Netflix has received a lot of publicity lately, and not because of its impressive worldwide library. From blog wars with Comcast to streaming deals with Verizon, it's easy to forget that the company exists for our entertainment, but sometimes that entertainment has drawbacks.

A boring work meeting. A conversation with someone you don't like. A date that's going horribly. A run-in with an aggressive and intimidating stranger. These are all situations where you want to flee—and fast.

While it may be impolite to play around on a smartphone at dinner, having it consume my attention while I'm on a deadline or trying to study can prove disastrous. With Netflix and social media just a tap away, it's a dangerous game of wills, one that the phone usually wins.

Earlier this morning, Twitter announced (through a tweet, naturally) that it has acquired Cover, roughly a minute after Cover made the same announcement. Cover Lock Screen, a lockscreen replacement app, has been vastly popular during its first year. The app places relevant shortcuts on your lockscreen that adapt to your habits, so whether you're at home, work, or in the car, you'll find the apps you use the most in these situations readily available for you. For more information on Cover, inc...
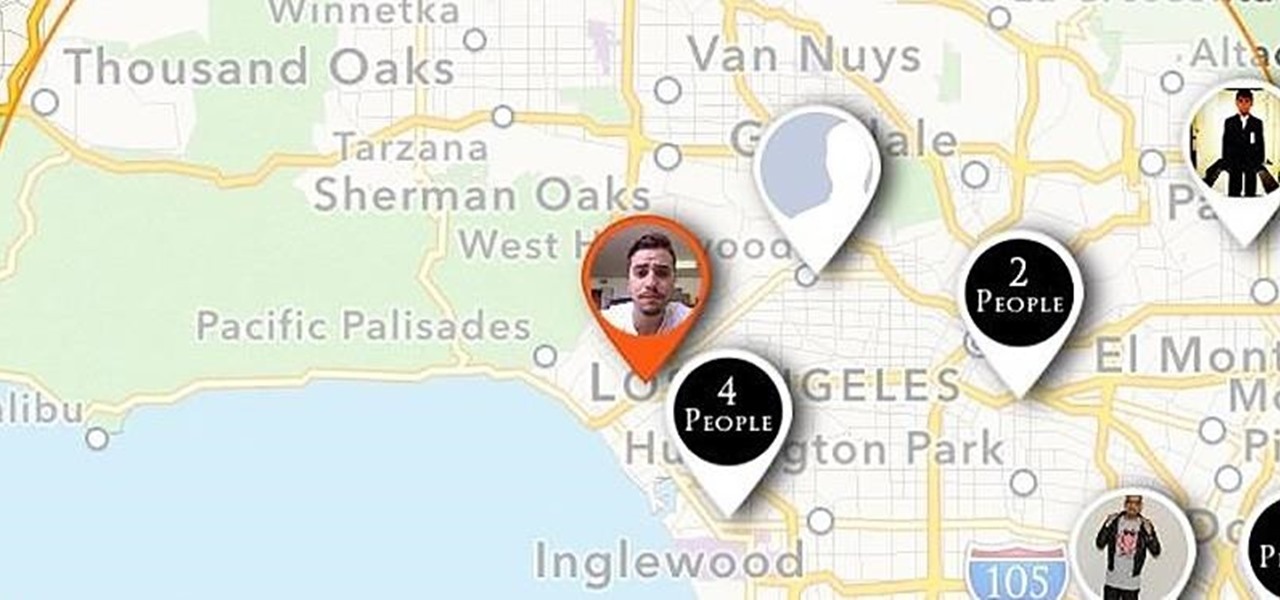
Imagine that Tinder fornicated with Facebook and had a baby. The product of that union would be the hideous, yet overwhelmingly interesting SocialRadar, an app dedicated to stalkers and stalkees.

I don't know many meat eaters who don't appreciate a good burger, but unless you eat it plain, it usually gets pretty messy. Toppings falling off and sauce running down your arms seems like it's all just part of the process.

Whether you're on the john or sitting quietly on the bus to work, there's always time for a little video. And thanks to my favorite high school procrastination site, I'm going to be turning that little into a lot.

When we take pictures with our smartphones, it’s safe to assume we’re taking more than one. We're either trying to capture the right light, look, or expression… or maybe a slight nod to the right to show off your good side.

We have shown you how to get CyanogenMod on your HTC One and Samsung Galaxy S3 in only a matter of minutes. But when modding your phone by installing custom ROMs, you'll often lose your access to Google Apps. Since Google's Apps are very useful (Gmail, Chrome, and Maps to name a few) most people will prefer to have these apps on their custom ROMs. While you can scour the internet searching for individual .APKs, it's hard to find the correct versions to work with your particular system (and do...

Change is something everyone needs every now and then. President Obama used it as his campaign slogan and adult movie stars use it to hide their real identifies. Change is in itself versatile. You never want to have the same thing day in and day out, and that's why us Android users appreciate the massive amount of customization available.

Welcome to this short and easy tutorial on hacking and DDosing (is that even a word I don't know) anyways lets get started

One of the first things most people ask for when staying with a friend is the password to the Wi-Fi network. Even if you trust your friends to the end of the earth, a super secure password can be a pain to share with them, especially if it's just a bunch of random characters.

We all know about PRISM. The Surveillance Program allowing the U.S Government to access private user information. Such as, Google Searches, Tweets, Facebook Posts, Private Images, and other private user data. "Hiding" yourself can be very difficult, but it is possible. I'm here to show you How to Become Anonymous & Browse the Internet Safely.

Rooting your Samsung Galaxy S4 has many advantages; theming, free wireless hotspots, deleting system apps, and generally being ahead of the curve when it comes to updates. It's also great for simple things like centering your clock or freezing apps.

Most of you probably have a set of blinds at home, the most popular being horizontal or vertical. They're great for keeping the sun out of your eyes and maintaining privacy, but unfortunately, each comes with its own set of problems.

Even though I am not cool enough to use Instagram on a daily basis, I still try to stay in the loop. I did take photography in high school, so I know a thing or two about picture taking. I just can't seem to find the motivation to take a picture of random crap during my daily routine, but I guess that's why I'm Instalame.

The first alarm clock in recorded history can be traced back to ancient Greek philosopher Plato, known for laying the foundations of Western philosophy and science. Plato was said to possess a very large water clock with an alarm signal similar to that of a water organ.

We share links on an almost daily basis, usually not even thinking twice about it. Whether you're sending a funny cat video to your sister, or letting your coworker know where to go to download relevant files, there are plenty of reasons you might be giving someone a URL.

In college, I enjoyed eating, sleeping and making my roommate's life a living hell. My most satisfying prank involved 500 red cups stapled together, filled with water, and strewn across his bedroom floor. He was not happy. To clean up, he had to unstaple each cup, carry it to the bathroom, and dump the water. He was furious, but I was okay with sacrificing our friendship in exchange for a fantastic story that I'll probably tell my grandkids one day. If you're not as cruel as me, there are oth...

If you've ever logged on to the popular music application Pandora, your password is saved onto that computer in the local storage...for good.

Earlier this week, Spiderlabs' vulnerability researcher Jonathan Claudius discovered a key in Windows 7 and 8 registries that makes it easy for anyone with physical or remote access to a computer get a hold of the user's password hints. When the "UserPasswordHint" key is read, the hints are displayed as a code that looks encrypted, but Claudius noticed a pattern of zeroes that could be easily translated back to plain text with a decoder he made in Ruby. He added this functionality to the Meta...

In this video, we learn how to perform a mind reading trick with Brian Brushwood. First, grab some random change out of your pocket and tell the other person to turn over any coin the choose. Then ask them to turn over two more. Now tell the person to pick a coin and slide it towards them and pay attention if it's heads or tails, then cover it up. Now tell the person to say "heads/tails" and tell them which one it is, depending on if the person leads forward. You can easily accomplish this by...

Apps can learn a lot about you just by reading information about your smartphone. They can easily track what device model you have, your phone number, and in some cases, your hardware MAC addresses. Many third-party apps will only track your device values for advertising purposes, but some might be trying to snoop on your data for ill intentions.

Greetings my fellow hackers, In the previous article, I discussed briefly about ransomwares and their devastating capabilities. Devastating in a way that ransomwares are not only known to encrypt files but to also lockout some specific functions of the system and hold it up for a ransom.

Welcome to Minecraft World! Check out our tutorials, post to the Inspiration board, and come play on our free server! HELLO, FELLOW MINECRAFTERS. Pmaguire here, bringing you my favorite idea for a competition so far! I hope that you will come to love it as much as I do! Well, starting off, as the title states, this week's Redstone Competition will be PvP Arenas! Except, not just ones where you physically fight. You have to have traps, things that make it hard to fight, and various ideas using...

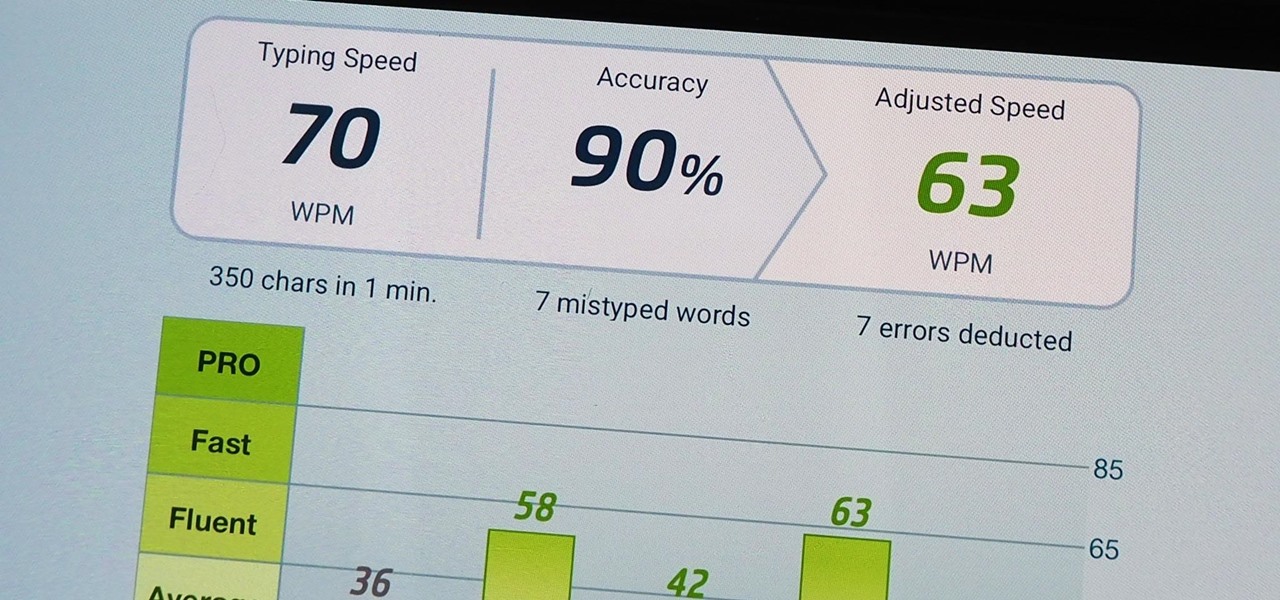
We use our smartphones every single day. They're a part of our daily routine, and as a result, we've gotten really good at using them — especially when it comes to typing very quickly. But just how fast can you type on your iPhone? Can you match your speed on a physical keyboard for your computer or tablet? You might just surprise yourself.

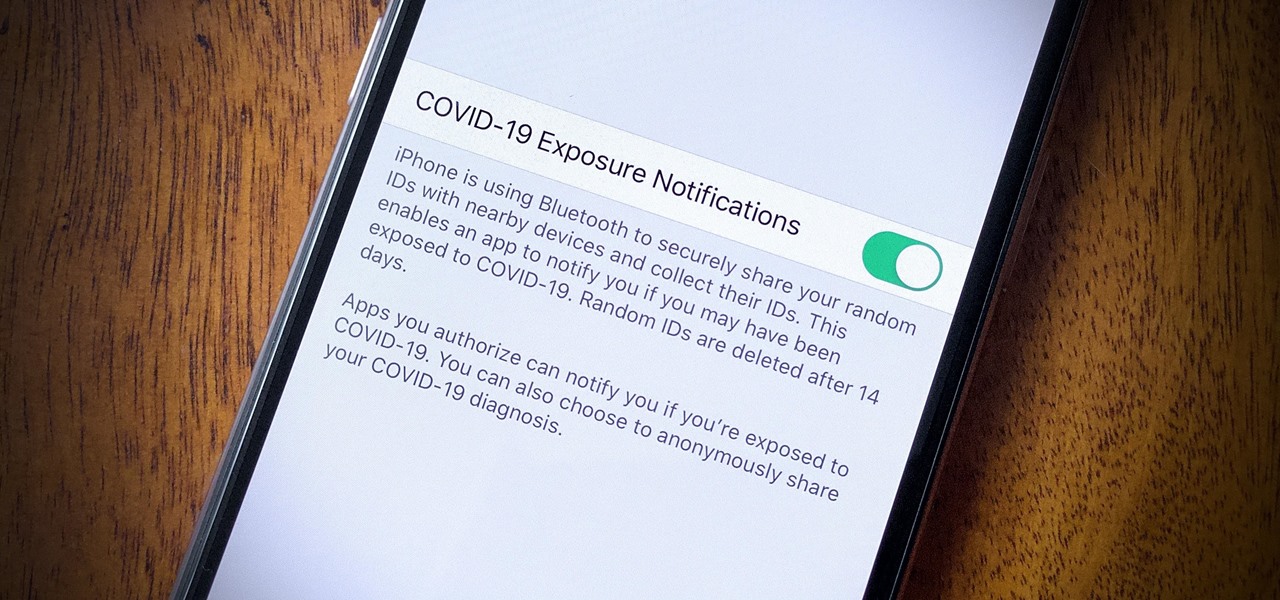
In iOS 13.5 and later, developers can create and release contact tracing apps for iPhone, which could help slow the spread of the novel coronavirus in the U.S. With these apps comes COVID-19 exposure notifications, which you may or may not want to receive. If you don't want to get these alerts, you can disable them.

The idea of a world without passwords used to be a pipe dream. But as we inch closer to making that a reality, we have services now that securely store all of our passwords under a single master password. It's a convenient way to keep our accounts safe and sound without having to remember all of their credentials. And there's no reason to be afraid — I'll explain why.

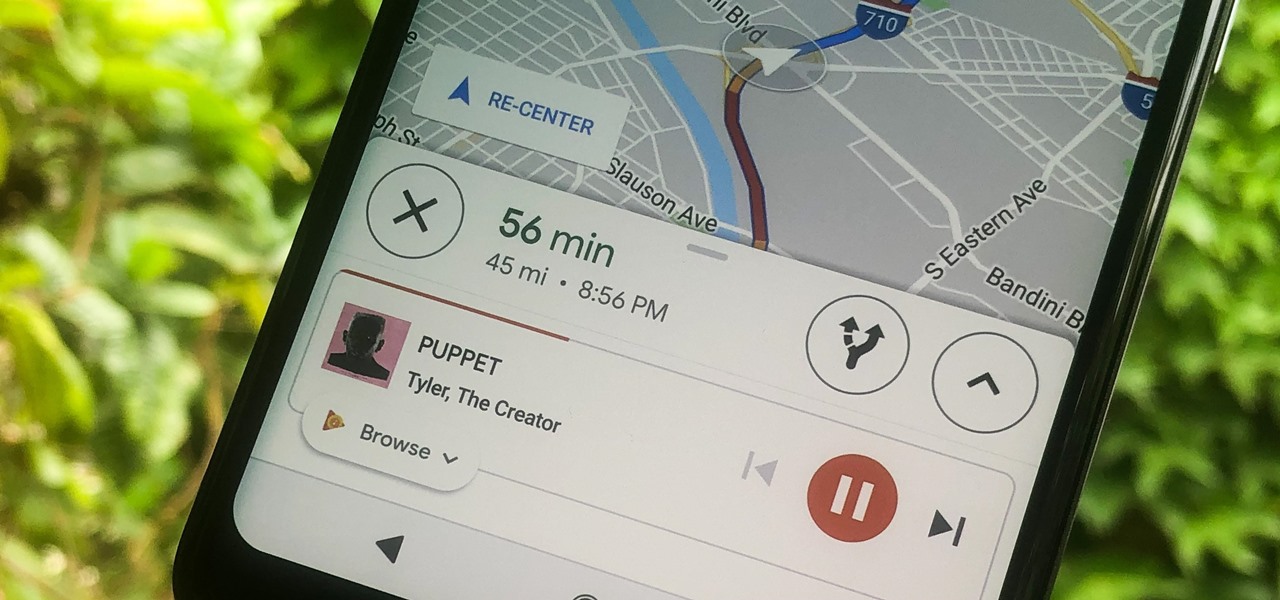
Staying alert to directions and changing the music you're listening to on your smartphone at the same time can be cumbersome, but Google Maps wants to fix that. One of the mapping service's features allows you to control music playing on Spotify, Apple Music, and Google Play Music from inside of Google Maps — while you're navigating in the car, on public transport, or even on your bike.

Stumbling upon a specifically tailored advertisement on your iPhone can be a bit disconcerting. But that's what happens when you let advertisers track your data. Some of you may appreciate more relevant ads in apps, but the rest of you might consider it a straight-up privacy invasion.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

Now that we've learned about keeping all our data safe with encryption, it's time to continue progressing through getting your Mac set up for hacking.

In this tutorial I will be explaining the purpose of unique encryption/decryption scripts ( I will be referring to these at "UEDS" for this tutorial). Then, I will show you how to make one. Finally I will talk about the downsides to the method I use. I will also provide links explaining the concepts and algorithms used in encryption to anyone who wants to see what is going on under the hood.

In most cases, when the free trial of software is over, that's it—you're left to either pay for it or find an alternative. But what happens if the trial wasn't long enough to sell you on the product? It'd be nice if there was a way to test it out again without having to whip out your credit card.

Cryptography is the science of keeping secrets, or more specifically, the science of disguising them. As a point of fact, cryptography has progressed quite a bit farther and now encompasses file and message integrity, sender authentication, and pseudo-random number generators.

TouchDevelop is a browser-based programming tool that allows anyone to build your own Windows 8 apps directly from any touchscreen device, including iPad, iPhone, Windows Phone, Android, PC and Macs. Once the script is created and the app proves to work, it can be placed in the Windows Store for free or purchase.

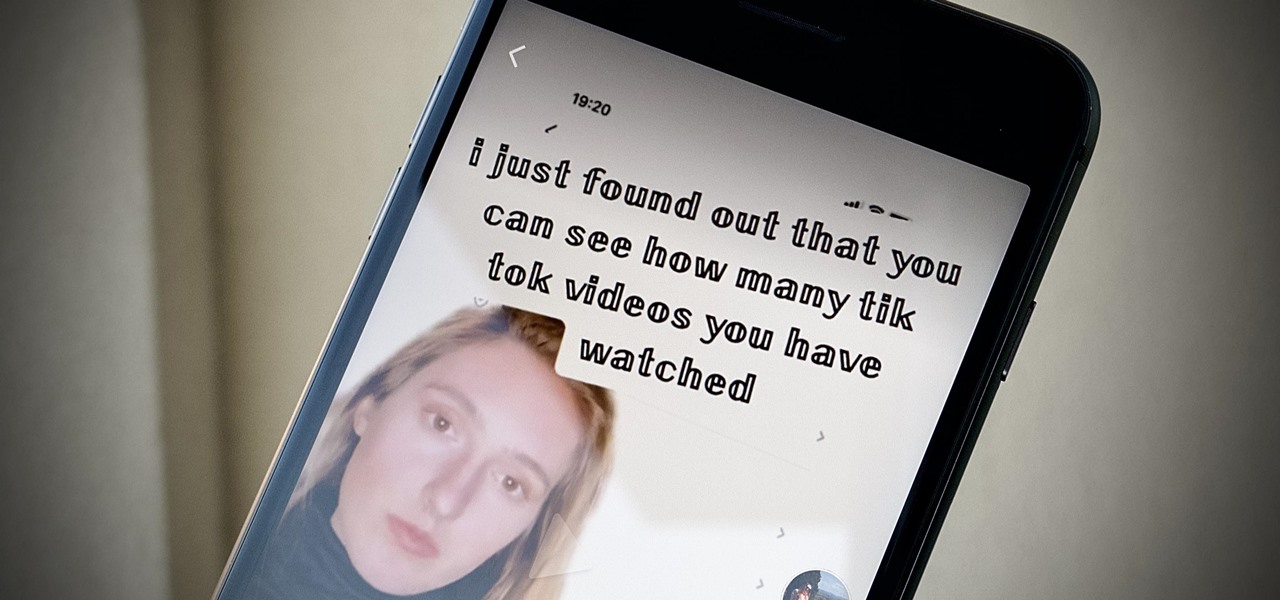
If you're as addicted to TikTok as much as I am, you probably heard about the app's alleged, hidden views counter, which can show you how many TikToks you've watched on your account. Most people who look at their counters are horrified to see that they've watched hundreds of millions of TikToks so far. Can that be right?

One Instagram creator's augmented reality homage to Disney's deep bench of animated characters has earned him fifteen minutes of fame.

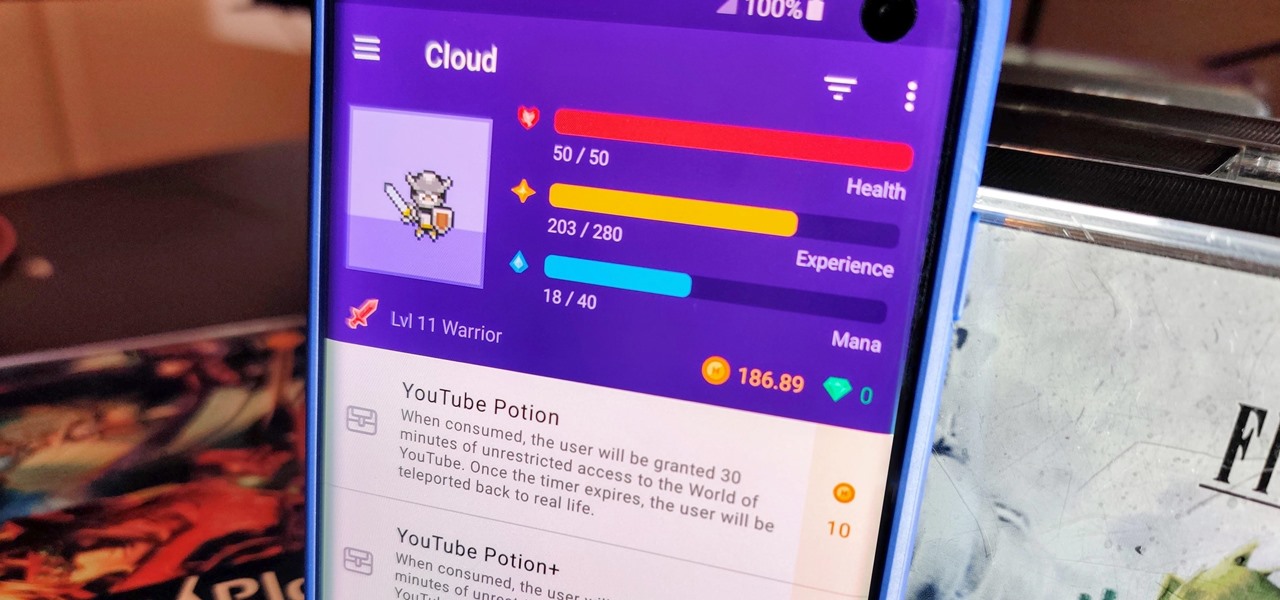
When you think about it, isn't life just one big open-world RPG just begging to be conquered? We all have a set number of specific tasks or chores we must complete every single day like clockwork. Sometimes, these items on our to-do list can become tedious and cause us to lose motivation. What if you could take those tasks and turn them into something awesome instead? Now you can.

I was today years old when I first heard of Bhad Bhabie, but I'm told she is apparently a rapper with a rags-to-riches story.