You can feel it in your bones. You may die if you don't get this phone. There's just one problem — the price. Suddenly, you come across what seems like manna from heaven. That very device, at a deeply discounted rate, can be yours.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

If you're using a mobile device, it's a pretty safe bet that your apps are sending lots of information back and forth from their servers. To make sure there is no inappropriate data collection going on, it's worth setting up a web proxy to spy on this traffic, so you know exactly which apps are "phoning home" and when.

Right on the heels of the iOS 11.4.1 beta 3 release, Apple pushed out iOS 12 beta 2 to registered developers on Tuesday, June 19. Public beta testers received the same version, labeled as iOS 12 public beta 1, six days later on Monday, June 25. Last year, the iOS 11 public beta opened up just five days after the release of iOS 11 developer beta 2, so iOS 12 is pretty much right on track in that regard.

This year's big iPhone update, iOS 12, aims to solve many of the issues that arose during iOS 11's controversial, buggy tenure. With that in mind, it may be tempting to jump on board the new software immediately and leave iOS 11 in the dust for good. Here are some reasons why you might want to reconsider joining the iOS 12 beta.

Hackers are always seeking zero-day exploits that can successfully bypass Windows 10's security features. There has been extensive research into creating undetectable malware and entire GitHub projects dedicated to automating the creation of undetectable payloads such as WinPayloads, Veil v3, and TheFatRat.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

A burner number isn't just for criminals and cheating spouses. In this digital world, with many of our interactions being conducted online, a throwaway phone number acts as a buffer — it lets you enjoy the web without having to give out your personal information, such as real name or phone number.

Its official: On May 8, T-Mobile finally released the Android Oreo update for the LG V30 and V30+. Now, every major US wireless carrier has pushed the update. For me, this update is a big deal. Not only does Android Oreo bring some new tools and features, but LG has also included a few additions as well.

Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

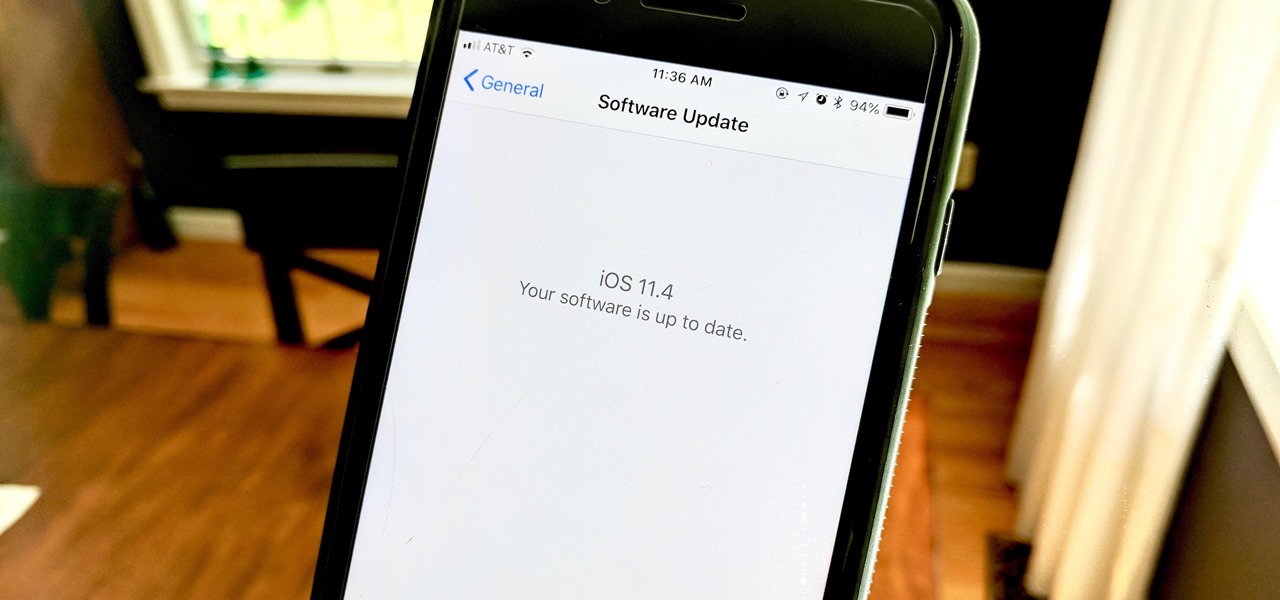
While there are at least five cool things coming in iOS 11.4, they may not be enough to get you to install the iOS 11.4 beta on your iPhone. Since its initial beta release at the start of April, there have been plenty of known issues and user-reported bugs to deal with. While bugs are to be expected with a beta, you may want to read these before installing this one on your iPhone.

If you want to follow Null Byte tutorials and try out Kali Linux, the Raspberry Pi is a perfect way to start. In 2018, the Raspberry Pi 3 Model B+ was released featuring a better CPU, Wi-Fi, Bluetooth, and Ethernet built in. Our recommended Kali Pi kit for beginners learning ethical hacking on a budget runs the "Re4son" Kali kernel and includes a compatible wireless network adapter and a USB Rubber Ducky.

Beginners learning brute-forcing attacks against WPA handshakes are often let down by the limitations of default wordlists like RockYou based on stolen passwords. The science of brute-forcing goes beyond using these default lists, allowing us to be more efficient by making customized wordlists. Using the Mentalist, we can generate millions of likely passwords based on details about the target.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

In the previous article, we learned how to set up our VPS, configure our PHP server, and developed an in-depth understanding of how the payload works. With all that taken care of, we can get into disguising our payload to appear as an image and crafting the note in the greeting card being delivered to our intended target.

With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer.

Apple has tools built into iOS to help parents monitor the iPhone habits of their children. However, those same tools can be used by everyday iPhone owners to both hide apps they don't care about, as well as restrict features they don't need or that infringe on privacy. Whether you fit into one category or the other, all iPhone users can benefit from the "Restrictions" feature.

Over the years, the internet has become a dangerous place. As its popularity has increased, it has attracted more hackers looking to make a quick buck. However, as our dependency on the web grows, it becomes increasingly difficult to sever all ties. This means we have to protect one of our weakest points, the password.

The Play Store hasn't been the most secure place for apps lately. A quick Google search for "Play Store malware" will give you a taste of some of the malicious apps that snuck their way onto Android's official app store. Google is aware of the problem and they're tying to fix it, but their new Play Protect program doesn't have a great track record, so you might want to look elsewhere.

The iPhone X was released in November 2017, and the iPhone 8 and 8 Plus dropped right before it, but the hottest news right now revolves around the 2018 iPhone releases. The rumor mill regarding the iPhone X's successor started churning out speculations on names, cameras, display size, and more almost immediately after last year's devices, and there have been many new leaked details since.

Internet Relay Chat, or IRC, is one of the most popular chat protocols on the internet. The technology can be connected to the Tor network to create an anonymous and secure chatroom — without the use of public IP addresses.

Virtual private networks, or VPNs, are popular for helping you stay anonymous online by changing your IP address, encrypting traffic, and hiding your location. However, common IoT devices, media players, and smart TVs are hard to connect to a VPN, but we have a solution: Turn a Raspberry Pi into a router running through PIA VPN, which will ensure every connected device gets the VPN treatment.

During a penetration test, one of the most important aspects of engaging a target is information gathering. The more information you have coming into an attack, the more likely the attack is to succeed. In this article, I'll be looking at SpiderFoot, a modular cross-platform OSINT (open-source intelligence) gathering tool.

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

A PirateBox creates a network that allows users to communicate wirelessly, connecting smartphones and laptops even when surrounding infrastructure has been disabled on purpose or destroyed in a disaster. Using a Raspberry Pi, we will make a wireless offline server that hosts files and a chat room as an educational database, a discreet local chat room, or a dead-drop file server.

Aircraft equipped with ADS-B are constantly shouting their location into the radio void, along with other useful unauthenticated and unencrypted data. In this guide, we will make an ADS-B receiver using a Raspberry Pi with a software-defined radio (SDR) dongle, which we can use to track aircraft anywhere in real time.

Our smartphones are full of personally-identifiable information. So much of what we do with these devices is tracked and recorded to make our experience more streamlined and personalized. For many users, that's a fair trade — but for privacy-minded folks, it's a raw deal.

Surveying a target's Wi-Fi infrastructure is the first step to understanding the wireless attack surface you have to work with.

In five short years, three generations of ultra-low-cost Raspberry Pi devices have challenged the boundaries of what a person can do with a $35 computer — especially with Kali Linux.

It's official — the newest version of Google's mobile operating system is called Android 8.0 Oreo, and it's in the process of rolling out to many different devices. Oreo has plenty of changes in store, ranging from revamped looks to under-the-hood improvements, so there's tons of cool new stuff to explore.

Autism affects 1 in 68 children in the US, and that means it affects at least 1 in every 68 families. More boys than girls are diagnosed as being on the autism spectrum, and it's estimated that almost 60,000 12-year-olds in the US have autism. That is a 37-fold increase from the 1 in 2,500 children diagnosed just 30 years ago.

When WhatsApp first came out in 2010, it quickly gained notoriety as a great way to meet new people all over the world thanks to group chats, which allow multiple admins for each group that can all add participants from their own contacts lists.

What happens when a entrepeneur/theme park creator and special effects artist/magician team up? You get a team crazy enough to create the first true virtual reality theme park (sorry, Six Flags). They only have a single experience so far, but it's already taken a giant leap beyond the wonders we've seen in today's consumer virtual reality headsets.

While iOS 11 is ready to take over your iPad, iPhone, and iPod touch, let's take a step back and check out all of the new features that iOS 10 brought to the public when it was released to everyone in Sept. 2016.

Gotta catch 'em all, right? That's easier said than done, considering that Pokémon GO has region-specific characters that you may never get a chance to see. Sure, you can spoof your GPS location to make the augmented reality game think you're at a different spot on the map, but Niantic Labs seems to be catching on to this method, and some users have been soft-banned for a few hours after trying it.

Greetings all. Today I intend to append a new series to my mini-collection of posts. This series will consist of informative guides for the purpose of depicting certain aspects of the White Hat profession that I believe are of profound importance. Furthermore, I will keep this series simple for everyone to follow, regardless of your tech level. So without further ado, let's get right into it.