If you've ever tried to record a Snapchat video of a song playing in your car, you know that it's impossible to do if the song is playing on the same device that you're Snapchatting with.
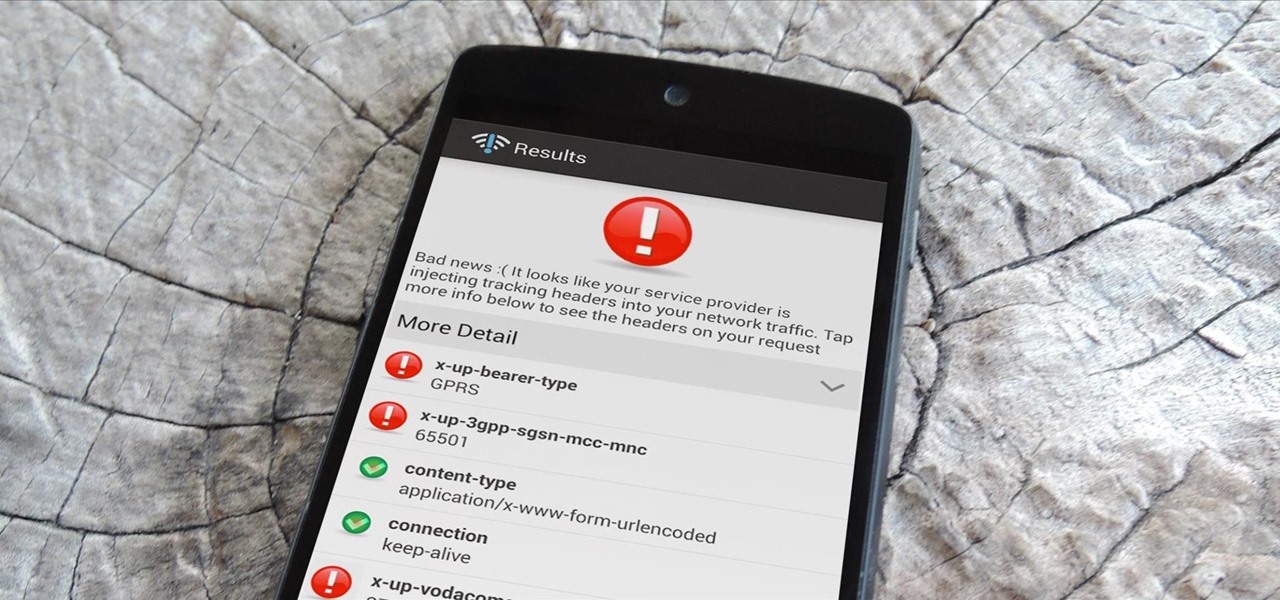
A shady practice in place by AT&T and Verizon Wireless—and possibly more wireless carriers—was recently uncovered. Outgoing data requests sent from devices on these service providers are being injected with a Unique Identifier Header (UIDH) that allows websites, the carriers, and potentially even government agencies to track your online activity.

How, you ask? They did it without requiring a goofy-looking face-computer. I know what you're thinking, "Without headgear, how is it a Glass killer?" It's because it does what Glass was meant to do: keep you connected while on-the-go, without constantly staring at your phone.

If you work at a large office or have a multi-story home, you're probably familiar with Wi-Fi range extenders. Since one hotspot isn't always enough to cover an entire area, Wi-Fi repeaters are generally set up in larger areas to capture and rebroadcast the original signal.

When I stumble upon a new song that I'm really into, I don't just listen to it repeatedly—I share it with family and friends that I think might enjoy it just as much as I do. Now, thanks to a new iOS app called Craaave, sharing those tunes are a cinch, no matter if I'm using Spotify, SoundCloud, or any other music streaming app on my iPhone.

We've had the pleasure of test driving the ASUS Transformer Book T100T for the last couple of weeks, and for a $400 Windows 8 machine, it's impressive to say the least.

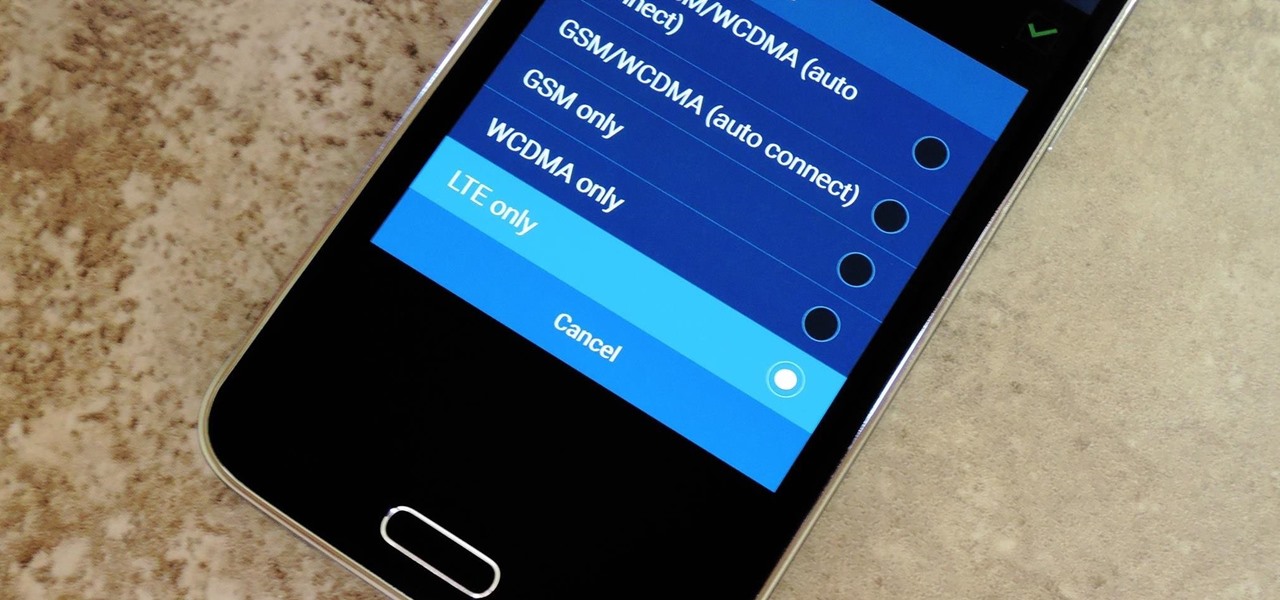
Even with the highest-tiered data plan available, there are times that your phone or your carrier might downgrade your connection to 3G or even lower. This usually occurs when you've made a phone call, or you've switched cell towers while traveling.

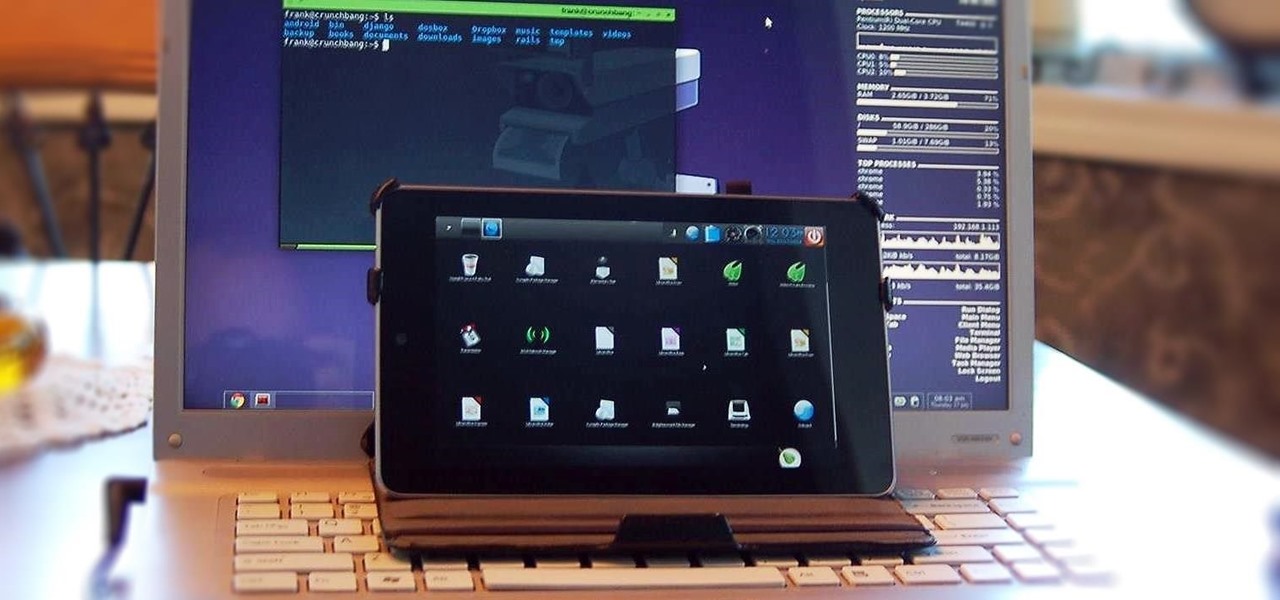
When people first learn that their Android device is capable of dual-booting different operating systems, e.g. Linux, they almost universally respond with, "That's so cool." And for those of us ambitious enough to actually try one out, we are typically filled with glee as we see Ubuntu, or something similar, boot up for the first time on our tablet or phone.

Ever use an open hotspot on your Note 3, only to find out that it's severely restricted to what sites you can access? While getting online with free Wi-Fi is great for those who have a limited data plan, when that one site you absolutely need to visit is blocked, you're left frustrated and sent back into the Wi-Fi menu for another access point.

There is no SD card support on the Nexus 7, so managing internal storage can be tricky. There are ways to free up space, but the biggest space hog on my tablet is music, and that's not something I'm willing to delete just yet.

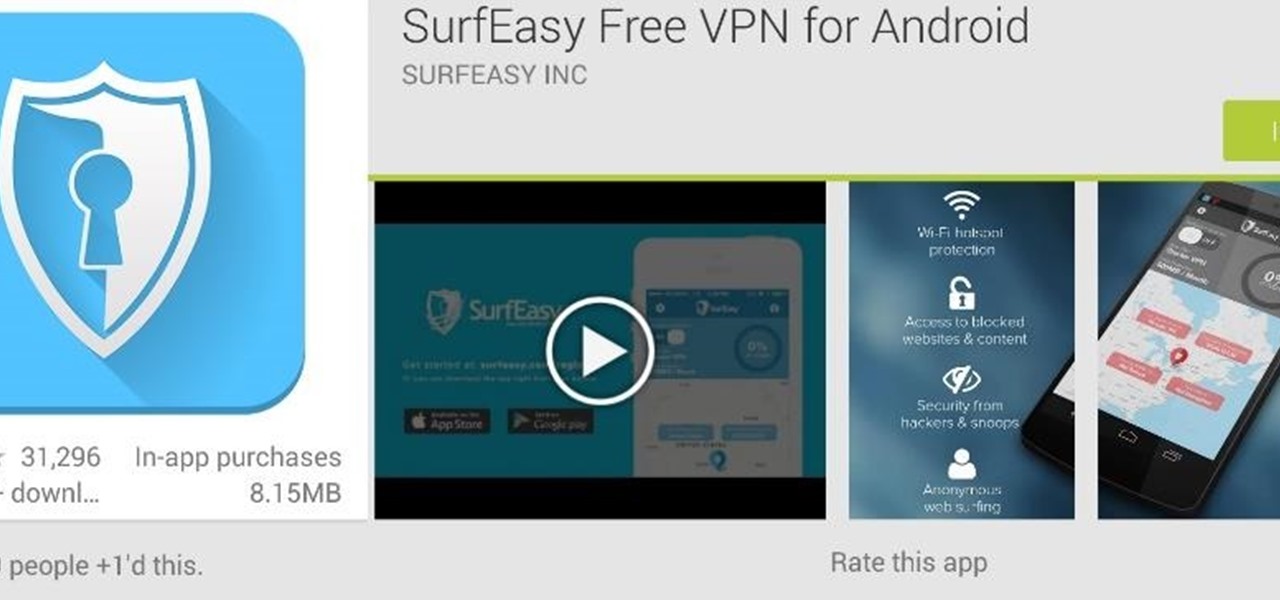
When browsing the web, you may not be quite as anonymous as you think, especially if you are using public WiFi. The easiest way to stay as anonymous and safe as you are going to get, is to use a VPN (there are a number of great free ones). In this tutorial, we will show you how to set up a VPN on Android, and how this protects you.

It's been over three months since iOS 7.1 came out, but your wait for jailbreak is now over. If you're still running iOS 7.0 iterations to maintain your jailbreak, you can now finally update to the latest and greatest thanks to a Chinese team of developers, who recently released their untethered jailbreak for Apple devices running iOS 7.1, 7.1.1, and even 7.1.2.

When OS X Yosemite was first announced, there were a number of features that struck my attention, but one in particular that stood out above them all was the ability to make and receive texts and phone calls from your Mac, which Apple calls Continuity.

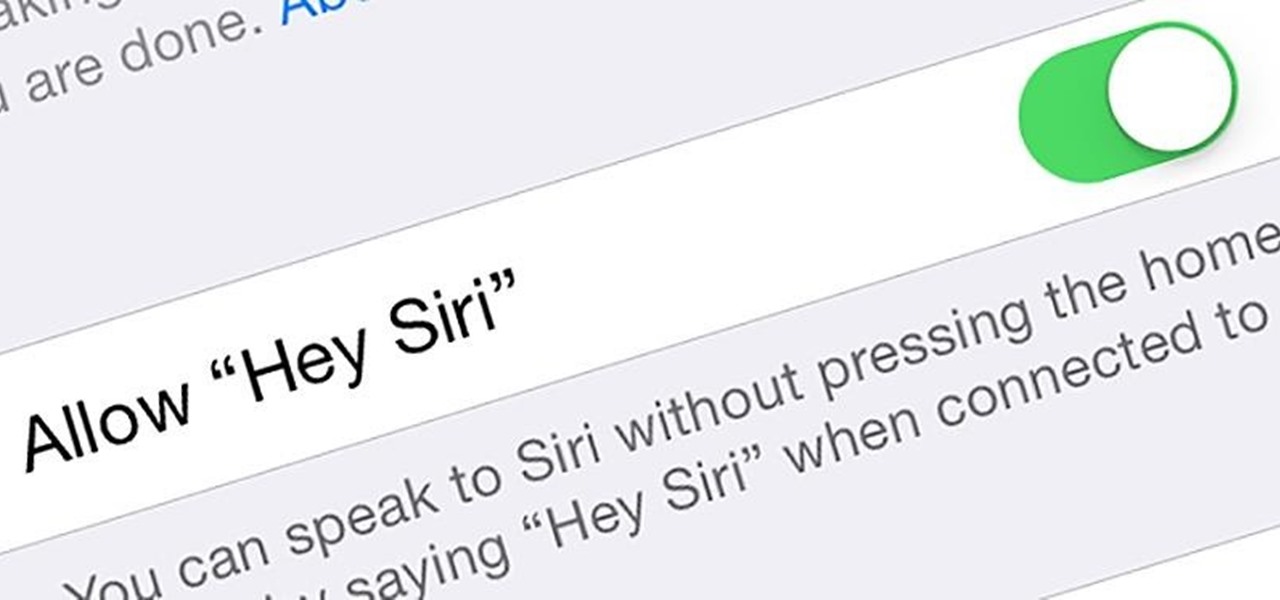
It seems that Apple is taking a page from Google's book with their new "Hey, Siri" voice activation feature in iOS 8. This feature mimics the one found in Google Now, the voice-activated intelligent personal assistant available to just about all Android users. Apple's version allows you to bring up Siri with a simple voice command, but there's a small catch.

Amazon just signed a deal with HBO to host the cable channel's original content on its Instant Video service. For those of us with Amazon Prime accounts, this is great news—but there aren't any readily apparent options for playing it on Chromecast.

These days, our smartphones carry some very sensitive data. From banking app passwords to personal photos, there are many things on your Nexus 5 that you might not want other people to have access to.

Welcome back, my tenderfoot hackers! We have looked at a number of ways that we sniff traffic on the network with such tools as Wireshark, tcpdump, dnsiff, and others, but each of these tools is only capable of pulling packets off the wire.

If you lend someone your phone, even if it's just for a second, there's a chance they can enter an app and see something you'd rather they didn't. Whether it's a personal email or a private photo, there are plenty of reasons why you'd want to keep snoops out of certain apps.

As the Chromecast becomes more and more popular (it's even available overseas now), the market has seen an avalanche of Chromecast-compatible apps. We can play games, cast TV stations, and even mirror our screens, but today I'm going to show you a multifaceted tool that'll do everything from broadcasting your camera to displaying your documents.

Pretty soon, every restaurant and store you walk into will know exactly what you're doing. Retail analytics companies like Euclid, ShopperTrak, RetailNext, and Prism Skylabs have penetrated hundreds of food shops and retail stores across the country, installing sensors that track and log customers' moves while they dine and shop.

Ever since its introduction back in iOS 6, AirPlay has been helping us iOS and Mac users stream content over to an Apple TV or third-party speaker system. It's an incredibly useful feature. However, it's also severely limiting. The few compatible products out there are extremely expensive, making wireless streaming a not-so-easy task.

Welcome back, my budding hackers! One of the keys to becoming a professional and successful hacker is to think creatively. There is always a way to get into any network or system, if you think creatively. In previous tutorials, I have demonstrated ways to crack passwords on both Linux and Windows systems, but in this case, I will show you a way to get the sysadmin password by intercepting it from a Remote Desktop session.

Applications, features, and software running in the background of your Samsung Galaxy Note 2 can drain a significant amount of battery power, even when your smartphone isn't being used. For this reason, smartphone carriers and developers suggest that you turn off Bluetooth, Wi-Fi, and other battery hogging features when they're not being used.

No offense to T-Mobile, but if you head over to their support page for the Samsung Galaxy Gear, you get the information below on how to take a screenshot of your smartwatch. Oh, thank you for that.

Welcome back, my rookie hackers! When Wi-Fi was first developed and popularized in the late '90s, security was not a major concern. Unlike wired connections, anyone could simply connect to a Wi-Fi access point (AP) and steal bandwidth, or worse—sniff the traffic.

Why do we still need to plug in our phones to charge them? Wireless charging exists, and has for quite some time, but most manufacturers don't include it in their devices. When it comes to the Samsung Galaxy S4, you can buy a QI-compatible wireless charging kit, but between the charging pad and the battery cover, you're looking at around $90 or more.

Welcome back, my greenhorn hackers! Continuing with my Wi-Fi hacking series, this article will focus on creating an invisible rogue access point, which is an access point that's not authorized by the information technology staff and may be a significant security vulnerability for any particular firm.

Welcome back, my neophyte hackers! As part of my series on Wi-Fi hacking, I want to next look at denial-of-service (DoS) attacks, and DoSing a wireless access point (AP). There are a variety of ways to do this, but in this tutorial we'll be sending repeated deauthentication frames to the AP with aircrack-ng's aireplay. Remember, hacking wireless networks isn't all just cracking Wi-Fi passwords! Our Problem Scenario

Like most Android devices, the Nexus 7 suffers from its fair share of battery gripes. Nobody wants to see that dreaded "connect charger" warning pop up on their screen. NOBODY. Yet it probably happens to you every day nonetheless. What can you do about it besides charge, charge, and charge? Well, there's actually plenty that you can do. You can manage your notifications better, keep your screen brightness low, and kill apps running in the background. Or, you could just optimize your battery t...

We've all seen the blue screen of death at least one time in our lives. I grew up using a Windows PC about the size of a small refrigerator and that damn screen popped up at least once a day. Thankfully, errors like these happen much less often, but now that our smartphones have basically become pocket PCs, these type of errors can and do happen.

While the majority of America was watching the Super Bowl yesterday, the crew over at the evad3rs was finishing its work on their untethered iOS 6.1 jailbreak called evasi0n. Well, the wait is finally over!

There's a lot that goes into making a nice crystal radio set, so this is going to have to be broken down into two parts. The first part is the actual making of a functional radio, and the second part is making the whole arrangement look nice. In this part, I'm actually going to tell you more than just how to make a crystal radio, but I'm also going to explain how and why they work. Crystal radios are pretty Steampunk in and of themselves, since they were first developed in the late 19th centu...

The reason Amazon's Kindle has become so popular over the past several years is due to the amount of digital books one can fit inside—over 1,000 for the smallest Kindle. Gone are the days of lugging around heavy books to school and the airport. Instead we can fit our e-readers snugly inside our bags and never worry about forgetting a book.

Sprint has announced that it will be the first U.S. carrier to release Jelly Bean 4.1 for the Samsung Galaxy S III. The over-the-air updates have already started, with users receiving a notification on how to update on their phone. The reason Jelly Bean has garnered so much attention is due to several, well-known features like Google Talk, Project Butter and expandable notifications.

Free stuff is pretty cool. Free internet is even cooler—and free internet that is actually free is the coolest. If you would rather avoid sitting in a Starbucks and having to listen to hipsters discuss the proper length of cropped jeans, then this should be of interest.

With the microwave oven transformer (M.O.T.) salvaged in a previous project, a simple electrical circuit can be rigged to get high voltage arcs to fly outward and upward along a "V" shaped spark gap.

There was a dynamic mic in my junk box, but without any stand or connection cable. I needed a high-quality microphone to narrate my project videos, so I had to think of a way to build a stand for the mic. This is what I came up with.

In an effort to appease iPhone fans eager for an NFC-equipped device, an option that is available on many other smartphones, Apple created Passbook, their version of a digital wallet.

Most newer computers come with a webcam, but if you're using an older system, you may not have one. If you only need to use a webcam occasionally, it may not be worth putting the money into, so why not just use your smartphone? There are a few apps out there that can help you turn your phone into a super-convenient wireless webcam and save some cash.

Doorbells are a great idea. They let you know when someone who's not a burglar is trying to enter your house, apartment, or squat. They eliminate the need for lots of noisy yelling and startling door pounding.