How to use quotation marks in British EnglishIn this video we are about to see how to use quotation marks in British English. This is a very useful video because most of us confuse the usage of quotations and the meaning it renders. There are two forms of quotations single and double. A single quote contains only one inverted comma and the double contains two inverted commas. A double quote is used for direct speech or actual quotations. Whenever a person says something a comma is given and t...

This is working about working with sources: Quotation, Summarizing and Paraphrasing. Quotation: When directly quoting an outside source, the author's words should be taken verbatim. Quotation can lend the essay credibility. Too much quotation makes it sounds like you, the writer don't have anything to say. Quotes should be used only when the writer needs to be precise, clear, and powerful. You should use the quotes when the person you are calling said in a unique way that really can't be put ...

In this Education video tutorial you will learn how to cite your sources in different citation styles. What does your professor mean when he or she says, "Don't forget to cite your sources"? Most citation styles require that you include intext citations, which may be footnotes or parenthetical citations. A footnote directs the reader to the bottom of the page for the source of the quotation or idea. A parenthetical note directs the reader to the bibliography at the end of the paper to see the...

In this Language video tutorial you will learn how to report another person's words. In other words how to restate what someone else said. This video focuses on two aspects. #1. What's the difference between quoted and reported speech? #2. When can we use say and tell? In quoted speech you quote the exact words spoken by a person within inverted commas or quotation marks. It is also called direct speech. Here is an example. Jennifer said, "I like birthdays." Whereas, reported speech does not ...

Plagiarism in some schools and universities is major offense and can even get you kicked out of school all together. Plagiarism occurs when ideas or words that you advance as your own have actually been taken from other people. In this video, learn how to avoid plagiarism and make the words you write, your own.
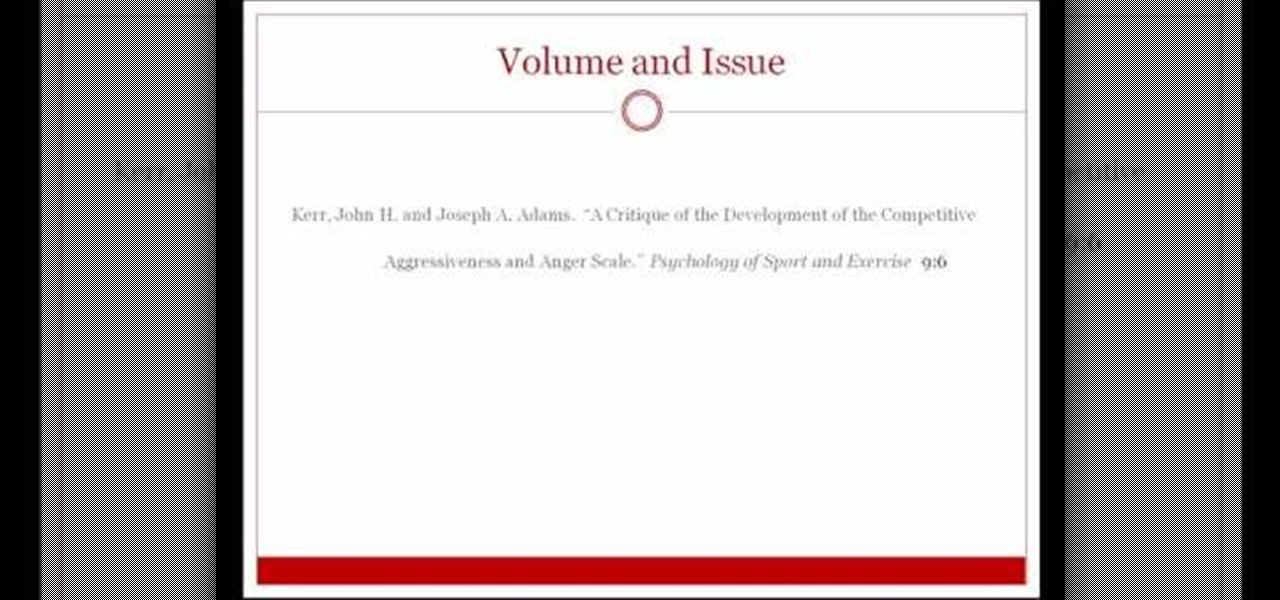
This video shows viewers how to properly cite scholarly journal articles in the MLA format. In your works cited page, the citation should begin by placing the author's last name first, followed by his first name. If there are multiple authors, all subsequent authors should have their first name first followed by their last name. Placing a period after this, the next item is the title of the article, placed in quotation marks and followed by a period. The name of the scholarly journal is place...

In this Googler's guide from the folks at Mahalo, we learn how to use quotation marks when searching for a name on Google Search. For all of the relevant details, and to get started Google stalking your own friends and acquaintances, watch this video tutorial.

Find MP3 files using Google by typing in the name of the song using quotation marks. Locate MP3 files with tips from a professional musician in this free video on music.

Get that song you heard on the radio out of your head and into your record collection with this how-to, which will teach you how to find song information using the Google search engine. Find a song by accessing the Internet and typing in lyrics using quotation marks. Learn to find a song with tips from a professional musician in this free video on music.

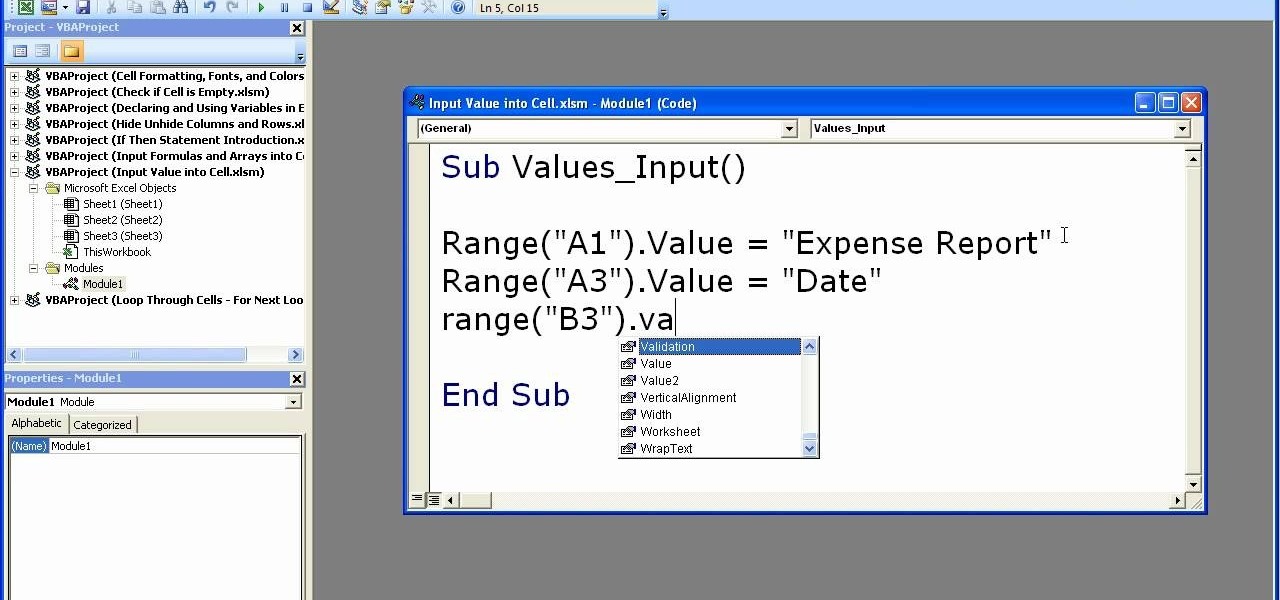
This video shows how to enter values into cells using Excel macros and Visual Basic. This includes a sample Expense Report that is used in this demonstration. In this demonstration, we will create the macro that inputs a title as "Expense Report", Three columns i.e. "Date", "Item" & "Amount", and the summery field as "Total Expenses", as well as the formulas located at the respective cells. Now, we're going to use two keyboard shortcuts i.e. "Alt + F11" to open-up the VBA window and "Alt + F8...

In this tutorial, we learn how to use quotes in an essay. When using a colon, you will set up the quote, then present it as proof of what you have just said. Note that the phrase before the quote could stand on its own as a sentence. For partial quotes, remember when summarizing to embed the author's words in your own sentence. If you take away the quotation marks the sentence should flow like you wrote it. When using commas with quotes, you can introduce the quote with an introductory phrase...

To start with you have to write the author's name, with the last name entered first followed by first name and then the period. Title of the article should be in quotation marks. Do not use italic format. Title of the actual journal must be written. After this there is a series of numbers the volume number, issue, year, pages number separated by a colon. Don’t write 'p' for pages as the number itself is a standard for it. Write the period and also the dates.

Bash scripting is a convenient way to automate things on any Linux system, and we're going to use it here to automate certain tasks we use all the time.

The Google Play Store hosts the largest collection of mobile apps on the planet, and it's the default app store for almost all Android devices. Ironically, though, while Google made its name with a powerful search engine, it can sometimes be difficult to find what you're looking for on the Google Play Store.

Hello all! In this tutorial, I'd like to show you one way of getting root on OS X. Check out this GitHub page for a recent privilege escalation exploit that was recently discovered. I've tested it and it works on both OS X 10.9 Mavericks and OS X 10.10 Yosemite, but appears to have been patched with OS X 10.11 El Capitan. If you check out the file main.m you can see where most of the magic is happening. This source code can very easily be changed to make it do more than just the system("/bin/...

Welcome back, my hacker noviates! In a recent post, I introduced you to Shodan, the world's most dangerous search engine. Shodan crawls the globe from IP to IP address, attempting to pull the banners of each web-enabled device and server it finds.

Hello Everyone Today in this post I will teach you how to get a banner for your terminal.(Video Available at the End of the Post) To get a banner first we need "figlet" and then we have to configure it. Its Easy ..

Plagiarism is a serious offense, even if you are copying from the web. With this tutorial, learn how to cite websites properly using MLA format and avoid any trouble.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

There is no shortage of defenses against cross-site scripting (XSS) since it is so prevalent on the web today. Filters are one of the most common implementations used to prevent this type of attack, usually configured as a blacklist of known bad expressions or based on regex evaluation. But there is hope with a wide variety of techniques that can be used to defeat these filters.

By using almost any packet-crafting tool, a hacker can perform denial-of-service (DoS) attacks. With the power to create just about any packet with any characteristics, a hacker can easily find one that will take down a host or network. Nmap and Hping are effective packet manipulation tools, but there's also Scapy, which is almost infinitely customizable.

In many programs on Linux, you'll come across programs which allow you to specify additional arguments instead of just simply running the program by itself. If you've used the Kali distribution, I'm more than certain you'll have come across these with the command line tools, else if you have been following these tutorials, we have already come across three tools which also use the same technique, i.e. gcc, gdb and wc. How do we do this with C? Let's find out.

What's up guys! It's time to discuss strings in more detail. Review

I spend a lot of time helping friends and family with their tech problems, like clearing a browser's cache, scanning a Windows computer for malware, and speeding up a Mac. However, the issue I deal with most frequently revolves around forgotten network passwords.

Having trouble getting a strong Wi-Fi signal on your Samsung Galaxy S3? Does the signal drop out on you when changing rooms? Frustrating, isn't it?

The Pixel and Pixel XL both use AMOLED screens, which are noted for their deeper blacks and sharper contrast ratios when compared to traditional LCD panels. However, AMOLED displays still have one fairly major downside, and that's the fact that they're vulnerable to screen burn-in.

This guide will explain how to configure a USB Flash Drive / Memory Stick so that you can run a keylogger within just a few seconds of plugging it in any computer.

There are a lot of songs out there, so it's tough to remember all of the words to every song you like. If you're like me and have a less-than-perfect memory, visual aids will ensure your Apple Music jams aren't interrupted with incorrect or forgotten lyrics. That's why Apple's update with time-synced lyrics is so cool, essentially turning your iPhone into a portable karaoke machine.

Welcome back, everyone! In this lesson, I'm going to go over the use of the echo function and variables, as well as basic syntax.

Hello everybody Joe here. Today I will be demonstrating how you can find XSS vulnerabilities in a website and what you can do with them

Welcome back, my hacker novitiates! There are many ways to hack databases, and most of these techniques require SQL injection (SQLi), which is a way of sending SQL commands back to the database from a web form or other input. In this tutorial, we will use SQL injection to get access to the underlying server. So instead of getting access to the database and its data, we will use the database as an intermediary to gain access to the underlying server.

You can check stock quotes, make quick calculations, see the weather forecast, get reminders, and view upcoming calendar events all from the Notification Center on your Mac. But if that's all your using it for, you're just barely scratching the surface.

Welcome back, my budding hackers! As you know, I firmly believe that to be a true professional hacker, you need to be proficient in Linux. This is for a number of good reasons.

Every Windows system includes command prompt; and while a lot of people on Null Byte and WonderHowTo in general know how to use it, some people don't know anything about it, even how to access it.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

Code execution in Microsoft Word is easier than ever, thanks to recent research done by Etienne Stalmans and Saif El-Sherei. Executing code in MS Word can be complicated, in some cases requiring the use of Macros or memory corruption. Fortunately, Microsoft has a built in a feature that we can abuse to have the same effect. The best part, it does so without raising any User Account Control security warnings. Let's look at how it's done.

Welcome back, my greenhorn hackers!

Welcome back, my greenhorn hackers! I recently began a series on scripting and have received such positive feedback that I'm going to keep this series going. As I've said before, to graduate from the script kiddie to the pro hacker, you'll need to have some scripting skills. The better you are at scripting, the more advanced your hacking. Ultimately, we are leading up to developing the skills to build your own zero day exploits.

Why can't I see who is stalking my Facebook profile?

Net neutrality is dead and your internet service providers can collect all the data they want. While VPNs are a great way to protect some of that privacy, they're not perfect. There is another option, though, called Noisy, which was created by Itay Hury. It floods your ISP with so much random HTTP/DNS noise that your data is useless to anyone even if they do get it.