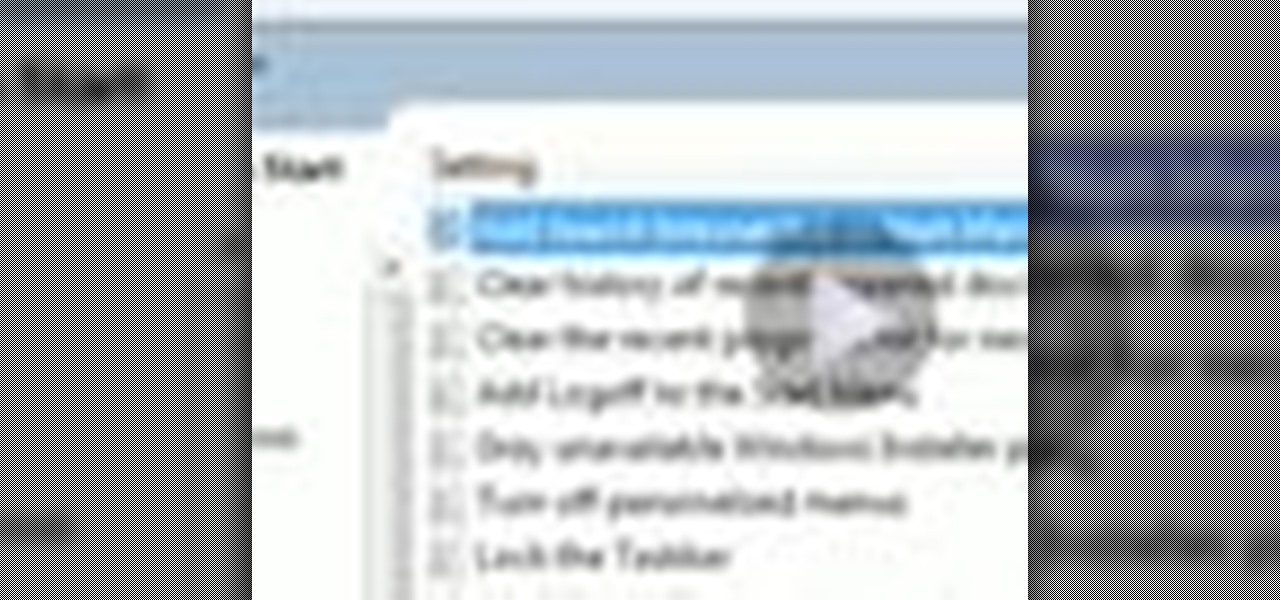
One of the cool things in Windows 7 is the new start menu. It is now possible to add an internet search area to your Start Menu. Instead of searching your computer, you can select a separate option called Search the Internet.
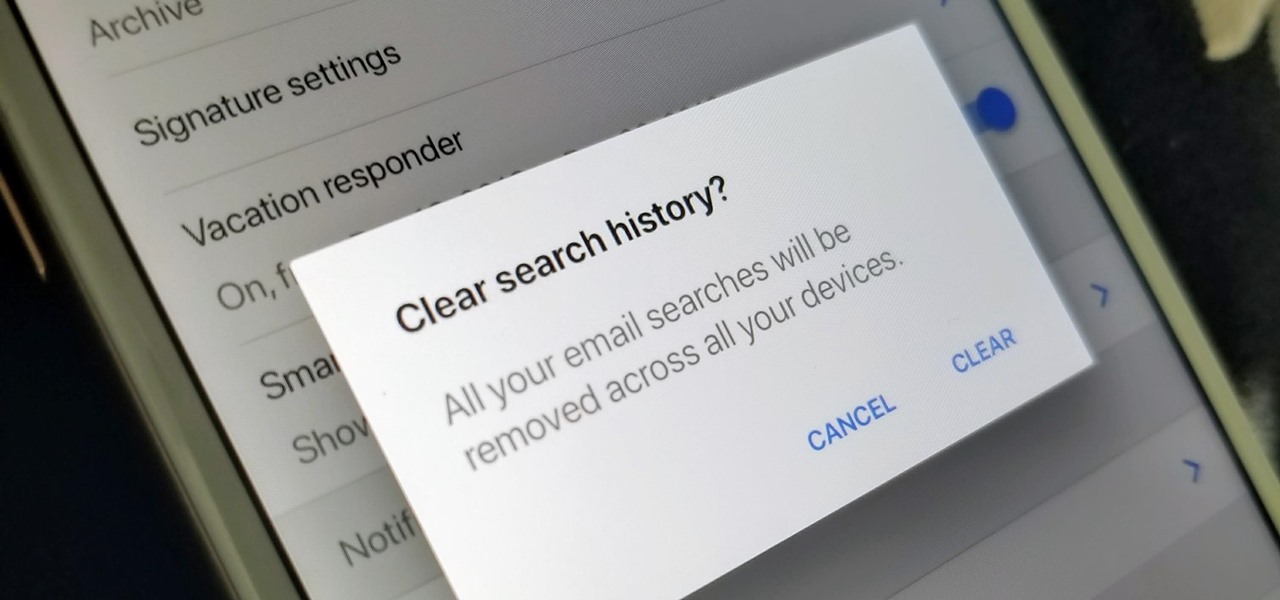
The Gmail app on both Android and iOS has a powerful search engine that helps you find any email with a few keywords. Even more impressive is Gmail's ability to remember previous search queries for future reference. However, this list of past searches can become extensively long and needs to be reset from time to time.

In my last how-to, we built a man-in-the-middle tool. The aforementioned script only established a man-in-the-middle. Today we'll be building a tool to utilize it. We'll be building a DNS packet sniffer. In a nutshell, this listens for DNS queries from the victim and shows them to us. This allows us to track the victims activity and perform some useful recon.

Now that we have our vulnerable server, it's time to start up BeEF. Getting Started

Privacy features have become quite the hot commodity, emerging from the aftermath of the NSA scandals that rocked the United States this past year. While the NSA has the means to gather information on all of us (regardless of any security software we implement), it doesn't mean that they're the only ones looking.

For Infinity Exists Full Disclosure's first Website Hacking episode, we demonstrate how to exploit a security vulnerability occurring in a website's database to extract password hashes. Sql (Structured Query Language) is a computer language designed for the retrieval and management of data in a system's database. The Attack, known as Sql Injection, manipulates Sql statements before they are sent to the Sql Server, allowing the Attacker to create, change, or retrieve data stored in the database.

For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and seeing all that glorious data displayed right in the browser. This is when more advanced techniques are needed.

The Operative Framework is a powerful Python-based open-source intelligence (OSINT) tool that can be used to find domains registered by the same email address, as well as many other investigative functions. This reconnaissance tool provides insight about your target through examining relationships in the domains they own.

Welcome back, my hacker apprentices! Although there is a multitude of different hacker types, the one target they all share is the database. I often refer to the database as the hacker's Holy Grail, or the ultimate prize for an effective hack.

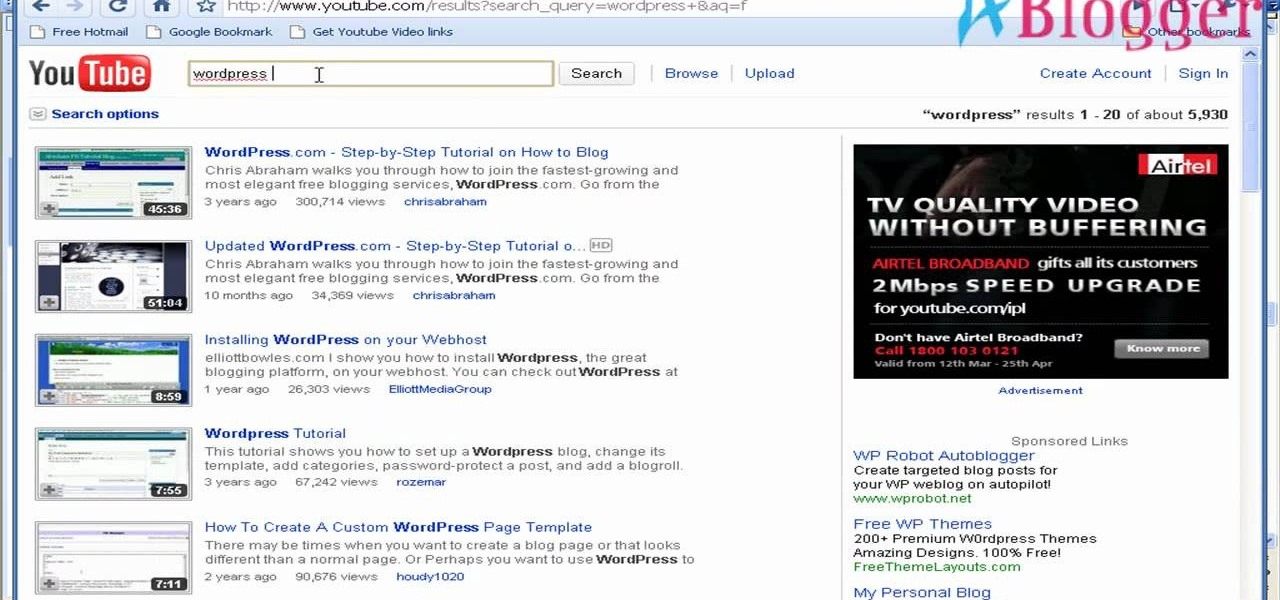
Searching YouTube is tough, because there's a plethora of content, so sometimes i's best to do an advanced search. This is not to be confused with the "search options" available during a YouTube search query, because those are limited to key features of YouTube, but not specific search terms. Much like Google, you can search YouTube via search operators. Many of the same search operators that work on Google work on YouTube also. Filter your results the way you want, not the way they want. You...

Crazy Taxi is a Facebook game that allows you to drive crazy in a cab. Watch this video tutorial to learn how to cheat and remove the traffic on Crazy Taxi (08/17/09).

Microsoft Excel is one of the most powerful programs for modern businesses. By allowing you to manage, sort, and analyze large collections of data, Excel provides an essential service for any company interested in using the power of data science to its advantage.

Aside from identifying songs with Shazam and using the "Hey Siri" feature while driving, Apple's personal assistant isn't something I regularly use on my iPhone.

Yosemite brought a new, Alfred-like Spotlight search to our Macs, but at times I still find myself wanting more out of it. However, after stumbling upon Flashlight by developer Nate Parrot, I am now able to perform Google searches, look up weather, and even enter Terminal commands straight from Spotlight's search bar.

People like Ralphige and The Jerky Boys have elevated prank phone calls to an art. Here’s how you can get in on the fun.

Need help tracing an IP address to a location? Well, Tinkernut has a clear and effect way to help out.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

Database technology has vastly improved the way we handle vast amounts of data, and almost every modern application utilizes it in one way or another. But the widespread use of databases naturally invites a slew of vulnerabilities and attacks to occur. SQL injection has been around for awhile, and as such, there are many defense methods in place to safeguard against these types of attacks.

Nmap is possibly the most widely used security scanner of its kind, in part because of its appearances in films such as The Matrix Reloaded and Live Free or Die Hard. Still, most of Nmap's best features are under-appreciated by hackers and pentesters, one of which will improve one's abilities to quickly identify exploits and vulnerabilities when scanning servers.

Thanks to Metaverse, it has never been this easy to create your own AR game.
Welcome back for another How-To on the Xbox Community Ambassadors World! In this How-To, we are going to tell you how to help someone the right way so you can get a 9/9 rating when your finished assisting someone! Lets begin, shall we?

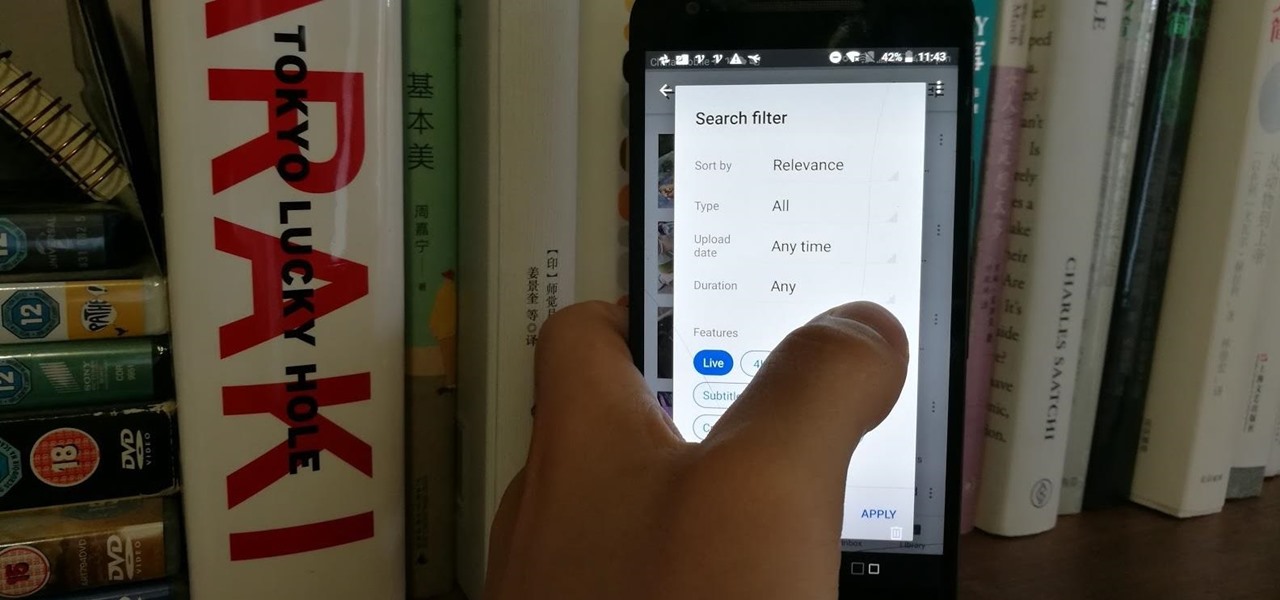
Have you tried searching for 4K HDR videos on YouTube, only to get 1080p videos just because the uploader used "4k" or "HDR" in the description? Or have you tried looking for a video about something that just happened, except YouTube's algorithm surfaces established videos first by default, so all the results you get are older than a month? Well, there's a better way.

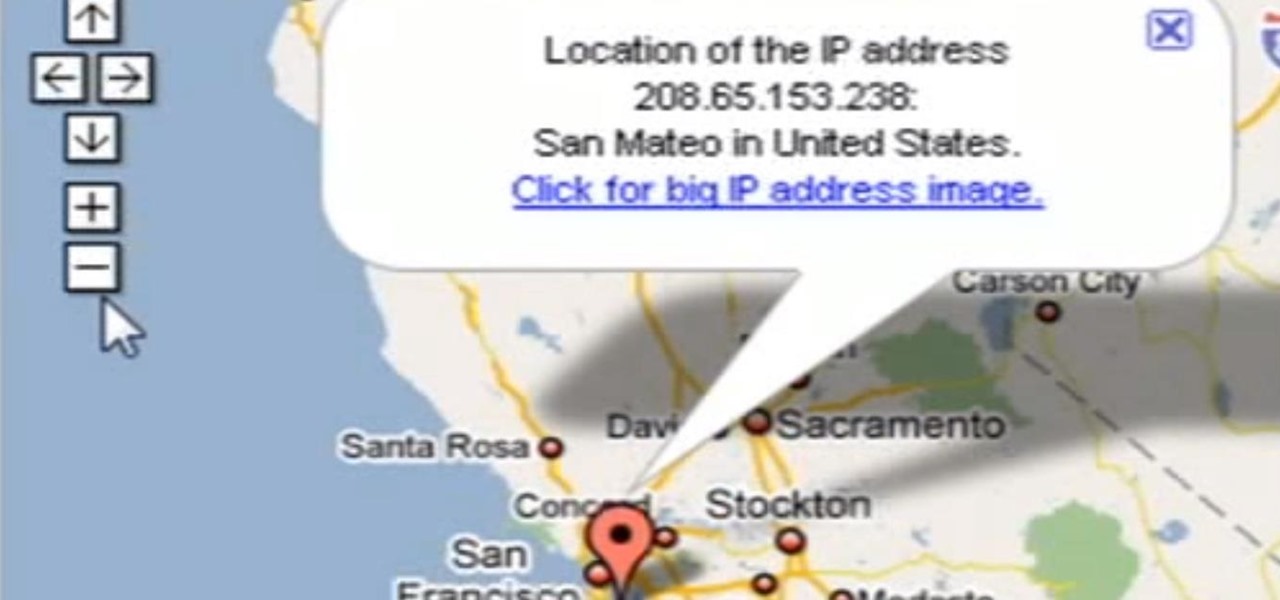
Welcome back, my tenderfoot hackers! Have you ever wondered where the physical location of an IP address is? Maybe you want to know if that proxy server you are using is actually out of your local legal jurisdiction. Or, maybe you have the IP address of someone you are corresponding with and want to make certain they are where they say they are. Or, maybe you are a forensic investigator tracking down a suspect who wrote a threatening email or hacked someone's company.

As Microsoft unveiled their new Windows Phone 8.1 software update yesterday, undoubtedly the most memorable takeaway was their showcase of Cortana. Competing directly against Apple's Siri and Google's Now, Cortana is Microsoft's entry into the digital voice assistant fray, and the official replacement to their search app.

You've probably used Google to search for recipes, or to find out what the heck that mystery food on the ingredients list is. But with all its built-in features, there are plenty of other ways the search engine can help you out in the kitchen.

If you're new to DreamCoder for Oracle, one of the things you may want to know how to do is to is write complex SQL queries. Happily, this tutorial will walk you, step by step, through the process. To learn how to use the DreamCoder for Oracle Query Builder, press play!

Since its launch in 2009, Google Apps Script has given creative thinkers the ability to perform light-weight application development within GSuite. Based on JavaScript, you can build your own simple tools that will increase your efficiency and productivity.

With group chats, arguments tend to devolve from a dispute between two people to a giant debate amongst all members. But before things get out of control, Telegram has a feature that can help.

With a new version of its ARCore in the wild and more than 30 devices now supporting it, Google is helping beginners get up to speed with augmented reality.

SoundHound, the Shazam-like song-matching service, recently announced a new mobile app called Hound, which wants to be your one and only intelligent personal assistant.

Now that we have control over a victim's browser, we need to use some attacks to maintain the connection, or even better: upload a shell.

Family Feud is one of the longest-running game shows in American TV history. Its viewer base spans generations, and this is mostly due to the fun nature of the show. Contestants have to guess the most popular answers to survey questions that were posed to 100 random strangers, and the responses often range from silly to downright funny.

Google continues to be the most commonly-used search engine for a reason. While continuing to stay ahead of the pack with advanced semantic search functions, Google even introduced Knowledge Graph results that offer key information without ever having to click a search result.

Facebook has always been notoriously difficult to customize. Personally, I think this is an improvement over MySpace's totally open platform (some people should not use code), but users should still have the option to change a few things if they want. While you'll never be able to choose your own background image or add an obnoxious number of aWeSoMe quiz results to your profile, there are a few browser plugins that let you at least change the color scheme.

Restaurant City is a Facebook game that allows you to create your own restaurant. Watch this video tutorial to learn how to hack the food quiz in Restaurant City with Cheat Engine (09/10/09).

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

If you need to scan a large number of domains for a specific web app vulnerability, Dorkbot may be the tool for you. Dorkbot uses search engines to locate dorks and then scan potentially vulnerable apps with a scanner module.

Open-source data scraping is an essential reconnaissance tool for government agencies and hackers alike, with big data turning our digital fingerprints into giant neon signs. The problem is no longer whether the right data exists, it's filtering it down to the exact answer you want. TheHarvester is a Python email scraper which does just that by searching open-source data for target email addresses.