Google's Material Design guidelines have finally brought some consistency to the look and feel of Android apps, bringing most of the user experience on par with what you would see on iOS. However, some developers are still using non-compliant home screen icons, even though Material Design calls for specific padding, size, and layouts.

You may not know what HTTP is exactly, but you definitely know that every single website you visit starts with it. Without the Hypertext Transfer Protocol, there'd be no easy way to view all the text, media, and data that you're able to see online. However, all communication between your browser and a website are unencrypted, which means it can be eavesdropped on.

When it comes to sharing files between a smartphone and a computer, there are several solutions available for a Windows and Android pairing. But for those of us with Apple devices, the selection of apps in this category isn't quite as great. You can use AirDrop to quickly share files, but searching for files is not so easy.
These days, there's almost an expectation that you have to deal with messages as soon as you get them. But that's not always the best way to handle things—sometimes, you're preoccupied with something, and it would be better if you could deal with a new message when you have a chance to give it your full attention.

Cool, refreshing fruit, ice-cold margaritas (or beergaritas), and popsicles... this combination of food and drink just screams summer. Turn up the chill jams on the stereo, fire up the grill, and throw on your shades—you're just one pool away from the best summer party ever.

This tutorial follows the same idea as my original tutorial for windows, but I've redone it to work with Mac OS X. Here's how to get a meterpreter session from your victim opening a malicious word document:

This is my first article on here, it's based off of a project that I'm working on at school which is on three ways to bypass windows user password's. If all goes as planned and you all would like I'll work on part two and part three and post them as soon as I can. I do have to give credit to Puppy Monkey Baby and The Defalt, both of whom are my classmates at college and have helped me with writing this article.

Even if you haven't heard of ube (pronounced "OO-beh"), you've probably seen pictures of desserts made with this brilliant purple yam.

Several years ago, I moved to Brooklyn, New York, just outside a Spanish neighborhood. It was here that I was introduced to chayote. Fast-forward to present day: I live in Los Angeles and buy several chayote squash a week to cook with—yes, I said several. It's so versatile and healthy! For the uninitiated, chayote (chai-YOH-tee) is a light green squash shaped like a pear originating from central Mexico. Although it's considered a fruit, chayote is a member of the Cucurbitaceous (gourd) family...

The headline above may have some spice addicts shaking their heads, but, believe it or not, there are people out there who either don't like or can't handle a ton of spice.

First and foremost, let me once again apologize for that bug, which I failed to notice in time. Alright, alright... Enough sulking, oaktree. Get to it!

Welcome back, my neophyte hackers! In the world of information security, the most common intrusion detection system (IDS) you will ever encounter is Snort. As you probably already know, an IDS works similarly to antivirus (AV) software on your desktop; It attempts to identify malicious software on your network and warns you of its presence.

While attempting to hack a web app, there may come a point where the attacker may have to escape the default directory in order to access unauthorized files. This is known as a directory traversal attack. Much as the name implies, this attack involved traversing the servers directories. But in order to move to an unauthorized directory, we need to know where those directories are. Today we'll be building a tool to brute force these directory locations based on HTTP response codes. Before we g...

When we were kids, Saint Patrick's Day was a green-hued holiday that promised green eggs in the morning and green mashed potatoes in the evening... along with some traditional corned beef and cabbage, of course.

Being able to customize the look and feel of your device is the main reason a lot of folks choose Android over iOS. And perhaps the single biggest way to visually overhaul your phone or tablet's UI is to apply an icon pack, which can liven up your home screen with bright colors or make things look a bit more classy with a sleek, minimalist style, for instance.

In this series you will learn how to use PHP to perform attacks, gather information, and setup backdoors. Along with performing attacks you will learn how to protect yourself from them. In this part you will learn about PHP as well as install Apache and PHP. What you'll need for this series

Here I will show you how to properly dig information on the web that has already been published, you just dont know it.

NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of last year, they've really out done themselves.

What's good, peeps? I've been noticing some rather advanced tutorials slowly emerging here on Null Byte and I know that people want more of them but I've been reluctant to post something of such caliber because I fear that the information will just go over their heads, but hey, as long as it's there, people can always go off to research themselves and eventually understand. So here is my contribution to the gradual and inevitable progression of Null Byte!

A little-known company in India is making waves after announcing that it will sell an Android 5.1 Lollipop smartphone for less than $4 (or, more precisely, 251 rupees). The Freedom 251, from Ringing Bells, sounds almost too good to be true. Is that because it is?

For me, shredded coconut is something that is eaten several times a week in a variety of ways—and that includes in savory dishes. It can be added to just about anything, and this is a good thing if you enjoy having some variety in your diet. Because I get tired of eating the same foods all the time, over the last few weeks I've tried some pretty interesting and simple ways to use coconut flakes in order to keep my finicky palate satisfied.

Welcome back, my hacker novitiates! Often, to hack a website, we need to connect to and exploit a particular object within said website. It might be an admin panel or a subdirectory that is vulnerable to attack. The key, of course, is to find these objects, as they may be hidden.

It has been a while since my last Raspberry Pi tutorial , but now I am back with another tutorial. This one I should note isn't your typical tutorial, but as always lets boot up our Pi and wreck havoc.

Welcome to my very first tutorial ever. Today I will be teaching you how you can use Arachni to scan vulnerabilities of web applications. I welcome all criticism good or bad as a teaching method for myself.

Home cooks are often quite intimidated when trying to reproduce the delicious ethnic dishes they enjoy at various restaurants. Thankfully, there are definite flavor profiles and spice/seasoning/herb combos that are very specific to various regional cuisines and cultures; with a little guidance, you can create dishes that are tasty homages to the cuisines you love to eat. In this two-part article (second part here), I'll cover both categories and sub-categories of some of the most popular ethn...

When it comes to cooking grains, there is an unspoken rule to never stray from the exact measurements. Consulting charts for the proper ratio of liquid to grain is considered the difference between crunchy, undercooked pebbles and a mushy mess... that is, until now.

Welcome to my tutorial where Voidx and I will be expanding on my previous article to provide more clarity into the logic of the code.

I mentioned in 2015 I wanted to start a 'DoXing' series, and since I havent seen this on Null Byte, I am now going to introduce this to the community.

The morning started out like most of them do: I was hungry, and it was time to chow down on some breakfast. However, this particular morning had me craving something besides the usual milk and cereal.

Tahini: it sounds like the name of a high-end fashion designer... or perhaps a variation on a two-piece swimsuit. But this "weird ingredient" is actually a delicious and nutritious paste made from toasted sesame seeds and oil.

This is my first tutorial and it is about accessing deep web for total beginner,sorry in advance if I make any mistake plz forgive me.

Manufacturers like Samsung and LG have added their own implementation of multi-window features to Android for years now, but with the release of version 6.0 Marshmallow, Google has finally gotten around to working the same feature into stock Android.

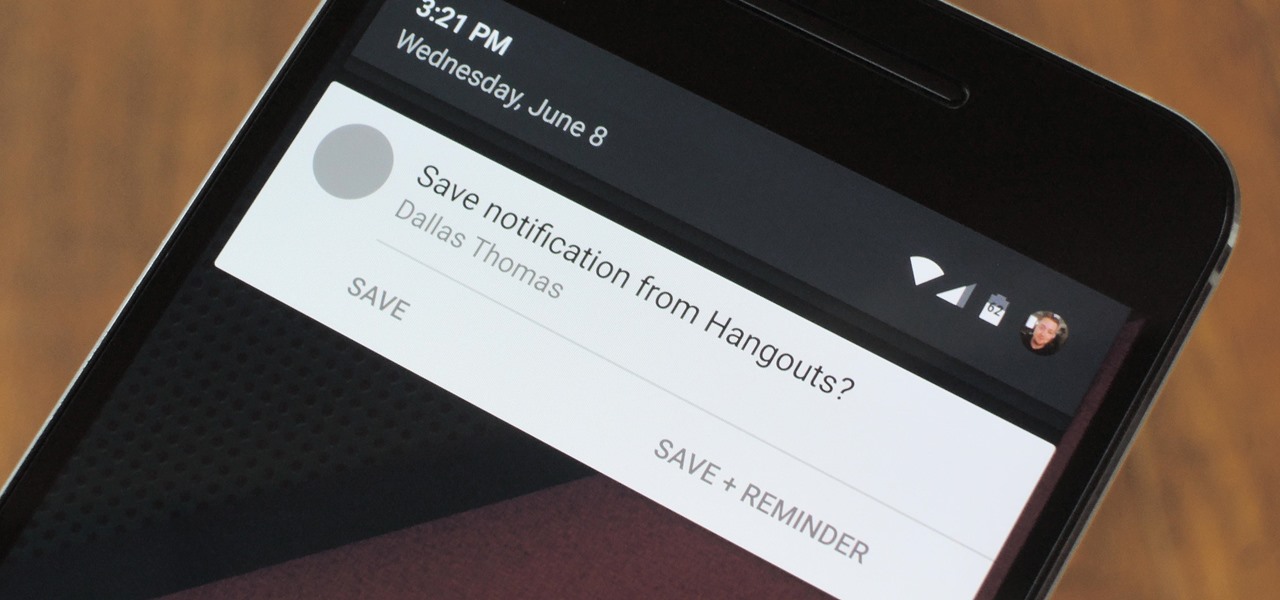
With new messaging services being pushed out constantly, it can be a pain trying to keep track of them all on your Android device. We had previously shown how to stay on top of them all with a unified "inbox" app, but that still requires you to have each individual app installed. While looking for a true one-stop messenger, I came across Disa.

Few things are as frustrating as grabbing food from the fridge just to discover that your leftovers have gone bad. When it comes to cheese, you may have taken every last precaution to keep it as fresh as possible—sealed plastic containers, saran wrap, parchment paper—but to no avail.

Frosting, for many, is the best part of the cake. There's not much to dislike about it, after all—there's a type of frosting for every person. Whipped frostings for those who like it light, dense buttercream for indulgent sugar fans, cream cheese frosting for the tangy crowd... and so on. But I'll bet you've never made or tried frosting made with Jell-O packages before! Infusing your frosting with the sweetness and bright color of Jell-O changes both its taste and appearance, and using Jell-O...

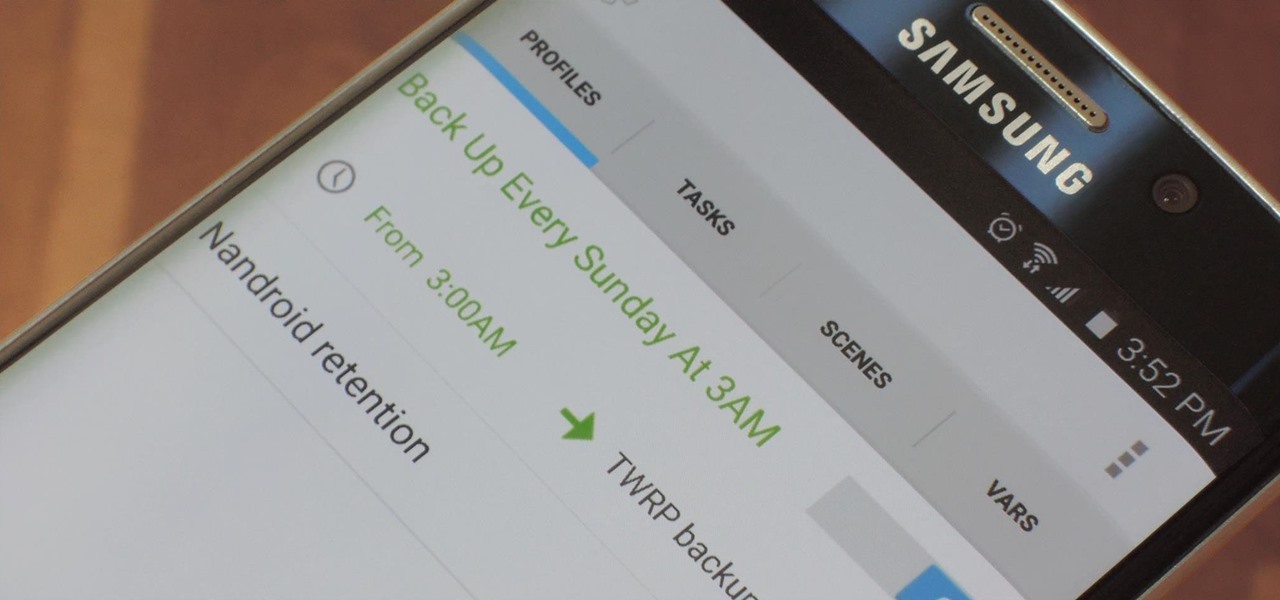
NANDroid backups are one of the best reasons to root your Android device and install a custom recovery. They're essentially a snapshot of your phone's entire operating system and all installed apps, so if you ever screw something up when installing a flashable ZIP or custom ROM, you can restore your NANDroid backup to get everything back to normal.

If there's one thing that gets used far too frequently in the modern kitchen, it's the trash can. Home cooks everywhere waste enormous amounts of food by throwing it away before it's actually ready to be tossed.

Welcome back, curious hackers! In today's tutorial, we will be diving deep into the manipulation of Google Operators, commonly referred to as "Google Dorks" in order to access Surveillance Cameras and other control panels.