Ethylene is an invisible, odorless, naturally occurring gas that aids in the ripening process of fruit. As a fruit produces more ethylene, it begins to create enzymes which help break down cell walls and starches, making the fruit softer and sweeter over time. If it weren't for this small hydrocarbon gas, the shelf lives of most fruits could last well over a year.
If you have a Samsung Galaxy S3 or Galaxy Note 2, you might not have noticed it yet, but there's an annoying little bug that centers around your clipboard. If you tend to do a lot of copy/pasting on your device, you've probably seen it happen—your phone crashes.

The problem of system freezes is not new to the world of Windows and this has come to light even in the latest Windows 8 release. In the event that your system freezes, you cannot open your desktop files, some controls stop functioning, or you are unable to launch the start screen applications either. You may experience this unusual behavior after updating Apps in the store or due to a driver issue. Sometimes, freezes occur because of video card problems too. In order to do away with these Wi...
The stock music player on the iPhone hasn't changed much since its inception. Sure, with the recent iOS 6 update the design became sleeker, but it's not really what you'd expect from a top of the line smartphone. And when I say "MEH," it isn't directed towards the Kendrick Lamar album (which is awesome). It's the layout of the application, the lack of gesture control, and the sometimes tedious job of shuffling through certain albums and artists.

"Cheating is for losers" is only something that losers like to say. If you want to smash your friends and fly up the leaderboards, though, sometimes you have to go that extra mile.

SNAP. That's the sound of your Samsung Galaxy S3's camera going off. Not that big of deal, unless you're trying to take some top secret pics or some candid shots of your friends. The shutter sound gives you away, and the next thing you know, you're deleting pictures. On most other smartphones, if the users turns the phone on silent or vibrate, the shutter sound is killed. If that doesn't do the trick, usually muting the shutter sound itself in the settings will do the trick. But for some of y...
Are you scared that the RIAA is about to track you down for illegally downloading songs. Well, here is a method of obtaining many songs absolutely free that is virtually untrackable

First off, I would like to say two things. One, this is not for beginners; if you don't feel that you understand this how-to at all, do not try it. Second, never ever install random software or change settings if you do not trust the source.

If you're anything like me, you probably rinse your mouth out after you brush your teeth. I know technically you're supposed to not rinse your mouth out after brushing, but I just can't stand the feel of the excess toothpaste in my mouth. It's a surefire way to dry it out.

Apple's latest update for iPhones, iOS 13, introduces over 200 new and exciting features. Many of those changes come to Siri, resulting in a better, more useful version of the digital assistant we've known for years. If you simply look at iOS 13's webpage, however, you wouldn't realize just how much Siri has changed this time around. We're here to fill in the blanks.

According to Google at their 2018 I/O conference, Google Assistant is now available on over 500 million devices. Now that the assistant is available on iPhones as well, Google has to give iOS users a reason to switch to its assistant over the built-in Siri. Today, Google has eight more reasons for users to do so.

Update 10/23: The hits just keep on coming. We're now seeing reports of a "smearing" effect when scrolling through apps on the Pixel XL 2. We'll expand on that at the bottom of this article, but it's still worth reading the background information on issues with LG's new POLED displays.

Welcome back, my novice hackers! This new series on Bluetooth hacking was inspired by a recent episode of Mr. Robot (my favorite TV show). In episode 6, Eliot hacked the bluetooth keyboard of the police office in order to hack the prison and release his nemesis, Vera. This is just one of the many hacks we will explore in the series.

Welcome back, my novice hackers! Episode 6 of Mr. Robot has come and gone and, as usual, it did not disappoint. Once again, our hero, Elliot, has used his extraordinary intellect and hacking skills to awe and inspire us.

I'm always looking for solutions to problems people are having with their smartphones. This means I spend a lot of time browsing forums and release sites looking for new apps. In doing so, I find a lot of apps that don't quite solve a major problem, but are nonetheless pretty cool. I came across four of those this week.

February is the shortest month, but it's marked by the celebration of Black history and the celebration of romantic love.

One of the biggest bummers about Netflix is the inability to create different lists for your favorite movies and TV shows. Instead, you're only able to lump titles into the single default "My List," and that can be impossible to browse. It doesn't separate titles into categories or genres, and titles are arranged for you automatically, so there's not much room for customization.

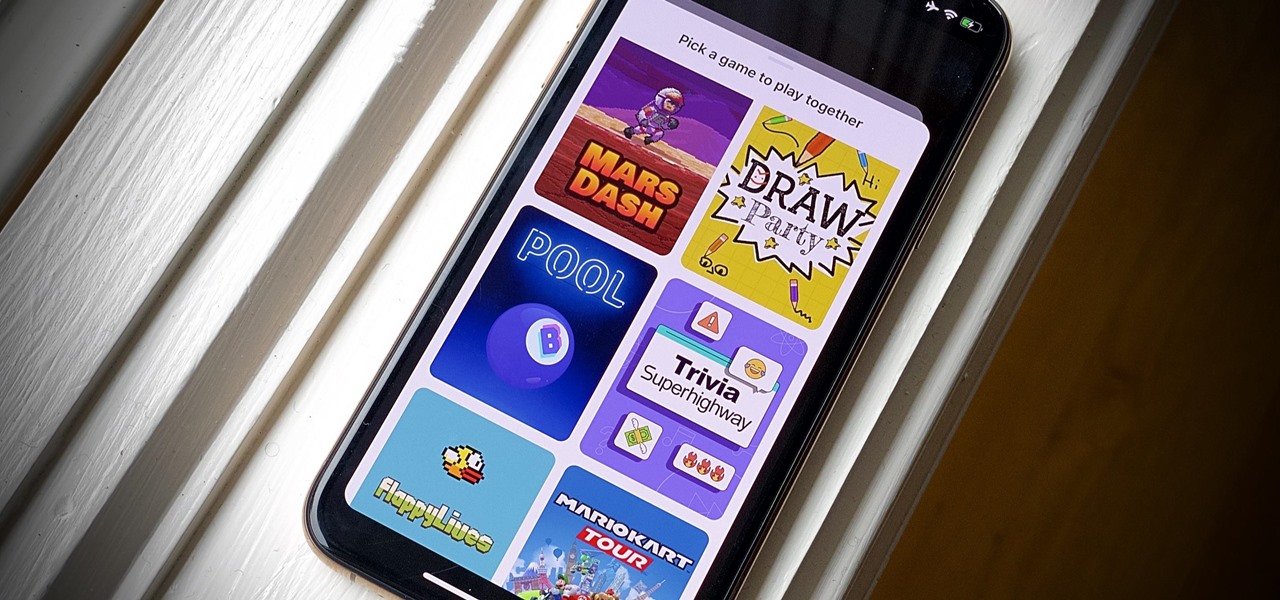
Even for those of us who enjoy spending time alone at home, at a certain point, it just gets boring. We all need social interaction, but with stay-at-home orders, that can be hard to come by. If you're feeling the itch to hang out with friends and have a good time, you should know there are plenty of free multiplayer games for iPhone and Android that will let you do just that — remotely.

Windows 10 passwords stored as NTLM hashes can be dumped and exfiltrated to an attacker's system in seconds. The hashes can be very easily brute-forced and cracked to reveal the passwords in plaintext using a combination of tools, including Mimikatz, ProcDump, John the Ripper, and Hashcat.

While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the internet for clues during an investigation. These are a list of my top ten favorite browser extensions for hackers — and how to use them.

Now that we have our payload hosted on our VPS, as well as Metasploit installed, we can begin developing the webpage which will trick our "John Smith" target into opening our malicious file. Once he has, we can take over his computer.

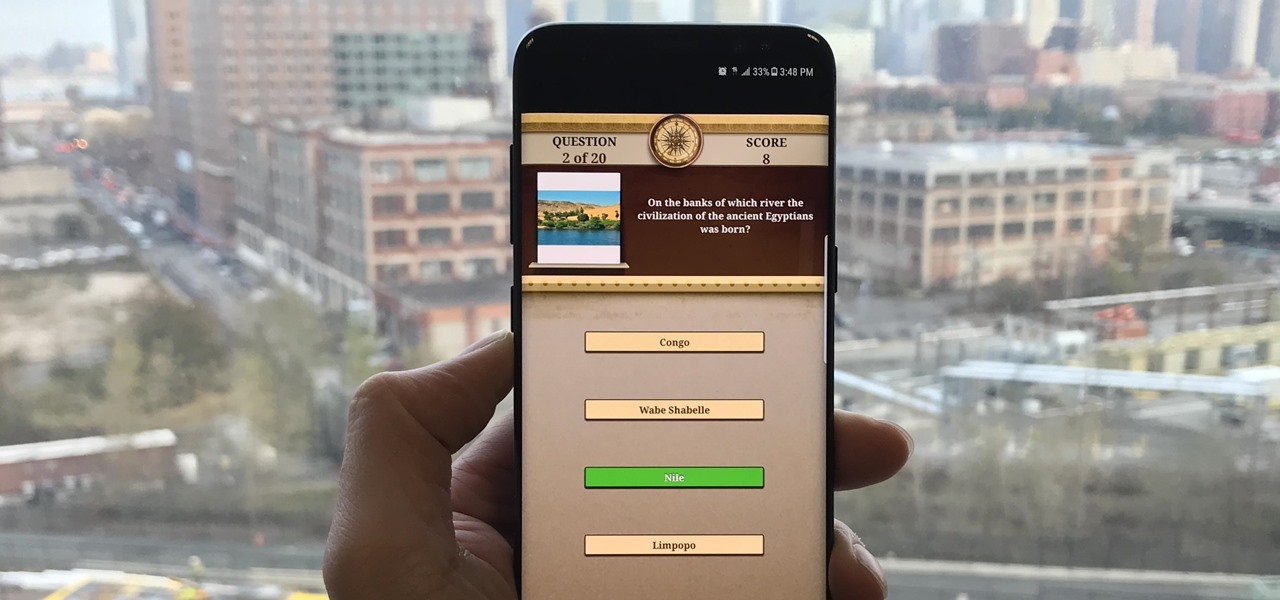
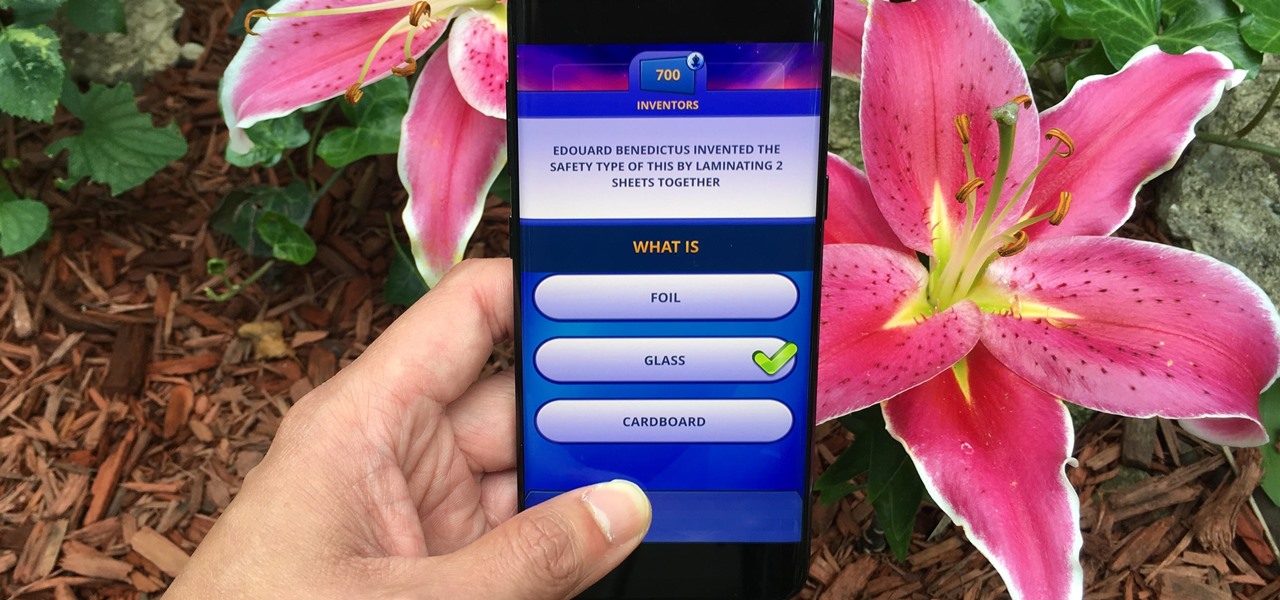
Trivia games are among the most entertaining ways to learn factoids and interesting info you may have never known about before. They're also the perfect genre to enjoy with friends and family, as they're particularly great at breaking the ice to make for a more memorable time together.

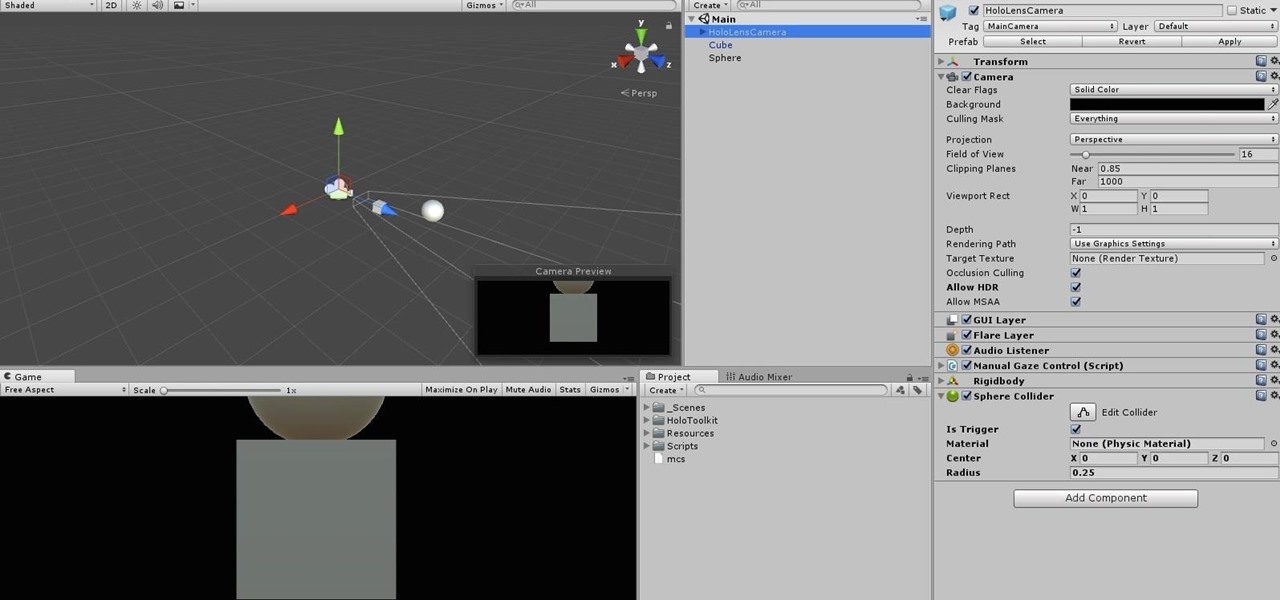
After previously learning how to make the material of an object change with the focus of an object, we will build on that knowledge by adding new objects through code. We will accomplish this by creating our bounding box, which in the end is not actually a box, as you will see.

Trivia games are a great way to test your knowledge and learn about people and things you never knew of before. They're ideal in a group setting because they can serve as the perfect conversation starter when you're enjoying time with friends, family, or even complete strangers.

When making a convincing mixed reality experience, audio consideration is a must. Great audio can transport the HoloLens wearer to another place or time, help navigate 3D interfaces, or blur the lines of what is real and what is a hologram. Using a location-based trigger (hotspot), we will dial up a fun example of how well spatial sound works with the HoloLens.

For years, smartphone makers have been caught up in a megapixel spec race to prove that their camera is better than the next guy's. But we've finally come to a point where even the lower-end camera phones are packing more megapixels than they need, so it's getting harder to differentiate camera hardware.

Welcome back, my fledgling hackers! Over the years, we have examined multiple ways to own, exploit, or compromise a system. On the other hand, we have not spent a lot of time on denial-of-service (DoS) attacks.

Welcome back, my hacker novitiates! In the previous two posts in this series, we looked at the basics of buffer overflows. In this post, we will look at one technique for finding buffer overflows. We will try to send random, oversized, and invalid data at a variable to see whether we can make it crash or overflow. This process is known as fuzzing. It is often the first step to developing an exploit, as we need to find some variable that is susceptible to overflowing.

People who know that I am a professional hacker often ask me what they can do to make their computers and personal information safe from people like me. The answer, of course, is that nothing will make you completely safe, but there are a number of measures any computer user can take to reduce the chances of being a victim of a hacker.

April Fool's Day, aka National Screw with Your Friends Day, is finally here. You can always pull a conventional prank, like strategically placing a whoopee cushion on your mom's chair, but that joke has been exhausted generations before smartphones were around. We live in a day and age where smack cam is the new level of pranking, so it's time to step your game up, novices.

One of the biggest problems in data security is authentication of data and its source. How can Alice be certain that the executable in her inbox is from the venerable Bob, and not from the not-so-venerable Oscar? Clearly Alice wants to know because if this file is actually sent to her by Oscar, the file might not be a game, but a trojan that can do anything on her computer such as sift through her email and passwords, upload her honeymoon pictures, or even turn on microphones and webcams. Thi...

Welcome back, my budding hackers! One of the most time-consuming, but necessary, activities in hacking is reconnaissance. Before we can hack a system, we need to know what operating system it's running, what ports are open, what services are running, and hopefully, what applications are installed and running.

Most of us have conducted an investigatory science project without even knowing it, or at least without knowing that's what it was called. Most science experiments performed, from elementary to high school students and all the way up to professional scientists, are investigatory projects.

Let's say that you've got the look down, and you have your Steampunk props all ready to go. Congratulations! You're a Steampunk!

First of all you need two different types of playing cards. You can take the blue and the red color cards. Spread these cards on the table facing downwards. Now mix them together randomly. Again mix them as thoroughly as you can on the table. Now pick out a red color card of your choice from anywhere on the table. Now again mix the cards thoroughly on the table. Now pick up any blue card of your choice anywhere from the table. Now ask the audience “what probability is that of picking the sa...

Hack mybrute with this mybrute cheat. MyBrute hacks, cheats, tricks. Watch this video tutorial to learn how to get a pet dog, wolf or bear in MyBrute (06/02/09).

Project managers — and those hoping to become one — should rejoice at this killer deal. The Project Manager's Essential Certification Bundle Ft. Scrum, Agile & PMP usually runs for $1,990 but is only $49.99 for a limited time.

As necessary as sleep is, millions of people struggle with it every night. More than 50 million Americans suffer from any number of sleep disorders. If you're one of them and want a more satisfying, consistent sleep, then the LectroSound Sleep & Relax Soothing Noise Machine may be the perfect addition to your bedroom. For only $15.99, you can give yourself the rest and reinvigoration that your body and mind crave.

It is a scary time to be alive. As states start to ease back shelter-in-place restrictions, the new world you're entering is still unsafe. With a vaccine months away, your best bet is to follow CDC guidelines and use the tools at your disposal.

Hacking web applications can sometimes be challenging due to the sheer amount of moving parts they possess. At the core of these apps are HTTP requests and parameters, but these things are often concealed from the user, due to security reasons, convenience, or both. However, a tool called Arjun can be used to discover hidden HTTP parameters in web apps.