Most users don't realize how much valuable data is in their network traffic. With a few simple tools, an attacker can quickly pick out cookies, passwords, and DNS queries from a macOS device as it covertly streams the victim's network traffic to the attacker's system. Here, we will cover two methods for analyzing packets flowing from a Mac.

Apple's own Photos app received some pretty amazing updates in iOS 11, but does iOS 12 have what it takes to one-up last year's Photos improvements? We think so.
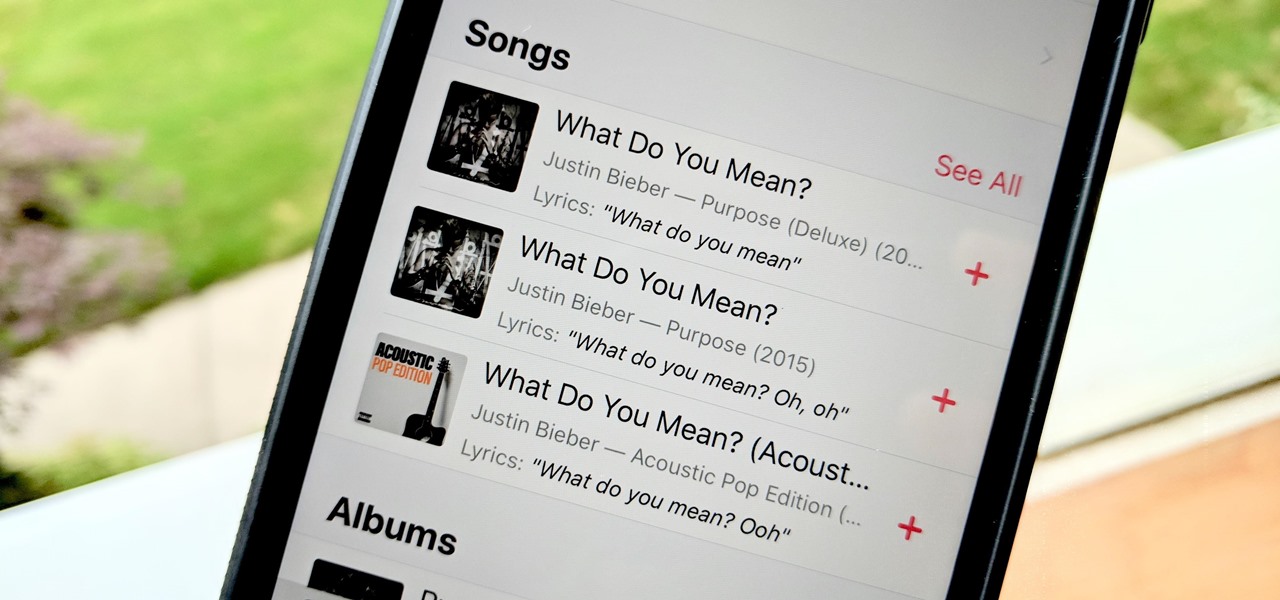
Has this ever happened to you: You're singing a song in your head and want to look it up on Apple Music but you just can't think of its name or even who recorded it? In iOS 12, if you can sing it, you can search for it, as the update lets you find songs in Apple Music by lyrics alone. It's like Shazam, only instead of identifying music by sound, it uses the lyrics in your head.

With Gboard, Google created a keyboard with more functionality than just inputting words. The app includes features such as GIF search and live text translation, but it gets even better when you let it learn more about you. With this data, Gboard grows from a good keyboard to one that can complete your sentences.

A new survey of game developers paints a somewhat less than rosy future for augmented reality gaming, but there's still some hope for its long-term prospects.

Among consumer brands, cosmetics companies rival furniture retailers as the quickest to adopt augmented reality as a means to help customers visualize how products will look before they buy them.

Whether you've stumbled upon an interesting location you want to bookmark for later, need to remember where you park your bicycle or vehicle, or want to keep track of your favorite food truck locations, Apple Maps makes it easy.

When you run an augmented reality company worth billions of dollars, backed by some of the biggest names in tech, and you haven't even released a product yet, even late night tweetstorms rank as worthy of dissection. Such is the case with Rony Abovitz, CEO of Magic Leap, who decided to spend a little time on Twitter on Wednesday to outline his vision of the future of immersive computing.

China's Baidu, the Chinese equivalent of Google, live streamed a video yesterday of CEO Robin Li riding a self-drive vehicle along the streets and highways of Beijing.

Google quickly learned over five years ago electric vehicles (EVs) were the powertrain of choice for its then fledging driverless car program and the industry has since followed its lead.

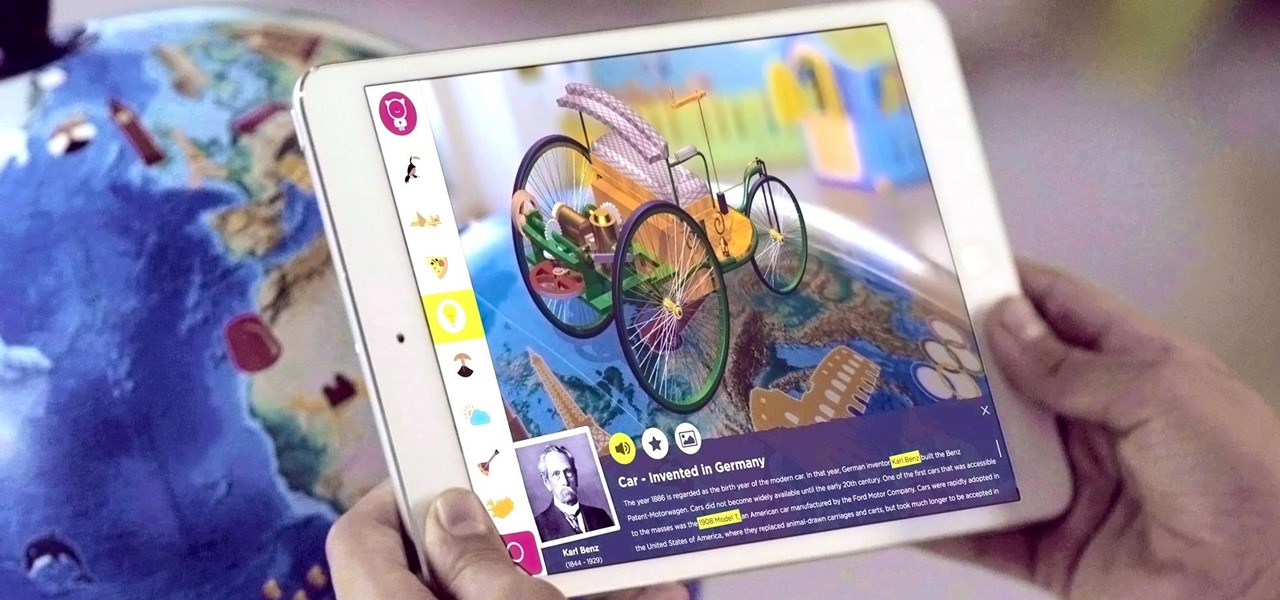
Globes used to be standard in households, usurped in many ways by modern mobile and desktop applications. But one company believes they can upgrade the globe for the 21st century.

Uber's driverless car program lead has quit after just one year working for the ride-hailing company.

Upskill, an enterprise software developer for industrial augmented reality applications, recently received an influx of funding and a major vote of confidence from two of their top customers.

There have been seven more people sickened from four states since the I.M. SoyNut Butter E. coli outbreak was announced earlier this month. The Centers for Disease Control and Prevention and Washington Department of Health have confirmed the I.M. Healthy SoyNut Butter was the cause of the outbreak in an update today.

Welcome back, my hacker novitiates! If you have been following this new Snort series, you know that Snort is the world's most widely used intrusion detection/protection system. Now a part of the world's largest network equipment company, Cisco, it is likely to be found everywhere in one form or another. This makes a compelling argument for learning how to use it, as it will likely be a necessity in any security-related position.

Samsung has been on a tear with its flagship devices since the release of the Galaxy S6; The S6 edge, the Note 5, and this year's Galaxy S7 models have all been met with universal acclaim, and even the staunchest of critics have almost nothing negative to say. Almost.

Hello fellow Nullbytiens, I'm Washu, a long time commenter but first time poster. Today we'll be making an IRC bot, if you haven't seen OTW's post about the new IRC channel I would encourage you to go check it out. He does a good job at explaining what IRC is and how to get set up.

Microsoft's new voice-enabled virtual assistant, Cortana, is a lot like a blend of Siri's personality and Google Now's predictive capabilities—but the best part is it's baked right into the taskbar in Windows 10.

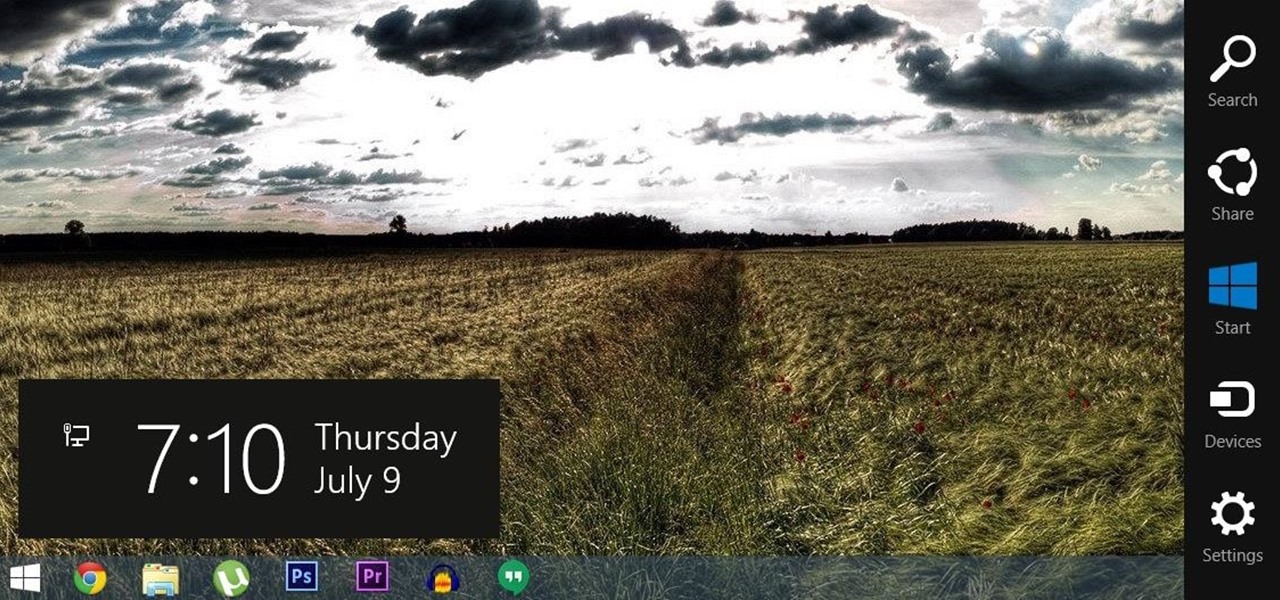
For all of the flak that Windows 8 received from desktop users, it certainly had some interesting and unique features. For instance, the "Charms" bar allowed you to easily access several key menus by simply hovering your mouse pointer in the top- or bottom-right corner of the screen.

This is a collection of various guides and tools available on the internet. Instead of searching for 1 you can easily find whaht your looking for here.

Let's say that we want to see what someone is doing on their computer? In this tutorial, we'll be hijacking cookie sessions to do just that!

I hate flying for two reasons. Firstly, I'm afraid of heights and turbulence is absolutely hellish. Secondly, I hate overspending on airfare. Flying can be unnecessarily expensive, especially if you don't plan ahead or must deal with inclement weather. Nevertheless, the travel season is almost here and we're always looking for the cheapest, most convenient flight. But what service actually provides you with exactly that?

Welcome back, my hacker novitiates! When we are trying to find vulnerabilities in a website to attack, we need a solid web server vulnerability scanner. Internet-facing web apps can open enormous opportunities for us as they are often riven with vulnerabilities and can often offer an entire point to the internal network and resources.

The new iOS 8 was just unveiled, and it looks pretty awesome. Apple showed off some of the enhancements and new features we can expect to receive in the fall at WWDC, and while not the huge facelift we saw with iOS 7, it does showcase what Apple does best—refinement. Continuity

Google is widely renowned for its mastery in using data to tailor specific search results and ads. Their Android and iOS search apps put this ability to use in finding the most relevant pages for your query, and their desktop site is the most-used search engine on the web as a result of it.

Google recently updated their TOS to reflect the email scanning practices they use in Gmail, which are used to display more relevant ads, among other things.

Google recently changed the way we search online, and from what I can tell, I'm not the only person online just a little bit irritated with the new design.

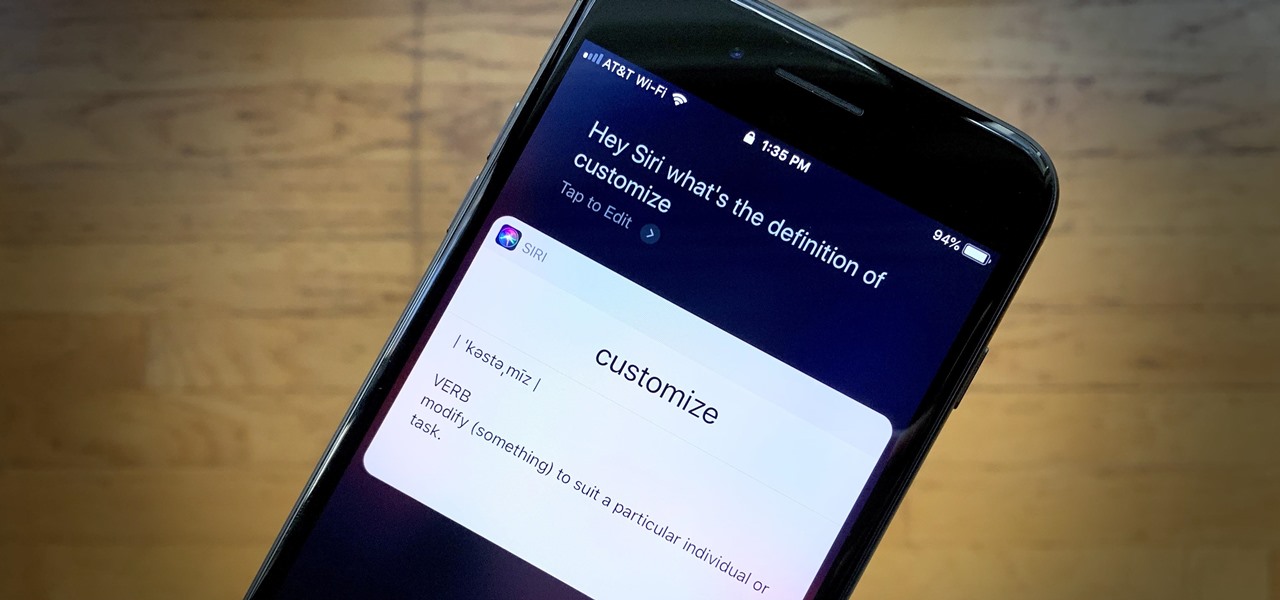
Out of the box, Apple's digital assistant could be a godsend or a nuisance, depending on your daily interactions it. No matter which camp you fall into, Siri can always be better suited to your personal needs with a little customization. You can make Siri a powerhouse not to be reckoned with, or you can minimize its presence if you only need Siri help sometimes — all without any jailbreaking.

Web applications are becoming more and more popular, replacing traditional desktop programs at an accelerated rate. With all these new apps out on the web comes various security implications associated with being connected to the internet where anyone can poke and prod at them. One of the simplest, yet the most prevalent types of security flaws found in modern web apps are SQL injections.

Apple's Podcasts app just got a big feature: transcripts. Before, you had to rely on third-party services or the off chance that podcast creators posted transcription links to each of their episodes. Now, you can view, read, and search show transcripts directly in Podcasts, whether uploaded from the creators or automatically generated by Apple.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.
Have you ever used an open wifi, which after you connect displays a website to enter your credentials to get internet? That website is called captive portal and widely used in airports, hotels, universities etc. Have you ever wondered what would happen if someone would set up an open wifi with the same name displaying a very similar web page asking for credentials? Usually if there are multiple wifi networks with the same name and encryption, devices only display the one with the highest sign...
Hello and welcome to my article. I have made this article for anyone who wants to become a hacker, and wants to know how to get started.

Google, you have something that I want. You may think you have some idea of what you are in possession of, but you do not. In a few moments, it will be mine...and it can be yours, too, dear readers.

I've been steadily making my way through the series Hannibal, which arrived on Netflix in June. I've just now made it to the back half of the third season, which introduces us to a new villain who (spoiler alert) seeks to become the Great Red Dragon.

Data analytics is one of the hottest fields around. With so much data at our fingertips, top companies are seeking experts to put all of this information to real-world use.

While conducting an OSINT investigation, it's important to be able to pull in information based on any clue you uncover. In particular, license plate information can turn up everywhere, from photos to live data to on your own street. You could use that data to find the VIN, see if a Tinder date has hit anyone, find out who's blocking your driveway, and so on. Skiptracer can help get the ball rolling.

If you made a resolution for 2020 to get healthier, it's essential to concentrate on your mental health just as much as you do on physical fitness. Running and exercising is great, but a sound mind is integral to a healthy and balanced life, and you can improve your emotional and physiological well-being with your smartphone.

While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the internet for clues during an investigation. These are a list of my top ten favorite browser extensions for hackers — and how to use them.