We've seen many things get gummy-ized over the years—worms, insects, Coke bottles, glass cleaner, Legos, brains, Nutella, and even tiny LEDs—but nothing compares to YouTuber and WonderHowTo favorite Grant Thompson, aka The King of Random, who made one helluva creepy gummy chicken that's just as big as the real deal.

How to dice Onions ( easily and quickly)

Dan Perceval, founder of the sport of Xtreme Ice Skating explains us in the video of how to properly lace ice hockey skates. It starts with the wax laces. There are different forms but he suggests heavy wax since it lasts long. These wax laces are used to grip the boots. We normally we use 120 inch if there is no wrapping around and it should be in excess if you wrap around. Now we start with lacing. You can start outwards or inwards in hole one. He prefers outward so he inserts the lace outw...
First and foremost, let me once again apologize for that bug, which I failed to notice in time. Alright, alright... Enough sulking, oaktree. Get to it!
In this clip, you'll learn how to create a barebones password generation app with PHP. Whether you're new to the PHP: Hypertext Preprocessor scripting language or are a seasoned web developer merely looking to improve your chops, you're sure to find benefit in this free video programming lesson. For more information, including detailed, step-by-step instructions, take a look.

This wavy shell crochet pattern uses three colors to make the design look complex and random. Actually it's quite simple. There are only two rows in this wavy shell crochet pattern. One row alternates between a few standard stitches and half pinwheel shape. The second row is completely plain. Try out this crochet project to achieve satisfying results.

Watch this instructional video to learn how to do the double shock card trick in which you appear to make four random cards turn into four kings and then four aces. All you need is a standard deck of cards and a double sided card. This video has no audio, but it does have subtitles.

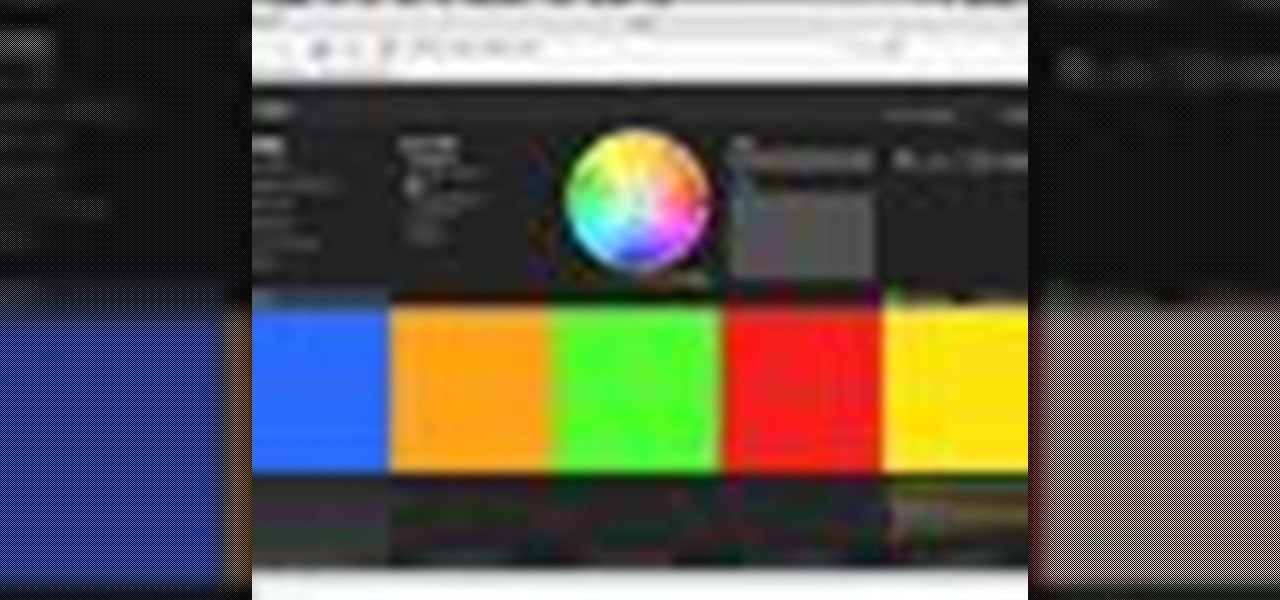
Kuler is a beta Adobe application at labs.adobe.com. It allows you to choose color schemes using rules or completely at random, then export the colors as an Adobe Swatch Exchange file for use in all of the Creative Suite applications. In this video tutorial you will learn how to create color schemes using Kuler.

Fable 3, like many modern 3rd person games it seems, has a Banjo Kazooie-like number of random collectibles for you to find to enjoy the entire game experience. One of these sets is Rare Books. There are a ton and tracking them down takes a long time, so watch this video to learn the locations of every Rare Book and how to unlock them.

These days, pennies are useless when it comes to buying things, and that's why Canada doesn't even have any anymore. But, there are a lot of cool things you can do with those worthless pennies, and what's better than a good old-fashioned prank?

The ukelele is a great little instrument that is easy to learn, sounds good, and is portable. How much better could it be? They work especially well for covering pop songs, since they're very simple and catchy, which is the essence of the ukelele. This video will teach you how to play the hit song "I Wanna Grow Old with You," made famous by Adam Sandler at the end of The Wedding Singer, on ukelele.

This is a extremely easy to follow tutorial which will allow you to learn to how to build a sugar cane farm.

Not two random broke girls, but the television show "Two Broke Girls". I think this show is hilarious, and I think Steampunk getting "dissed" by the show is sort of like a song getting parodied by Weird Al: it's a rite of passage for anyone who's famous.

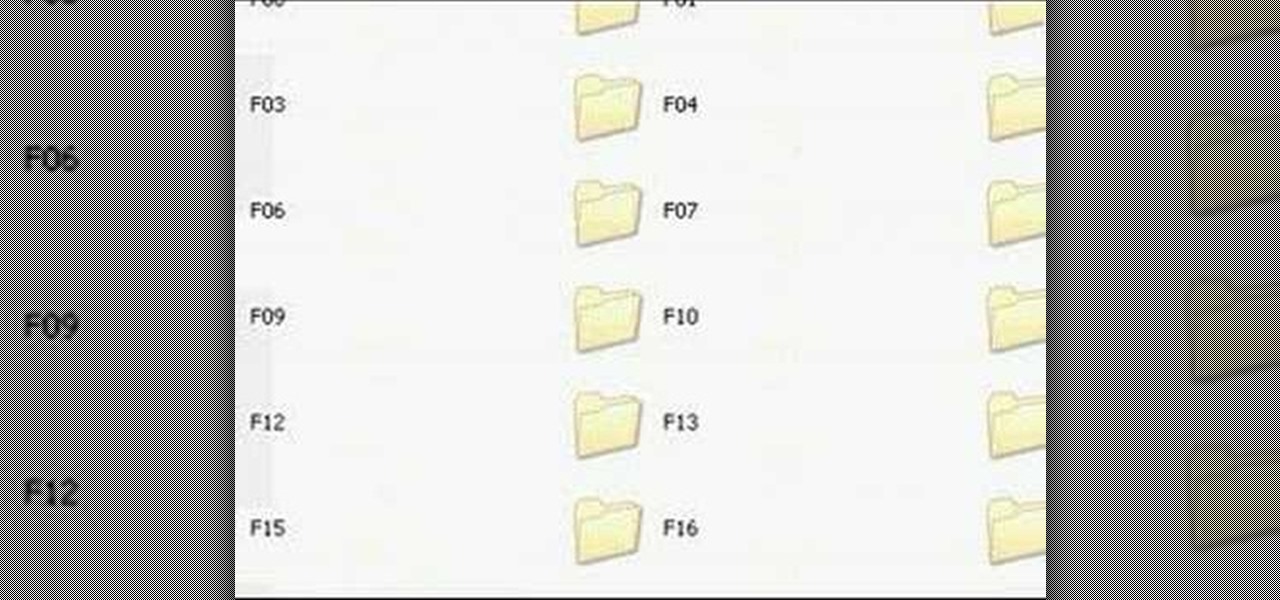
Using a Windows PC, our host shows us how to retrieve the music off of an iPod and copy it to our hard drive. First he opens the "My Computer" icon and selects the iPod, which is shown as a hard drive. There are a few folders shown, such as Calendar and Contacts, but no Music folder. We are shown how to reveal the hidden files on this drive. A new folder appears, called "iPod Control." Once this is opened, we can see the Music folder. Inside the Music folder are many folders labeled in a seem...

Sanding is an important step when preparing wood for painting or staining. You Will Need

While there's no denying that iPads are better when it comes to multitasking and productivity, your iPhone has a few tricks up its sleeve to rival even the best iPad features. One thing about iPadOS is that it's really easy to highlight editable text with gestures, but it's just as simple on iOS if you know all the secrets.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

With the holidays over, a lot of people with shiny new Google Homes are getting their first chance to explore the new Google Assistant. Before the Google Home's release, the Assistant was only available for the Google Pixel and Pixel XL, or in a text-based form with Google Allo—but now it's gone mainstream.

If you've ever noticed, even just for a fleeting moment, that the auto brightness on your Nexus 5 seemed to "glitch out"—you are not alone.

When it comes to clubbing makeup, the crazier the better. Because clubs tend to have very dim lighting (and lots of girls dressed to the nines hoping to impress), your ordinary nudes and natural makeup simply won't show up.

The Running Man was everywhere in the 1990's, and we do mean everywhere. From Will Smith to random kids on the street trying to look cool, the move was popularized by the likes of MC Hammer and Vanilla Ice.

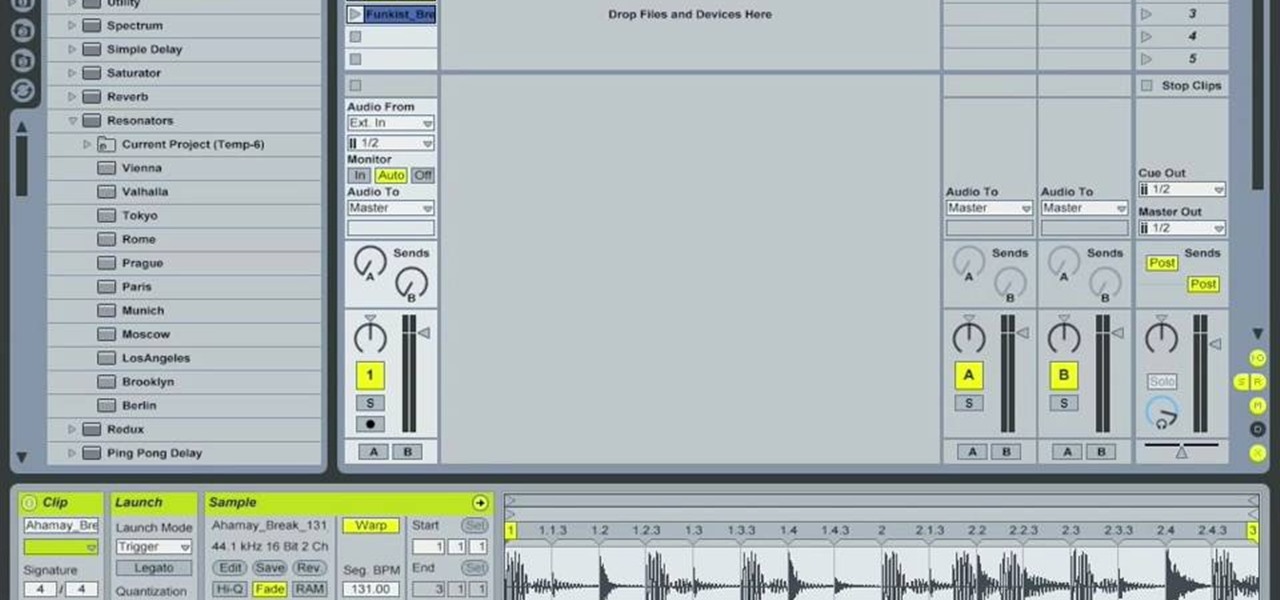
In Ableton, you can set follow actions to tell clips to do something on a timed basis. The time can be immediate or random, but it is automated. This is more efficient than doing the follow actions manually. Go to clip view, type "L". This launches the settings which gives the space of time in which the follow action happens. You can set more than one follow action. You can determine when and how often the action will take place. You can determine when the clips occur automatically. The clips...

It's flattering enough to be complemented on your pretty bag. So how awesome would it be to get compliments on a bag you made yourself? Not many people endeavor to craft a homemade bag (for fear of loose ends, things falling out of random holes, etc.), even though it's actually pretty easy.

In this tutorial, we learn how to use salty hashes to keep passwords secure. A hash is stored in a database that is hashed with an algorithm, so not everyone can see exactly what your password is. When you type your password into a website, it doesn't actually register as words, it registers as a hash. This keeps your passwords secure so not everyone can see them. Salting is when you use random pits and attaching them to your regular hashes so not every password is the same. The salt is what ...

This video is about how to create colorful leopard print nails. So the first thing that you will have to do is to choose any colors of the nail polish that you want. After deciding for the first color of the nail polish, apply it to your nails and let it dry. The next step is to get a plastic plate and place a bit of a small amount of the second color that you chose. With the use of the nail art brush, carefully start forming small random spots on the nail. Apply these to the rest of your nai...

Here we learn how to insert secret symbols from your keyboard onto Facebook or any other regular program. This only works on PCs, sorry Mac users! By holding down the alt key and pressing numbers on the keypad from 1-9 and beyond, we discover there are many different symbols that pop up. There are smiley faces, arrows, numbers, punctuation marks, and various other random symbols. Exploring these on your own is simple and will show you everything there is to choose from. You can get creative w...

First wet your hair with styling cream. Take the upper part of your hair, right above your ears and clip it. Take a small section of the bottom hair layer and twist it. Clip the twisted hair with the hair curler and spin it till the root. The curler will be finished in 30 seconds. Repeat the previous three steps with all the bottom hair layer. When finished with the bottom, take another small layer of the upper clipped hair and repeat the steps but without twisting the hair. Put spray regular...

Finding all of the rare trade objects in Assassin's Creed: Brotherhood can be infuriating, what with random item drops and quests to juggle. Watch this video for a guide to farming trade objects by killing bandits along a particular route.

In this video, we learn how to use secure online passwords. There are a ton of things to consider when creating a password. A weak password is something that someone can easily guess. If you are using a birthday, common dictionary word, child's name, or something common then you are at risk. Your password should combine letters and numbers, and be at least eight characters long. It should also be completely random and have upper and lower case letters. You can use a password assistant if you ...

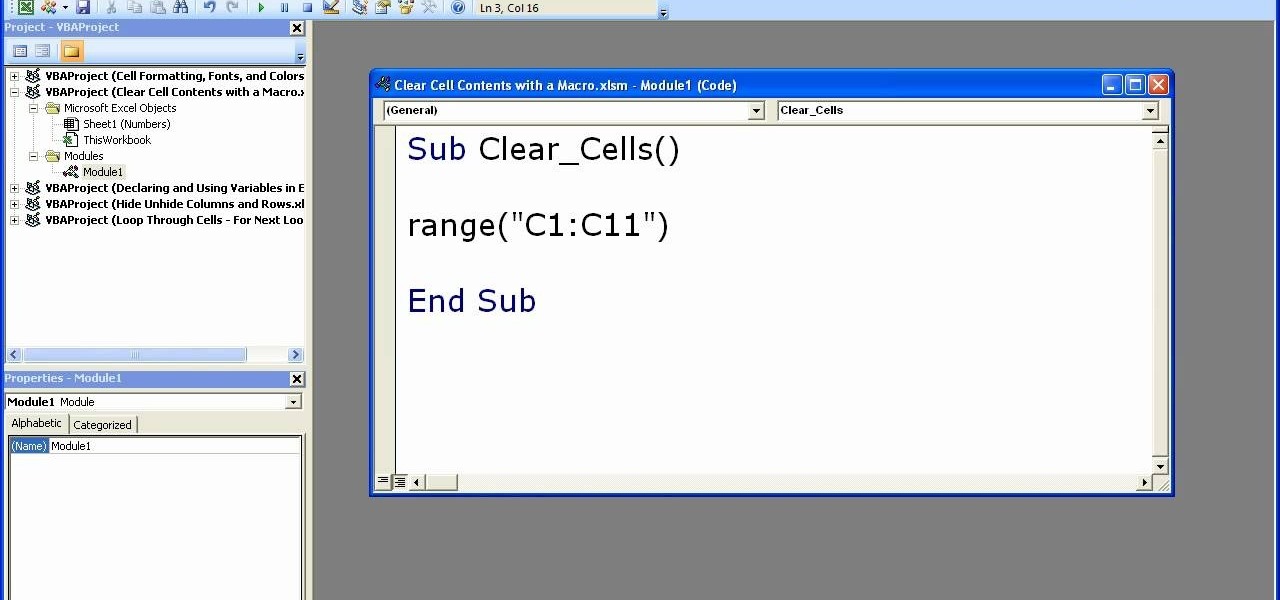
In order to clear the cell content in Excel, using a macro, you will first need to have a table. If you don't already have a spreadsheet, you will need to create one with random numbers. Next, highlight some numbers, by clicking one box and dragging in order to select a number of boxes. Click Alt + F11.

Don't want to throw away that raggedy pair of old Levi's with small paint stains and random tears all over because it's stuck with you longer than your trusty 12-year-old jack russell terrier? We totally understand. Continue to use your favorite pair of blue jeans by watching this video.

Check out this tutorial for a cool magic trick that you can easily perform for your friends. All this trick requires is a little preparation and you will be wowing crowds in the bar in no time.

Navigating on your HP TouchSmart 3.0 PC is easy, fun and takes nothing more then your fingers. To click, simply create a single point of precise contact between your finger and the screen. The HP TouchSmart uses optics to determine clicks so avoid leaning on it with your hands, knuckles, large jewelry or the random fly. The screen is not pressure sensitive so pressing harder has no effect. To right click you simply press and hold. For tasks that require multi-touch input use more than one fin...

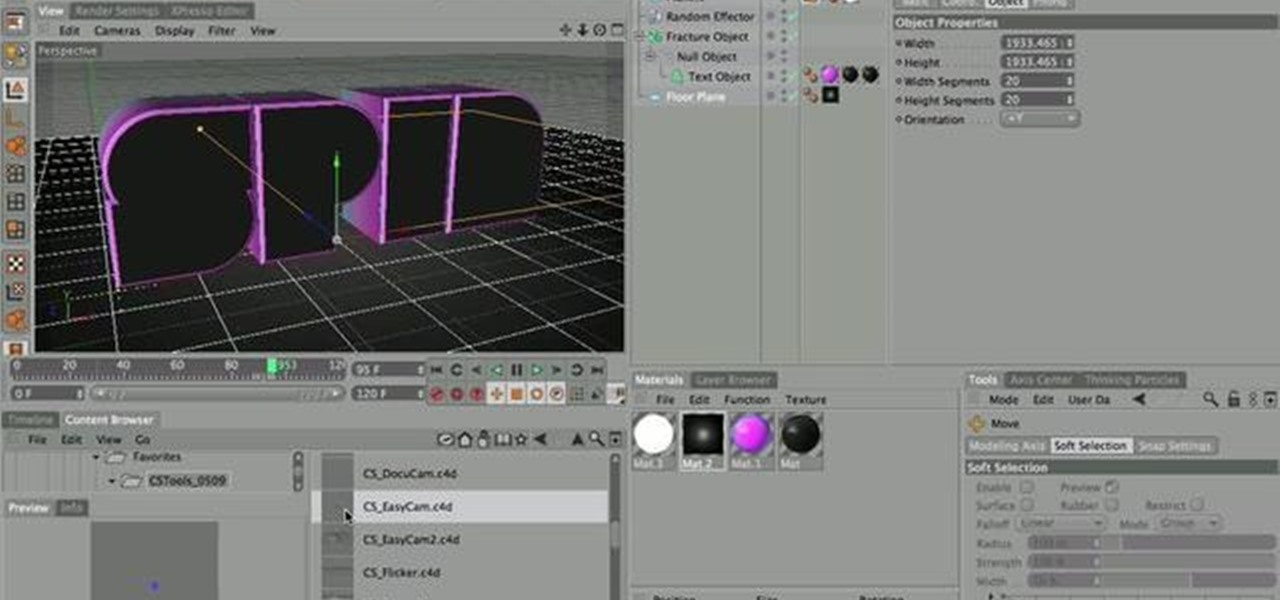
Nick from Greyscale Gorilla demonstrates how to create a very simple spinning logo animation. Using Cinema 4D, Mograph, and Random Effecter, Nick combines different textures and camera angles for a rich, slick finished product.

For anyone interested in learning a new jewelry technique, this video tutorial shows how to crochet a bead rope necklace. You can use large pony beads like the video tutorial, or use much smaller beads. The pony beads are suggested for beginners so that you can see what you are doing. To begin, thread all of the beads you will use onto your yarn. You can alternate colors or place them onto the string at random. Both techniques will yield two different effects. Begin with six chains slip stitc...

This video shows how to paint Piet Mondrian inspired block print nails yourself. Apply a white base coat and top coat. Use black nail art paint because of the thin brush. Paint two black lines the length of your nails. Then paint black lines going across the width of the nails to make random size boxes. Dab the color of paint you are going to use on a piece of paper and use the nail art brush to get the paint off of the paper and apply the different color paint to the boxes. Wait about 10 min...

Create a bootable USB flash drive to keep an extra OS of Windows or Ubuntu. You always want to have a copy of your Linux or Windows operating system on a separate device other than your computer. Because even if your computer or laptop is relatively new, it's very easy for some random fluke - an internal error or virus - to completely shut you down when you least expect it.

Net neutrality is dead and your internet service providers can collect all the data they want. While VPNs are a great way to protect some of that privacy, they're not perfect. There is another option, though, called Noisy, which was created by Itay Hury. It floods your ISP with so much random HTTP/DNS noise that your data is useless to anyone even if they do get it.

Passwords are everywhere. We use them to unlock phones, computers, websites, encrypted disks, encrypted files... the list just goes on and on. Savvy users will already have a password manager of some sort that can generate a very strong password on a per site basis. However, these password managers also require a password. Not only that, it has to be something memorable.

Hello people again, I wrote my last post about crypto about 10 months ago, now I will introduce something not fresh for the science, but fresh for the people who wants to learn. In my http://null-byte.wonderhowto.com/forum/cryptography-0161538/ post of crypto concepts, there is just basics, today we will see something that targets wide concepts like Symmetric crypto, Public Key Cryptography, Hashing, Keys etc...