A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.

Attention all Redditors: Between June 14 and June 18, Reddit experienced a data breach. The popular website claims it discovered the breach on June 19 and has since made the necessary moves to contain and eliminate the threat. Unfortunately, there isn't much they can do about the data was that accessed and stolen — your user data.

Samsung has legions of loyal fans, and for good reason — their Galaxy S lineup ticks so many boxes that it would be a downgrade to switch to any other phone. Though if you're still rocking an older model like the Galaxy S7 Edge, the all-new Galaxy S9 can tick all the same boxes plus a few more. But is it worth the money to upgrade at this point? That's actually a tougher call than you might think.

If you have an iPhone, you probably know that iOS 11 hasn't been the smoothest iOS version released, to put it lightly. We've seen bug after bug cripple the software's usability, many times within the Messages app. Now, yet another glitch has emerged to drive us crazy, one where just a simple Indian character can crash Messages as well as other third-party apps.

Millions of travelers pass through airports each day without understanding how powerful and insecure a boarding pass can be. Anyone can scan the boarding pass barcode with a mobile app, allowing access to frequent-flyer accounts and even a passenger's temporary airline account. In this guide, we will explore how hackers scan and decode the information contained in a boarding pass barcode and why.
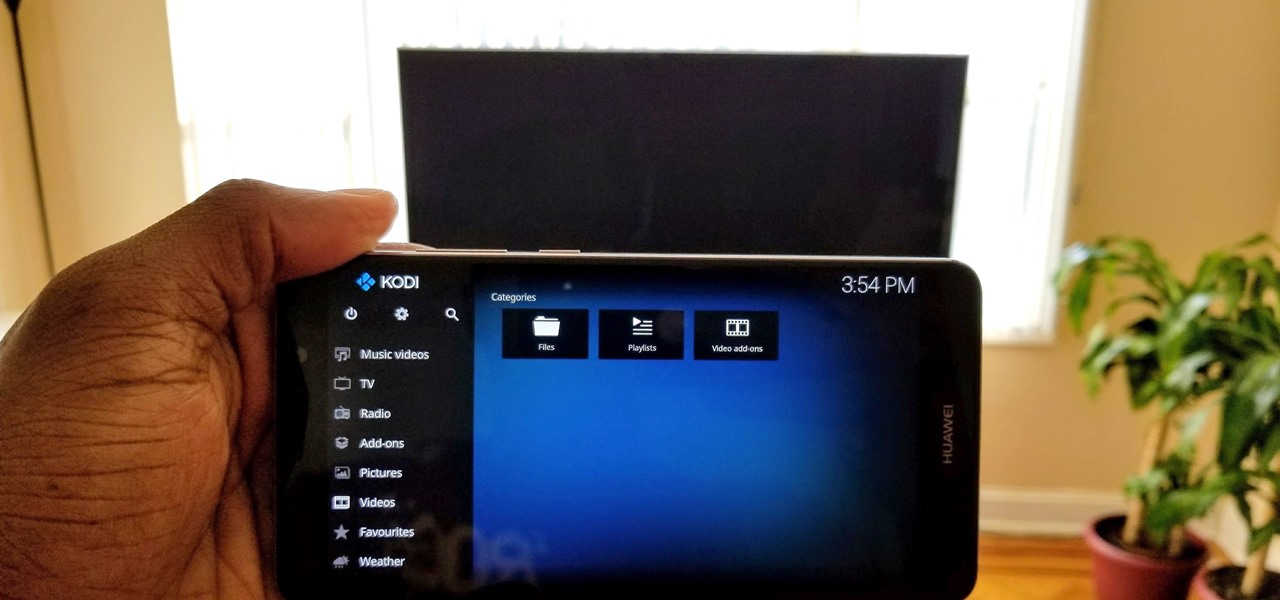
Over the years, Kodi (formerly XBMC) has become one of the most popular media players. It provides all the essential functionality needed for any home theater setup while remaining open source and free. However, Kodi is not limited to just your living room. With the Kodi app for iOS or Android, you get a streaming media player that can act as a video player, music player, picture gallery, and so much more.

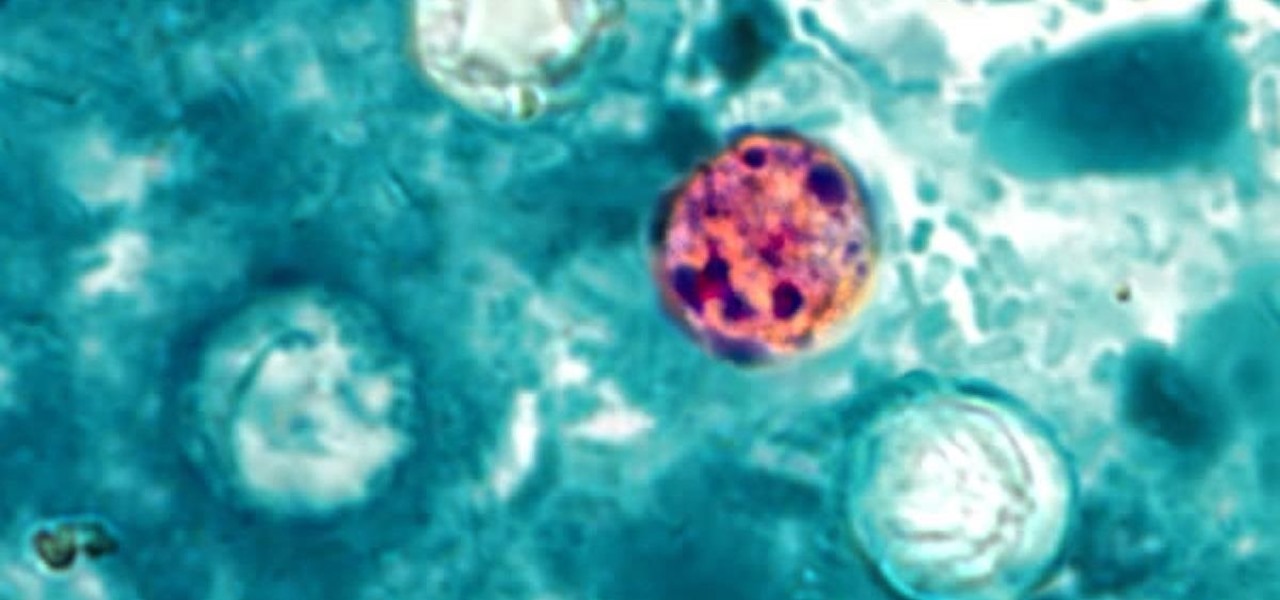
The intestinal parasite Cyclospora cayetanensis has a dramatically increased infection rate this summer, and the source is still unknown, the CDC advised today. 2017 is a good year for Cyclospora looking for homes to start their families and a bad year for those of us who don't like food-stealing tenants living in our bodies.

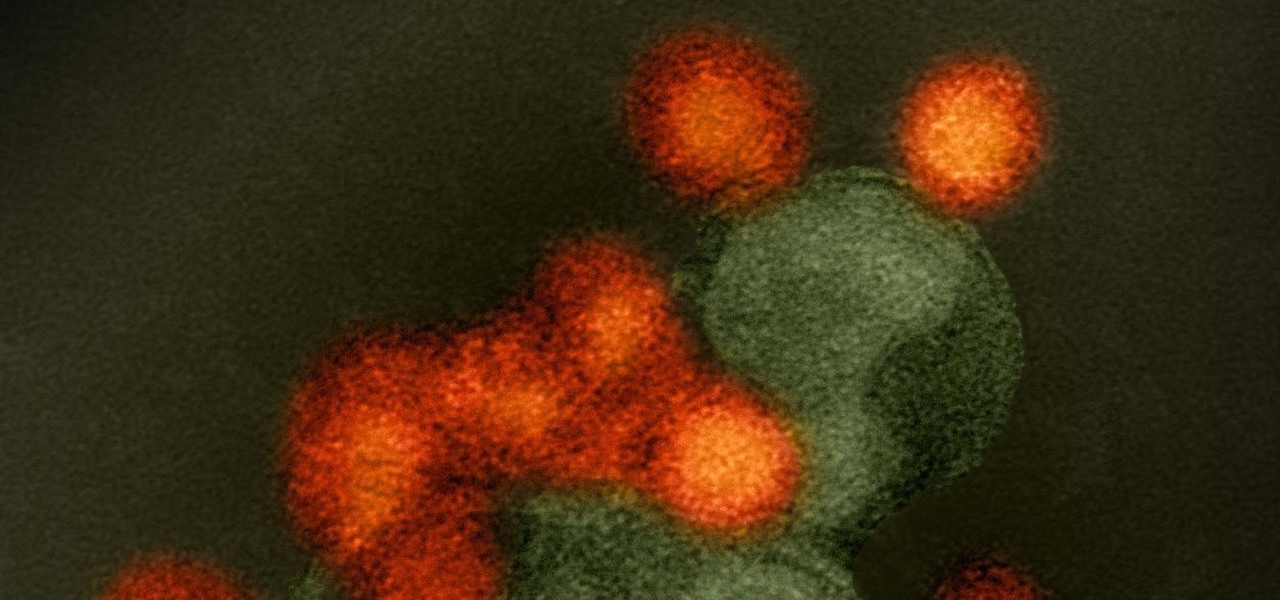
Results of an early-stage clinical trial of an HIV vaccine could mean a hoped-for breakthrough in the battle against AIDS.

We might think of Zika as a mosquito-borne virus that effects developing fetuses, but, it also can be passed through sex by either a man or a woman, just like herpes and other STD viruses. New research has shown that vaginal bacteria can inhibit sexually transmitted Zika virus and Herpes Simplex Virus-2 in women.

After watching Samsung's exploding phone fiasco this past year, I took comfort knowing that the likelihood my iPhone would suddenly combust was slim. However, after hearing about a recent incident in Wisconsin, iPhone owners may have reason to worry.

Cytochrome P450 (P450s) are proteins found in nearly all living organisms, which play roles that range from producing essential compounds and hormones to metabolizing drugs and toxins. We use some of the compounds synthesized by P450 in plants as medical treatments, but the slow growth and limited supply of these plants have put the drugs' availability in jeopardy and jacked up prices.

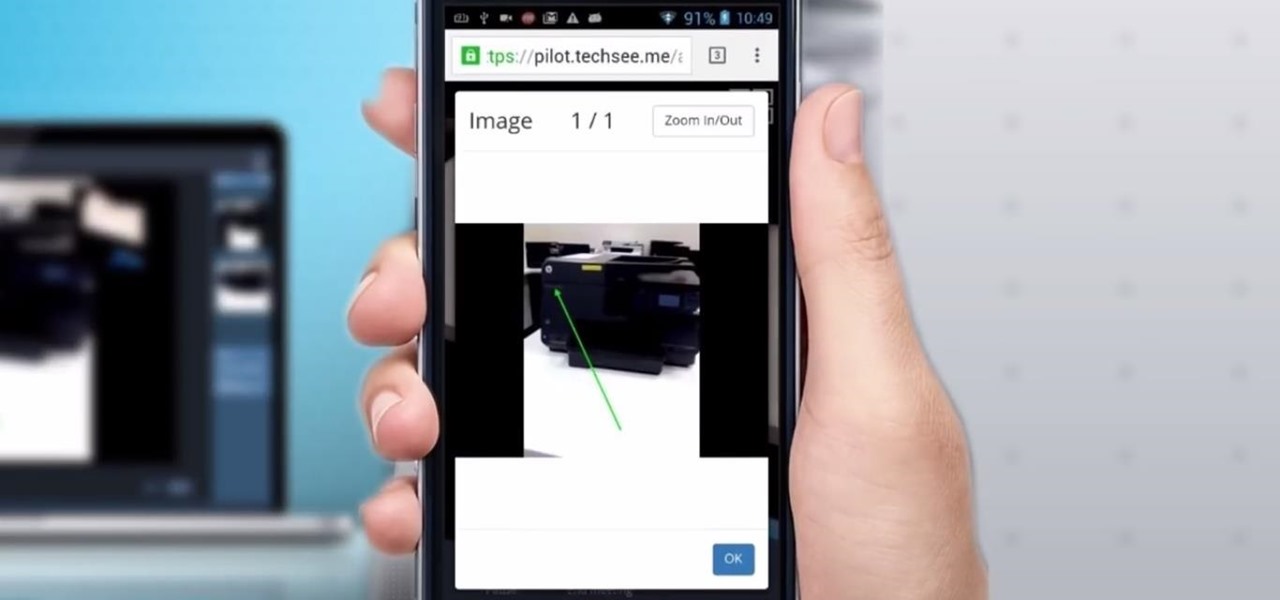
Four augmented reality companies made deals this week to grow their businesses. Two companies, TechSee and Car360, completed funding rounds, while DAQRI signed with a production partner and Decalomania landed a prime spot with a top retailer.

Waymo claims in court documents filed yesterday in its lawsuit against Uber that ex-Uber CEO Travis Kalanick knew that former Google engineer Anthony Levandowski was in the possession of stolen documents while employed at the troubled ride-sharing firm.

To celebrate its tenth anniversary, PornHub has just exposed all of our porn habits. All. Of. Them. Before you panic, no individual information has been released. Instead, PornHub has exposed the adult video trends and preferences of a variety of demographics.

Dirty, malformed, and outright mischievous text strings have long been the enemy of interactive website developers. Strings contain any combination of letters, numbers, spaces, and punctuation, and are entered into text boxes on websites by users. These strings in particular can do everything from highlighting XSS vulnerabilities to soliciting 404 error pages.

Most people know atopic dermatitis by its common name, eczema—that dry, flaky skin that itches incessantly. Along with the scratching comes frequent skin infections, often with Staphylococcus aureus.

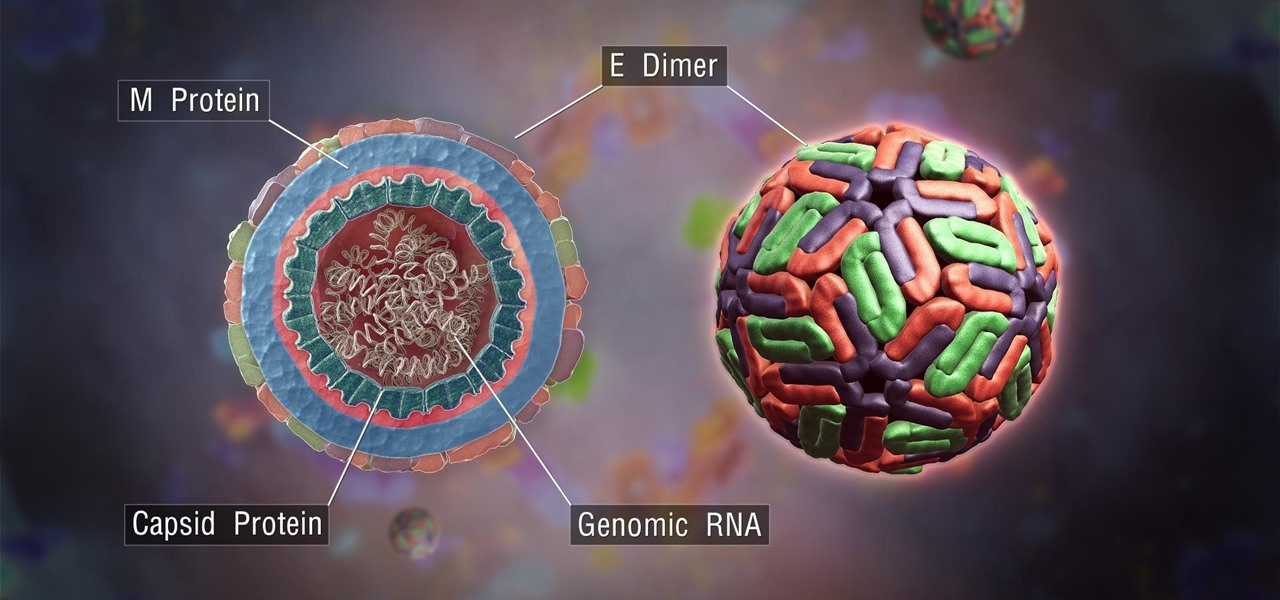
The mention of Zika can strike fear in the hearts of pregnant women. With infections increasing around the world, including in the US, researchers are fighting the clock to figure out how the virus can have such horrific effects in some people.

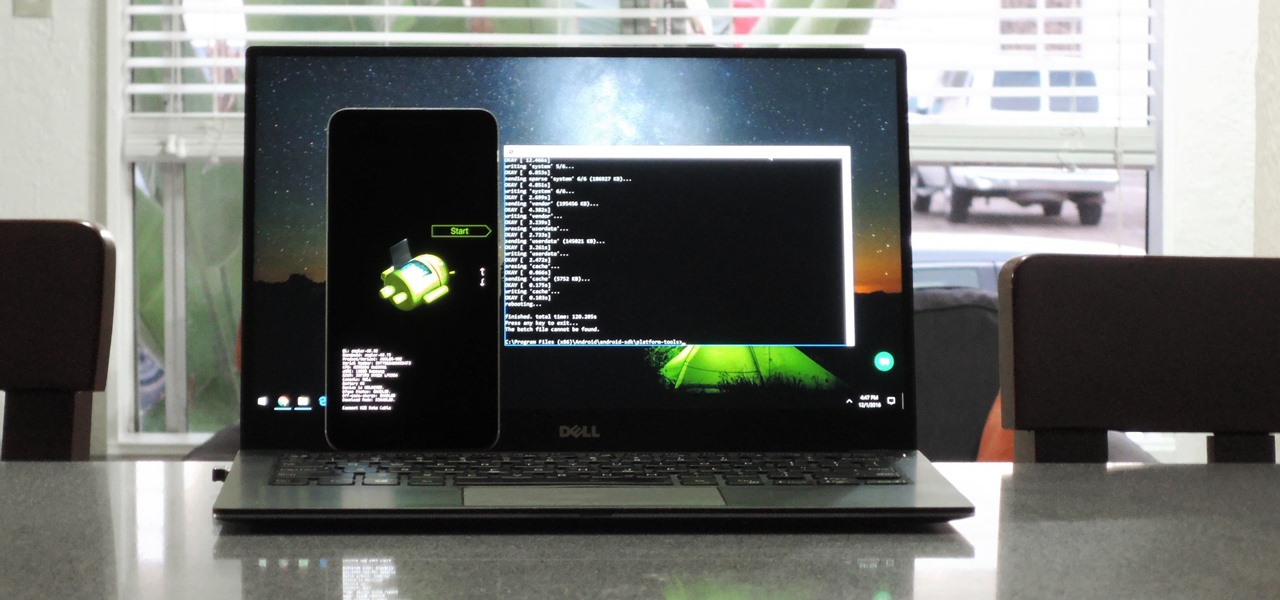
If your phone has an unlocked bootloader, you can use Fastboot commands to flash factory images. That may sound like a bunch of technical jargon, but when it comes down to it, this is the best method for updating a rooted device, fixing a bricked phone, reverting to stock, or even getting new Android updates before everyone else.

You're all kale-d out, you've had it up to here with golden milk, and you're on the prowl for the next superfood. Well, get ready for some unicellular goodness: the next superfood is an algae named Spirulina, also known as Blue Majik. (Kudos to the marketing exec that came up with that, am I right?)

A human rights activist from the United Arab Emirates recently stumbled upon three gaping security loopholes in iOS that work by enticing you to tap a link sent to your iPhone. Ahmed Mansoor received a text message from an unknown number roughly two weeks ago, but instead of following the link it included, he sent the message over to a security researcher at Citizen Lab.

Scrambled, sunny side up, hard-boiled, soft-boiled, over easy, and poached: there are only so many ways to cook an egg before you get bored and look for inspiration somewhere else.

Although there has been much speculation about how much damage could be done if hackers were to take control of a country's SCADA systems, there have been few examples - until a few months ago, with the power outage in Ukraine caused by hackers.

What's up guys? Welcome to a sort of general walkthrough on how one might approach a reversing and analysis on a crypted malware. This is by no means a universal technique so don't assume that this will occur in every scenario, it's more of a demonstration than anything really.

Hi guys, this is going to be kinda like a follow up to my previous post on hacking facebook with the remote keylogger. If you haven't seen that post I suggest you do. So like you can click here. Anyway let's move on.

In part one of this tutorial we found out that your English teacher is a paedophile, by using a Man in the Middle attack to intercept his internet traffic.

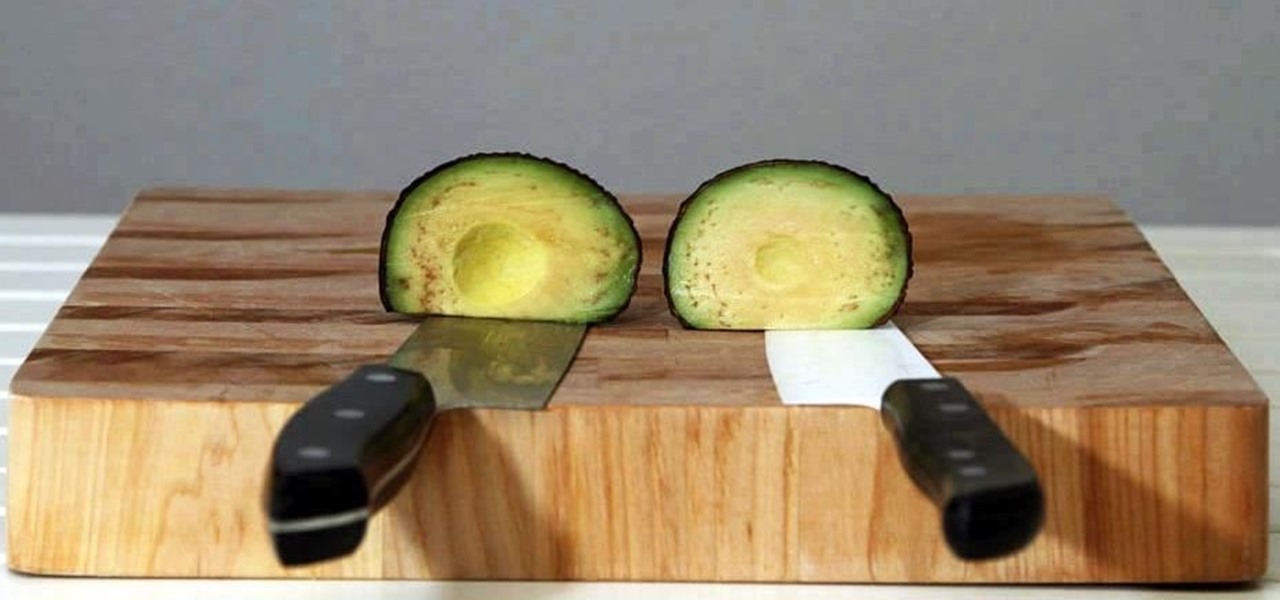
Keeping apples or avocados from browning after being cut is impossible; within minutes of being exposed to air, these fruits (yes, avocado is a fruit) begin to brown. No matter what you try—adding lemon juice, keeping the pits in place, immediately sealing the produce in an airtight bag—brown discoloration always occurs. However, air is not the only reason that foods like apples, avocados, and lettuce brown: it's also due to the knife you're using.

I love eating fish at restaurants—the flesh is flaky and tender; the scent, fresh and sweet. Cooking fish at home is a completely different story, though. Even when I do cook successful fish dishes, it often leaves this (for lack of a better description) fishy smell that permeates everything it touches. Monday's salmon becomes Wednesday's odor. It's enough to deter me from cooking fish, period.

Editor's Note: The research described in the article below has been criticized and any conclusions based off this research should be examined with a skeptical eye. The article has been edited to reflect these issues.

Black lights come in all shapes and sizes, and they're useful in a variety of ways. They can help you spot fake currency, urine stains, interesting rocks, and deadly scorpions, and they can even help you view cool fluorescent artwork.

Convenience in the kitchen can be a very, very good thing. As fun as it can be to spend hours toiling over Julia Child's boeuf bourguignon, there's a reason that we have canned soup, microwave dinners, bouillon cubes, and, of course, boxed mixes.

If you've switched ROMs before or flashed quick mods on your Android device, you've probably used TWRP or another custom recovery to install them. But another great purpose for flashing through a recovery is to install your own custom .zip file filled with everything a fresh ROM needs—namely, all your apps.

Taking care of your car requires effort, whether you take it to the pros for washes, waxes, and detailing, or you spend time to make it shine yourself—and it often seems that, right after your car is sparkling again, rain or midnight moisture appears to cover its surface in water spots. With a small tweak to your typical car care routine, you may be able to keep your car's surface and windows shining longer and better: you just need to add a little hair conditioning liquid.

Just recently, I was experimenting with a dual-boot Windows setup, and somehow managed to wipe my primary Windows installation in the process. "Why," I asked myself, "Why didn't I make a backup before I started this?" Still to this day, I'm going through the painstaking process of installing and configuring all of my favorite programs, and I may not ever get things back exactly the way they were.
Hello, Hackers/Viewers! My name is nullf0x, and I have 4 years of experience as a hacker. You might see everyday that one of your friends or acquaintances get a new virus in their computer. You might think, How cool would it be if I made a virus? or How cool would I be if i could remove viruses from others computers for money or free?

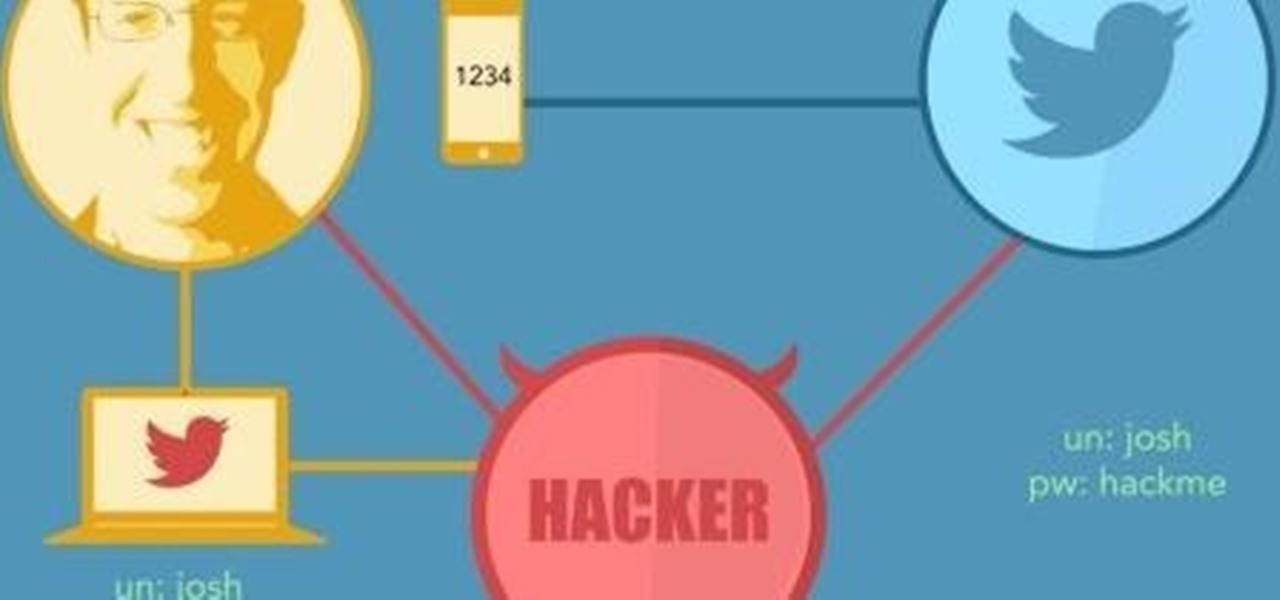
Welcome back, my tenderfoot hackers! Hacker newbies have an inordinate fixation on password cracking. They believe that cracking the password is the only way to gain access to the target account and its privileges. If what we really want is access to a system or other resources, sometimes we can get it without a password. Good examples of this are replay attacks and MitM attacks. Neither requires us to have passwords to have access to the user's resources.

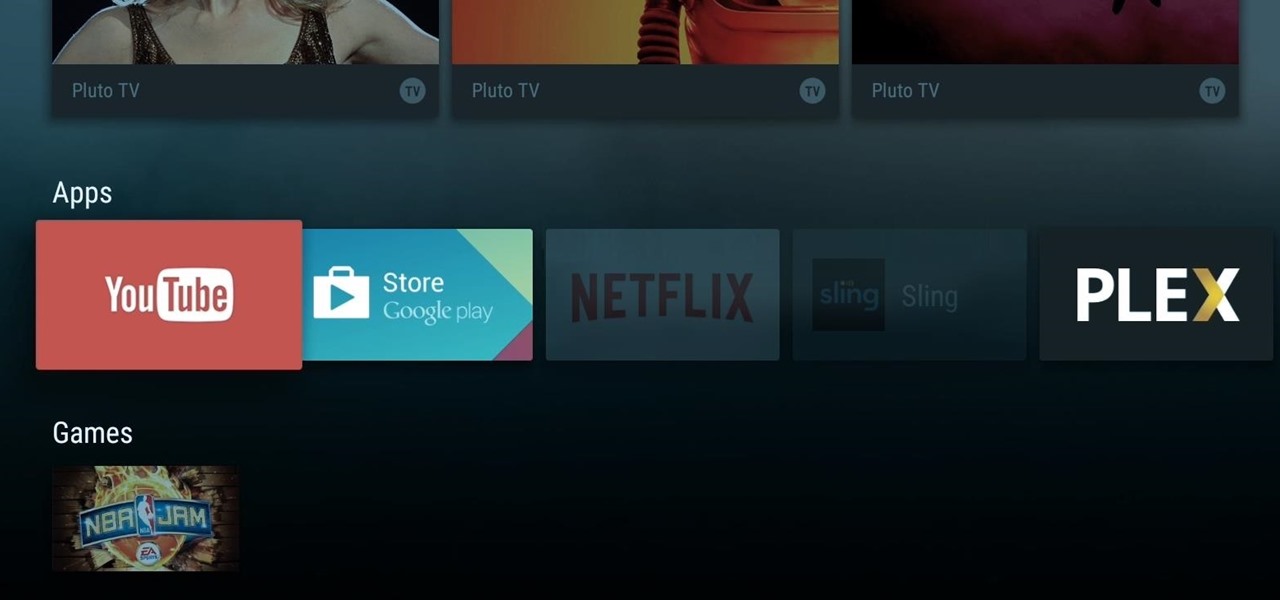
When Google announced its new Android TV platform, one of the features they advertised was a home screen that automatically reorganized your apps based on how frequently you used them. Unfortunately, this feature either didn't make the cut, or is still under development, since the home screen on the Nexus Player always remains static.

It's a shame that one of the world's tastiest foods can be such a pain to prep. Most cooks are familiar with this conundrum: chopping or crushing garlic releases a pungent liquid that causes bits of garlic to stick your knife and hands, creating a messy affair. So what is going on here? The common assumption is that the garlic is releasing some kind of oil, but the truth is that this liquid rinses away easily in water. Yet one of the basic precepts of chemistry is that oil and water don't mix.

Whiteblock : A Whitestar skyblock survival map Video: .

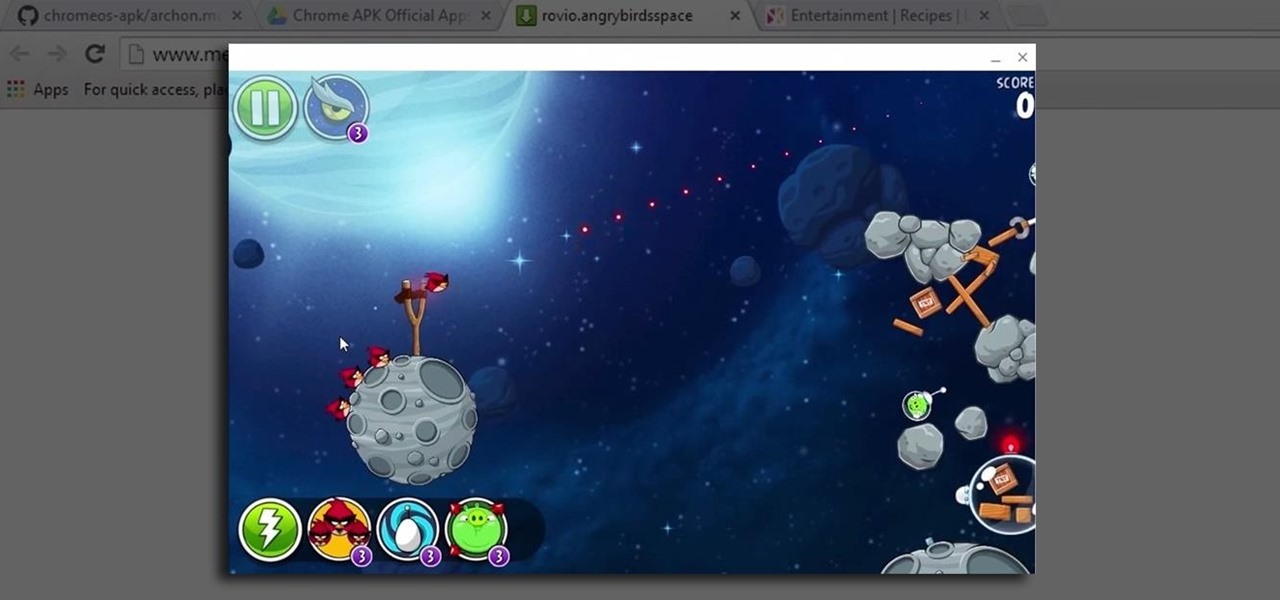
When Google announced that it would begin supporting Android apps on its own Chrome OS, it was great news for all the folks with Chromebooks. But, as that operating system only makes up about 0.2% of the PC and laptop market share, most of us were out of luck.

Naps provide some serious mental and physical benefits, but not if they last too long or occur too late in the day. Ideally, you want to awake from a nap feeling alert and refreshed enough to attack the rest of your tasks with renewed zeal, but not energized to the point where you can't get to sleep at night. Alas, most of us don't know these tricks and end up messing with our sleep cycle (guilty).