A few months ago, LlabTooFeR leaked a full system dump from Google's then-unreleased Pixel and Pixel XL smartphones. That may not seem like a big deal at first glance, but the system dump contained all of the preinstalled apps and services from Google's new flagships—including the much-anticipated Google Assistant.

Out of all of the "odd couple" food pairings you could imagine, this has got to be one of the outright weirdest.

If you just can't wait to see the Pixel and Pixel XL, the new Google-branded smartphones expected to be announced tomorrow, you're in luck. After weeks of rumors and blurry images, a smartphone sales company called Carphone Warehouse just accidentally dropped the entire ball. The UK business accidentally set the product pages for the Pixel and Pixel XL live a couple days early, and for just long enough for them to be archived before they were taken down.

Whenever I went to the grocery store on a mission for blueberries, I'd inevitably find myself staring at these weird little tomato-looking berries... and wondering what the hell they really were. Tomatoes? Berries? A weird science experiment? Then, I'd set a pint of blueberries in my cart and carry on, forgetting about them for the time being.

The sprouts, they're alive! Alive, I tell you—aaaaaaliiiiiive! (Cue dramatic music.) It's true: sprouts are a living food, and they're packed with more nutritional benefits than some raw vegetables. It's easy and fun to grow your own sprouts from seeds, legumes, and grains. Plus, watching them grow is incredibly satisfying—you're bringing new life into the world (and onto your plate)!
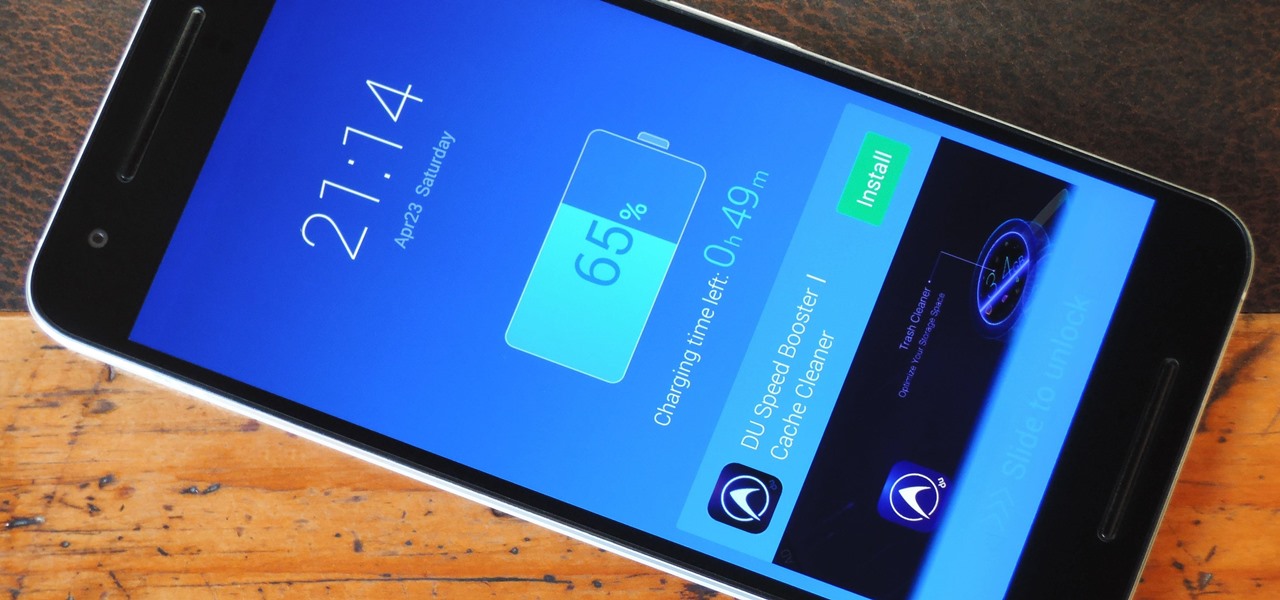
There was a somewhat recent outbreak of malware on Android, and it came from an unlikely source—the Google Play Store. Several established apps have received updates a few months ago that contained an unwanted add-on called either DU Quick Charge, DU Battery Boost, DU Boost Charge, DU Speed Charge, DU Speed Booster, or another name starting with DU.

Onion scrubs, salt and olive oil blends, a baking soda slurry... despite the many methods already out there to clean your (old or brand-new) cast iron cookware, there's one you may not have considered: using a potato.

This week has been quite a successful one for Google, thanks to non-stop news coverage of their developer-focused I/O conference.

With the FBI getting access to iPhones, and apps like Waze being used to track people's locations, you've got to wonder just how safe and secure your smartphone is... or isn't. When you consider everything you do on your phone, from taking and sharing pictures to mobile banking, keeping your information safe is a crucial step that may seem out of your hands.

As most of you know, I am a strong advocate for using Linux for hacking. In fact, I would go so far as to say that you cannot be a hacker without knowing Linux well. I laid out various reasons for this in my "Why Every Hacker Should Know & Use Linux" article, and I even have a lengthy, continuing series on Linux Basics to help those new to Linux master it.
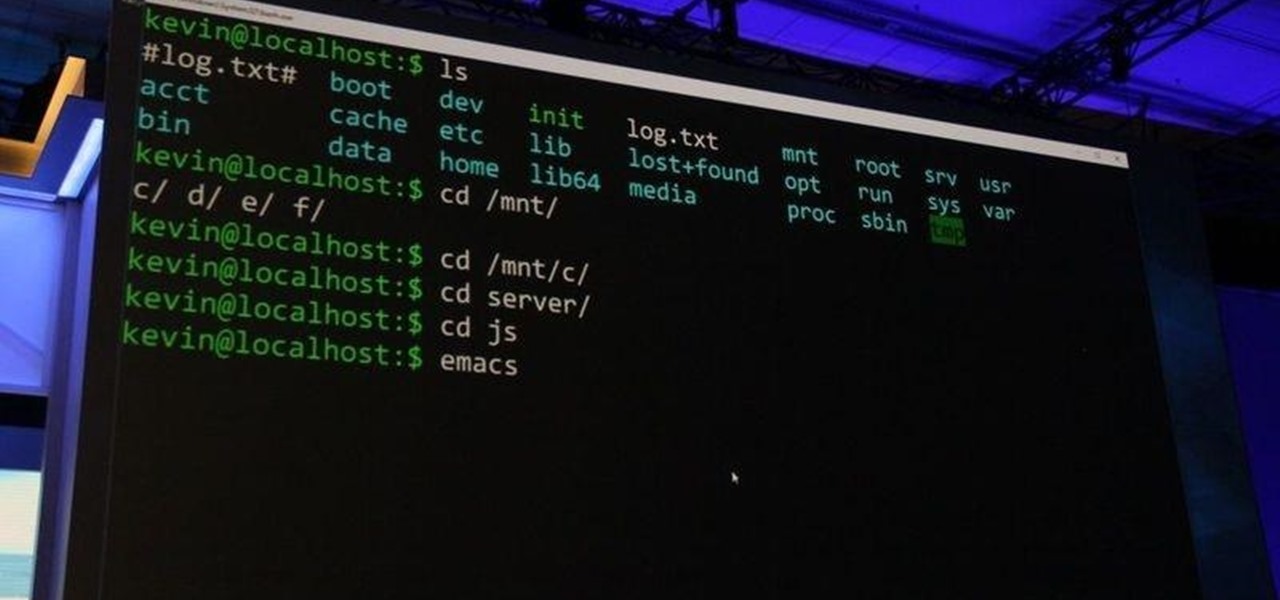
Hello guys I am ROMEO 64 (sounds weird I guess but who cares. :D).. Alright....Ever wondered what happens when you login to your Facebook account?

While there are tools online that let you turn photos into interesting emoji art, and mobile apps that let you create emoji mosaics, none do it better than an iPhone app by second verse, which makes it a super easy, highly customizable process.

The Null Byte community is all about learning white hat hacking skills. In part, this is because I believe that hacking skills will become the most valuable and important skill set of the 21st century.

Very often we have processes in Linux that we want to always run in the background at startup. These would be processes that we need to start at bootup and always be available to us.
Fugu - a simple virus in bash. I once told a friend of mine I'd written a virus in bash and he scoffed - "You can't write a virus in bash!" - he sniggered, like an ignorant idiot.

I've been doing tutorials on Rasberry Pi and I would like to thank everyone that have both read the tutorials and gave me feedback on how well I'm doing. But now I've decided to take a small break and start a mini series that I'm hoping to be at least five tutorials. This doesn't mean I'm gonna stop posting Raspberry Pi tutorials, but since I'm learning so much at the same time I've decided to share some of that knowledge. Hence this tutorial. Please sit back, relax and read on.

If you consider yourself a regular coffee, tea, or hot chocolate drinker, you probably have a kitchen cabinet full of stained mugs that refuse to scrub clean. Thankfully, there is a better solution that doesn't involve continuing to fight those stains with a sponge, bleach, and elbow grease. The answer to your coffee or tea stain problems is Cafiza: an awesome espresso machine cleaning product that is popular amongst professional baristas... but also doubles as an extremely effective ceramic ...

I'll be the first to admit that I have a problem: I'm utterly addicted to tea.

Welcome back, my aspiring hackers! In this series, we continue to examine digital forensics, both to develop your skills as a forensic investigator and to avoid the pitfalls of being tracked by a forensic investigator.

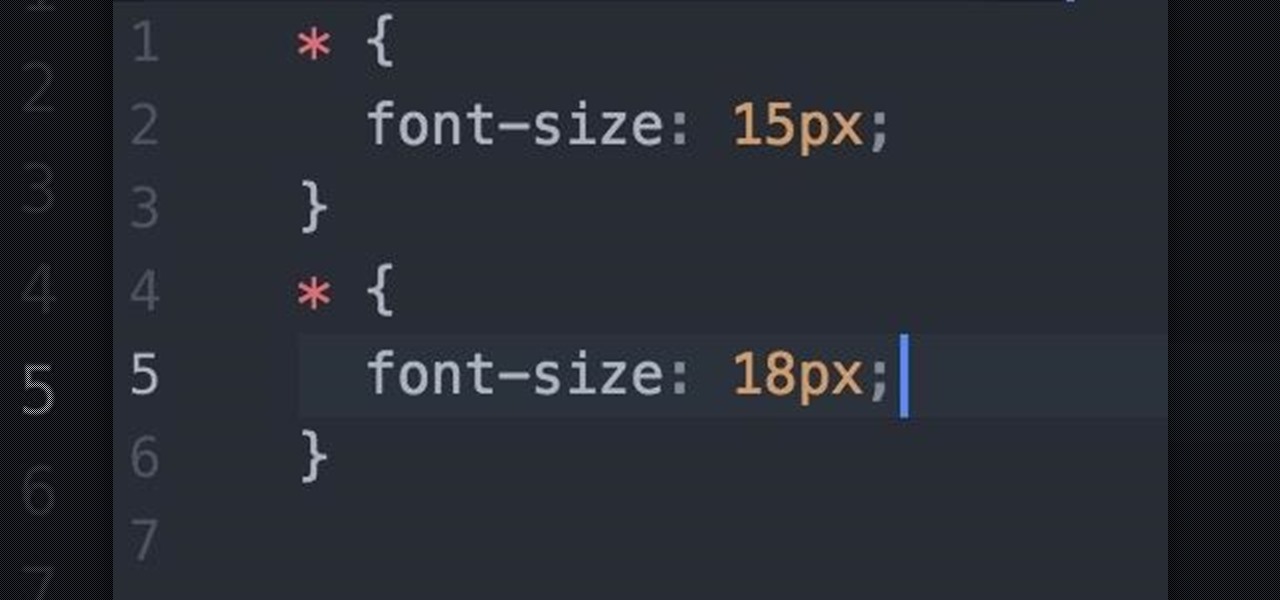
Welcome fellow Null-Byters! I would suggest you watch reading my last tutorial before we begin. In our last adventure, we began making a simple, ugly website. If we want it to make it look good, we should add some styling. But first, we need to understand the basics.

What's up guys! It's time to discuss strings in more detail. Review

The Nexus 5X and Nexus 6P have identical camera hardware—in fact, both use one of the highest-end camera sensors ever put into a smartphone. The only real difference between the cameras on Google's latest flagship devices is that the 6P natively supports electronic image stabilization (EIS) whereas the 5X does not.

I loved the original Star Wars trilogy when I was a kid, but loathe all of the current DVD, Blu-ray, and streaming versions available today. Ever since 1997, every version of A New Hope, The Empire Strikes Back, and Return of the Jedi has had horrendous CGI effects added in that George Lucas deemed necessary to bring his "ideal" version to life.

Winter and the winter holidays in general are a time of joy, laughter, and love… but not for everyone. For some, the stress of preparing for parties, hosting family, traveling long distances in bad weather, and just keeping up with your daily routine can start to bring you down.

While it took Apple a damn-long time to finally include widgets in iOS, I do admire their implementation. Accessible from within any screen by pulling down the Notification Center (or, more correctly, the "Today" view), the home screen remains clean and minimal, which some of you with Android devices might appreciate—despite any Apple hatred you may have.

Elle, who grew up on the East Coast, would have described the weather as "brisk." I, a Southern California native, called it "deathly cold." As we waited for the water to boil over our campfire, despair began to creep in.

If you're lucky enough to have a dishwasher, you probably use that sucker to clean everything (minus your good cooking knives), and maybe even to cook your food, too. However, dishwashers are not without their faults. Dishes can still come out spotty and even with chunks of food on them, which usually leads to some hand-washing afterward.

When attempting to compromise a target, we want as much control as possible over the victim. Metasploit's meterpreter allows us to have immense control over the victim, the only issue is that sometimes we can't land a meterpreter. We may only be able to land a standard shell, but fear not, there is a way to upgrade our shell into the all powerful meterpreter!

Hello fellows nullbyters, first of i will start saying that im addicted to this community, i feel the challenge growing up so fast, all the newbies, amateurs,advanced and professionals hackers around trying their best to help the community, badly but we got some script-kids too but anyway, today we are going to learn how to install and use clanAV in kali linux.. INTRODUCTION

Greetings all. Before I get into the tutorial, I would like to mention that I am fairly new to Null Byte (been lurking for some time though), and what really appeals to me about this place is its tight, family-like community where everyone is always willing to help each other and the constant search for knowledge that inhabits this subdomain is a driving motivator for me to join in. I'm glad I arrived at the right time. Anyway, wipes tears (not really)...

Alcohol isn't exactly considered a healthy lifestyle choice; more often than not, it's associated with empty calories and bad decisions. But that doesn't mean there aren't a few benefits to drinking in moderation. In fact, gin is a liquor with a wealth of potential benefits to offer. So read on, and discover ten ways in which gin might actually be a good drink for you.

Hello, my web huggers! In today's tutorial we will learn how to use the Google Hacking Database (GHDB) developed by Exploit Database, to find vulnerable web servers and "juicy" information.

Greetings, hackers and friends! I know it has been a while since I posted a tutorial, and hopefully I can make up for that by posting a series.

Step aside, vodka—whiskey will soon be the best-selling hard liquor in the United States. The whiskey renaissance has been largely attributed to the current trend for locally- and artisan-produced goods. Local whiskey distilleries are rapidly increasing in number across the nation while bars in every state are including the old-fashioned cocktail on their menus in an attempt to capitalize on the trend (which we can probably thank Mad Men for).

T-Mobile's credit-checking system was recently hacked, and this one is about as bad as it gets. The names of 15 million customers, their date of birth and social security number, as well as driver's license numbers and additional information was illegally accessed, meaning the potential for identity theft here is huge.

You must have read news about hackers dumping the data online, recent one was Ashely Madison. It's only the big companies' data, which gets noticed once it is out. There are many other small leaks which don't even get a mention. So this article is the first one of my series which will help you to find hacked accounts. Some of you must already know about this, but this post is intended for the new learners. This also serves as an example of my learning how a good service can be used in other w...

It's official: The next version of Android will be code-named "Marshmallow," and we're getting a whole number bump to version 6.0. Lots of exciting new changes are coming to the world's most popular operating system, including a "Now on Tap" feature that will give you relevant information about any screen at the press of a button.

When you go to the grocery store, chances are you're confronted with the usual piles of apples, berries, bananas, and melons. All well and good, right?

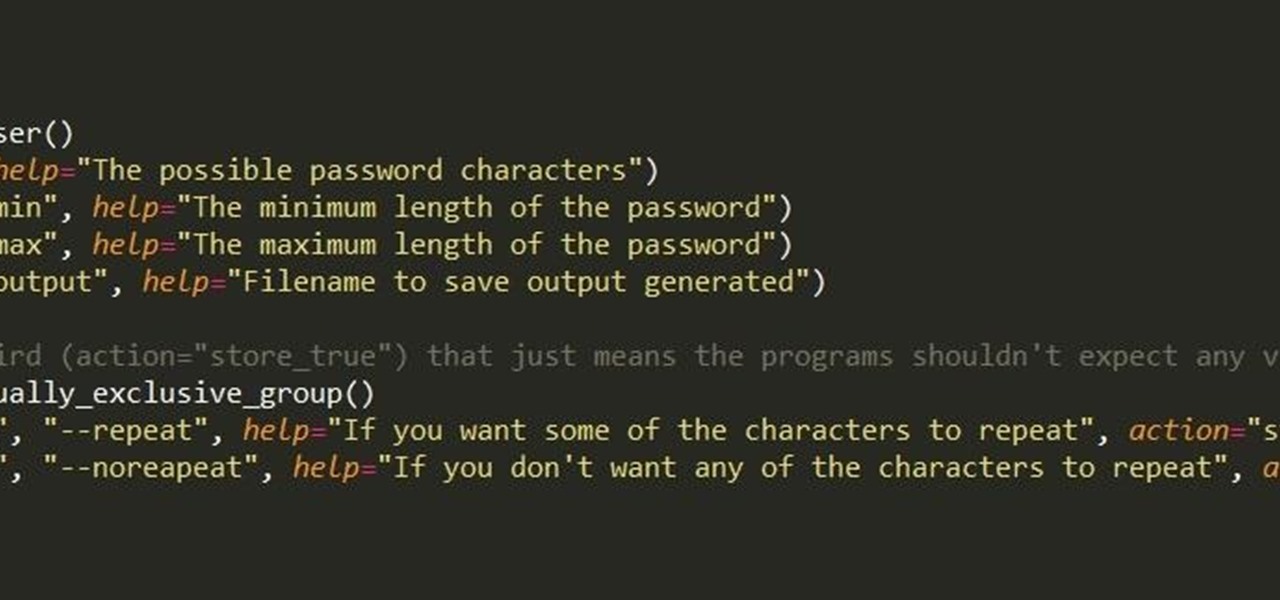
First of all, I hope the title makes sense. :D Well, this is basically creating a program that can help with dictionary attacks. Generate possible passwords. It pretty much lies in you knowing the person you want to hack.

Well, this is my first article so if it sucks tell me...lol!! Story Time