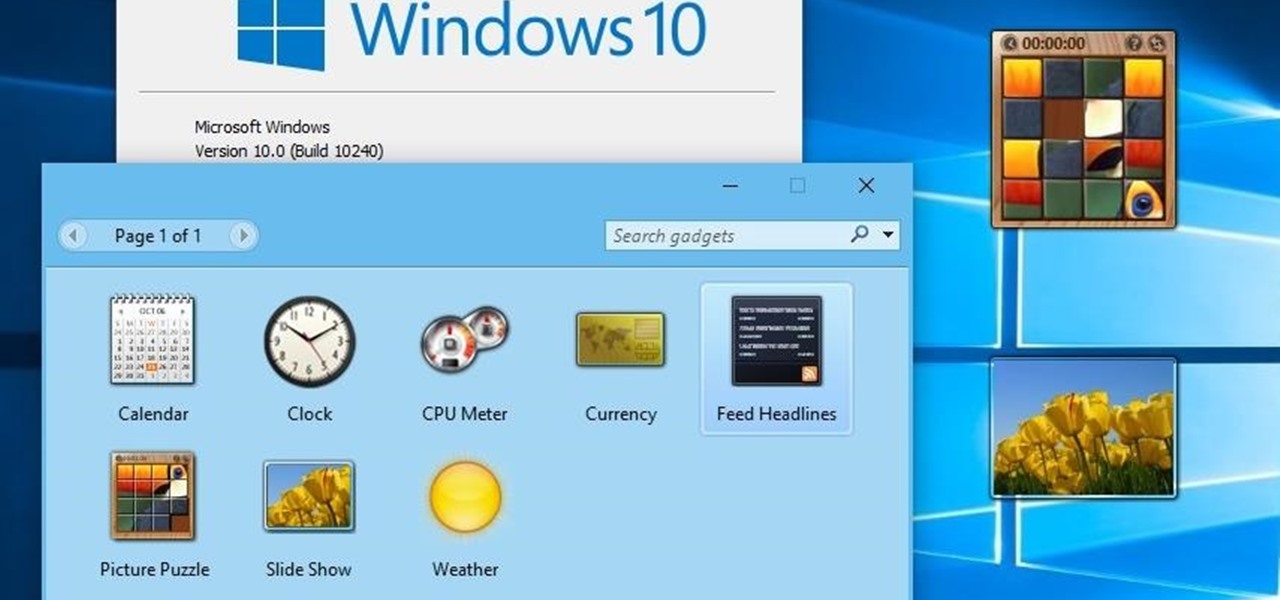
The concept of desktop gadgets has been around for quite some time, and Microsoft officially introduced them in Windows Vista to much fanfare. Desktop gadgets offered the ability to view various information at a glance, play mini-games, and more. Unfortunately, Microsoft decided to kill this beloved feature after Windows 7, citing security reasons.

In my last how-to, we built a man-in-the-middle tool. The aforementioned script only established a man-in-the-middle. Today we'll be building a tool to utilize it. We'll be building a DNS packet sniffer. In a nutshell, this listens for DNS queries from the victim and shows them to us. This allows us to track the victims activity and perform some useful recon.

If you have some photos, videos, and documents that you want to keep completely hidden and encrypted on your Android device, Andrognito is the app you need. We showcased this app in the past, but since then, CODEX has rebuilt it from the ground up with new and improved features.

As you might know, there are a multitude of tools used to discover internal IP addresses. Many of these tools use ARP, address resolution protocol, in order to find live internal hosts. If we could write a script using this protocol, we would be able to scan for hosts on a given network. This is where scapy and python come in, scapy has modules we can import into python, enabling us to construct some tools of our own, which is exactly what we'll be doing here.

Social Engineering was mentioned a few times here on Null Byte, but not very many explained what it is, or how to do it. I love this quote because it's true: Social Engineering is the key to carrying out client side attacks, and all you need is a little creativity!

Hello, ladies and gents! Today I will be discussing the fun and excitement of backdoor on an OSX system.

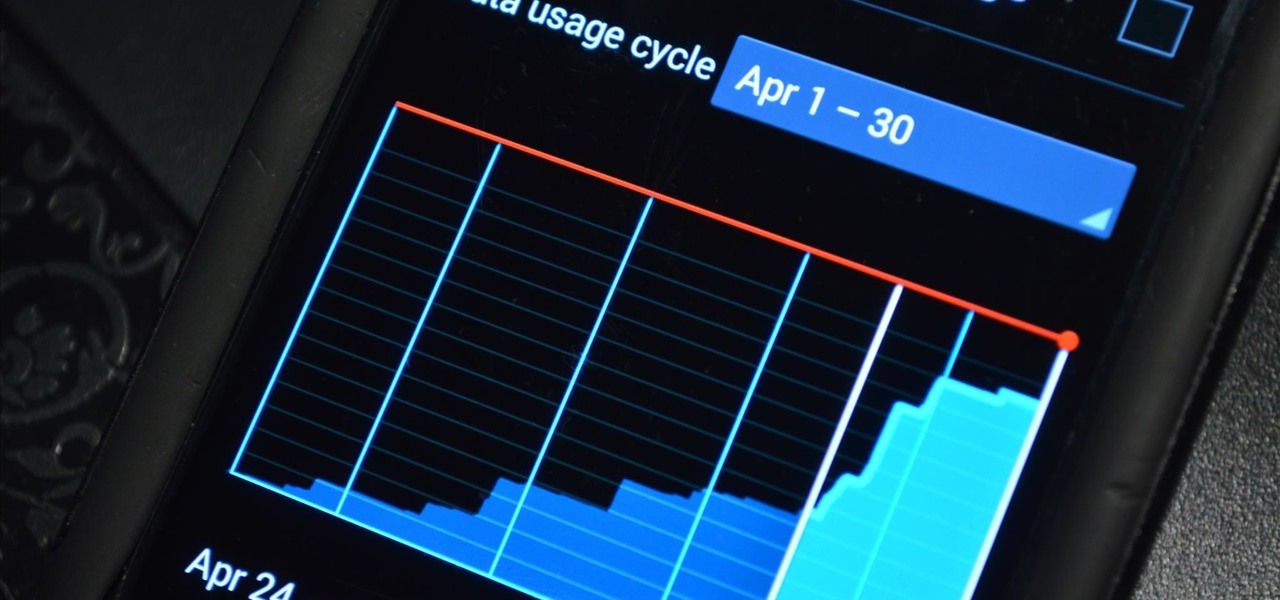
Make no bones about it—Google is an advertisement company first and foremost. Nearly everything they do is geared towards targeting the right people with the right ads.

Hi everyone! In the previous part of this series, I introduced one way to hijack a program's execution flaw, though I only showed you how to crash the program and left you with a little mystery to solve. Today we are giving the solution of that and then introducing shellcode usage and remote command execution.

Hi everyone! Last time we finished analyzing the assembly representation of our vulnerable piece of code (have I ever told you it is vulnerable?). This time we are going to introduce some fundaments about exploitation by demonstrating how to crash a program's execution. If that sounds lame, next time we will see how this crash can in fact be useful to control the program's execution, achieving remote code execution!

The Apple Watch is finally here! We'll have loads of guides and videos for you guys to check out in the following week and beyond, but we thought it'd be best to start off showing you how to set up and pair that brand new beautiful Apple Watch of yours to your iPhone.

Hi everyone! After messing around a little bit with IDA and Hopper disassemblers and briefly introducing you to memory, registers and Assembly, we are going to understand what happens when a process is running, which variables join the play and especially what happens when a function is called and why is this procedure-logic so interesting and useful along with the concept of stack.

One lump or two? That was the age-old question with sugar cubes, which used to be a staple of any tea salon or dignified household this side of Downton Abbey. These days sugar isn't really used in cubes much except in bars and restaurants, and that's a shame. Cubes are a lot less messy than granulated sugar, and you can measure the exact amount you put in your drink no matter what.

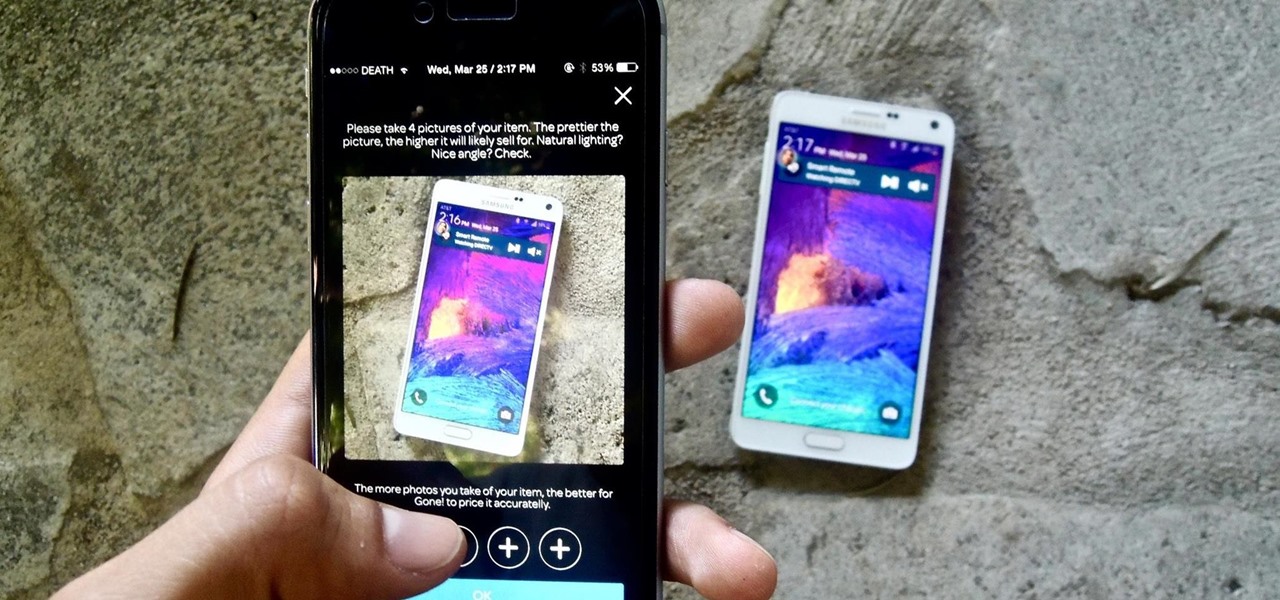
If you want to sell all of the old electronics lying around your home, it takes a lot of work. If you go the eBay route, you have to take tons of pictures, describe it accurately, wait for a week until someone bids on it (or not), then package it, ship it, and wait for feedback. Craigslist is a little bit easier, but usually requires you driving somewhere to meet the buyer in a public place (if you want to play it safe).

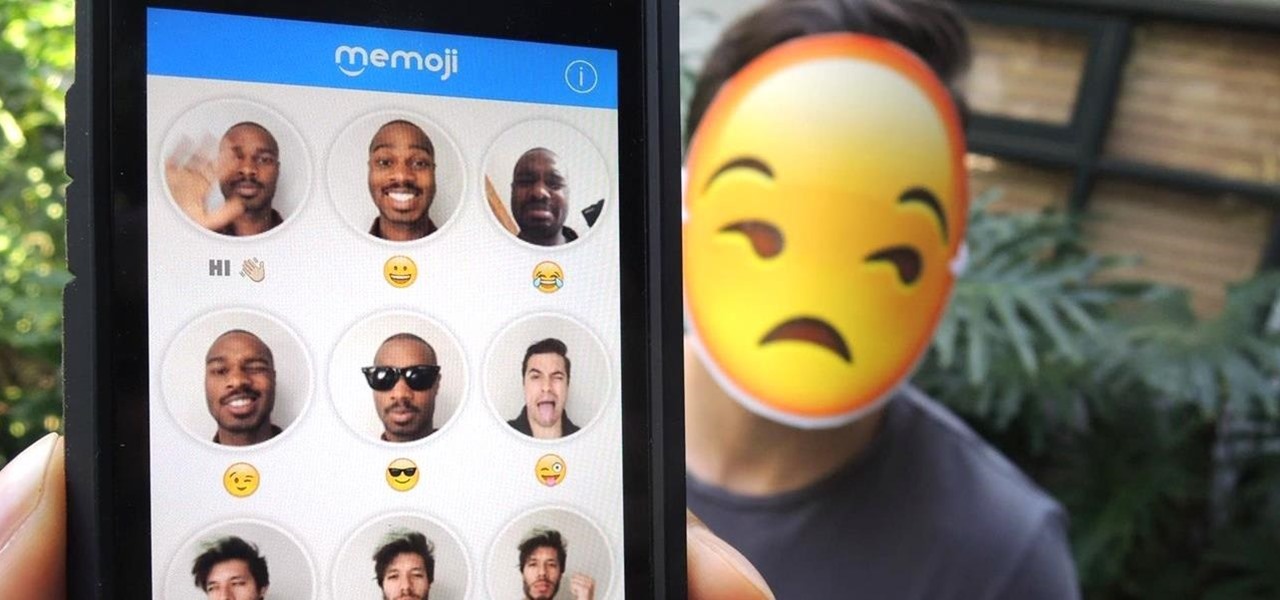
Yes, emojis are the [insert poop emoji here]. They can help improve your love life and even let you portray emotions in a more diverse and well-rounded way now. But combining emojis with GIFs? Well, that's some next-level [insert poop emoji here] right there, and with a new iOS keyboard from Puppy Ventures, that next level is finally here.

Inspiration for tutorial: Foxtrot's "How to Trap a Tracker"

When you're expecting an important call or text, it's pretty annoying to hear or feel your phone go off just to find out it was your reminders app telling you that you need to buy more contact lenses. Not quite as annoying as phantom phone vibrations, but it's up there.

I first became acquainted with this dish when I worked across the street from a Chinese restaurant. After that I ordered it every time! Now that I don't work by there anymore I don't get to eat it but I sure do still crave it! So I researched and tried a couple recipes and this was my favorite. Hopefully this version lives up to your expectations.

Keeping your OnePlus One running smoothly can be taxing, especially if you spend most of your day looking for ways to tweak performance settings like me. Sometimes I get lucky and end up with a faster phone, but because I experiment so much, I often end up restoring it back to stock. This process can get old really quick, but when I started using the Bacon Root Toolkit from WugFresh, it became exponentially easier.

Spills happen in the kitchen, and while every good cook knows to clean as you go, not every cook has an endless supply of cleaning materials. Besides, one spill can exhaust your entire stockpile of sponges, paper towels, and rags in a matter of minutes. Particularly egregious mishaps can make everything they touch feel sticky and gross.

It wasn't too long ago that I showed you how to unlock the LG G3 bootloader and install TWRP, and while the process was extremely easy, the custom recovery can look a little intimidating to new users. Even long-time users who know how to navigate it find it boring to look at, as TWRP has had the same basic aesthetics since its creation.

We're always looking for great food hacks to help us become better cooks who can create delicious food with less waste, fuss, and hassle. You never know where the next good tip will come from, so we've all learned to keep our eyes and ears wide open.

We live in a time where privacy is rare and our files can be easily accessed by just about anyone. Having your phone protected by a passcode is great, but if someone figures it out, they can easily access anything on your phone.

A couple months ago, I attended a Pokémon-themed party. Everyone dressed as their favorite Pokémon or trainer, Poké balls flew around the backyard, and more importantly, there was a lot of Poké booze. My friend who created the colorful drinks you see below informed me that they were infused with Skittles. This, my humble readers, was a defining moment in my life.

Losing important data is the modern-day equivalent of misplacing your wallet or keys. We have tons of vital information stored in our digital worlds, and losing any of it can be devastating. But if you've accidentally deleted something important from your Android device, there's still hope.

The bootloaders on the AT&T and Verizon Wireless variants of the Samsung Galaxy Note 3 still cannot be unlocked, despite the $1,400+ bounty that arose late last year. Nine months later and still nothing. But just because we can't "unlock" the bootloader doesn't mean we can't get around it.

It was a chilly but otherwise beautiful night at YouTube Spaces LA—food trucks, ping pong, a photo booth, and the chance to view film school projects created completely with Glass. About a year ago, the Glass Creative Partnership was formed to explore how Glass could be used in filmmaking, with partnerships spanning from the American Film Institute to CalArts and UCLA. On July 16, 2014, the products of that partnership were screened under the Southern California night sky. Three films were sh...

Hi! Let me get started on this subject as it is a very "touchy" subject. We all want to "hack" these days, and that's logical. Te be real honest here, i was inspired once by the words someone from the Null byte community said. In the (near) future, wars will be ended by computers and not a nuclear missile. That's something i really do believe in. But let us take a defensive measure instead of the offensive one. Sure, Full frontal bryte forcing is an option, but when it'll come that far we'll ...

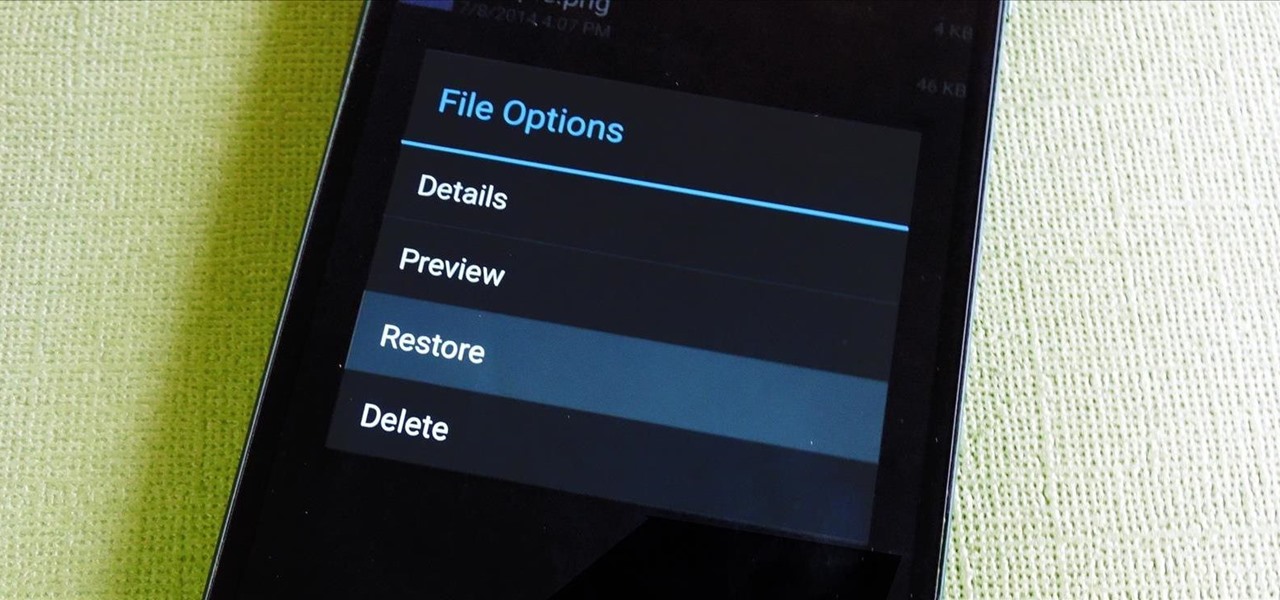
If you've ever used a computer, you're surely familiar with the concept of a Recycle Bin (Windows) or Trash Can (Mac). To sum it up, files that you've deleted are not actually gone from your storage, they've just been moved to a different location. You can then restore the files if need be, or empty them, permanently deleting them forever to free up space.

Although lacking in megapixels, the HTC One M8's camera can be considered a top-tier, flagship-level shooter. With the Duo Camera and UltraPixel technology behind it, it can make even the most inexperienced photographer snap pictures like a pro. There seems to be little missing for the average user, but for the more seasoned photographers, some of the standard settings may seem a bit too dumbed down.

I regularly use iTunes on my home laptop and my work desktop forty-five traffic minutes away. I'm ashamed to admit it, but until recently, I'd been saving my iTunes library on a USB and transferring it back and forth, over and over again, between the two computers.

Text input on a touchscreen device is constantly evolving. From early beginnings of pecking out each individual character to today's predictive text and gesture keyboards, we've already come a long way.

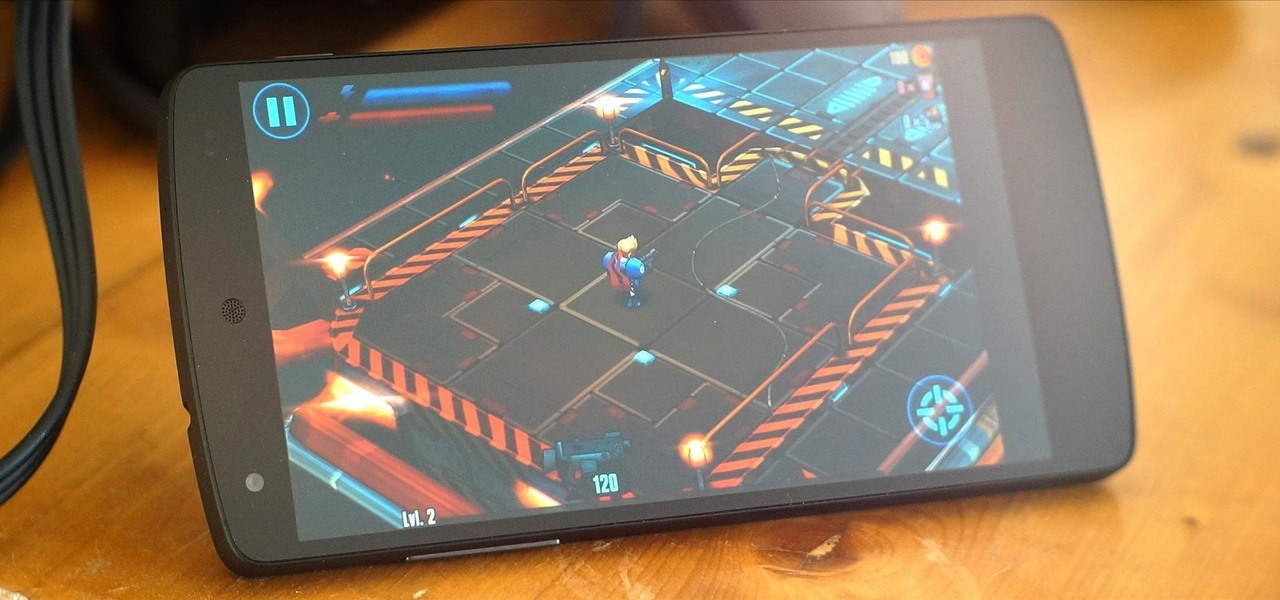
Aside from the newer HTC One M8 and Samsung Galaxy S5, the Nexus 5 still has one of the fastest processors on the market today. However, despite its superpowers, some graphically intensive games can still have a bit of lag to them during gameplay.

It's been over two whole years since the Samsung Galaxy S3 was released, so let's face it—our beloved GS3, once an iconic heavyweight in the tech arena, is almost as washed up as Sylvester Stallone.

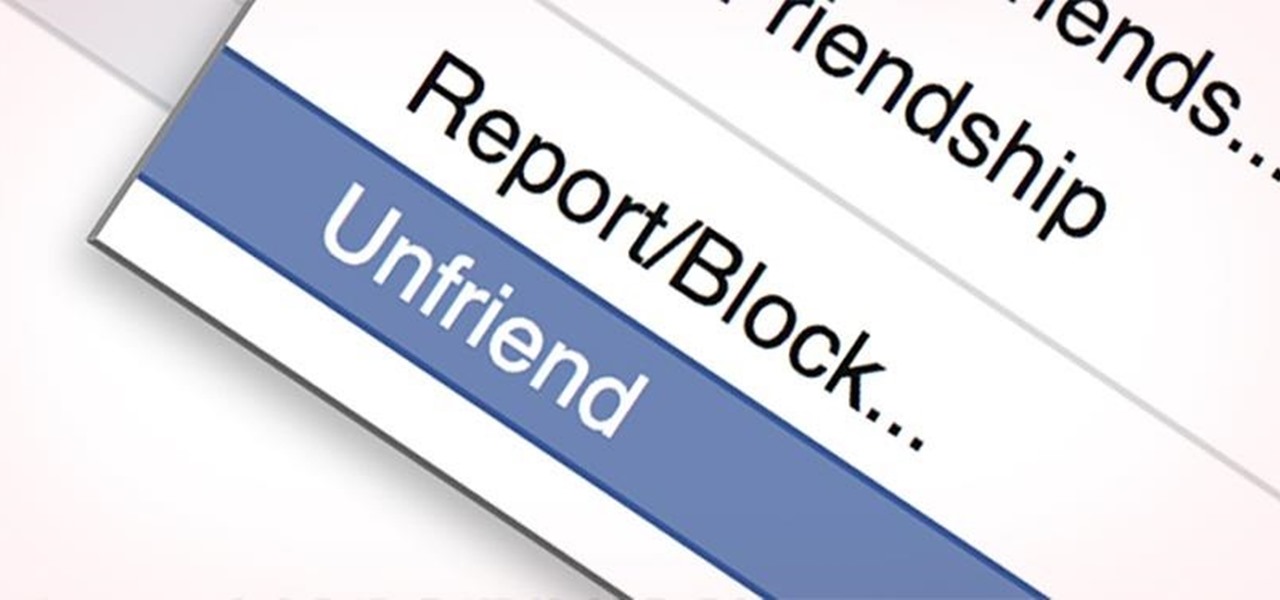
Admit it: you haven't talked to more than 70 percent of your Facebook friends in the last year. Whether you barely know the names crowding your friends list, or have vague memories of high school Spanish class with them, Facebook friends are easy to find and difficult to get rid of.

Someone does't really like you. I don't know who or where they are, but they exist. If you want to change that, simply ask them to do you a favor.

Erudite. Barbiturate. Cacophony. Denouement. Okay, that last word is technically French, but words like these make the average person sweat, and it turns out that the key to learning how to pronounce them once and for all just might be getting them wrong.

The international hit Xperia Z2 may be headed to Verizon if a posted, and quickly erased, image is any indication. Take this information with a grain of salt—I certainly am—but this could be Sony's entrance into the non-GSM realm. The image above was posted to Sony's Xperia Google+ page, and very quickly removed. Compared to the Z2 that's currently on the international market (below), we can see that not only has the Sony logo shifted to the bottom, but a Verizon logo rests squarely along the...

To flip, or not to flip, that is the real question. When you're nervously standing over the stove or grill, what do you do with that steak before you?

You've got to be sick of it by now. Those meaningless and unsatisfying articles, lists, and videos you were duped into clicking on because their headline made them impossible to resist.

A few days ago I finally finished my 2 week journey into trying to get OpenVas to work properly. You all may have noticed that you can't just click the setup openvas in kali and have it working properly.