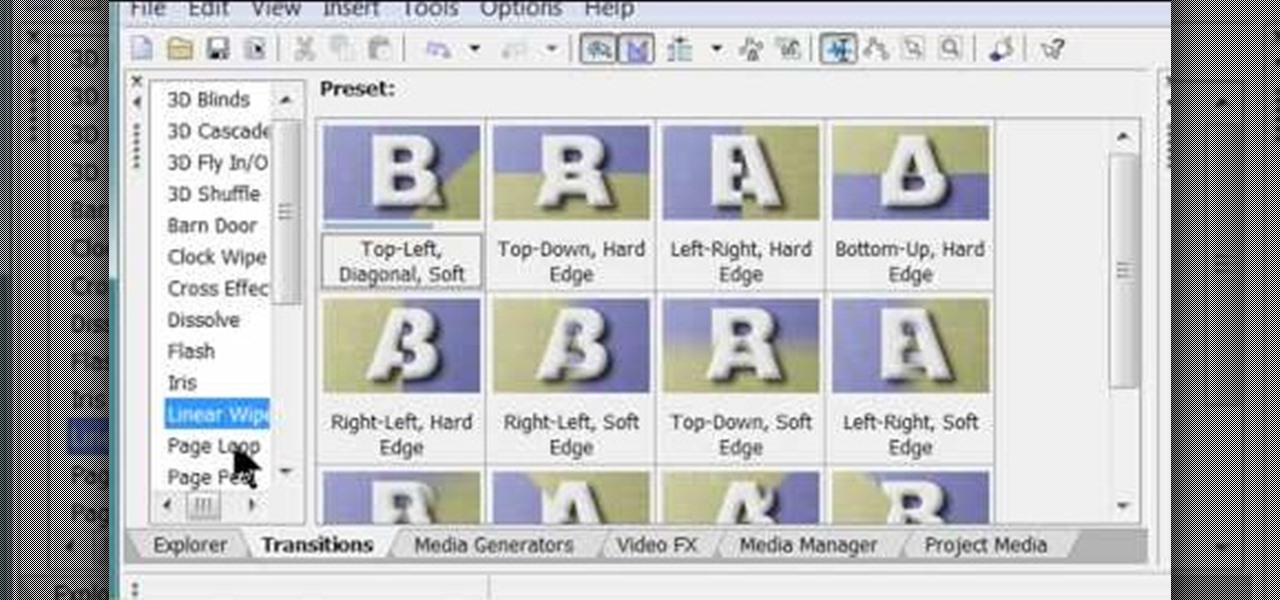
In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.
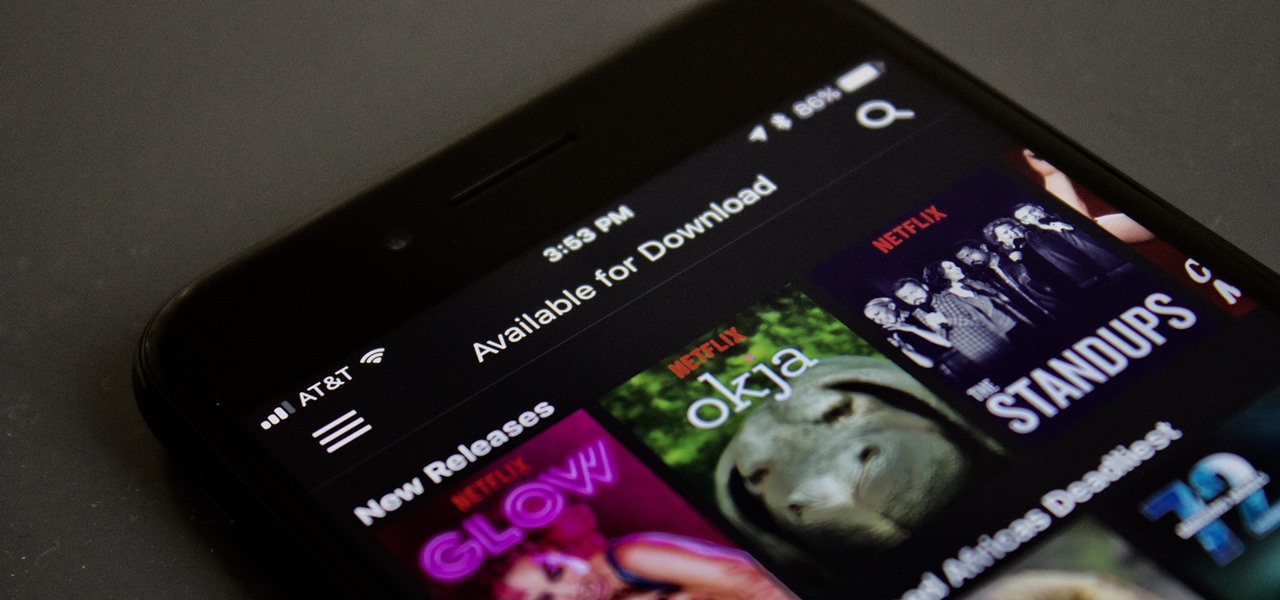
Netflix added the ability to download TV shows and movies on Android and iOS for offline binging back in Nov. 2016, and the process is the same as it is today. So if you anticipate having some downtime to catch up on Narcos or give Bright a try when you'll be away from a secure Wi-Fi connection, download videos onto your phone and save your data for more important things.

The Raspberry Pi loads an operating system from whatever SD card you insert, allowing you to keep different operating systems on separate SD cards depending on which OS you wish to run. A tool called BerryBoot cuts down on the number of SD cards needed by providing the ability to boot multiple operating systems from a single SD card, similar to Boot Camp for Mac computers.

Several recent research studies have pointed to the importance of the microbes that live in our gut to many aspects of our health. A recent finding shows how bacteria that penetrate the mucus lining of the colon could play a significant role in diabetes.
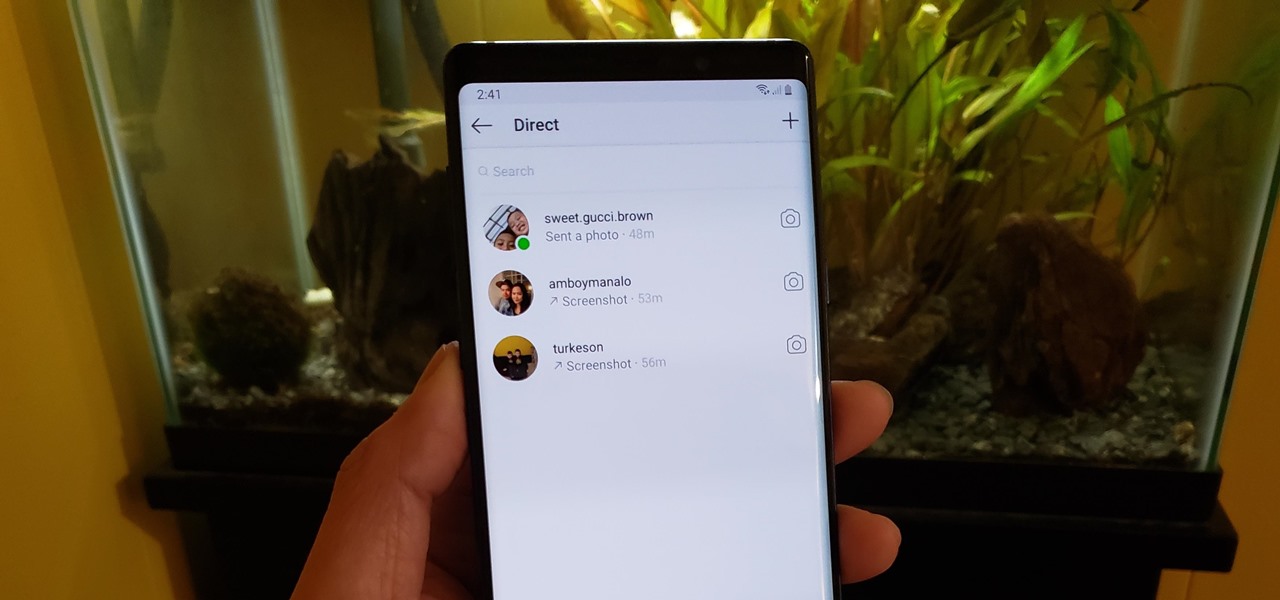
If imitation truly is the sincerest form of flattery, then Snapchat must be blushing profusely as Instagram continues to shamelessly copy its features and dig into its wallet. Instagram has also managed to copy some of the security aspects — or lack thereof — of one of Snapchat's hottest characteristics.
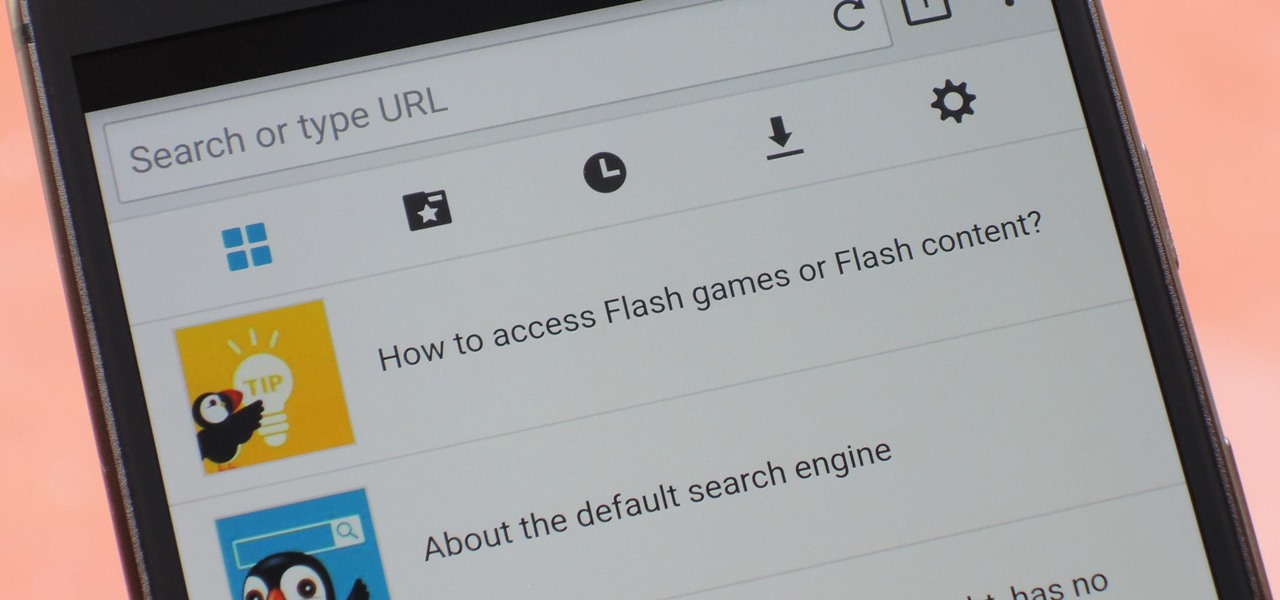
Once upon a time, Flash games reigned as some of the best entertainment the internet had to offer. But then came the smartphone, which quickly overtook this genre with similar games that you could play no matter where you were. If you yearn for the good old days, though, you'll be happy to know that you can still use the Puffin browser to safely play old favorites and discover new gems.

Bluetooth 5 was announced and made officially available on December 7, 2016. It comes with a handful of improvements to speed, range, maximum device connectivity, and anti-interference from other nearby devices. While this might be great for those special few who use Bluetooth on a daily basis to send and receive (or steal) data, what about the average Joe?

While it may not sound scary right off the bat, Blue Coat Systems now has an intermediate certificate authority. If you don't know what a certificate authority (CA) is, or who Blue Coat is, who cares, right? But you should... whether you use Mac or Windows.

Hello, everyone. Stealth is a large part of any successful hack; if we don't get noticed, we're much less likely to be caught. In these next few articles, we'll be building a shell based on keeping us hidden from a firewall. There are many ways to stay hidden from a firewall, but we'll only be incorporating a couple into our shell. This article will outline and explain these evasion concepts and techniques.

Keeping your online data and identity private is an uphill battle, but with the anonymity network Tor, you have a pretty decent line of defense from prying eyes.

If beauty is in the eye of the beholder, music lies in the ear. Even within a group of friends who share enough common interests to sit around and socialize over, music tastes can vary dramatically.

Shopping: you either love it or hate it. With a tight budget, shopping can become a huge headache for even the biggest shopaholic. We've all been there, and we've all given in to our impulses and bought something we probably shouldn't have. Yet strolling through the mall doesn't have to require a strong will to keep your credit card from entering a downward spiral. You just need to keep your hands to yourself.

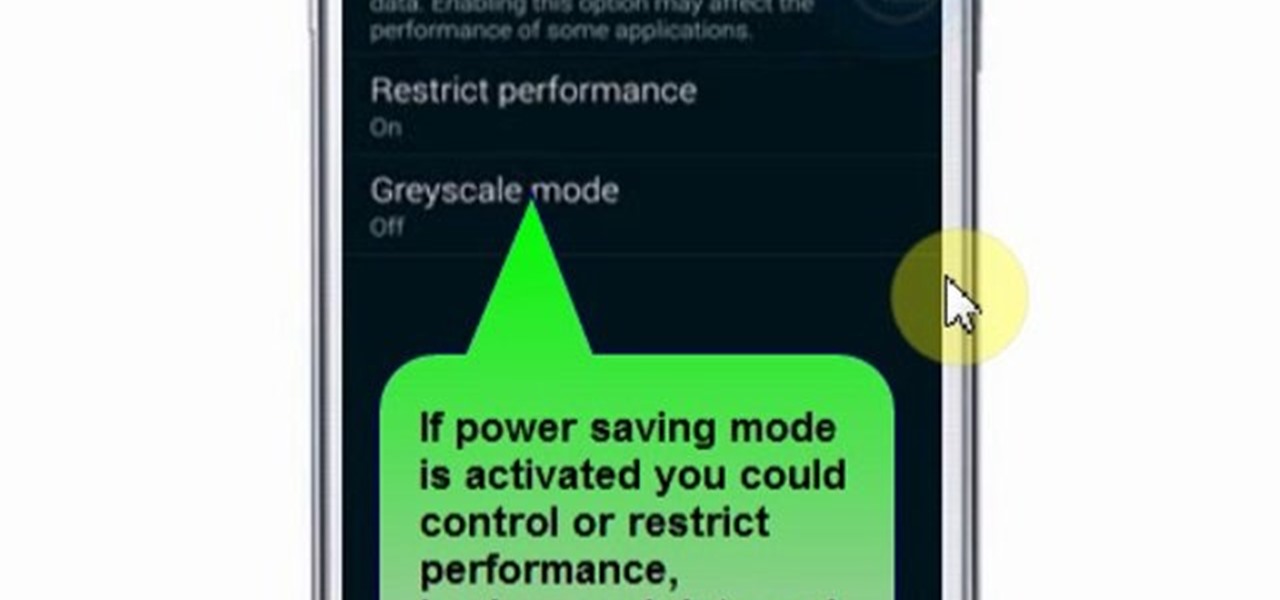
This video will show you how to set power saving mode in Samsung Galaxy S5 phone. Power saving mode will save or extend your battery life. So power saving mode will prevent unnecessary data usage. This mode will reduce screen brightness or turning off vibration and that will save your battery. This mode will control the display color which also saves battery. So this mode will save your internet connection usage and battery life. Follow the video.

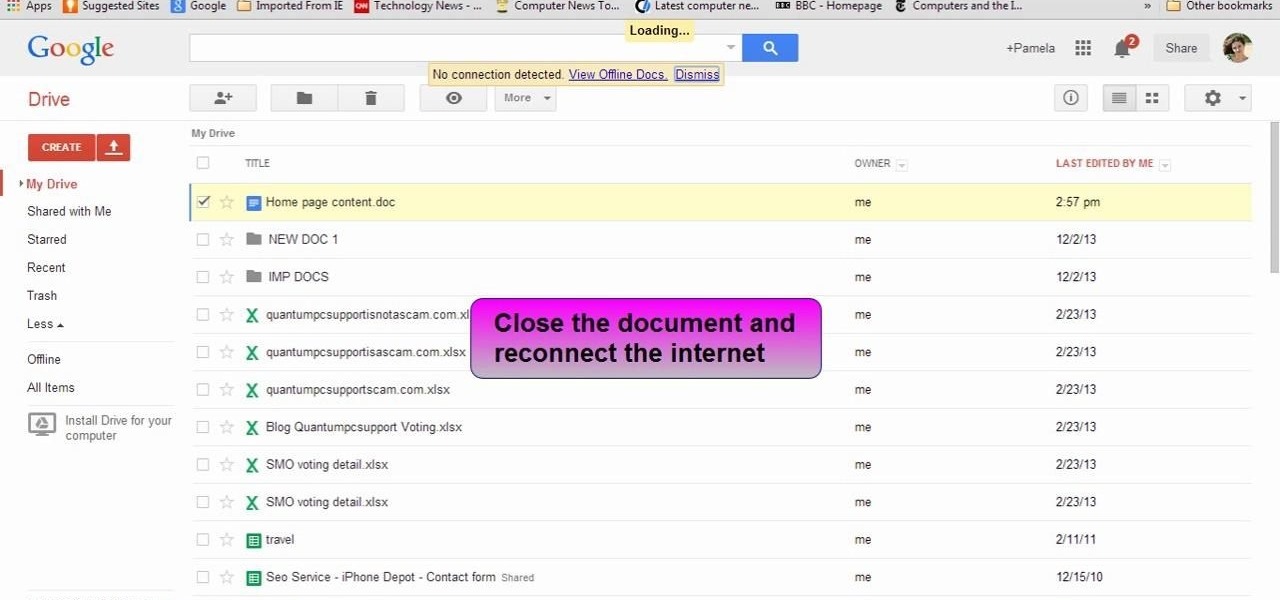
This video will show you how to view and edit Google drive documents offline. You could do this only in Google Chrome browser. If you are editing or viewing a Google drive file and suddenly internet connection is gone, you can still view and edit. You should only download an app for it. It will save your changes offline and will automatically update when you will reconnect with internet. Follow the video and do it in your Google Chrome browser.

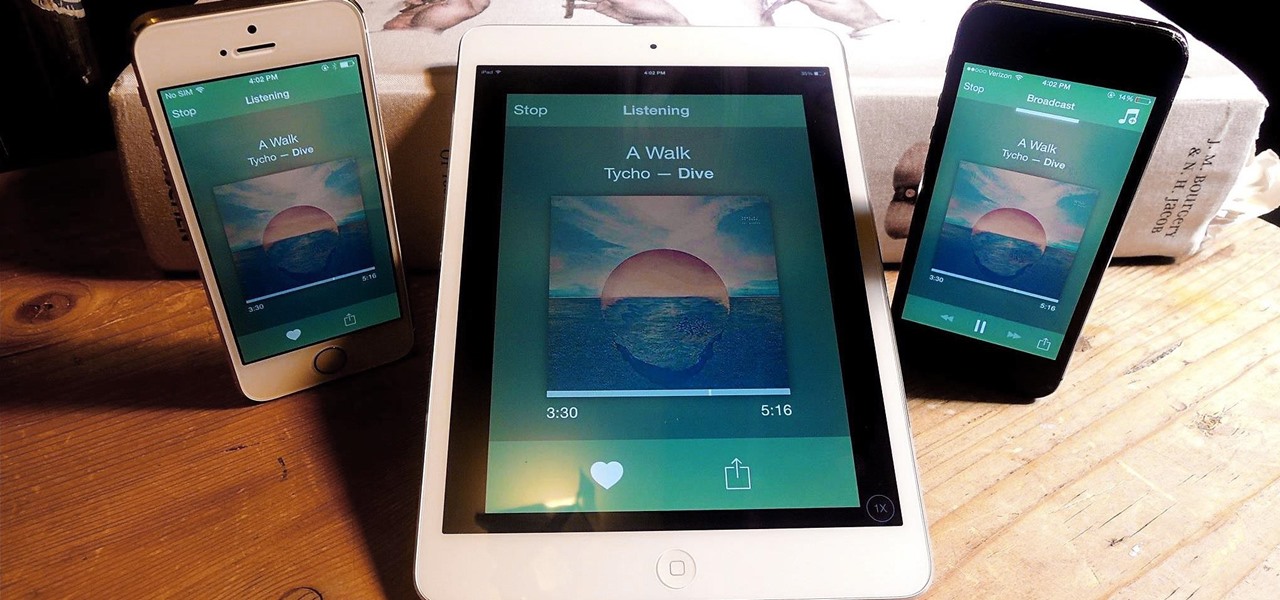
Officially, in order to use AirPlay to stream music from your iOS device, you would need either an Apple TV, AirPort Express, or an AirPlay-enabled receiver or set of speakers. Despite what Apple wants you to think, there is another way to stream music without any of those AirPlay-capable devices—you just need to have two iOS devices (or just one iOS device and a Mac).

Audibly, from iOS developer Nick Frey, allows you create playlists and sync your music across other iOS devices. Like the Samsung-exclusive Group Play or the older Seedio app, you can connect a slew of compatible devices to create a surround-sound stereo of sorts when playing your music.

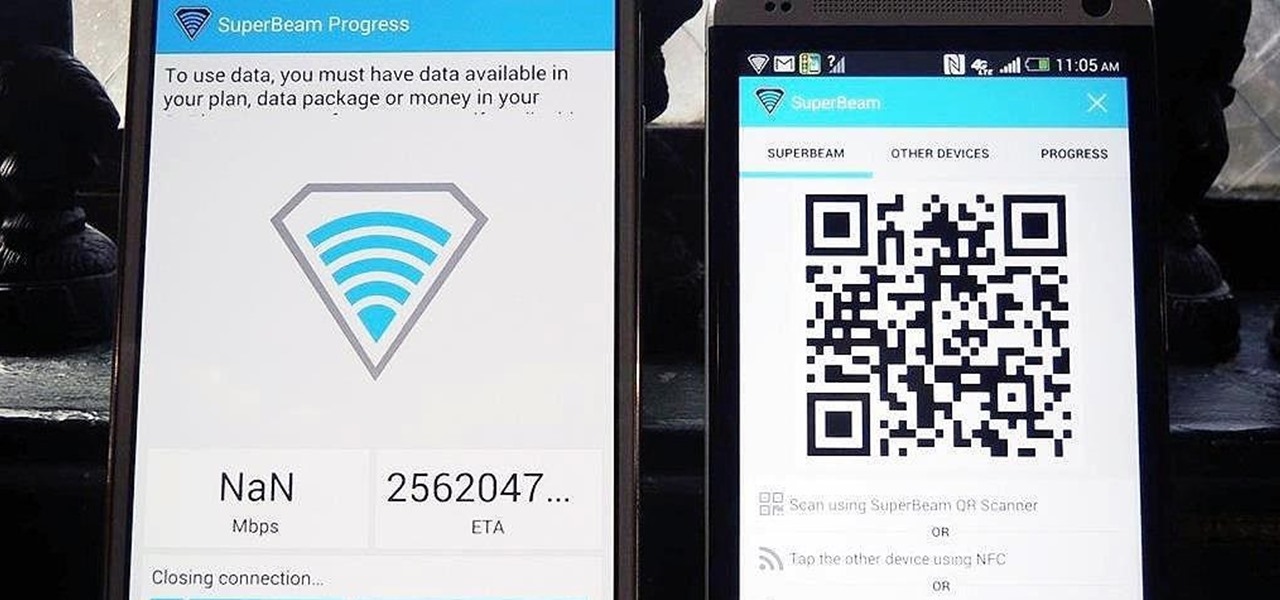
Sending and receiving files between Android devices has no shortage of options—Bluetooth, email, MMS, and Wi-Fi are just a few of the more popular ones that we use.

For the most part, transferring files from your computer to your Nexus 7 (and vice versa) is a simple process. Just hook up your tablet to your computer with the USB cable and transfer. However, most of the time you'll need additional software on your computer to do this, and then, of course, you need the USB cable.

Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.

Welcome back, my hacker wannabees! Most of my recent posts have addressed using Metasploit’s Meterpreter and what we can do once we have embedded it on the victim’s system. This includes remotely installing a keylogger, enabling the webcam, enabling the microphone and recording, disabling the antivirus software, among many other things. The list is almost unlimited.

THis video shows you what types of videos you can make, why you should make videos and exactly whant you need to get started.

Need a good way to hold your iPhone up? There are a ton of smartphone stands out on the market, but they can be pricey or just downright ugly—and potentially phone damaging. But like the Une Bobine above, they do have their perks, like movability at almost any angle. But to alleviate pressure off of the connection port, Sharon Vaknin from CNET developed her own flexible iPhone stand—from an old desk lamp and suction cup.

With Sprint already rolling out their Jelly Bean updates to Samsung Galaxy S III owners here in the United States, international users have already had a chance to check out Android's newest OS on their S3, but all is not gravy.

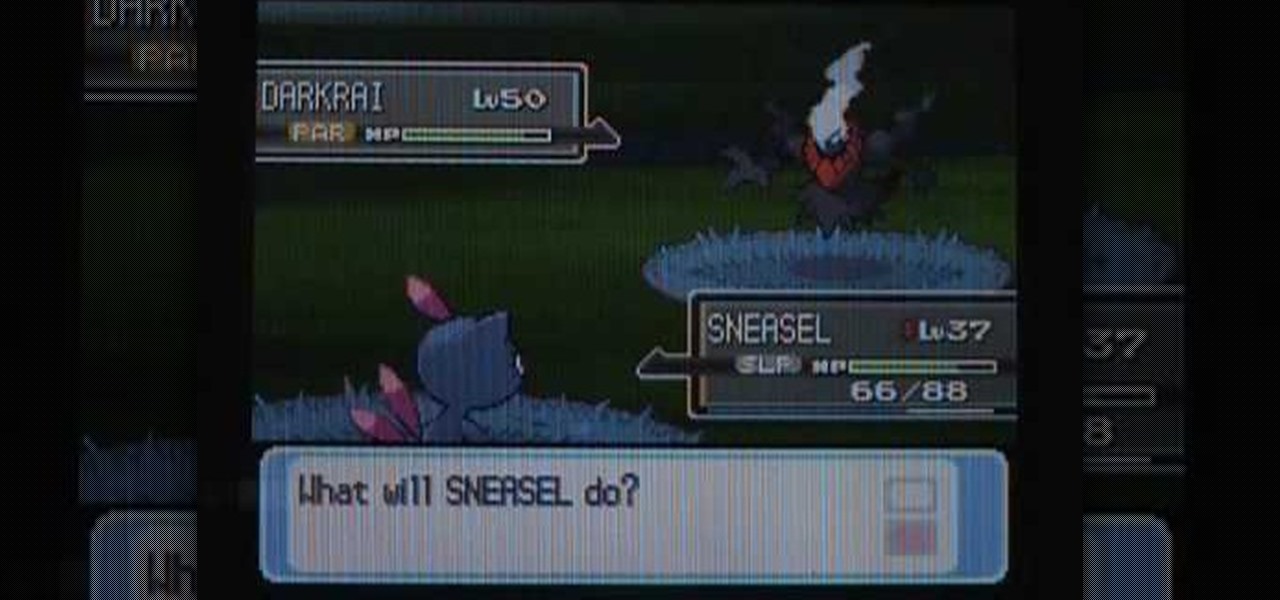
Pokemon's Darkrai is one of the most coveted levels of the game. With this tutorial, learn how to find Darkrai in a few easy steps, as well as secure a Membership Pass and a Mystery Gift in Pokemon Platinum. So grab your Nintendo DS and follow along!

Congratulations, iOS device owners! You can officially view Flash content on the web using the Skyfire web browser. This video will walk you through how the Skyfire browser works and how it converts Flash content to HTML5 content, allowing you to view it on your Apple iPhone, iPad or iPod Touch running iOS. It's about time.

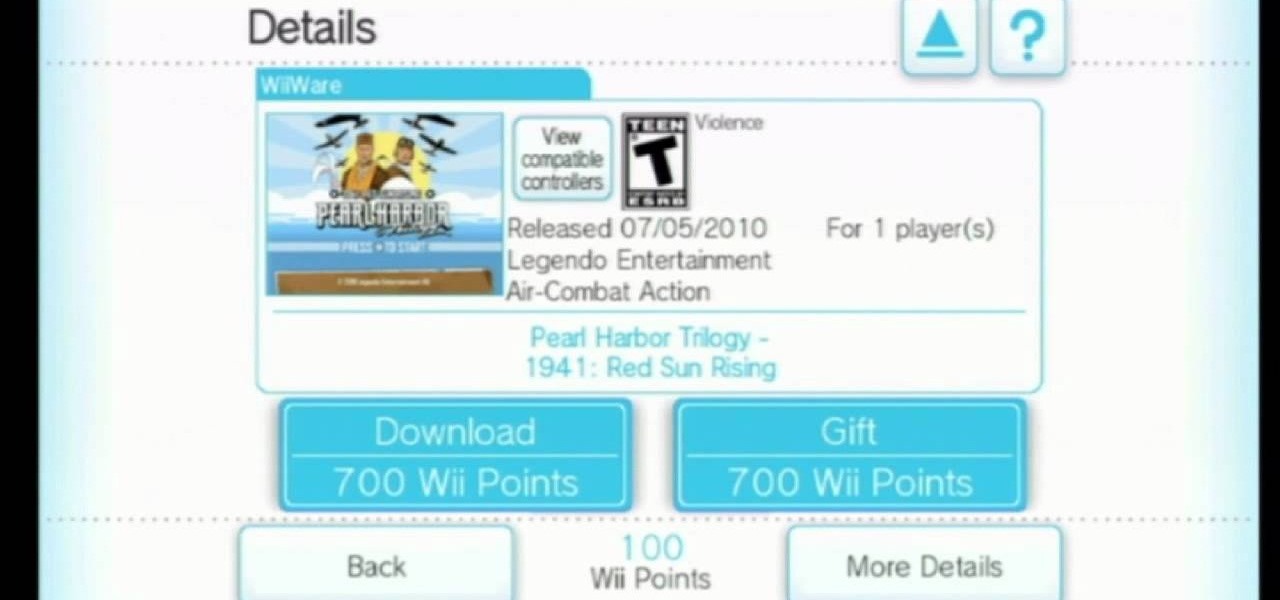
This video tutorial will teach you how to use the Nintendo Wii Shop Channel to download and play your favorite console games on your Nintendo Wii. To follow along, you'll need either a WiFi Internet connection or Wii Lan adapter.

Software manufacterers always advise you to read the instruction manual first before attempting to do anything on a new program. But who has the time to obsess over ever little boring detail in a 300-page tome when just playing around the controls on your own gets you attuned to the program immediately?

Solo camping is a scary and exciting prospect. Alone in the woods at night, no one can hear you scream. But for those who crave solitude and love the wilderness, there can be no greater thrill, no greater connection to the primitive part of yourself. In this nine-part video, we learn all kinds of useful survival and camping skills by watching our host Colhane experience a three-day solo camping trip in the Brazlilian bush. You will learn how to cook, how to make fire, how to prepare a campsit...

Chris Davis with the Educational Technology Center shows us a few easy steps to putting YouTube videos in our Microsoft PowerPoint 2007 presentations. To start you'll need to have an active internet connection and you should have the developer tab in PowerPoint active. To do this go to the Office menu, PowerPoint options, popular and click show developer tab. Locate the hammer looking more control option button and scroll down to Shockwave Flash Object and click it. This allows you to draw a ...

Peggy Erbison shares her knowledge of palmistry in this video. The heart line starts under the pinky and moves across and up towards the middle and index finger. The next line she talks about is the head line. This line is the center line that explains how your thinking is. The line that rounds out and wraps around the base of the thumb is the life line. This line connects to the head line at the beginning. These are the 3 main lines on the palm. Contrary to popular belief, the life line does...

Welcome to Google's Python Class – a seven-segment, two-part free virtual class for people with a little bit of programming experience who want to learn Python. The class includes written materials, lecture videos, and lots of code exercises to practice Python coding. The first exercises work on basic Python concepts like strings and lists, building up to the later exercises which are full programs dealing with text files, processes, and http connections. The class is geared for people who ha...

New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install cool themes on Ubuntu Linux.

XSS Shell is a cross-site scripting backdoor into the victim's browser which enables an attacker to issue commands and receive responses. During a normal XSS attack an attacker only has one chance to control a victim's browser; however, the XSS Shell keeps the connection between the attacker and the victim open to allow the attacker to continuously manipulate the victim's browser. XSS Shell works by setting up an XSS Channel, an AJAX application embedded into the victim's browser, that can ob...

It's a myth that regular users only need the protection of a virtual private network when on a public Wi-Fi connection. First, almost all network connections can be accessed without the proper permissions. Second, ethical hackers also need to think about using a VPN as one step to encrypting and protecting their activity and identity during pentests, phishing, and other actions.

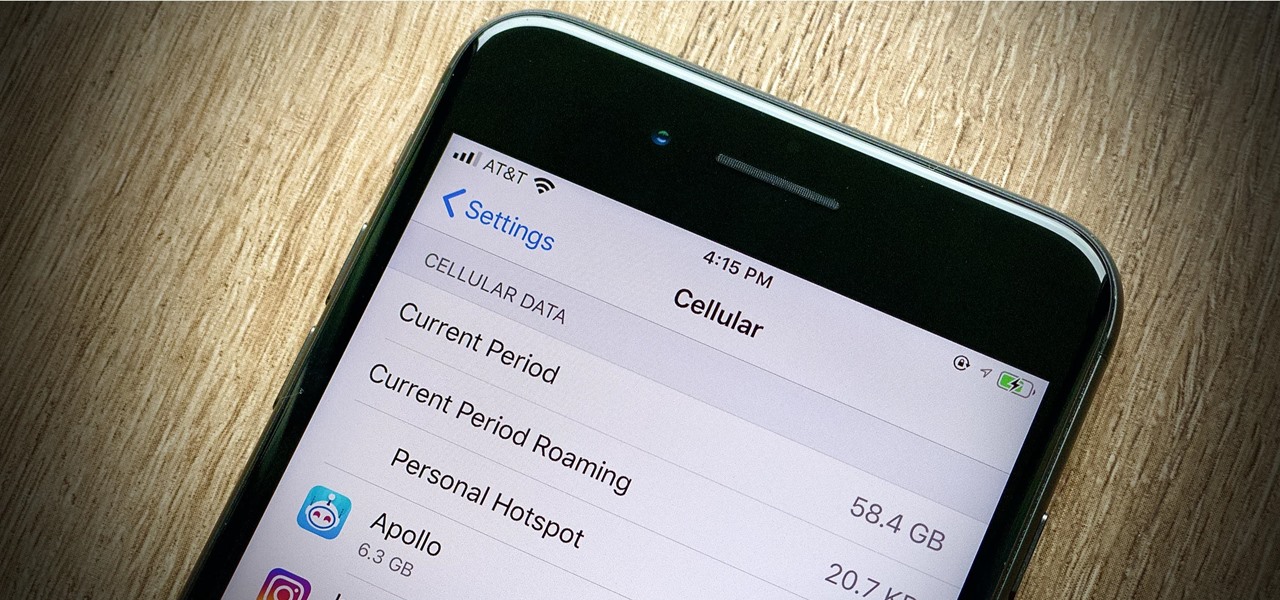
While mobile data caps are larger than they used to be, many of us still have limits to contend with. If you find yourself up against that ceiling month after month, your iPhone itself might be to blame. Luckily, there's an easy fix to stop your iOS device from burning through data in the background.

When you look at the top corner of your phone, what do you see? Upon upgrading to Android 11 or iOS 14, you'll see either "5G," "5G+," or "5G E" if you're connected to the right network. But what exactly do these symbols mean? They indicate not only if you're using 5G, but also what type you're connected to.

If you're using a VPN app to block ads or secure your Galaxy's internet connection, Samsung has decided you need yet another non-dismissible notification from One UI to tell you about it. Not just a status bar indicator like Bluetooth or Wi-Fi, but a full-size alert that can't be dismissed. The entire time your always-on VPN is running.

For the most part, Google Wifi and Nest Wifi systems take care of themselves. But there are still a few manual features that might come in handy, like being able to check on network activity to see which devices are using the most bandwidth when your connection gets bogged down.

Anything from work or a missed flight to a worldwide pandemic (COVID-19, anyone?) can make it difficult or nearly impossible to see your loved ones. You can make phone calls or send iMessage, text, or email messages, but nothing compares to seeing family and friends right in front of you. That's where FaceTime comes in.

In this post-3.5 mm world, Bluetooth is the most universal option. But a lot of older electronics still don't support wireless audio. Welp, now there's a dongle for that.