Welcome back, my hacker novitiates! In previous guides, we have used one of the most powerful hacking platforms on the planet, Metasploit, to perform numerous hacks. They ranged from exploiting Windows XP and Windows 7/8 vulnerabilities, to installing a keylogger and turning on a webcam remotely. We have even been able to save the world from nuclear annihilation, see if our girlfriend is cheating, spy on suspicious neighbors, evade antivirus detection, and more.

First off—Happy Independence Day! Since it's the 4th of July, let's make this week's roundup short and sweet, so you can all get back to your holiday festivities.

Childcareland has shared with us the most easy way possible to make attractive colorful flowers using nothing but coffee filters, pipe cleaners, felt pens, water spray, and tape.

So you're into Emo music and are looking to dress the part? Look no further! EmoWorldTV shows you a few simple steps to make yourself totally Scene. Scene girls are unique, cute and always check their MySpace pages. So, get out your makeup, your digital camera and some scissors and start styling yourself Scene.

Learn how to read the secret thoughts of three friends! This video is a great trick to perform at a bar or while sitting around with fiends. They'll be amazed when they think you are capable of reading their minds!

Though impressive, reading minds in person has been done and overdone. Revamp this tired sport by learning how to mind read over the phone and even on Twitter.

To make a journal made of junk you're going to need a couple of things. First an unbleached linen thread because it doesn't bleed out into your work, you'll need a candle, a binder clip and a stack of papers. The papers you need to fold down the middle and put in four evenly spaced holes down its spine so that it looks like a book. Use the clip to hold the papers together while you measure the thread. The thread needs to be three times the height of your book. Wax this thread using the candle...

This video from Do as I do presents a simple card trick. Cut the deck in half.

1. First moisturize the face. 2. Trim and cover the brows, to conceal the eyebrows. 3. Apply foundation, use Studio fix powder set foundation. 4. Use Contour with TANTON blush and the 242 on the sides of nose and the eye brows. Blend using the 217 5. Use random Lise Watier Brush for the cheeks. And blended base contour with the 217. 6. Use CARBON+ANGLE BRUSH to mark the eyebrows. 7. Use CARBON+217 to get dark contoured lids and use 282+CARBON harshly lining and winging out to enhance the eyes...

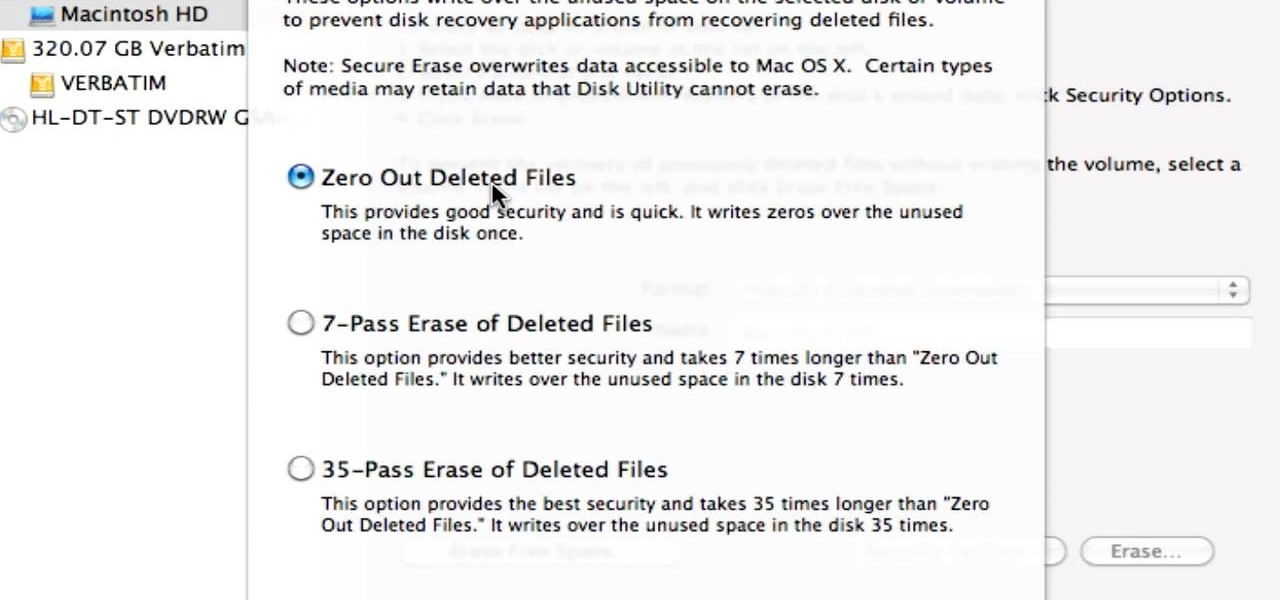
Did you know that even after you've emptied your Mac's trash can, the data still has not been permanently removed from your system? Anyone who knew where to look could easily unearth this data. You can prevent this by using the secure empty trash option on your Mac. Whenever you put something in the trash, instead of pressing delete, go into 'finder' up top and press 'secure empty trash'. What this will do is replace the data that is left behind on your hard drive with random ones and zeros. ...

Jessica Harlow presents a great look for Halloween. She mostly uses eye shadows by "Beauty from Earth" and "Obsessive Compulsive" brands, but thinks it is OK to use colors from any 88 shade shimmery shadow palettes available in the market.

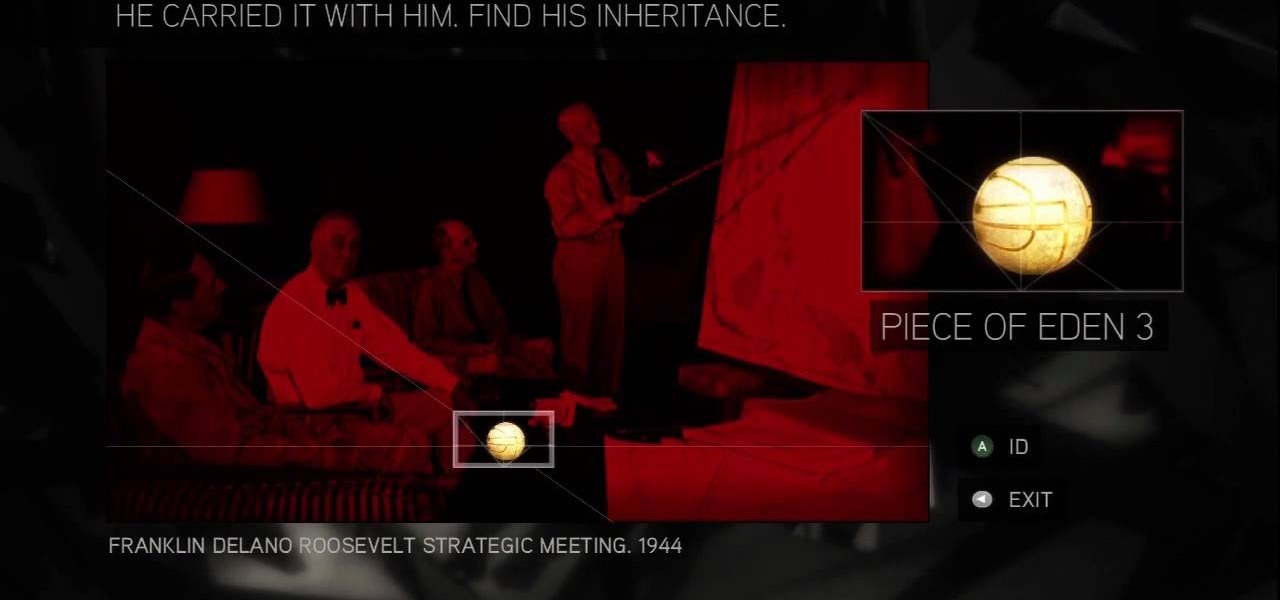
Find out about the third puzzle in Assassin's Creed 2. Another simple one – just highlight the spot in each image where the Apple is hiding. You can click around at random and maybe find a couple of hidden messages. For more info, watch the whole gameplay.

Do you have coworkers who use the hunt-and-peck method of typing? This trick is guaranteed to drive them completely bonkers.

Watch this video tutorial to see how to build a fun foam boffer sword! These boffer swords for any of your larping needs!

Newton Virus is the first art virus by Troika. In the beginning were harmless computer viruses. Viruses born out of the wit of early computer adopters, viruses whose sole purpose was to surprise and amuse. A non-destructive form of artificial life.

This Houdini 9 software video series focuses on examples of when and how to use Attribute Transfer. Part 1 covers Attribute Transfer One Point:

While many people may use Bluetooth every day, the majority don't know how it works or that it can be hacked. Bluetooth hacking gives a clear window into the world of the target. Nearly every device has Bluetooth capabilities, and people store a great deal of personal info on their phones and tablets. Hack their Bluetooth connection, and you may be able to access all of that data.

Gmail has been the email standard for quite some time now, and for good reason: it's a free service provided by one of the largest tech companies in the world that offers users an amazing feature set to manage, send, and keep track of all their important emails.

Welcome back, my aspiring hackers! In recent tutorials, I have made reference to the name and location of the Linux devices in the file system, such as sda (first SATA or SCSI drive). Specifically, I have mentioned the way that Linux designates hard drives when making an image of a hard drive for forensic purposes.

Welcome back, my novice hackers! The worst thing that can happen to any hacker is being detected by a security admin, the security technologies (IDS, firewall, etc.), or a forensic investigator.

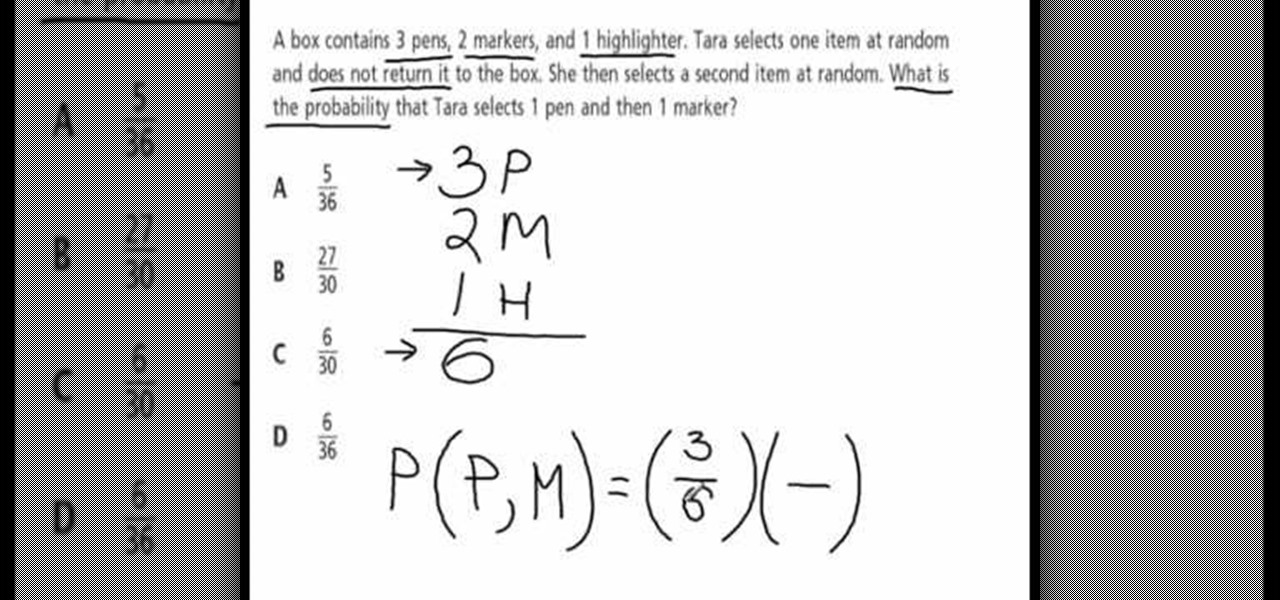
This video explains how to solve the problem of probability dependent events. In this video the problem is that a box contains three pens, 2 markers, and 1 highlighter. The person selects one item at random and does not return it to the box. So what is the probability that the person selects 1 pen and 1 marker. That is 6 items total. First she count the all items that involved in this problem. Then count the individual probability of the pen and marker. The person selects 3 pens out of 6 item...

If you want to get tiger style nails first you need to paint a clear base coat on your nails. Now, you should take a vinyl shine nail polish that is a gold-ish color and pant this on each nail as a single coat. You should try to get a nail polish that dries fast - so let this coat dry. Now, get an orange nail polish and dot this color on your nails in random spots. You do not have to do this in any particular design. Now let this dry. Next, with a black Art Deco nail polish, paint and draw th...

This tutorial shows the viewer how to make polymer clay look like wood. Begin by using a pasta machine and roll out ecru on a number four and rolling out brown on a number six. Stack the brown on top of the ecru and cut the stack in half. Then sandwich the two stacks so it goes light - dark - light - dark. Repeat the process by Cutting it in half and stacking them again. Roll this stack through the pasta machine on a number one so it squishes them together. Cut in half and stack. Repeat this ...

This video is about how to make uTorrent 2.0 faster. The first step that you will have to do is to open your uTorrent 2.0. Once you have opened uTorrent 2.0, go to "options" then click "Preferences". Once you have clicked "Preferences", go to "Connection" found on the left side of the window. Then beside the random port, change the numbers to "45682". After you have changed it, go to "Bandwidth". Then change the maximum upload rate to "15". Also change the maximum download rate to "1890". You...

Check out this video to learn how to do this makeup look inspired by Vanessa Hudgens! 1. Protect your hair from heat damage with a heat protectant such as V05 heat defense.

If you have habits that are repetitive, time-consuming, and don't seem to make sense, and they interfere with daily functioning, you may have Obsessive-Compulsive Disorder.

Apple's dedication to iPhone security is one of the company's biggest selling points. It's no surprise then that iOS 12 offers users a simple yet powerful way to make, save, and auto-fill strong passwords to your iCloud Keychain when creating accounts in both Safari and in apps. The best part? You hardly need to do a thing.

There has been significant debate over law enforcement's right to access our digital devices in recent years. New tools from Grayshift and Cellebrite are popping up faster than ever to help government agencies, as well as traditional hackers, break into iPhones. If you're concerned, you can take steps right now to beef up your passcode and prevent outsiders from gaining access to your device.

A couple weeks ago, GM's Cruise Automation released a remarkable self-driving video from the streets of San Fransisco that Driverless analyzed in detail. And now they've just released a new one giving more insight into their growing mastery of the complex roads in San Francisco, specifically, the Potrero Hill and Mission Dolores neighborhoods.

When was the last time you restarted or shutdown your Mac? In the post-iPhone era, most devices are now powered on almost constantly. For better or for worse, the computing landscape has accommodated this "always on" trend, but you still need to periodically restart your devices—especially your Mac.

Like previous installments in the Pokémon series, as you progress through Pokémon GO you'll be able to evolve your Pokémon into more-powerful monsters with new and more-damaging attacks. However, unlike older entries in the series, your Pokémon won't simply evolve when they reach a certain level. Instead, you'll have to "feed" them a certain amount of character-specific candy to induce the transformation.

Nobody's supposed to know where the Batcave is, but as most everyone thought, Batman's underground lair lied below the estate of his secret identity, Bruce Wayne, in Gotham City.

Google has added some fun Easter eggs to Hangouts that'll give you a few more ways to procrastinate throughout your day. All of them (except for one) work on the web browser version, the Chrome app, and the mobile apps for Android and iOS, and are activated by sending a specific message.

Instagram is not only a great platform to easily share some of your favorite moments with friends and family, it's a useful service for peering outside of your physical location. While you share a picture of your dog in Los Angeles, you can almost instantly view and like a picture someone posted of their breakfast in Tokyo.

No matter how cool my 3D live wallpaper is, or how often my Google Now wallpapers automatically change, I always want more backgrounds. Zedge has made it easy for me to find new ones, and 500 Firepaper helps me keep my background lively with rotating wallpapers—but these aren't enough.

In order to perform the Four Kings magic card trick, you will need to begin with the set up. Remove the four kings for the deck. Place the four kings on top of the deck. When they pick a card, force your king as their card. Make it look like you are pushing their card into the center of the deck, instead, put it at the bottom of the break: i.e. underneath the 3 other kings. Show them the top four cards and show them that one of the cards is theirs, but peel off 7 cards, showing them their kin...

Get wavy hair with no heat by watching this tutorial. After shower, to dry hair, do not use heater dryers. Use a towel. Just place the towel on the hair rinse it. Then cover up the hair with the towel and let it dry on its own.

Ham radios are a form of amateur radio that anyone can use. This is a great video series for anyone looking to connect with other random people through wireless means.

Some may find it annoying to get YouTube notifications randomly throughout the day. Every time a YouTube channel uploads a video, every time someone replies to your comments. But at the same time, you don't want to turn off those notifications so you don't miss out. Well thankfully, YouTube offers a happy medium where you can get important notifications, but only get them once a day at your desired time.