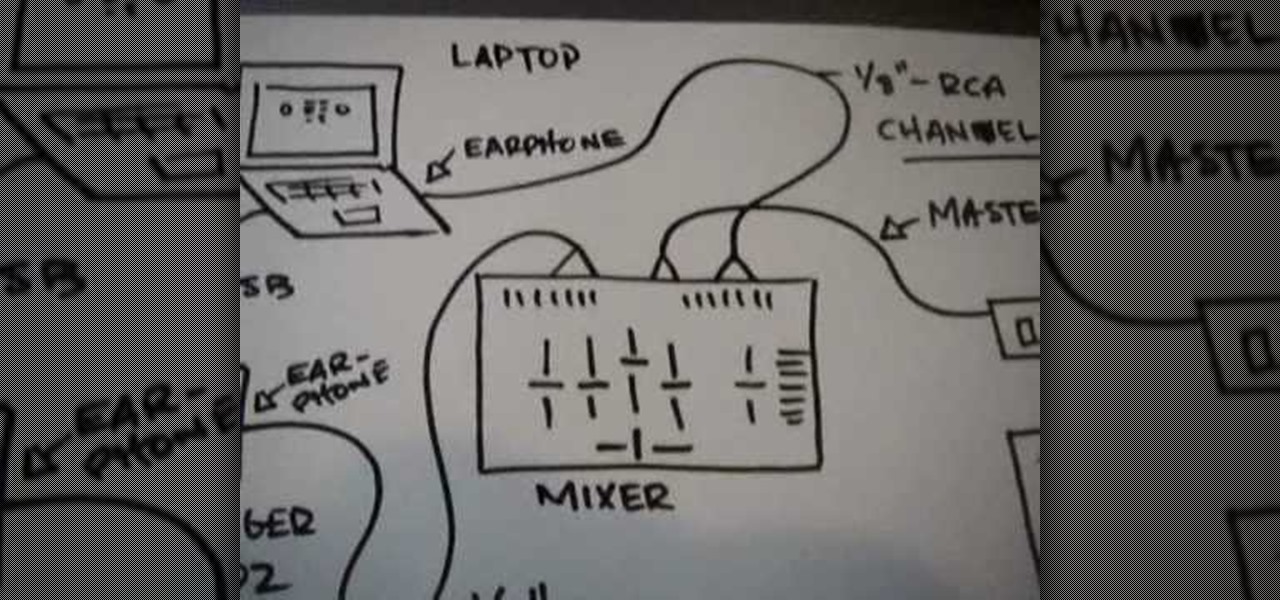
This video shows you how to connect your laptop to your mixer. First you will need two different sound sources from your laptop to your mixer. This is so that you can use all of your mixer functions on two different channels. The way to do this is to run a 1/8" RCA cable channel 7 from your normal earphone jack to the mixer. Also use a behringer uca202 audio interface to connect to the laptop via USB cord. This provides another earphone jack. Then use a master out cable to connect it to an am...

Learn how to connect a XBox 360 to the Internet via a Windows PC.

In this tutorial, we learn how to use Quick Connect Wireless with Epson Projectors. First, make sure you have one cable connected to the projector and one cable connected to the computer with a USB streamline. This makes it much easier and more efficient to plug in your projector. As soon as you plug this in, you will see a message appear on your notebook, then the screen will star to appear on the projector as it does on the notebook. It will take a few seconds, depending on the monitor and ...
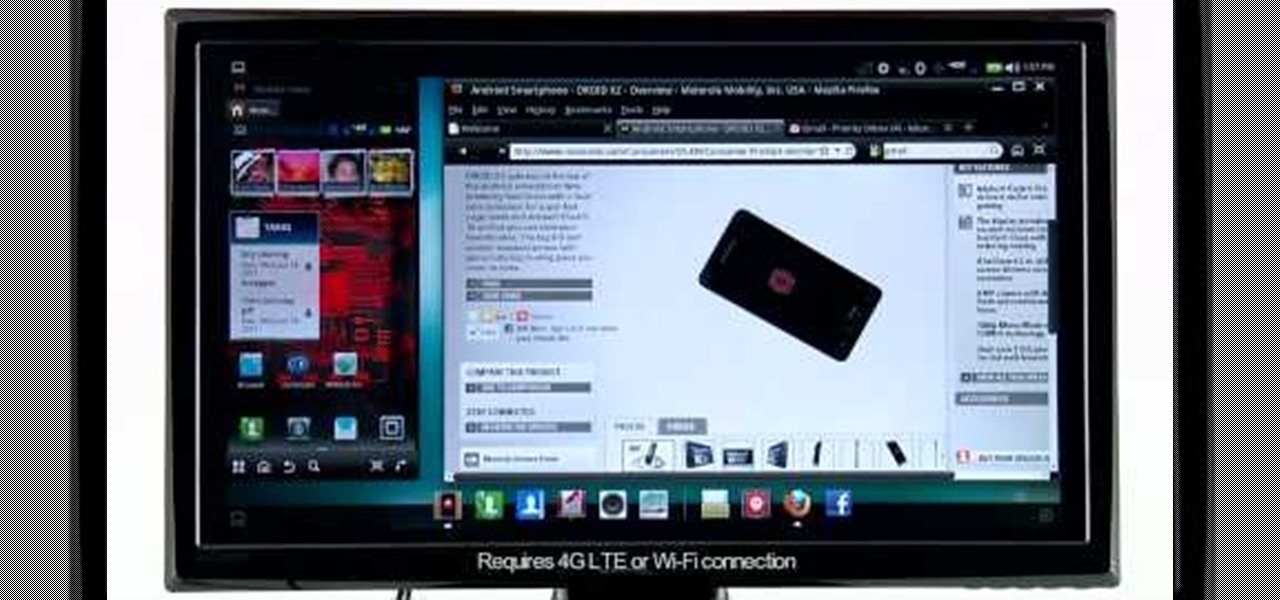
This four part segment from Motorola provides a ton of information and serves as a guide on Webtop for the Droid Bionic.

Yes, you can connect USB flash drives to your Apple iPad, but the trick is… you have to jailbreak it first. Most people won't want a jailbroken iPad, but when it comes to something like flash drive connectivity, that's when people start changing their minds! This video shows you how easy it is to connect USB drives via an application called iFile available on Cydia.

Learn how to connect a DVD or Blu-Ray player to the Internet. You'll see the simple steps on how to connect a DVD or Blu-Ray Player to the Internet using the powerlines in your home with Powerline Adapters from Actiontec Electronics.

Learn how to connect a DirectTV set-top box or DVR to the Internet. You'll see the simple steps on how to connect a Set Top Box or DVR to the Internet using the power outlets in your home with MegaPlug Powerline Adapters from Actiontec Electronics.

Learn how to connect your computer to the Verizon MI424WR FiOS Router using wireless. This video tutorial will show you the easy steps to connecting wirelessly from your computer to the Verizon FiOS Router by Actiontec.

Learn how to connect your Apple iPhone to the Verizon MI424WR FiOS Router using wireless. This video tutorial will show you the easy steps to connecting wirelessly from the iPhone to the Verizon FiOS Router by Actiontec.

Wireless can be a pain sometimes with video games on the Internet, with disconnections and signal losses, but why not revert back to a wired connection? This video will explain how to connect your Nintendo Wii to a wired network using Actiontec Powerline Networking technology. This will enable your Nintendo Wii to connect to the Internet to download games, console updates, and other information.

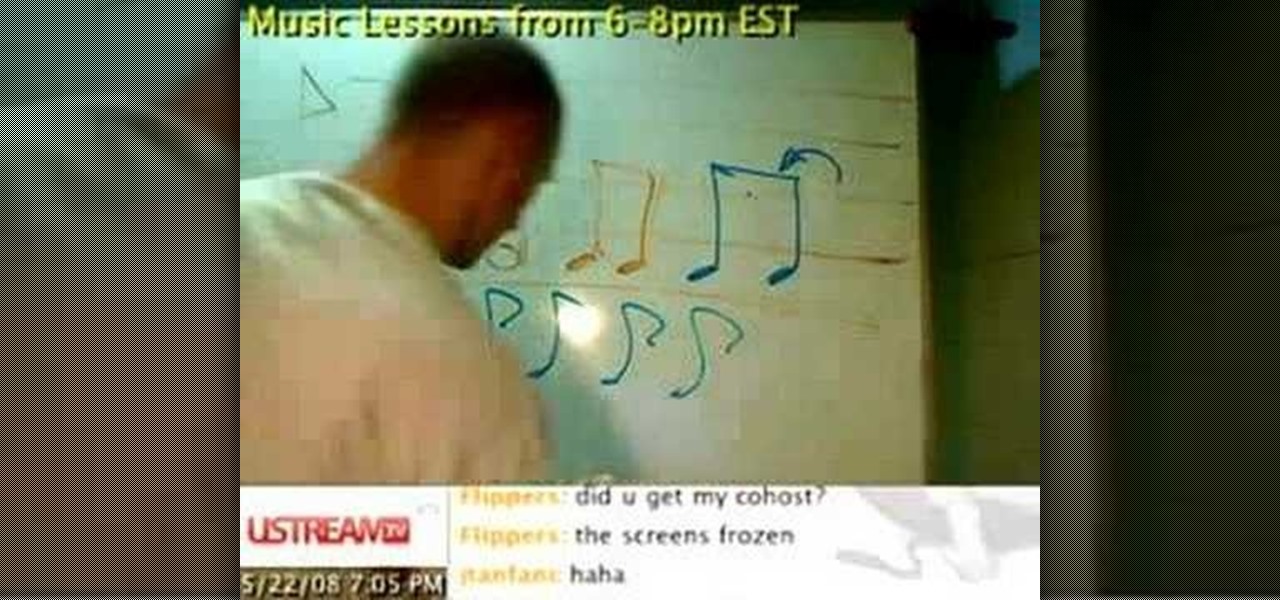
Connecting the flags on eighth notes, sixteenth notes, etcetera, is very important to neat, legible music. This how to video teaches you when to connect the flags in the music notes. Learn how to read and write music better with this music theory tutorial.

PirateBox is a great way to communicate with others nearby when cellular and Wi-Fi networks aren't available. With it, you can anonymously share any kind of media or document and even talk to one another by voice — without being online. However, it needs a Raspberry Pi, which is more expensive than ESP32 boards, and if you only need a text-based chat, there's a much simpler option.

The biggest hurdle to rooting is that it usually requires a computer. Things get complicated when you're trying to use a desktop operating system to exploit a mobile OS, and the connection isn't always reliable. But with the help of Magisk, you can now use one Android phone to root another.

UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, examining the underlying code to understand it, and creating our own version of the exploit in Python.

The Files app received a big update in iOS 13. Before, it was limited to local and cloud-based files, but now you can access data from external storage devices, including SD cards and USB drives. But before you try to connect your favorite card or drive to your iPhone, there are a few things you need to know.

Apple's update for iOS 13 is not without bugs and other issues, and if those problems become annoying or impede your ability to use your iPhone like usual, you may want to downgrade. Hundreds of new features may not matter if you can't use your iPhone like it's meant to be.

Imagine a scenario where you're nowhere near your iPhone, but it's on loud, and you really need to silence it. An alarm may be blaring, notifications could be spitting out sounds left and right, and calls may be ringing. Things can get annoying real quick for whoever's around it. Plus, all that attention makes it easy for someone to find and possibly steal your iPhone. Luckily, you can quiet it down.

In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffic like images from a Wi-Fi or IP security camera if we can get physical access to the Ethernet cable carrying the data.

Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

For lack of a better word, a missing iPhone sucks. Not only do you lose a physical device that cost you a small fortune, but there's also the probability you'll never see your precious data again. Hackers and thieves might, just not you. To keep this from ever happening, there are preventative measures you should take, and the sooner you do them the better.

Many popular IoT devices have terrible security. For instance, a hacker who's on the same Wi-Fi network as a Sonos speaker can assume direct control over the device's behavior. If an IoT device doesn't secure the messages used to control it over a network, it's easy for somebody to write a few Python scripts to make it do whatever they want.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

If you're currently running macOS 10.11 or higher on your Mac and connect your iPhone to sync with iTunes, you may get an alert saying that "a software update is required to connect to your iPhone." Here's everything you need to know about what that means, how to update your system, and what to do if updating doesn't work.

When you want to post a breathtaking landscape or picture-perfect portrait that you just took with your DSLR camera to Instagram, Facebook, or some other social platform, there's an easy way to do so — even if you don't have a computer handy, which is typical when you're out and about.

Deleted bank statements and private photos are still within an attacker's grasp, so don't think that emptying your recycling bin is enough to keep your files from coming back to life. It's possible for a hacker to recover compromising files and images from a backdoored computer completely without the victim's knowledge.

In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the necessary tools to begin our attack on John Smith's computer.

With the addition of the OpenSSH client and server in the Windows 10 Fall Creators Update, you no longer have to rely on third-party programs to open an SSH server and connect to a Windows machine. While still a beta feature, this represents a long-overdue update fulfilling a promise made back in 2015.

Last week, augmented reality startup Proxy42 released Father.IO, a multiplayer game that turns any indoor or outdoor space into a laser tag arena.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

When hacking into a network during a penetration test, it can sometimes be useful to create your own wireless AP simply by plugging a Pi into an available Ethernet port. With this setup, you have your own backdoor wireless connection to the network in a matter of seconds. Creating an AP is also helpful while traveling, or needing to share a connection with a group of people.

Android has several features built into the platform that improve user experience but require extra attention to prevent a security breach. By modifying these settings, you can drastically reduce the possibility of someone exploiting your device or intercepting information.

Hello ladies and gentlemen, PySec here coming at you with another informative(hopefully) article for you all. In the last tutorial, we finally finished our discussion about IP Addressing and I intentionally didn't mention a really important concept with which IP Addressing wouldn't be feasible without it. What I'm talking about is how our network device gets the IP Address in order to communicate with other devices on the network/Internet. There are many different ways for that to be accompli...
Have you ever used an open wifi, which after you connect displays a website to enter your credentials to get internet? That website is called captive portal and widely used in airports, hotels, universities etc. Have you ever wondered what would happen if someone would set up an open wifi with the same name displaying a very similar web page asking for credentials? Usually if there are multiple wifi networks with the same name and encryption, devices only display the one with the highest sign...

Recently, I've been experimenting with BeEF (Browser Exploitation Framework), and to say the least, I'm hooked. When using BeEF, you must "hook" the victims browser. This means that you must run the script provided by BeEF, which is titled "hook.js", in the victims browser. Once you've done that, you can run commands against the victims browser and cause all kinds of mayhem. Among these commands, there is an option to use the victims webcam. This is what we'll be doing here today, so, let's g...

These days, that pocket-sized computer we call a smartphone is home to your entire digital life. But with the onset of mobile payments and online banking, the line between your virtual world and the physical realm is becoming increasingly blurred.

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

Hi there again, aspiring hackers (and veterans as well)! I'm going to explain how to perform a dictionary attack on a WPA/WPA2 protected network with Wifite. Please note that this doesn't work with WPA Enterprise For that end, you'd have to use an Evil Twin to get the "Enterprise" auth attempt, and then crack it.

These instructions are applicable to both bObsweep models. Follow the video or text descriptions to replace the disinfecting UV lamp on your automatic vacuum.

Probably SSH is not as clean and fast as other useful tools like netcat, but it has some features which are very useful, and when you'll need them, here's how to behave with that huge amount of computers all over your house.