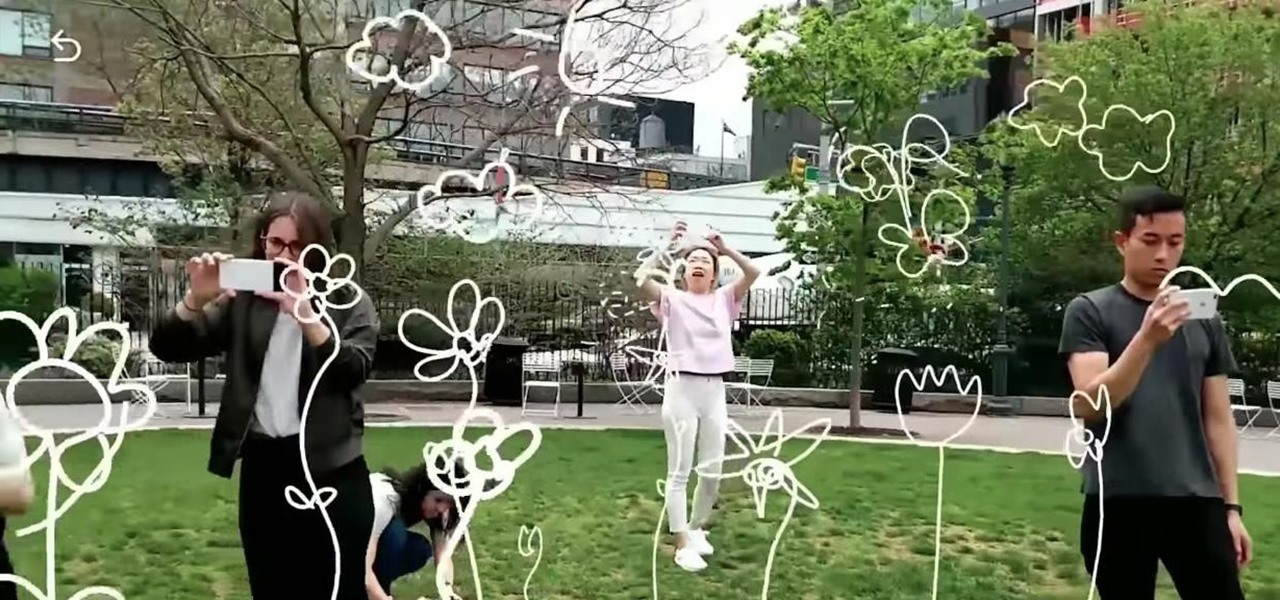
This is a walkthrough of the final moment as one achieves Warrior Hero and the title of Omnipotent. This is an ultimate goal in Spore that happens during the Space Stage of PC game play. This is a good insight into how to beat the game.
This is a walkthrough of the hunt for our solar system and home planet Earth. The searching is fast forwarded. Saw a picture on the net of a vague location of where it might be. This is an Easter egg in Spore.
With Spore you can nurture your creature through five stages of evolution: Cell, Creature, Tribe, Civilization, and Space. Or if you prefer, spend as much time as you like making creatures, vehicles, buildings and spaceships with Spore’s unique Creator tools.

Motorcycles are two-wheeled motor vehicles that are used for cruising, racing and other recreational activities. Learn the basics for riding motorcycles from an experienced motorcyclist in this free sports bike video series.
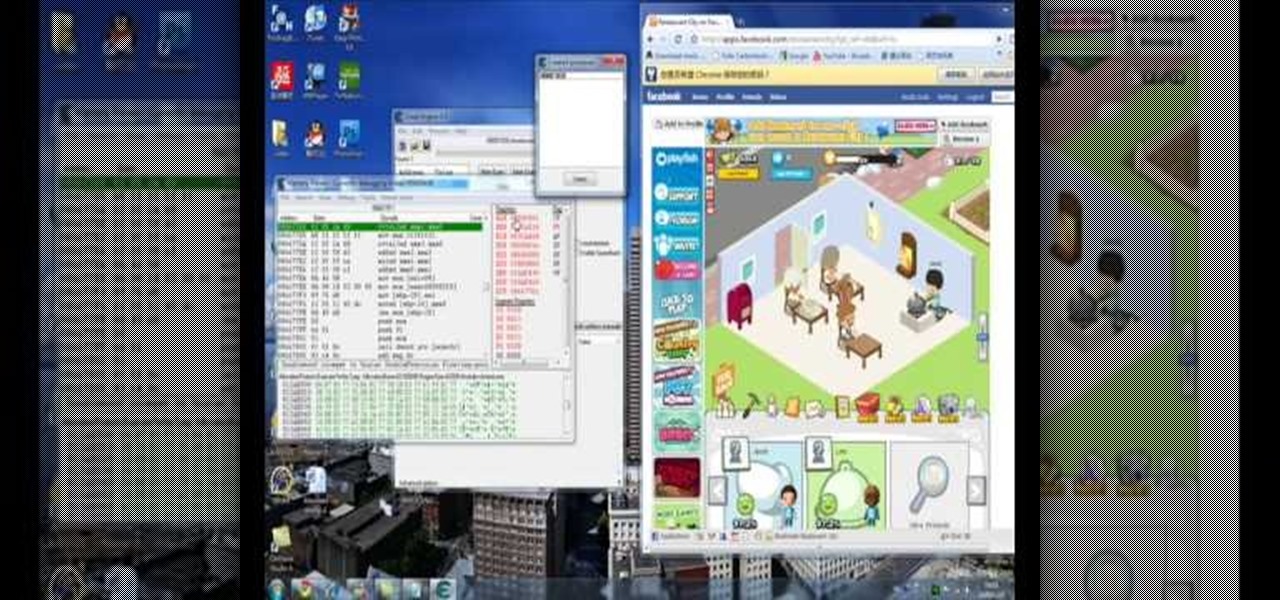
Open up Cheat Engine and be prepared to hack Restaurant City! This is a new level hack that will help you gain levels fast.

Your iPhone is fairly secure by default, but Apple's Lockdown Mode takes it to Fort Knox levels of protection. If you're a high-value target for spyware, phishing attempts, and other sophisticated cyberattacks, it's an essential feature. But for almost everyone else, it's an extreme move. If you simply want to verify someone's identity when chatting, Contact Key Verification is a more practical option.

After dipping its toes into the AR cloud arena last year, Ubiquity6 is now jumping in with both feet this year.

The USB Rubber Ducky is a famous attack tool that looks like a USB flash drive but acts like a keyboard when plugged into any unlocked device. The Ducky Script language used to control it is simple and powerful, and it works with Arduino and can run on boards like the ultra-cheap Digispark board.

Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.

For Snapchat users wondering if that selfie is ready to send to their crush, independent Lens Studio creator Andrew Mendez created a handy tool called the Smile Rater.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

For many, the stock version of Android is often considered the epitome of what the operating system should look and feel like by default. It's clean and clear of unwanted extra apps that come pre-installed with the system, provides a fluid and fast user experience, and runs on just about any device that has an unlocked bootloader to install a custom ROM with the stock version ready to go.

Hacker's are always looking for new ways to exploit systems and exfiltrate passwords, even in hashed form. Sophisticated brute-force attacks powered by high-end GPUs can perform millions of password attempts per second. But Ubuntu and Debian users aren't completely helpless. There are ways to harden the hashed password to better defend against Hashcat attacks.

Slack recently released a dark mode for its Android and iOS apps, and for the most part, it works great. Super dark gray backgrounds and light gray fonts, which is much easier on the eyes than blinding white backgrounds and black text. But there's one thing that is not affected by the new night mode setting — your sidebar.

Android's settings menu is actually pretty daunting. There are options for nearly everything, so in the sea of various menus and submenus, it's easy to overlook important privacy and security settings. On Google's Pixel phones in particular, there are 20 such settings that you should double check.

The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python tool for brute-forcing websites called Hatch, this process has been simplified to the point that even a beginner can try it.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

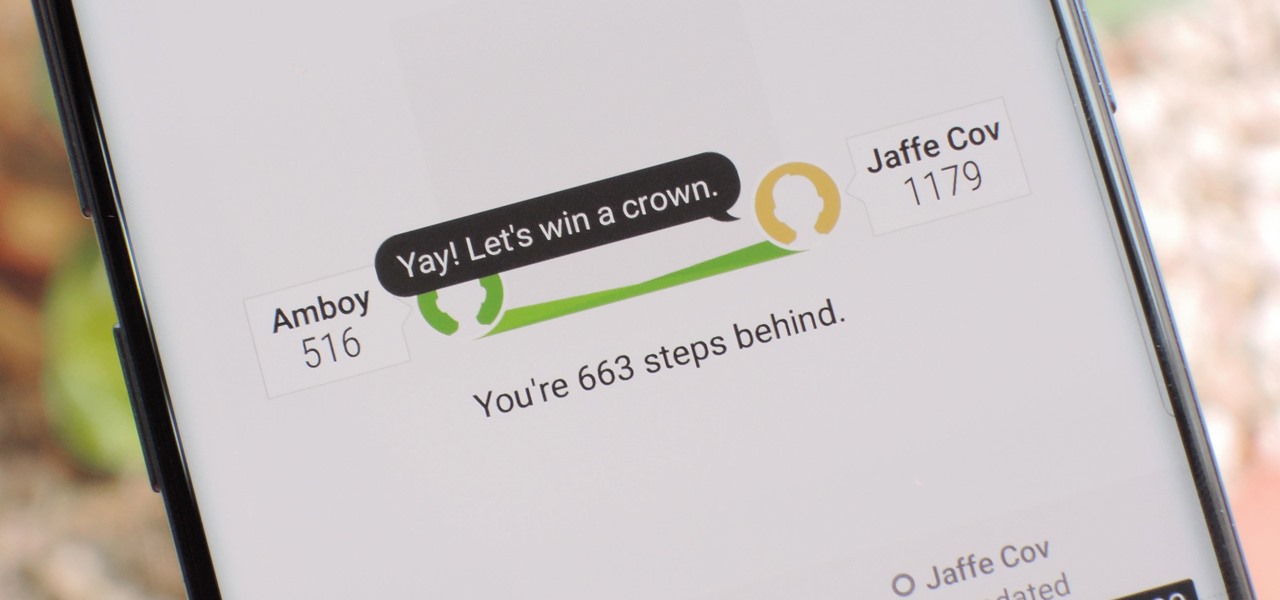
When you're trying to get fit, friendly competition can go a long way towards keeping you motivated. Samsung Health has a great feature for just that, letting you challenge your friends or even complete strangers to bring some excitement to an otherwise routine workout experience.

All of the new iPhones from 2018 were released with dual-SIM support, but none of them were capable of actually using the eSIM in iOS 12, only the physical nano-SIM. But on iOS 12.1 and later, you can finally take advantage of eSIM so you can have, say, a business and personal plan on your iPhone XS, XS Max, or XR at the same time.

With the same starting price as its predecessor and a nice list of improvements, the OnePlus 6T is a great buy for a number of reasons. But for many Android users, the main selling point for the latest OnePlus flagship is how easy it will be to root and mod the device.

With just one line of Ruby code embedded into a fake PDF, a hacker can remotely control any Mac computer from anywhere in the world. Creating the command is the easy part, but getting the target to open the code is where a hacker will need to get creative.

If you want to use your iPhone with another carrier, all you have to do is contact the original carrier to request an unlock, which is usually granted in a few days. Unfortunately, you need to meet specific criteria to officially carrier-unlock your iPhone, like paying off the device in full and completing any contracts. But that doesn't mean there isn't a workaround you can use beforehand.

There's a lot more to your iPhone's dialer screen than just entering phone numbers and hitting the green call button. It's not very obvious, but there are secret codes that you can enter on the dialer to find out information about your device, help troubleshoot issues, and mask outgoing calls, to name just a few things.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

Kali Linux is established as the go-to operating system for penetration testing, but in its default configuration, it's less than ideal for regular desktop use. While in many scenarios, a live boot or virtual environment can resolve these issues, in some situations, a full installation is better. A few simple changes can be made to a Kali Linux desktop to make it safer to use in this environment.

The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already built into macOS.

In the arms race between ARKit and ARCore, Google scored a big win with the announcement of its Cloud Anchors shared AR experiences platform at Google I/O on Tuesday.

French automaker Renault is tapping into the promotional machine for Solo: A Star Wars Movie by deploying an AR experience through Shazam that's triggered via synergistic advertising.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.

After a hacker has configured Metasploit on a remote private server, created a resource script for automation, and created a simple payload, he or she can begin the process of remotely controlling someone's Windows 10 computer with just a few moments of physical access — even if the computer is off.

At Apple's education event in Chicago on Tuesday, augmented reality stood at the head of the class among the tech giant's new offerings for the classroom.

As with most social media platforms, Instagram can be a double-edged sword. On one hand, it's a great way to share and express yourself — but on the other, it can be just as effective at compromising your privacy. Thankfully, there are a few things you can do to protect yourself.

The Consumer Electronics Show (CES) is the first big tech event of 2018. This year, if the early news is any indication, augmented reality could be the big star of the show.

Millions of travelers pass through airports each day without understanding how powerful and insecure a boarding pass can be. Anyone can scan the boarding pass barcode with a mobile app, allowing access to frequent-flyer accounts and even a passenger's temporary airline account. In this guide, we will explore how hackers scan and decode the information contained in a boarding pass barcode and why.

If CES 2018 is the starting gate for this year's race to release smartglasses, then Vuzix is already racing down the augmented reality track with its Blade smartglasses.

Thanks to Metaverse, it has never been this easy to create your own AR game.

Wise Snacks wants baseball fans to reach for potato chips instead of peanuts and Cracker Jacks, and it's calling augmented reality out of the bullpen to close the deal.

China's Baidu, the Chinese equivalent of Google, live streamed a video yesterday of CEO Robin Li riding a self-drive vehicle along the streets and highways of Beijing.

Google quickly learned over five years ago electric vehicles (EVs) were the powertrain of choice for its then fledging driverless car program and the industry has since followed its lead.