André Broessel of rawlemon has developed a solar energy generator that can use both sun and moonlight to create usable power. Oh... and it's gorgeous. The device is essentially a huge glass sphere filled with water that uses a ball lens to refract light in a way that increases energy efficiency by 35 percent. It's completely weatherproof and has an optical tracking device, meaning that it can be incorporated into architecture. Here's a concept design of how it could be used to power buildings...

Taco Bell's in the news for umpteenth time, and today the controversy is over their infamous beef taco meat. Gizmodo leaked a picture of Taco Bell's "Taco Meat Filling" and surprise, surprise— it's missing a lot of the "meat" that it claims in its advertisements. Taco Meat Filling Ingredients

Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website was viewed. There's no doubt Coinhive, an innovative mining method, is being abused and exploited by hackers in the wild.

So your friend started humming "Who Let the Dogs Out" and now you CAN'T get it out of your head. Oh yes you can! This helpful little video shows you what unhearit.com can do for you. This website generates random catchy tunes, so you can dump what's in your head and move on to something fresh. Here comes Lady Gaga!

Justin Heimberg demonstrates a few of the best ways to prank people using your cell phone. Watch this how-to video to baffle random passersby using only your cell, especially if you have headphones and look like you are talking into space! Use this as inspiration for one of your April Fools Day pranks!

Check out this video to see how to draw a head by building it out of random organic shapes.

Cross-site scripting is one of the most common vulnerabilities found on the web today, with repercussions of this type of flaw ranging from harmless defacement to sensitive data exposure. Probing for XSS can be tedious and time-consuming for an attacker, but luckily there are tools available to make things a little easier, including Burp Suite, Wfuzz, and XSStrike.

We spend over 30 percent of our lifetimes sleeping—yet it never seems like enough, does it? Distractions ranging from work issues to personal relationships keep our minds racing well after they should be shutting down for the night, and the onset of smartphones has only added to this problem with the instant information and easy entertainment that they offer.

Welcome back, my nascent hackers! In the conclusion of the Mr. Robot television series, Elliot and fsociety successfully completed their mission of encrypting all of Evil Corp's data with AES-128 encryption and destroying the key.

From amateurs to professionals, DSLR cameras are the standard weapon of choice for most photographers. If you own one, then you probably know how expensive of a hobby photography can be. A good starter camera can run between $400 and $500. Then there are accessories like tripods, lenses, filters, and memory cards that can slowly empty out your wallet.

Not everything at the dollar store is a bargain, or even safe to use. Learn to spot the difference between an item that's cheap, and a cheap item.

Abstract art may seem random but it often utilizes basic art and design theories. Learn more about making an abstract painting in this free art lesson from an art instructor.

Correctly identifying the underlying technologies that run on a website gives pentesters a considerable advantage when preparing an attack. Whether you're testing out the defenses of a large corporation or playing the latest CTF, figuring out what technologies a site uses is a crucial pen-tester skill.

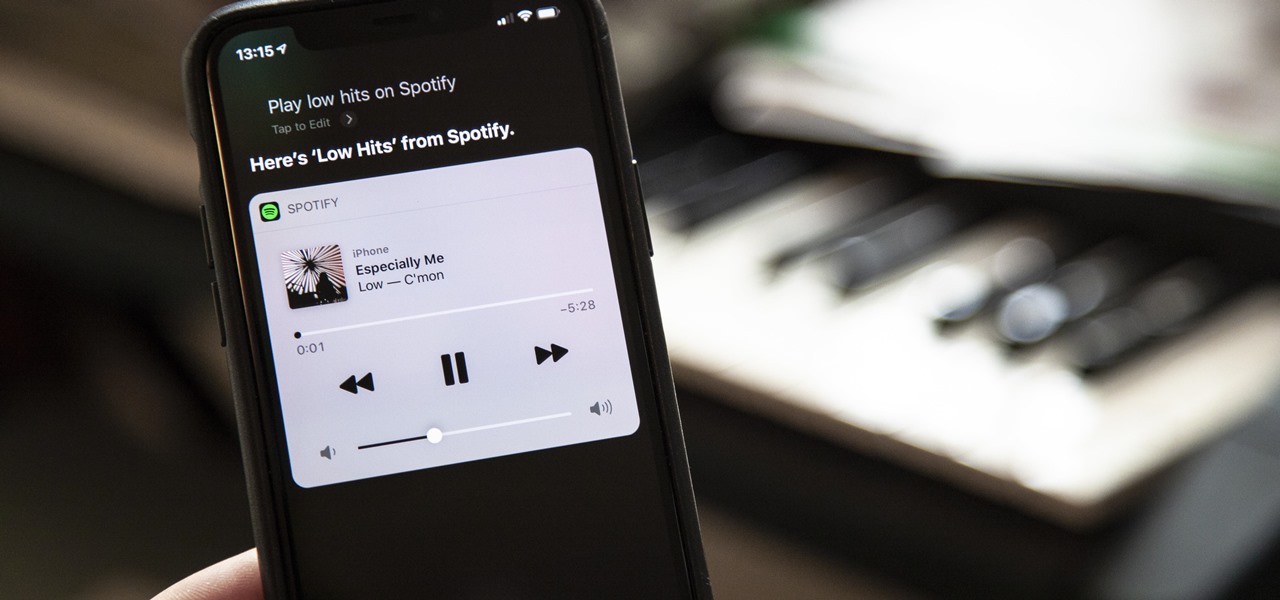
Finally, Spotify now works with Siri! It's been a long time coming, but as of Spotify Music version 8.5.6 for iOS 13, you can make Siri or Hey Siri on your iPhone play and control music in your Spotify account. But what commands can you use? We've built a list of everything you can tell Siri to do on Spotify right now, and as time goes on, the list may grow even more powerful.

Ever since the introduction of Google's SafetyNet feature, it's been an ongoing battle with apps trying to detect root access. For a while, there was a lot of back and forth between Magisk and certain apps. Pokémon GO was a high profile example of an app aggressively checking for anything related to root. Luckily, Magisk has made great strides to keep apps from detecting root for good.

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.

Since starting as a simple messenger with self-destructing pictures, Snapchat has grown into a full-fledged social media platform. As features were added, new permissions were requested, and we're all probably guilty of just tapping "OK" to try out the latest and greatest. But at some point, it's a good idea to review your settings to see what personal data you're putting out there for all to see.

As expected, Apple began pushing out the final version of iOS 11.2.5 to all iPads, iPhone, and iPod touches today after 41 days of beta testing. Highlights include a fix for the ChaiOS vulnerability, a persistent Now Playing bar in Music, and some signs of AirPlay 2 just in time for the HomePod launch on Feb. 9.

before I move on to more exciting areas in this series, I want to also point out some things to protect your information & how to not get DoXed.

Hello again, reader! In this post, we are going to cover some data types and how to declare variables. It shouldn't be too hard so just sit back, relax, grab some popcorn and enjoy the ride (while you still can!).

welcome back my masters , teachers and classmates , in this second part of this 0-day series we will learn the basic of fuzzing, and i bought some gift for nullbyte(a 0 day vuln that will be released today exclusively on null-byte) .

In recent weeks, major bank websites around the world have experienced outages after being have been hit with Distributed Denial of Service (DDoS) attacks. Although few, if any, of these banks have been totally knocked offline, these DoS attacks have dramatically slowed the response time of their websites to legitimate customers. The most recent victim was the Royal Bank of Scotland. Due to this attack, RBS customers were unable to access their accounts for about an hour last week.

Mirror, mirror on the wall, who is the fairest of them all? Besides being one of the most notorious misquotes of all time (the line is "Magic Mirror on the wall, who is the fairest of them all"), it's a question that men and women probably have asked themselves more than once.

WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the communities. But don't wait—start submitting your own projects to the most appropriate World now!

WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the communities. But don't wait—start submitting your own projects to the most appropriate World now!

WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the communities.

Last week, we rolled out a major site-wide update on WonderHowTo, making it even easier to follow the subjects you're passionate about—and easier to share your creations with people who'll give you the kudos you deserve!

In today's world of social media, there's really only two powerhouses—Facebook and Twitter. And those of you with Twitter accounts know the power of a Tweet. Getting more followers means reaching more people, but the vast majority of Tweeters are following only a handful of Twitterers themselves. Do you ever wonder why them? What's so special about these selected followed users? Is it worth it to follow them, too? That's up to you, but if you're searching for more people to follow, then it's ...

If you're interested in nabbing superhero memory strength, the secret behind training your brain is not necessarily what you might expect. Your standard G-rated brain strengthening exercises range from crossword puzzles to Sudoku to calculating fairly simple math problems to improve short term memory, but the real clincher used by some of the pros is essentially... porn. Yep, you read right.

This video will teach you how to increase your PC's virtual memory. Or in other terms, the Random Access Memory space to be used when doing something with your computer. 1. Press CTRL+ALT+DEL. Go to Performance tab. 2. Check the Commit Charge which is also the amount of virtual memory used. 3. Right-click the My Computer shortcut on your desktop. 4. Go to Advanced tab. 5. On the Performance box, click Settings button. 6. Click the Advanced tab. 7. At Virtual Memory box, click Change button. 8...

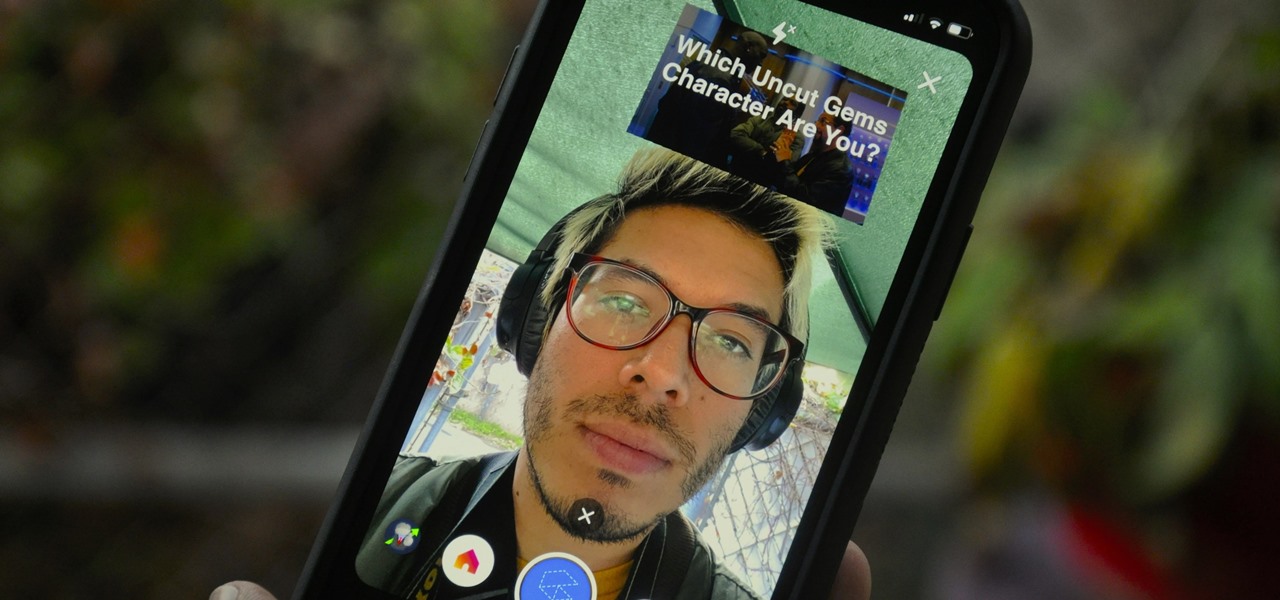
There's a new trend on Instagram Stories: People are making viral AR filters where images of popular characters from TV shows, movies, and other mediums shuffle above your head until one sticks. The filters range from Disney and Pokémon characters to Harry Potter and Friends, but you're not limited to just that because you can create your own "which are you?" filter.

The HoloLens 2 hasn't even reached most of the market, but it's already a big-time TV star. Microsoft's augmented reality device made its primetime debut on FOX TV last night on an episode of the hospital drama The Resident.

"Why do I keep getting popups on my phone when I'm not even doing anything?" I see this question asked all the time. The answer? You have a shady app on your phone and it started showing full screen ads. But people either don't know this (so they don't know they just need to find and uninstall the problematic app), or if they do know it's a bad app, they don't know which app is causing it.

Apple Card, Apple's foray into credit cards, is to be released this summer. There's no exact date set yet for when you can apply for one or when iOS will support it, but it's getting close. Apple just released iOS 12.4 developer and public beta 7, meaning we're almost there since iOS 12.4 is mainly intended to add Apple Card support for iPhone.

Apple's upcoming iOS 12.4 isn't the company's most exciting release on its surface, given iOS 13's impending fall unveiling. However, anyone interested in Apple's in-the-works credit card, Apple Card, will need iOS 12.4 on their iPhone to use the card, and that day seems to be getting closer. The sixth beta for iOS 12.4 was just released today, July 9, for both developers and public software testers.

Right now, Apple is testing two versions of iOS. On the one hand, you have iOS 13, buggy but feature-filled. On the other, iOS 12.4. The latter just got an update to the fifth developer and public beta versions, 13 days after the release of iOS 12.4 developer beta 4.

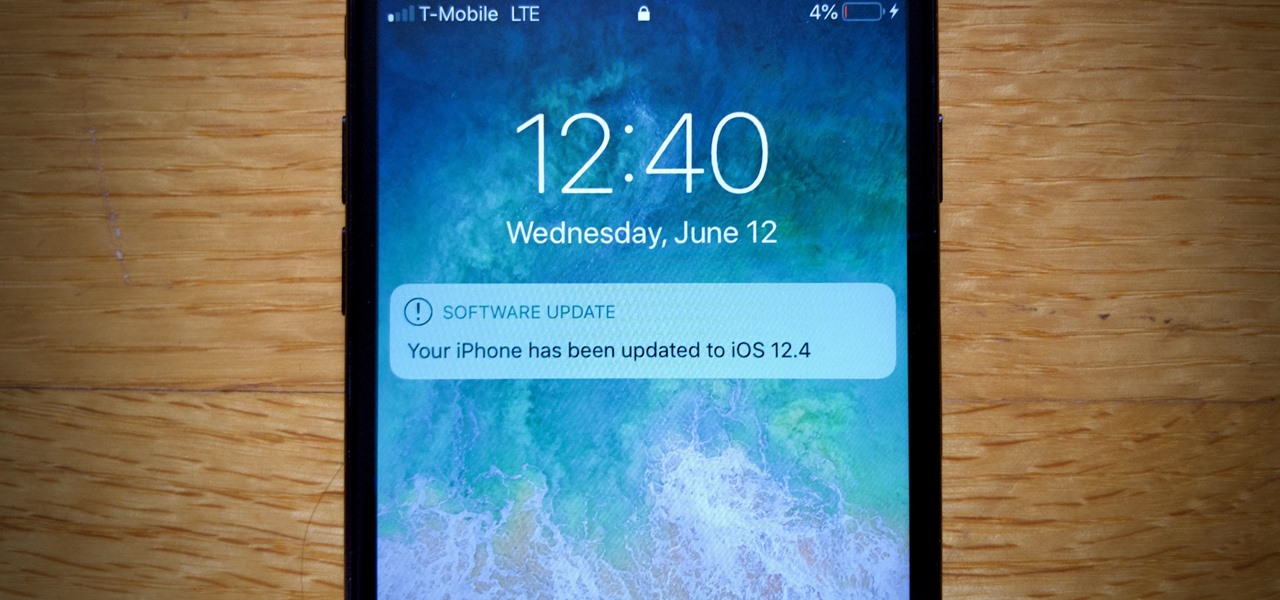
While iOS 13 is not ready for public beta testers just yet, Apple is still testing iOS 12.4 out, and you can install that right now on your iPhone. The latest version, iOS 12.4 public beta 4, was released June 12, a day after its developer version.

With iOS 13's developer beta in full swing, it can be easy to forget that there's an entirely separate iOS beta cycle still running right now. Yes, iOS 12.4 is still in beta, and unlike iOS 13, it's available to the public for testing.

Imagine being able to play a video instantly on hundreds of thousands of devices across the globe. It's totally possible, as long as all of those devices have a Chromecast plugged in. When Chromecasts are left exposed to the internet, hackers can use add them to a botnet that can play YouTube videos at will. The "attack" is made even easier thanks to a simple Python program called CrashCast.

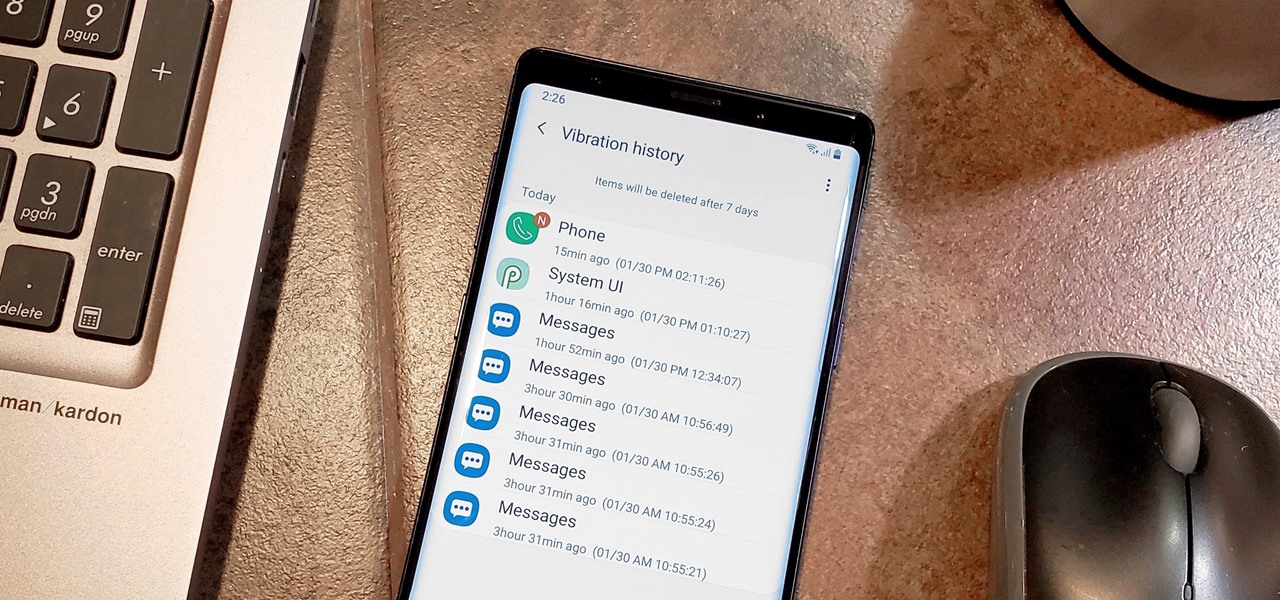
Random vibrations, ghost buzzing — whatever you call it, when your phone goes off for seemingly no reason, it's pretty frustrating. Finding the source of a phantom vibration can be almost impossible if there's no associated notification, especially given the myriad apps and system processes that run on your Galaxy device.