
How To: Start Your Own Organic Seedlings Indoors
Starting your own seedlings is a great way to save money, have a wider selection of varieties and gain personal satisfaction. Here are easy to follow tips on getting your seeds off to a great start.


Starting your own seedlings is a great way to save money, have a wider selection of varieties and gain personal satisfaction. Here are easy to follow tips on getting your seeds off to a great start.

While the Google Play Store is filled with big name magazines like Time, Forbes, Sports Illustrated and Maxim, it also panders to smaller audiences, like with Coin Prices, Soap Opera Digest, Watch Journal and Quilter's World (which yes, is all about quilting). If you have a select few that you enjoy reading, prices aren't usually a problem; issues range from $1.99 to $4.99 for each one, or from $19.99 to $39.99 for yearly subscriptions. If you're someone that is a magazine connoisseur, prices...

Android devices are known for their USB and Wi-Fi tethering abilities—rooted or unrooted—which comes in handy for those that travel and need internet on their laptops in areas that don't have any Wi-Fi networks available, but have a strong cellular signal.

Last week, HTC released their new Droid DNA smartphone in hopes of gaining more traction in a smartphone world currently dominated by Apple and Samsung with their popular iPhone and Samsung Galaxy lines. The new Droid DNA boasts a 5-inch 1080p display—the highest resolution for any smartphone on the market. It runs Android 4.1.1 Jelly Bean with HTC Sense software, and has may other typical features, such as NFC and wireless charging.

The newest update of the Firefox web browser was released yesterday, and whether you were upgraded automatically or manually, Mozilla is advising that you downgrade to Firefox 15.0.1 as soon as possible. Firefox 16 is Mozilla's latest release, and is apparently extremely susceptible to malicious sites hacking their users complete browsing history.
If you're familiar with games like Half-Life 2, Left 4 Dead, Portal, and Team Fortress 2, then you've probably seen some of the cool animated movies that Valve has made for them using their Source Filmmaker moviemaking software. It's a tool built to make animated films inside their Source game engine. It's even been licensed to make the upcoming animated film Deep.

Looking to gain access to Skeletron's dungeon, without having to fight and kill Skeletron himself (herself? itself?) This video demonstrates a technique for entering Skeltron's dungeon without having to fight that particular Terraria boss. Watch and lean how to break into Skeletron's dungeon in Terraria.

Pacman is gaining in popularity lately due to the game's 30 year anniversary. If you would like to take Pacman out of the game and into real life, check out this tutorial.
Want to be the John (or Jane) D. Rockefeller of Restaurant City? Watch this video tutorial to learn how to hack Restaurant City with Cheat Engine 5.5 (02/04/10).
The chunin exam. It's one of the hardest parts of Ninja Saga. Can you pass the test? Or do you need a little help on this exam?
Watch this video tutorial to learn how to level hack Restaurant Life (12/05/09). 1. Open RL and Cheat Engine 5.5, then point CE 5.5 to the process of your browser.

If you are looking to improve your piano technique then this how to video is the place to start. You will learn how to strengthen individual fingers with these easy piano exercise. This is a great exercise for intermediate to advanced students. With this tutorial you will be able to gain strength in your fingers with this piano exercise. Play stronger, faster and with more confidence with these exercises.

Check out this Korean language tutorial video to practice introducing yourself in Korean. Watch as other Korean learners introduce themselves in this demonstrational video. This video is a great way for beginners to gain familiarity with the common effort of introducing yourself in Korean. This instructional Korean language video also provides a great way to improve your listening skills.

Like most RPG games, accruing money in the classic Nintendo game Ultima Exodus is a long grueling task. Take a look at this tutorial and learn how to quickly gain the cash you need to save the world. With this video, you should be able to rack in at least 20,000 gold in an hour.

This Sun Salutation sequence is a very invigorating 23-minute yoga routine and a great way to start your day. In this fitness how to video, Sarah Sutton leads you through a strenuous yoga workout, the Sun Salutation. Yoga help us both obtain physical balance and helps us in keeping balance in our lives. Watch this tutorial and you will learn how to gain strength and flexibility through yoga.

Learn a relaxing yoga routine to release the tension in your head, neck and shoulders. In this fitness how to video, Deborah York guides the viewer through a yoga routine designed to stretch and relax the upper back and neck muscles. Yoga help us both obtain physical balance and helps us in keeping balance in our lives. Watch this tutorial and you will learn how to gain strength and flexibility through yoga.

Many of the minor pains in the lower back are directly related to tight hips and psoas. In this fitness how to video, Deborah York guides the viewer through a yoga routine designed to stretch out the lower back, hips and psoas muscle. Yoga help us both obtain physical balance and helps us in keeping balance in our lives. Watch this tutorial and you will learn how to gain strength and flexibility through yoga.

The Downward Dog is one of the most popular yoga poses, but it is often done wrong. In this fitness how to video, yoga instructor Deborah York teaches how to properly do the pose Downward Dog. Yoga help us both obtain physical balance and helps us in keeping balance in our lives. Watch this tutorial and you will learn how to gain strength and flexibility through yoga.

Controlling your breathing in yoga is one of the ways to bring in more energy, life force, or in yoga it is called "Prana". In this fitness how to video, Pius Ruby and Deborah York will guide you through one yoga breathing method. Yoga help us both obtain physical balance and helps us in keeping balance in our lives. Watch this tutorial and you will learn how to gain strength and flexibility through yoga.

Learn how to gain better control of handling the ball with both hands while staying in the lane with the help of this great basketball dribbling drill for alternating hands.

Check out this video for a step by step tutorial on how to perform the very cool hitchhiker stunt on your BMX bike. In this clip, Rad Dad shows you how to combine a bunch of different tricks into one - the hitchhiker! This is a pretty advanced move so you will need to be familiar with steamrollers, double footed steamrollers, half hikers and karl kruisers.

In the Xbox 360 game Darksiders, you're nearing the end of the game when you get to the Black Throne, which consists of three guardians and Straga. Proceed across the bridge as it constructs itself then enter the main room of the Black Throne. Here you will find Azrael who will tell you about Straga and how he gains great power from the Well of Souls. You will need to defeat the three Guardians that protect the Well of Souls and use their power to destroy the three statues that imprison Azrae...
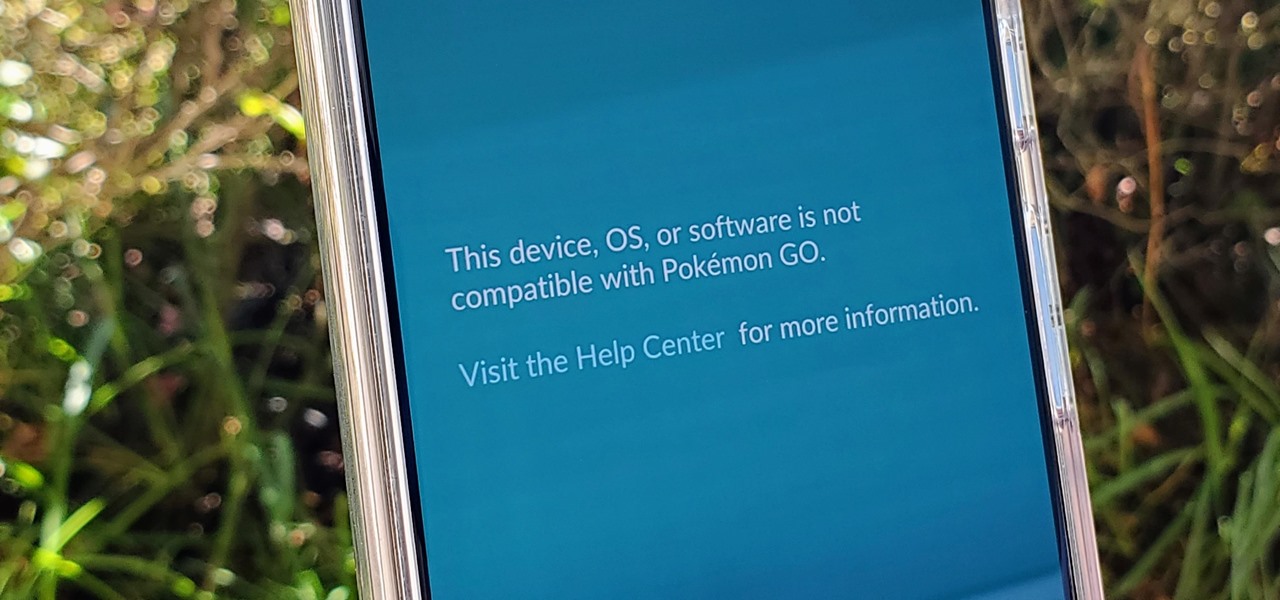
If you're a root user who has played Pokémon GO over the years, then you're probably familiar with the detection methods used to spoil your fun. The game's developer, Niantic, has publicly mentioned their ongoing battle with rooted Android phones and are unwilling to let up. They have a no-nonsense approach to try and keep you from playing, and they've stepped their game up once again.

Privilege escalation is one of the essential skills a hacker can have and often separates the newbies from the pros. With a continually changing landscape and a plethora of exploits out there, it can be a problematic aspect of any attack. Luckily, some tools can help expedite the process. Linux Exploit Suggester is just one of many to help you get root.
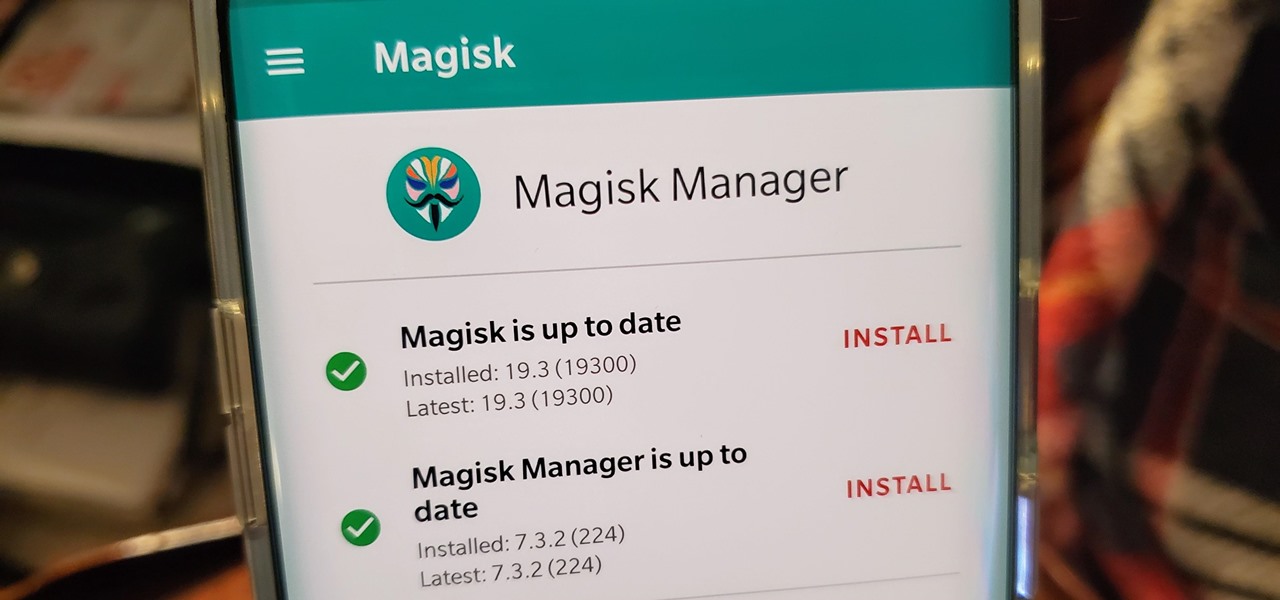
OnePlus has purposefully made their devices easy to root so that you can spend less time waiting and more time doing. These phones are a solid choice for anyone looking to dive into the rooting and modding scene. Using the same principles that Google has with the Pixel line, you can always be sure your OnePlus 7 Pro will get first-class treatment from launch day and beyond.
The Pixel 3a came out of nowhere and flexed its muscles to show the industry that you can have a great phone without a hefty price tag. Since Pixel smartphones are first-party devices straight from Google, you can be sure you'll have root access one way or another. For right now the method used to get your Pixel 3a rooted will take a few steps, but they go by real quick.

When shooting video on your phone, you have two cameras at your disposal, the rear camera and the selfie camera, and you can switch freely between the two. As for microphones, you may have more than one but, unlike with the cameras, it's not easy to switch between them. Filmic Pro solves this problem by isolating the mics so you can choose the best option for the audio track.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.
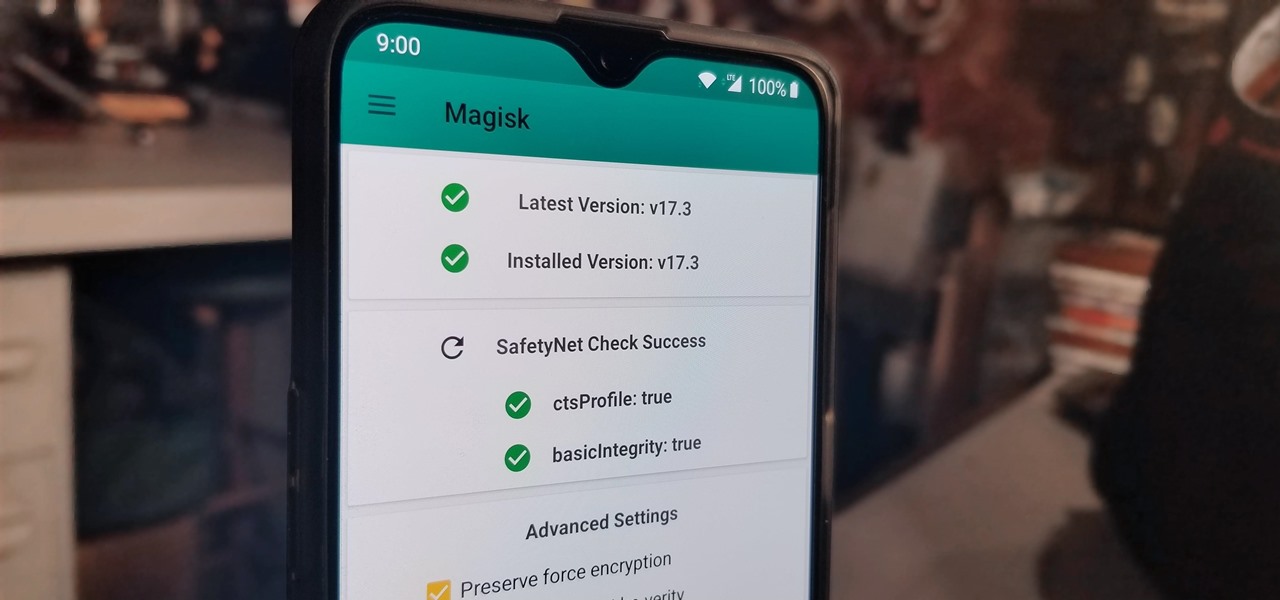
With the recent launch of the OnePlus 6T, the company continues to impress us with some of the best phones when it comes to the rooting and modding. OnePlus has made it easy enough to get up and running with the rooting process as fast as possible. The OnePlus devices follow the same core principles Google uses for their Pixels, which is excellent news for both the user and the development side of things.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

With just one line of Ruby code embedded into a fake PDF, a hacker can remotely control any Mac computer from anywhere in the world. Creating the command is the easy part, but getting the target to open the code is where a hacker will need to get creative.

We're all aware that Google collects a notable portion of our data. Thanks to the increasing awareness, Google has added a number of privacy controls to limit data collection. But Google doesn't just collect personal data for no reason — many of your favorite apps will use this info to improve their services and add new features.

Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life.

One unique feature of Firefox Mobile is extensions. Extensions allow users to add in features that didn't originally come with the browser. These add-ons provide an array of features, including improvement to privacy and security.
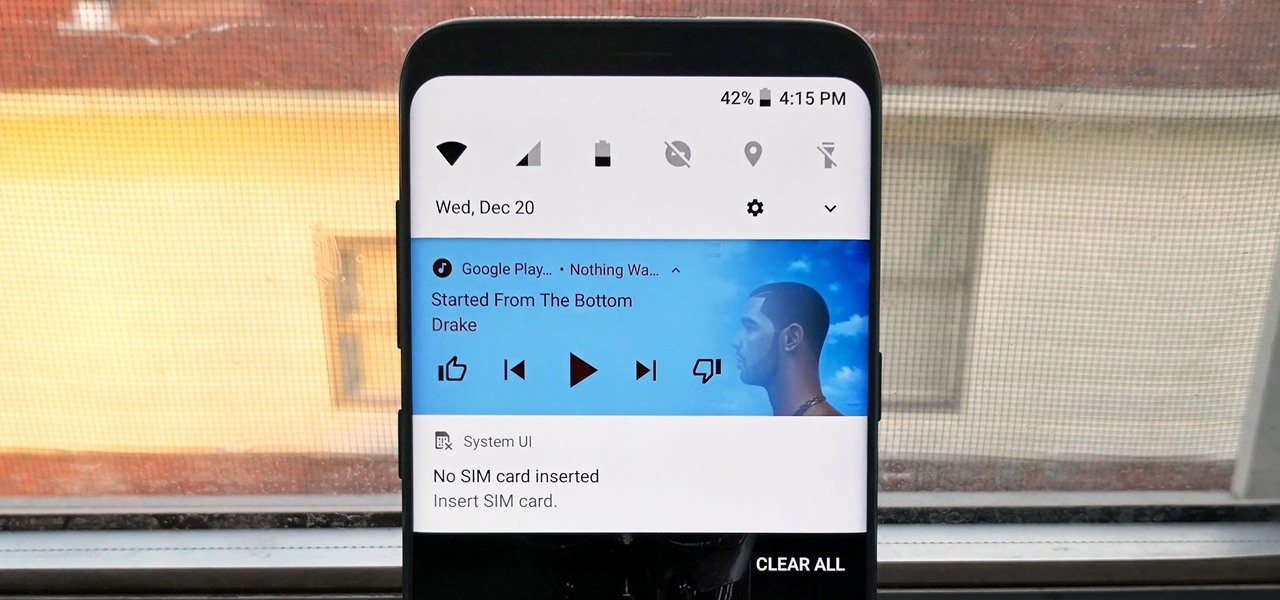
One of the biggest gripes we always hear about is the changes OEMs make to Android's notification shade. Icon styling and home screen layouts can be fixed with custom launchers like Nova and Action, but we're stuck with the tacky Quick Settings theme our phones came with. Today, we no longer have to envy Pixel 2 owners, as a new app will give you that clean stock Android look on any phone.

If you own a Pixel or Nexus device, Project Fi is a great alternative for cellular service outside of the four major US carriers. Project Fi is a Google-managed MVNO, providing service primarily through the T-Mobile and Sprint networks. One of the biggest mysteries on Fi is which network you're connected to at any given time, but there's a simple solution.

When it comes to applying augmented reality to various business functions, as the saying goes, there's more than one way to skin a cat.

The problem with HIV is that it attacks and kills the very cells of the immune system that are supposed to protect us from infections — white blood cells. But a new technique, developed by scientists at The Scripps Research Institute (TSRI) in La Jolla, California, offers a distinct HIV-killing advantage.

The Shadow Brokers, a hacker group known for its dump of NSA hacking tools in 2016, has just leaked their remaining set of data which implies that the NSA compromised SWIFT, the global provider of secure financial services, to spy on banks in the Middle East.

As fun as it is to see Fido's face light up when you feed him table scraps, American dogs are getting fat. The good news is that research is homing in on nutritional strategies to boost canine capabilities to maintain a healthy weight.