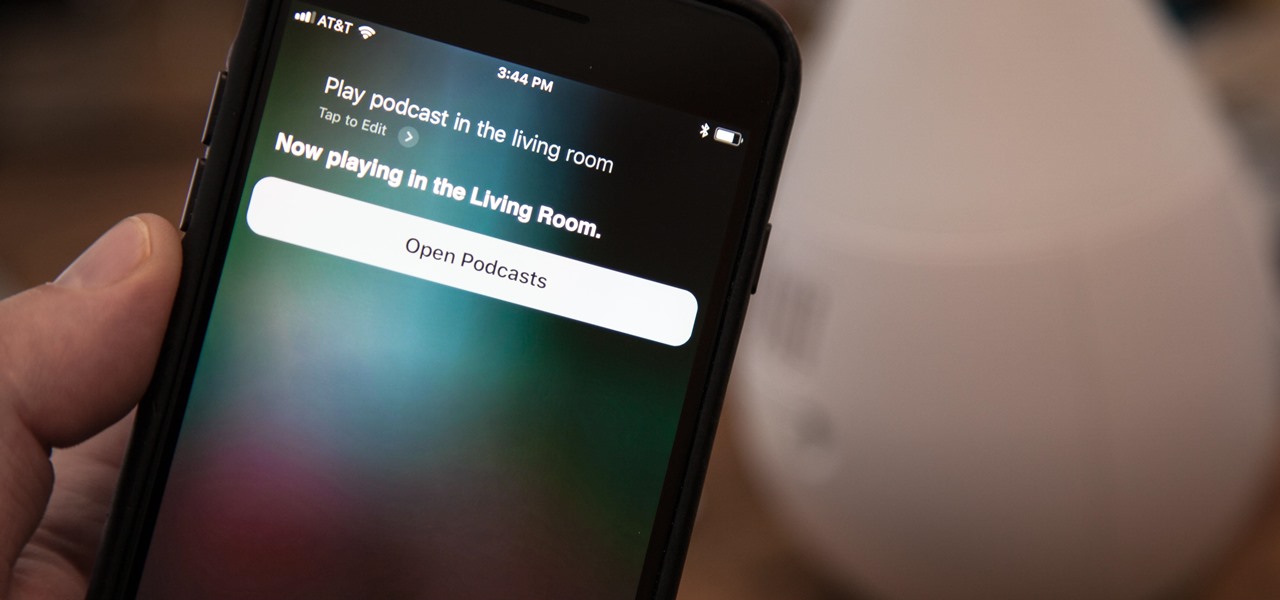
A few long-awaited iOS 11 features that Apple had promised way back in June 2017 have finally made their way to iPhones with the iOS 11.4 update. Aside from finally delivering on those, there's not a whole lot new in iOS 11.4 as a whole, though, there are a few things you'll definitely want to know about.