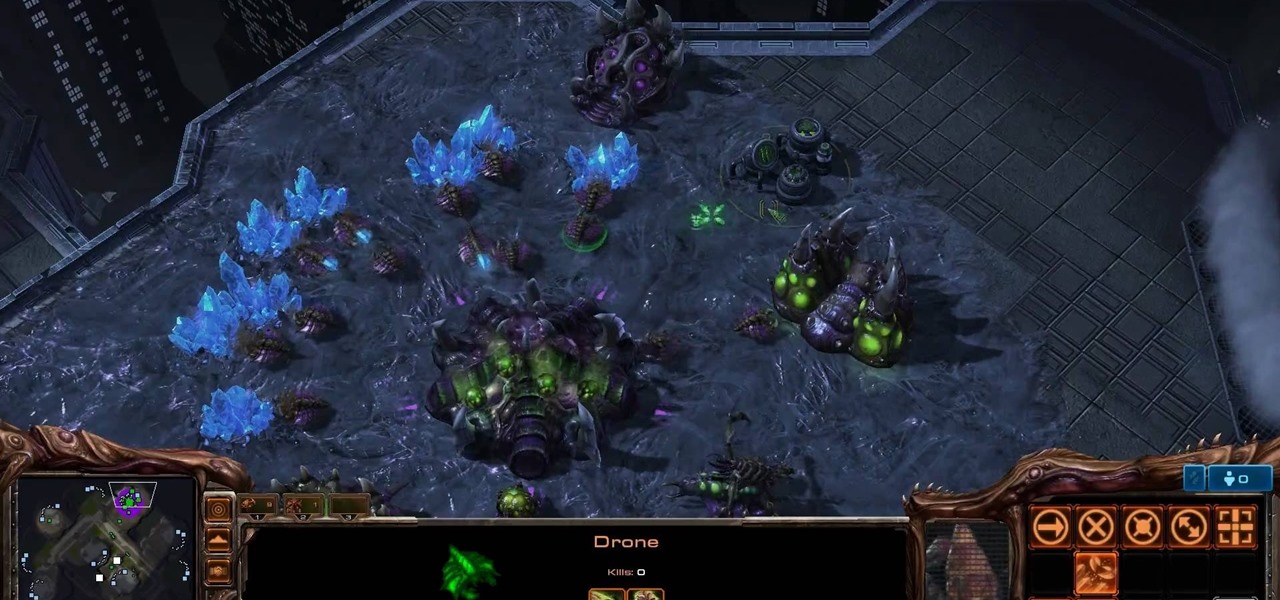
This is a quick Zerg tutorial for the upcoming StarCraft 2: Wings of Liberty game using the StarCraft 2 Beta game. HuskyStarcraft gives you all the advice needed for the standard Roach opener with the Zerg race. It's a really great build to your own friends. Check out the build order below.
HipHop for PHP is a source code transformer that allows you to optimize your PHP code easily, which will allow you website to run faster on less server space. This video is a record of a seminar on using HipHop done by a Facebook employee who had a hand in it's development. If you make websites using PHP, this will be very good stuff for you to learn.

Before you know it, Valentine's Day will be here. Or your boyfriend's birthday. Or your two year anniversary. And while buying the newest techie gadget for your boy will earn you a gold star on your head, you can truly get his heart racing by making him a pair personalized boxer shorts.

This how-to video is a vibrant and animated tutorial on how to paint children’s furniture: in particular, a little girl’s tea table and chairs. It’s fast paced yet easy to follow. The video couple takes you from the taping and preparation of the table and chairs to the completed and professional quality finished product, which would thrill any little girl. Their method of communicating the most important steps is to race to the camera and speak to the audience, in an amusing sort of wink, whi...

This video is demonstrated completely through visual movement and accompanied with a brief written description. A young man speeds down the soccer field with a ball and scores a goal. His signature move leading up to the goal is broken down into very specific methods of movement, the first of which is a high speed attack as he races down the field. The next method to this signature move is the weight shift, in which the goal scorer shifts his weight, along with the ball, from foot to foot to ...

Need to make an newsletter for your company or business? It's really not that hard to do, if you know a little bit about HTML coding. Ryan Quintal and the Email Dance House sits you down and shows you how easy it is to make a custom HTML email from design to Constant Contact.

In this instructional video brought to you by Lowe's, a leader in the home improvement retail business, host NASCAR driver Jimmie Johnson, demonstrates how to create and customize a pinewood derby car with the help of a Dremel tool. New and experienced enthusiasts in the pinewood derby arena will appreciate the level of detail and tips found in this video. Whether you are building a car for yourself or your kids anything you could want to know about creating a pinewood derby car can be found ...

If you're fond of remote-controlled vehicles, you might appreciate this video tutorial on how to modify gearing on a Traxxas Rustler R/C vehicle. The Traxxas Rustler is a proven favorite with a formula for rugged fun that nothing else can touch. The Rustler blows the doors off the competition with more power, smoother control, better grip, and performance that makes it one of the fastest Ready-To-Race electric trucks available. Modifying the gears is an easy way to boost top speed. You can in...

This lesson in boffer sword fighting with the Knights of Gray is the most important of them all! This video tutorial for all you LARPers out there focuses on the rules and the code of foam boffer weapon fighting.

Whether you're looking to add a substantial coding foundation to your hacking skill set or want to get a job in programming and development, knowing one or two programming languages just isn't going to cut it.

A stager is a small piece of software that's typically used by malware to hide what's happening in the early stages of infection and to download a larger payload later.

A lot of time can be wasted performing trivial tasks over and over again, and it's especially true when it comes to hacking and penetration testing. Trying different shells to own a target, and testing out privilege escalation commands afterward, can eat up a lot of time. Fortunately, there is a tool called One-Lin3r that can quickly generate shells, privesc commands, and more.

One of the first steps when pentesting a website should be scanning for hidden directories. It is essential for finding valuable information or potential attack vectors that might otherwise be unseen on the public-facing site. There are many tools out there that will perform the brute-forcing process, but not all are created equally.

We've already shown you our favorite new action games that have come out this year, but now it's time to share our all-time top ten list. These games are available for both Android and iPhone, they don't have intrusive ads or freemium schemes, and most importantly, they're all completely free to play.

It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to throw off any investigators is to change the file attributes to hide activity. We can do this with Metasploit's Timestomp.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

QR codes have become a staple in our everyday lives. Companies use them for everything from marketing promotions to movie tickets thanks to security they provided for these types of transactions. But for years, Android users had to download an app to scan these codes. Well, not anymore.

Cross-site scripting can be one of the easiest vulnerabilities to discover, but to be successful with this type of attack, it is essential to learn how to get past filters. In the previous guide, we explored some ways to do this, such as abusing attributes and event handlers and tricking the application into accepting unusual characters. Now, let's take a look at more techniques used to defeat filters.

Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.

Uber is one of the best ways to get around, but nobody said it was cheap. What's even more infuriating is when you have a bad experience with a ride. Sure, you can get a refund, but then you need to figure out where to enter in the promo code for the coupon that Uber sends your way.

Like Costco's price codes or the tags on your bread, the numerical codes printed on those sticky little fruit and vegetable labels can reveal a lot of information to us consumers. Once you understand the codes, you can look at that little label (also known as PLU, or "price look up" label) and know whether the produce you're about to buy or eat was treated with pesticides, genetically modified, both, or neither. Before we go any further with deciphering the codes on these labels, let's take a...

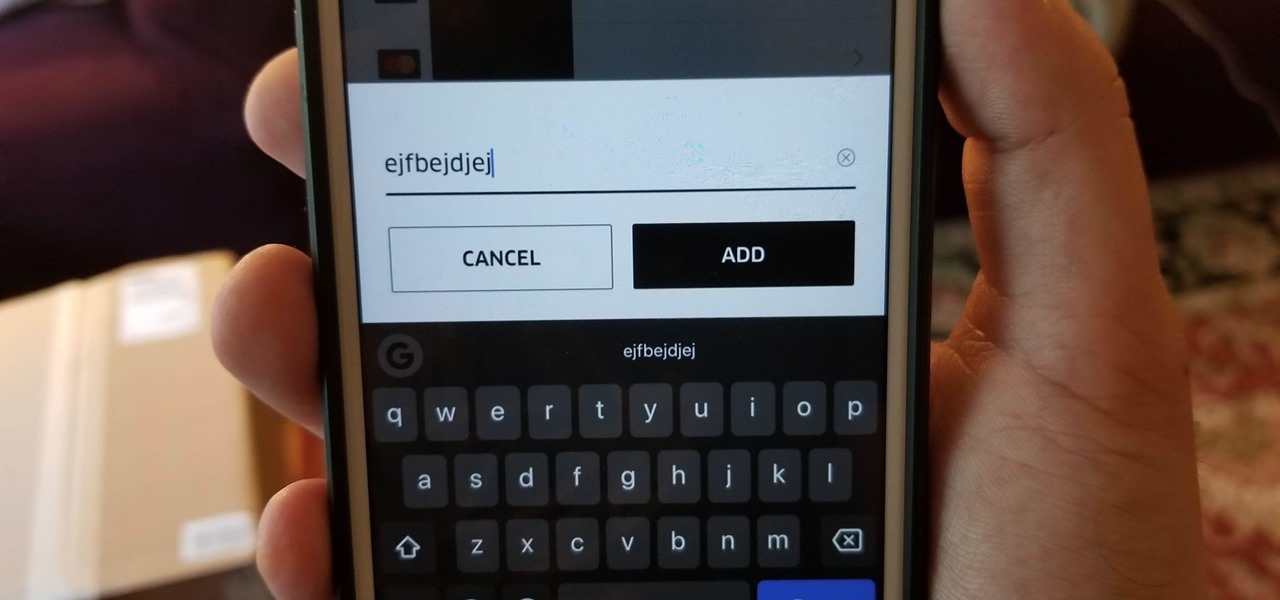
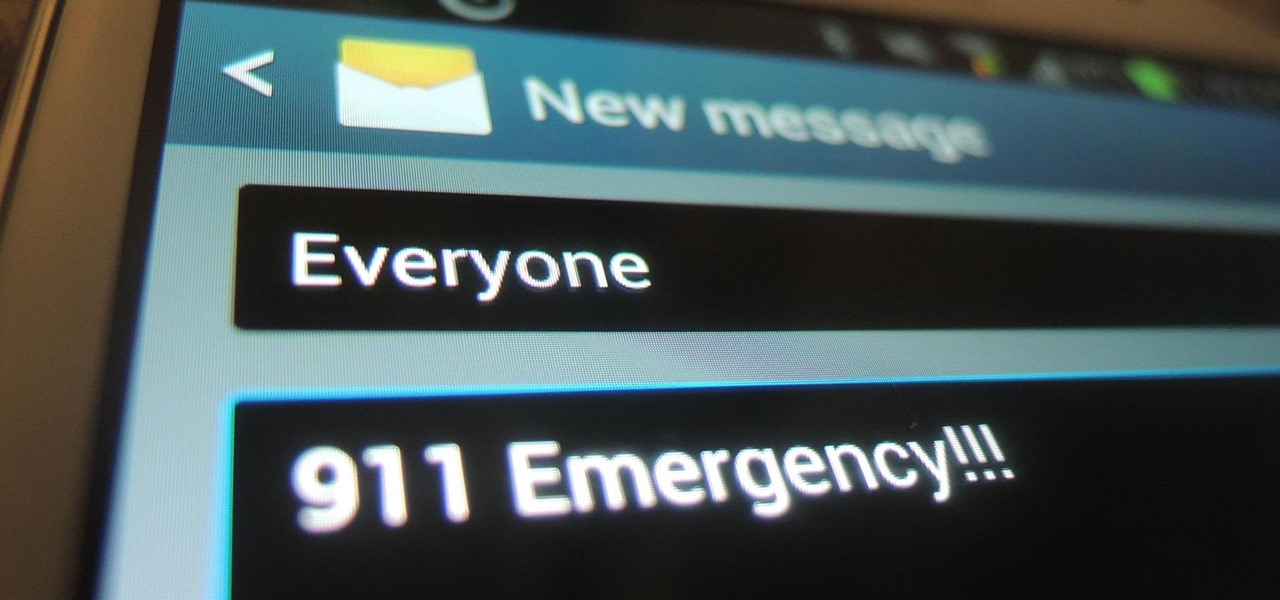
Just because your Samsung Galaxy Note 2 is on silent doesn't mean that the world stops spinning. Emergencies can pop up at any time, even when your phone is put away during a lecture in class, in the library, or at an important business meeting.

We all know about partying like it's 1999, but what about gaming like it's 1999? The folks over at Irrational Games, the studio behind the new BioShock: Infinite, which was just released today, decided to go a little retro and include a hidden game mode for the most hardcore gamers. By default, the game starts out with the normal Easy, Medium, and Hard difficulties, with "1999 Mode" made available only after you beat the game. But if you enter in one these secret Konami codes provided below, ...

John Roy demonstrates the tutorial to view or retrieve layouts that ens with .swf. SWF files can be viewed by pasting the url in the address box.

In order to create a custom caption box in WordPress you'll need to go to your dashboard. Here click on appearances, then on editor. Now over on the right select the sidebar option. Here you'll see some code, what you need to do is find the word that you want to replace on the main page, you can use ctrl+F to find the word. When you've found it within the code just replace it with whatever you want and then press the 'apply' button. You'll see that the main page will now be displaying the wor...

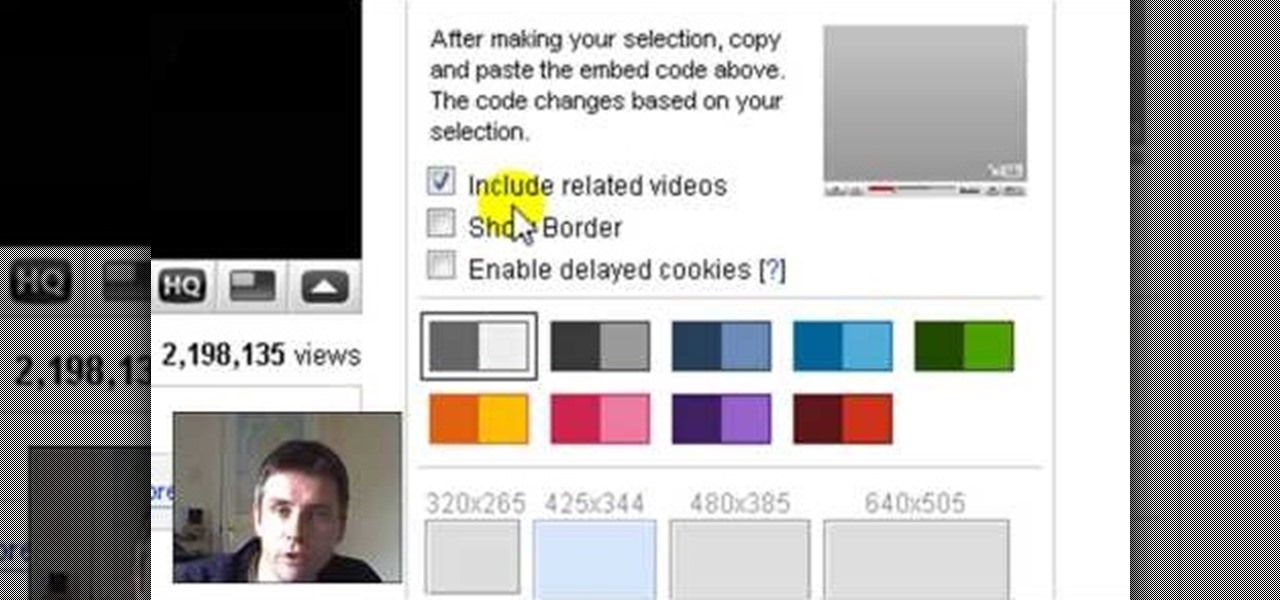
Learnasyouwatch shows viewers how to automatically play YouTube videos. First, you need to open your web browser and go to YouTube. Find the video you want to automatically play or upload your own video to YouTube. On the ride bar there is a section that says 'Embed'. Click on the pin wheel icon next to it that is 'customize' and you can set various parameters. Now, you need to copy the embed code and right click and copy this code. Paste this code into a word document. You will need to add '...

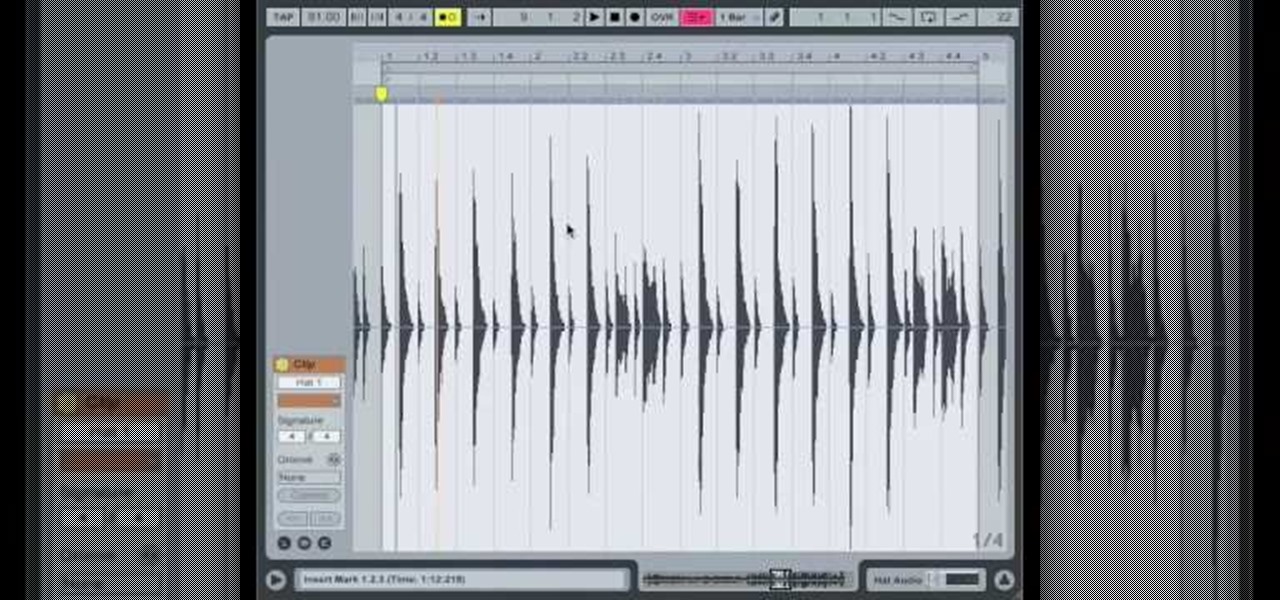
In this video, we learn how to use Ableton Live 8: Quantizing audio. To find the bars you want to use, find the up and down arrow keys. These will jump the loops back and forth based on the width of the loop race itself. Press play to search around for the best four bar section in your music. Now, set your first attack in your loop by zooming in on the hit. Hover over the audio and create a warp marker to drag from each of the bars. Label it as the beginning of your clip to the end, then save...

Learn how to personalize birthday cards with this informative video! This tutorial will show you how in just a few steps, you can make a race car birthday card with the help of a simple pattern. Why go out and buy a card from the drugstore that looks like everyone else's when you can create something unique for your birthday boy? All you will need to make this fun card is some colorful card stock, the Cricut racer paper doll pattern, glue, and a little time. This video also shows you how you ...

How to hack Yoville! Yoville cheats, tricks, hacks. Yoville is a game that can be played on Facebook or MySpace. In the words of Yoville's Facebook app, YoVille is a world where you can buy new clothes for your player, purchase items for your apartment, go to work, and meet new friends. Yoville is a city building simulation game.

I may be a bit weird, but I enjoy listening to music at night as I fall asleep. Sure, you could create a playlist of songs so that it stopped after all the songs finished playing, but I have a rather extensive database of music and I enjoy listening to them randomly. Also, I like to ensure it terminates after a specific amount of time (I don't want it playing all night). Or sometimes I use it when I am cooking so that when the music stops, I know I need to check on my food, etc.

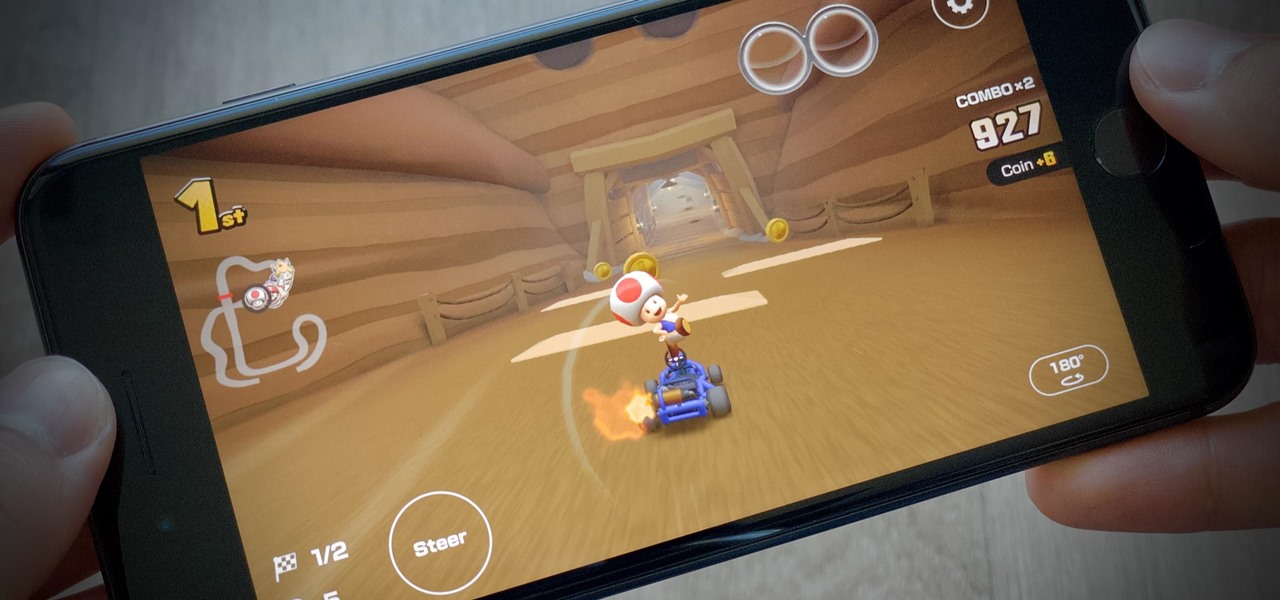
Nintendo's decision to add landscape mode to Mario Kart Tour makes the game feel more like the real deal. That said, it can be annoying to rotate your phone every time you want to play in landscape orientation. It can be even more annoying when the game switches between landscape and portrait view in the middle of a heated race. Luckily, there's a way to make sure every competition is played in widescreen.

Password cracking is a specialty of some hackers, and it's often thought that raw computing power trumps everything else. That is true in some cases, but sometimes it's more about the wordlist. Making a custom, targeted wordlist can cut down cracking time considerably, and Wordlister can help with that.

Privilege escalation is one of the essential skills a hacker can have and often separates the newbies from the pros. With a continually changing landscape and a plethora of exploits out there, it can be a problematic aspect of any attack. Luckily, some tools can help expedite the process. Linux Exploit Suggester is just one of many to help you get root.

There are many password-cracking tools out there, but one of the mainstays has always been John the Ripper. It's a powerful piece of software that can be configured and used in many different ways. Metasploit actually contains a little-known module version of JTR that can be used to quickly crack weak passwords, so let's explore it in an attempt to save precious time and effort.

Hashes are commonly used to store sensitive information like credentials to avoid storing them in plaintext. With tools like Hashcat, it's possible to crack these hashes, but only if we know the algorithm used to generate the hash. Using a tool called hash-identifier, we can easily fingerprint any hashes to discover the right Hashcat mode to use to retrieve a password.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

Correctly identifying the underlying technologies that run on a website gives pentesters a considerable advantage when preparing an attack. Whether you're testing out the defenses of a large corporation or playing the latest CTF, figuring out what technologies a site uses is a crucial pen-tester skill.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

MouseJack vulnerabilities were disclosed over three years ago. Some wireless keyboard manufacturers have since issued firmware updates, but millions (if not billions) of keyboards remain unpatched worldwide, either because they can't be updated or because the manufacturer never bothered to issue one.