
News: Glued to the car
Glue any random car with monster glueWait until 2 idiots get glued to the carwait until the owner comes and drives off and not knowing that these 2 are glued there.


Glue any random car with monster glueWait until 2 idiots get glued to the carwait until the owner comes and drives off and not knowing that these 2 are glued there.

Get a list of some of the worlds most random foods out there. Then have some of the crew (or all of them) to try them. Mix some together to get that "JACKASS" taste!

Throw a bucket of mud on a random car as they drive out of a car wash.

No one likes it when random people wander into your home and mess things up, which is why it behooves you to hide your things from even the most prying eyes with builds like this totally invisible, 2x2, piston-operated door with no visible redstone either inside or outside. The story of Goldilocks and the Three Bears may have gone differently if they would have had one of these babies installed in their home: I did a tutorial for a piston-powered trapdoor and many people wanted to know how to...
A playlist is simply a list of songs which can be played in sequential or shuffled/random order. Many people tailor-make playlists to suit a particular style of music or atmosphere, so being able to share these between people is great.

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

Today's tutorial will teach you how to erase data permanently so that it cannot be recovered. Many believe that having a file shredder on the computer means you are up to no good.

It's only been a few weeks, and already there are a lot of misconceptions and myths floating around Google+. Let's take a deep breath, and tackle some of the more prominent ones.

Is that House? Built in Minecraft? Well, time to cross out one more item off my bucket list! As inspiration for this week's Minecraft-themed Tuesday Giveaway (enter here to win an awesome Minecraft Pickaxe!), I present a roundup of amazing things found in Minecraft.
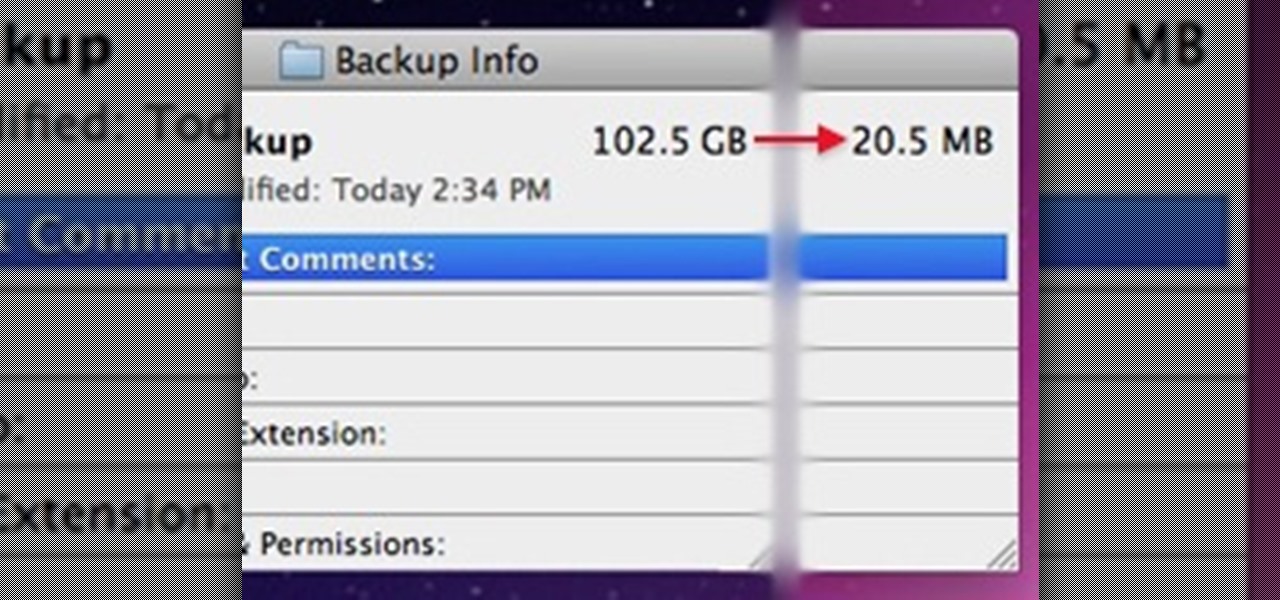
By now, you probably know that your iPhone secretly tracks and stores the locations you've visited in a backup folder on your computer's hard drive. The files are unencrypted, which means anyone with access to your computer or device can retrieve the information, which is downright scary. But Pete Warden and Alasdair Allan are making it fun with their iPhone Tracker application, which lets you map out everywhere you've been with your smartphone.

Gears of War fans around the world are excited (possibly drooling) over the upcoming release of the third installment in the series, Gears of War 3. There's a lot of hype about the game and its new features, which includes a 4-player co-op mode and a slew of new female characters. But there's one problem—it doesn't come out until September 20th. But for a lucky circle of gamers, the Multiplayer Beta just opened up today.

Making your way into an online community can be really exciting. Some life-long friendships and lasting romances begin in humble chat rooms and message boards. But for the novice internet user, one of the biggest hurdles can be trying to figure out just what people are saying to one another.

Here, ladies and gentlemen, is my main deck. The youngest card in it was printed in 2000. It makes me feel a little crusty and old for one of the first times in my life. But it does mob pretty well against all of the mostly pre-2000 decks I've played it against (none of my friends really have new cards either) and I'll tell you why:

WELCOME & THANKzZz For Your Contribution, Support And Time...! ...Hello, zZz~AKA~StanDP Here...;

Each aspirant nursing assistant is require to obtain CNA certification for their work employment. Thus, passing the CNA state exam is highly recommended. Usually the CNA testing process has two types of test - written and clinical exam. The most difficult yet challenging part of CNA test is the skill exam.

Finished Act 1 (3 total) of Red Dead Redemption and it was disappointing. The act is divided into five important people who you have to do missions for in order to progress the story. Around five missions per person on average. Only Bonnie and the Marshall's story missions felt tied to the storyline. Dickens, Seth, and Irish's missions felt like they added nothing but padding to the game. Add that nothing that you do in the game affects the world around and it's like you never existed in the ...

HAND AWARDS TO RANDOM PEOPLE AND TELL EM ITS FOR COCK SUCKER OF THE YEAR

Tell Ehren that he is going to do a prank by coming out of a coffin in pubic. When he is in the coffin take him to the top of a building. Tell him that the people who he was going to prank are going to be there in a few miniutes. Then leave, and about five min later tell him leave the coffin via walky-talky. When he gets out he will be surprised to see that he is on top of a building. Not only that but there will be some random dude up there too, and the dude will act as if nothing weird is g...

Today I was the only admin online at like 2:30 to 3:45. I had to deal with 27 people....asking me to World Edit all of their builds, and I explained how to apply online 3 different ways to 1 person...it was horrible. The other people who were online with me were getting super upset at this Guests. They were rude, and not able to understand super simple things.

In the last article, we left off with the Tor network and its hidden services. As I mentioned, Tor is not the only option in the game, and I want to offer a general introduction to I2P.

Law enforcement can make a lot of folks cringe. Too often do we hear on the news, and even experience in our own lives, the unjust way that an unacceptable portion of law enforcement treat the very citizens they are supposed to protect. People's rights are violate each and every day by law enforcement, simply because they are timid and uneducated with the laws of society. This dirty trickery shouldn't be played on harmless citizens under any circumstances.

When it comes to webcams these days, most people are using their laptops over desktops. The cameras are centered, integrated, and require no configuring. They're a cinch and usually have great resolution. So, then what do we do with all of those old wired desktop webcams that we've accrued over the years? Even if you still use an external USB one, chances are you're not using it daily, so why not come up with a better use for it?

Here's something fun for the Null Byte community to do—a coding competition! This week, I wanted to get everyone involved by offering you all a nice library of possible program types to choose from and try to code. At the end of this competition, all of the submitted programs will be reviewed by the community and myself. The coder that receives the most votes will be dubbed THE BEST.

Lost the product key for your game? If you have to reinstall the game and don't have that key anymore, you're out of luck, especially if you didn't "buy" the game. But never be in fear of losing product keys again with today's Null Byte, where we'll be practicing a little bit of mind-kung fu.

Lock picking is defined by locksmiths as "the art of opening a lock without the key". There's many ways to accomplish this, but I'm specifically interested in using a lock pick set. Since locks vary in shapes and size, it's better to stick with just one kind of lock at first. Most locks are based on fairly similar concepts, so sharing methods across locks is possible.

Technology in computers these days are very favorable to the semi-knowledgeable hacker. We have TOR for anonymity online, we have SSDs to protect and securely delete our data—we can even boot an OS from a thumb drive or SD card. With a little tunneling and MAC spoofing, a decent hacker can easily go undetected and even make it look like someone else did the hack job.

Following the first part in this series on advanced cracking techniques, we are going to go over how we can intelligently crack passwords using the old-fashioned bruteforce method. These unique cracking techniques aren't widely used, because most crackers are Script Kiddies who have no idea what the concepts are behind cracking passwords, thus, word won't get around too quickly.

How did it happen? How did your ultra-secure WPA password on your wireless network get broken into? Well, you might have just found yourself at the mercy of a cracker.

Here's a nasty little Null Byte. An open redirect vulnerability was found in both Facebook and Google that could allow hackers to steal user credentials via phishing. This also potentially allows redirects to malicious sites that exploit other vulnerabilities in your OS or browser. This could even get your computer flooded with spam, and these holes have been known about for over a month.

I'm pretty sure that it's a universal dream for everyone in the world to retire early. Who wants to to be stuck with the rest of the country and retire when you're almost 70 years old? You heard me right, 70! Most people can't go out and do the things they love to do by the time they're 70, unless they've been practicing good health and exercise their entire life.

VNC is a great protocol that you can use on Windows and Linux machines to remotely control computers. This is useful if you need to control your computer when away from home, help your grandma check her email, or help a client with a disk cleanup. VNC is secure in the sense that it requires authentication in order to make the connection, but after that, the data is sent over the internet unencrypted. This means that an attacker could sniff your traffic and snoop everything that's going on. Th...

If you've ever heard software piracy terminology being discussed, I'm sure the term KeyGens came up. KeyGens is short for key generator, which is a program that exploits algorithmic faults in software by generating software license keys that appear to be genuine. Normally used as a technique to protect the source code software and prevent piracy, a key generator exploits the key algorithm to effectively nullify the need for any software licenses. For example, we must try to find patterns in t...

Zynga just added another game to their Zynga with Friends series called Scramble with Friends. If you've ever played Boggle, it's basically the same thing, but is dedicated to playing your buddies just like Words with Friends or Hanging with Friends.

With the purchase of my latest computer, installing Linux turned into a nightmare from Hell. The graphics drivers are probably the biggest issue that anyone with a newer computer will run into when installing Linux. AMD and NVIDIA are the dominant ones on the market, both of which have awful support.

Paying for web hosting isn't ideal in most situations. If you have your own website, hosting it yourself is very acceptable and easy to do, assuming your internet bandwidth permits. Most people want to run a personal site, nothing crazy, so hosting from home on low-bandwidth internet is actually a better solution in most cases.

Shortening URLs has become a necessity in this age of Twitter and limited-character status updates. It not only allows us to cram more words into our oh-so-important Twitter statuses, but it also helps us with a few other things.

Having an SSH or Secure SHell to tunnel your traffic through is something we have talked about many times at Null Byte. As we know, it allows us to securely route and encrypt our traffic through a remote server, effectively anonymizing us and protecting our traffic from all forms of analysis—simultaneously. We have gone over how to make a home SSH tunnel. However, the question has come up, "How can I get an SSH tunnel to somewhere other than my computer?" This would be useful in a situation w...

Flash memory can be a tad unpredictable at times. I have had 4 flash drives die out on me over the last few years, and they usually die without warning. When a flash memory based device dies, the data is likely impossible to recover. Adversely on an HDD, or Hard Drive Disk, even if the disk dies out, someone will probably be able to fix it and get it back to working order—at least long enough for you to back up your data. Hard drives are a bit more forgiving. As you can guess, due to the unpr...

Another Community Byte announcement from Null Byte! The Community Byte projects serve to teach people in a co-operative, hands-on manner. Learning from experience and immersing yourself in a subject is the best way to learn something foreign to you. In our sessions, we have started to both code and complete HTS missions. There is something for everyone here, so make sure you join in on the fun learning experience.

File Transfer Protocol, or FTP, is a network protocol made for transferring files in a client and host fashion over a Transmission Control Protocol (TCP) network, such as the internet. FTP is integrated into most browsers, and you have probably used it before. It is a common way to host files and transfer them easily. To access an FTP, a login is required, unless the server is configured to use anonymous logins (like the Arch Linux mirrors).