
The process of trying out new augmented reality and virtual reality hardware is as personal as it gets. Bottom line, if you can't directly try these immersive devices on, it's difficult to really understand the benefits they can bring to your life and work.

Among the various components of the emerging augmented reality space, the most lucrative is the advertising market. The prospect of turning every object, every location, ever signpost in the real world into a discount code or virtual transaction interface is why AR will ultimately be more profitable than VR.

In the case of Apple Watch v. Fitbit, the winner comes down to the judge at hand. Apple currently offers two smartwatches — the Series 5 and the Series 3 — while Fitbit offers three models — the Fitbit Versa 2, Fitbit Ionic, and Fitbit Versa Lite. Whatever your assumptions about these devices are, throw them out the window, as each has something unique to bring to the table.
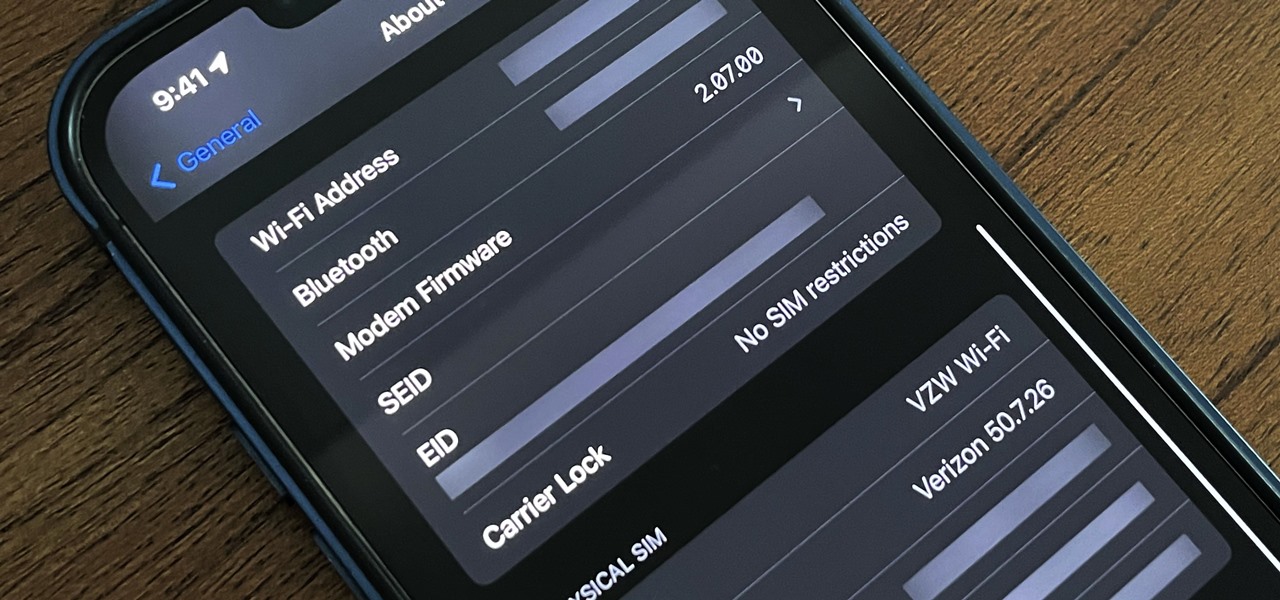
If your current cellular provider costs too much, has poor reception in your area, or doesn't support features you'd like to use, switching to another carrier is the obvious move. But can you bring your current iPhone or Android phone?

In this tutorial, Aharon Rabinowitz introduces you to the Fractal Noise Effect, and shows you how to create the animated backgrounds seen in the opening of the Creative Cow After Effects tutorials. Fractal noise is a powerful way to add variation and randomness to surfaces or scenes and this tutorial only covers the VERY basic basics of the tool. Use fractal noise in After Effects.

Electronic waste (or e-waste) is becoming a bigger and bigger problem thanks to the rapid growth of technology. In 2009, the United States produced 3.19 million tons of e-waste in the form of cell phones and computers. It's estimated that 2.59 million tons went into landfills and incinerators with only 600,000 tons actually being recycled or exported. Recycling programs just aren't cutting it, so what's the next best thing? Art.

Kevin Van Aelst creates witty visual "one-liners" by recontextualizing everyday, ordinary objects. With a few simple tweaks, the viewer recognizes a roll of tape as the ocean or reads gummi worms as chromosomes or understands mitosis through the use of sweet, sugary donuts.

Have an old-school tabula recta lying around? No? Then just print out the chart below. Nothing ensures better password security than this centuries-old cipher technique. Here's how it works, via Wikipedia:

Chi gyo ichi nyo is a familiar expression in the dojo. The word chi means knowledge. Gyo means doing, or action. Ichi nyo means inseparable. Action and knowledge are one! Acting without adequate knowledge or understanding is a constant source of frustration and problems. In our lives we are often busy and active without really understanding the basis of our actions and their full impact. Some people practice karate without really knowing why they are training. In class they do the techniques ...

Despite the fact that you may not find this as a necessity, if you do follow this quick guide, you will wonder how you ever managed before. This tutorial is based on the assumption that you're using Google Chrome, so if you aren't, I advise you to download and install it. Furthermore, this tutorial is aimed towards beginners, however advanced users may also learn a thing or two.

Note: The article assumes that the reader has a fundamental understanding of at least one other programming language and Perl. This is intended serve as a quick reference for Perl's input/output of data to databases.

Last time, we looked at archaic cryptography, so you should have a basic understanding of some of the concepts and terminology you'll need. Now, we'll discuss one of the most important advances in computer security in the 20th century—public key cryptography.

There are a lot of fantastic video games out there. Indie Games Ichiban's bread and butter is making sure that you steer clear of the bad ones and embrace the good. But really, the biggest goal here is to help everyone have more fun. To that end, today a game is not recommended, but an event. If you like games—not just video games—but tabletop, board and even hopscotch, then PAX Prime is one of the best events you could possibly go to.

"Simplicity is the ultimate sophistication." -Leonardo da VinciLearning a kata requires that you go through several stages. First you have to learn the basic pattern and the techniques. Then you have to perfect what you've learned. Then you have to deconstruct what you've learned and perfected in order to truly understand what the kata is teaching you vis a vis close quarter engagement.

So far in this game, my score card: 0-1 from saving a guy from coyotes. My first ever fail in the game.

Welcome to Minecraft World! Check out our advanced tutorials and come play with us on our free server.

Introduction PostgreSQL is a very popular Open-Source database management system. It competes heavily with many proprietary and commercial database management systems. More information on what it is and it's history can be found here and here.

You want to put out a live web server, but you don't want to be owned in the process. An expert eye for security is not needed if you take a few basic steps in locking down the hatches. Most successful attacks today are not the complex, time-consuming tasks you might think, but simple lapses in policy that a hacker can take advantage of to compromise your server.

Have you ever forgotten your password and didn't know how to get back on your computer? Or ever had an annoying roommate you wanted to play a trick on to teach them a lesson? Or perhaps overly religious parents who think the internet is of the devil and won't let you read online articles about elliptic curve cryptography applications to C++? Well, then this article is for you!

Note: The article assumes that the reader has a fundamental understanding of at least one other programming language, and that this is intended serve as a quick reference for Perl's basic syntax & behavior in regards to Variables, Control Structures, & Functions.






















