
Apple AR: Alexa Plays Nice with ARKit in Demo
A developer has previewed a pair of potential applications built on ARKit that can be triggered by Alexa, the resident voice assistant of the Amazon Echo.


A developer has previewed a pair of potential applications built on ARKit that can be triggered by Alexa, the resident voice assistant of the Amazon Echo.
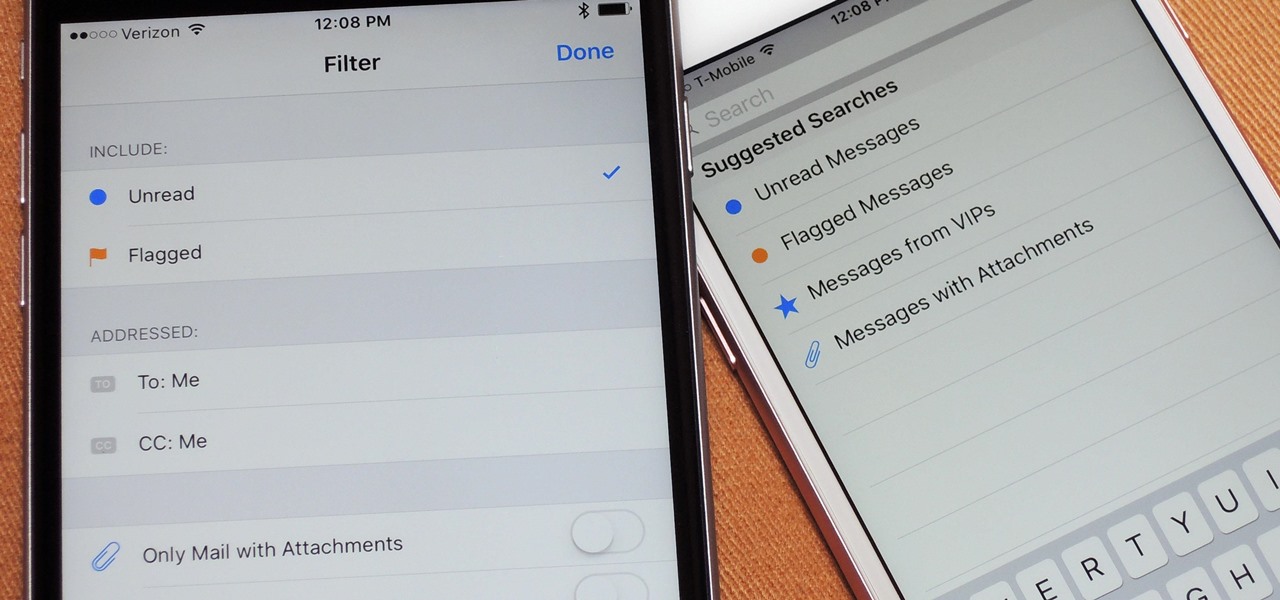
While filters were technically available in Mail for iOS previously, you would have to hit "Edit" on the main Mailboxes view and add them as folders, which made your already crowded main screen even more crowded.
Google's design chief Matias Duarte has gained fame and acclaim for his recent visual revamp of the Android operating system, and now, Google's starting to incorporate this Material Design styling into more of its products.

As one of the most frequently used Android browsers, making Chrome work faster and more efficiently is something we can surely all appreciate. And just like its computer-based counterpart, there are experimental flags for the mobile app that can speed browsing up significantly.
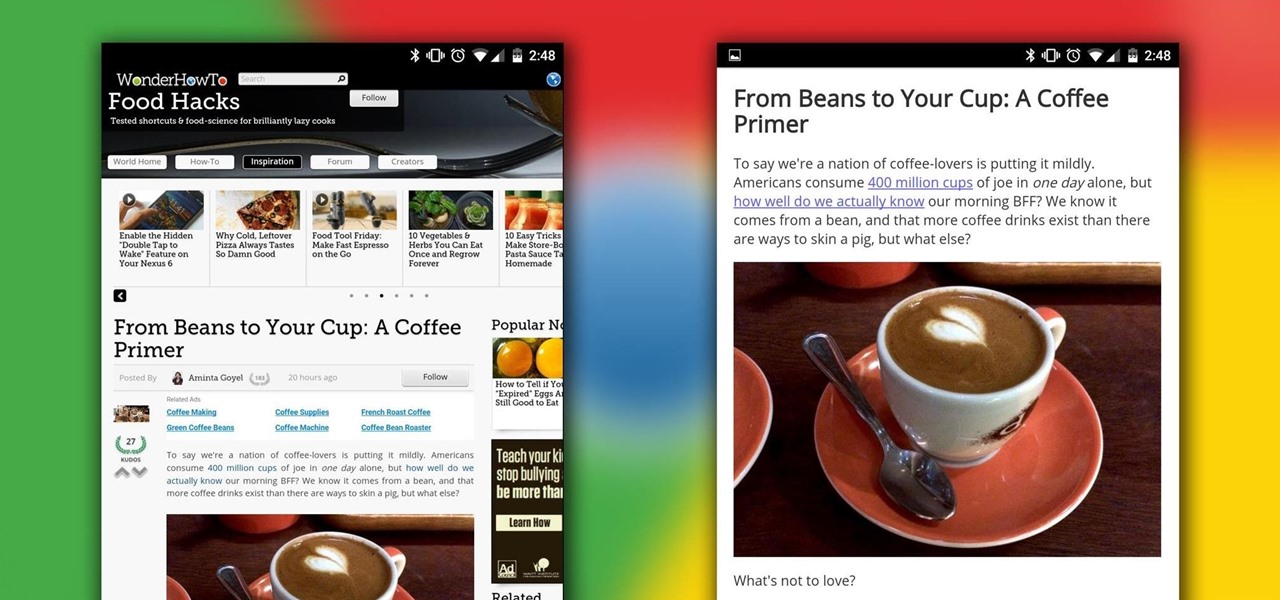
Reading articles on an Android phone using Chrome Browser can be a little bit of a battle; it often times requires adjusting the page to fit the screen in order to make it easier to read and scroll through. I sometimes lose this struggle and give up trying to read on my device, saving the article for a later time when I'm on my laptop.

In this video tutorial, viewers learn how to type in special characters. Begin by opening System Preferences and select International under Personal. Then click on the Input Menu tab and check Character Palette and Keyboard Viewer. Now check "Show input menu in menu bar" and click OK. Then click on the flag icon on the top of the screen and select Show Keyboard Viewer. This will allow users to type or mimic the actions of the keyboard. Users are also able to change the character by selecting ...

This video shows you how to do video lighting for product shots. In order to do this the presenter begins by putting the product on a plate. He has three lights that are placed around the product. 650 watt shooting onto the background. The second light is 1000 watts, with an open face shooting into a soft box. It has a flag to protect the light. The third light has an umbrella giving fill on the background. He then shuts off all the lights except for the background light giving a shot of the ...

Cooking steak can be a challenge but head Chef Donald Russell will show you how you can cook your steak perfectly every time. It is important to start with a nice piece of fresh meat and with a few helpful tips you will be sure to have succulent steak.

Relationship experts Dan and Jennifer addressed a letter from a worried boyfriend concerned that his girlfriend may be practicing unfaithful behavior. The girlfriend went out of town for her birthday and did not invite the boyfriend along. She did not call or text him the entire day, which of course threw up red flags. Dan and Jennifer advised the boyfriend to calmly approach the situation and explain to her how these actions made him feel. They stated that the girlfriend may be backing up fr...

In this video there is a person in the background who helps people with the game of Minesweeper that is on most computers. He shows you what is on the mine grind and all the basics to start. And, to start, you first hit the happy face and you see what the numbers on the mine grind means and where the bombs are. Then he shows how to post a red flag to show the computer where the mine is and know not to click the bomb. Some beginners might find some bombs in the very beginning; but with practic...

In this series of internet commerce videos, our bookselling professional gives you expert advice on how to sell your old books. She tells you how to determine their value using the esoteric language of the rare book world.

Gathering information on an online target can be a time-consuming activity, especially if you only need specific pieces of information about a target with a lot of subdomains. We can use a web crawler designed for OSINT called Photon to do the heavy lifting, sifting through URLs on our behalf to retrieve information of value to a hacker.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

While maggots living in human eyeballs isn't necessarily a problem in the states, it could happen to you one day if a fly decides your warm eyeball is a suitable place for its larvae. If this rare event should happen, before you start gouging your eyeball out, remember this trick from National Geographic explorer and engineer Albert Lin and everything will be okay.
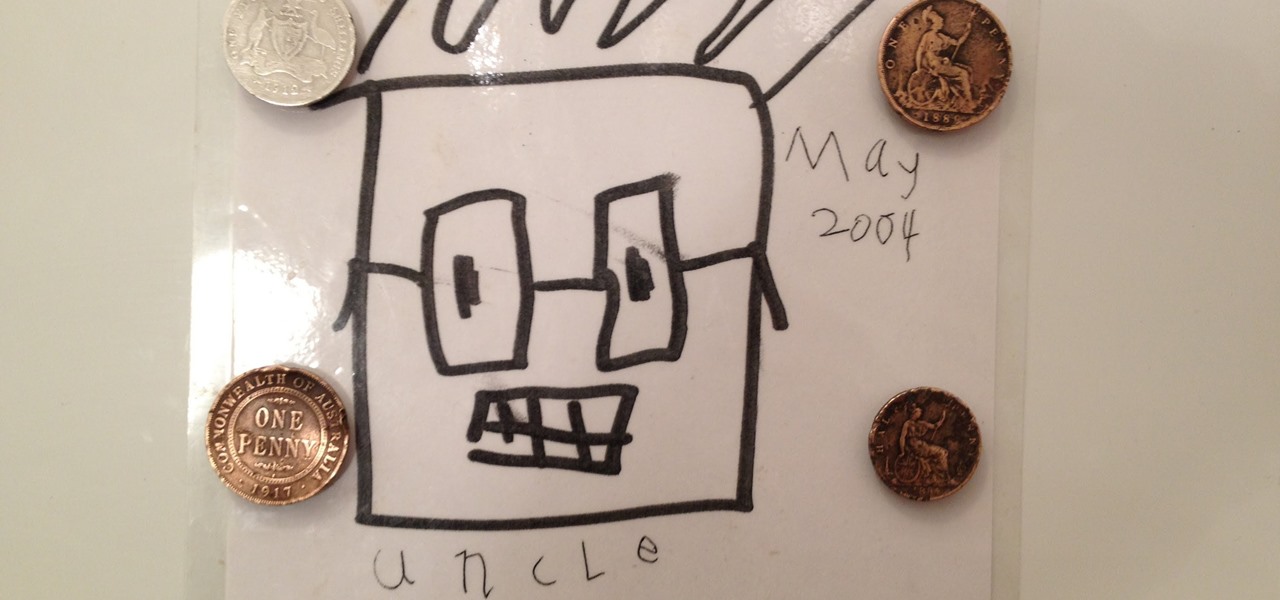
How to make a fridge magnet. The Worlds Oldest Fridge Magnet! Using rare earth magnets, l've made these refrigerator magnets using old, no longer in use, coins.

Cross-site scripting is one of the most common vulnerabilities found on the web today, with repercussions of this type of flaw ranging from harmless defacement to sensitive data exposure. Probing for XSS can be tedious and time-consuming for an attacker, but luckily there are tools available to make things a little easier, including Burp Suite, Wfuzz, and XSStrike.

After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.
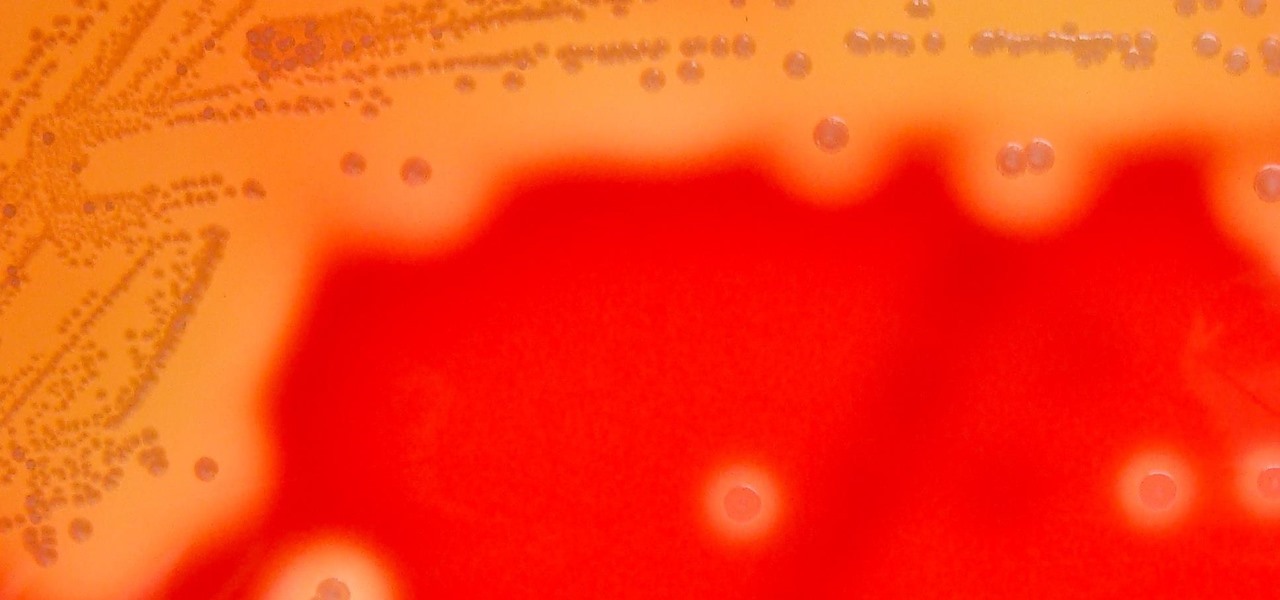
Streptococcus and staphylococcus bacteria produce toxins that can cause toxic shock syndrome.

It's not the bacteria itself that takes lives and limbs during invasive flesh-eating bacteria infections. It's the toxins secreted by the group A Streptococcus bacteria invading the body that causes the most damage.

Finding Pokémon in the wild isn't the only way to add to your collection in Pokémon GO—you're also able to hatch your own from eggs that you've gotten from PokéStops.

In this video series, CGI Animator will teach you how to make a waving flag using the computer program Cinema 4D. Learn all about particles and deformations, planes and cylinders, how to build a leaf, how to run the wind emitter, how to form a flag, and how to integrate all the processes.

Did you know that you can tell whether rare cards are inside of a booster pack justby the pack's weight? Scaling is a method of finding rare Yu-Gi-Oh (YuGiOh) playing cards.

In this video the instructor shows how to choose options on a batch file. In a batch file if you write the command '@ echo off', the person running the batch file cannot see the commands being executed. You can use the 'if' condition to make the program execute either of two commands depending on the condition. While writing the if statements make sure that there is space between the 'if' and the '%' sign. If you write 'shutdown -t 30' command in your batch file, then the batch program when r...

Home improvement expert Danny Lipford helps you figure out a way to get the perfect hole depth when drilling. Watch this video tutorial to see how to make an easy drill bit depth gauge.
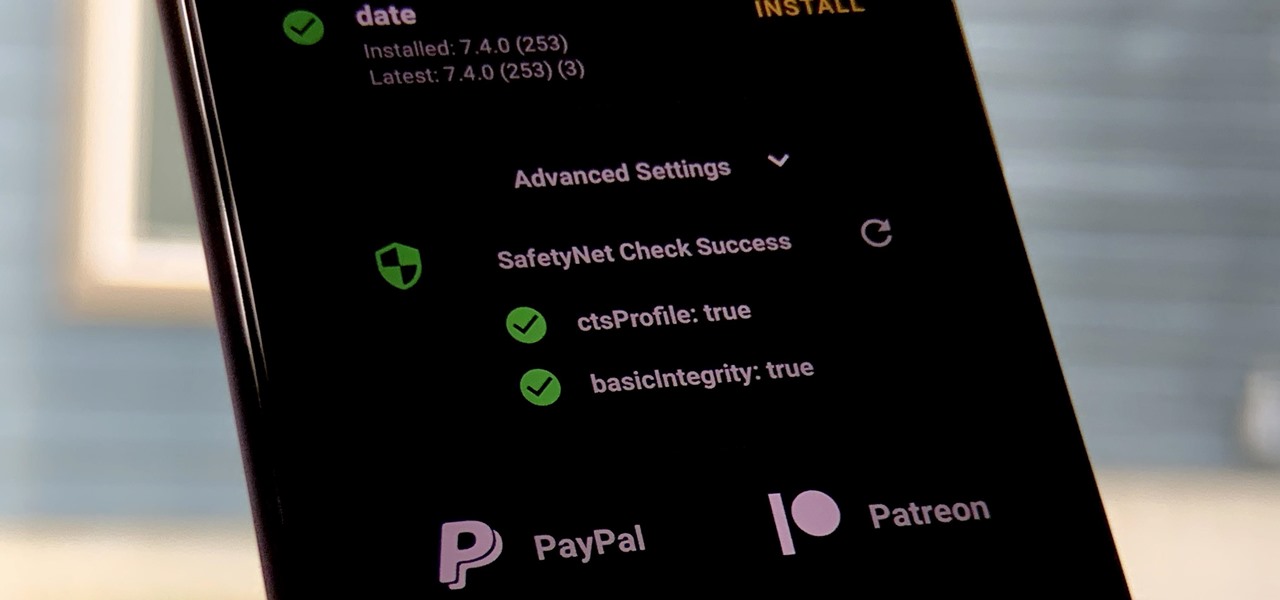
One of the longest-running cat and mouse games in Android has to be that of Google's SafetyNet feature and specific apps that can trip the flag. Many developers have resorted to using Magisk to create their modules since it can systemlessly pass SafetyNet in most cases. However, EdXposed is having some issues passing SafetyNet right now, which affects more than just your mods.

To be honest, the Mail app for iPhone had always been somewhat forgettable. It lacked many of the features that made third-party clients like Spark and Edison better, but with iOS 13, the gap between Mail and its competitors is much smaller. Apple updated the layout and added many new features to its native emailing app, and that may be just enough to get you to switch back.

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

Wargaming's World of Tanks — the popular multiplayer online war game — teamed up with The Tank Museum to create an augmented reality experience like no other. Alongside several German tanks that are part of the exhibit, visitors can use Microsoft HoloLens and Google Tango technology to explore a rare Stürmtiger tank inside and out.

Hello, everyone! If you haven't read the recent announcement on the official release of the Null Byte suite, I suggest you do so. This is going to be a quick tutorial on how to download and install the suite so you can see our communities genius. So, let's get started!

When an album sells a million copies, it gets certified as platinum and cements itself as one of its generation's biggest hits. When an album sells 10 million copies, it reaches diamond status and transcends generational gaps. But when an album sells well over 40 million copies, there's only one thing you can call it—Michael Jackson's Thriller.

Independence Day is right around the corner, and that means three things: fireworks, cold beer, and great food. I always love to cook festive foods for the Fourth of July, and I don't just mean the classics, like grilled chicken and brats. I mean foods that celebrate the Stars and Stripes: foods that are red, white, and blue.
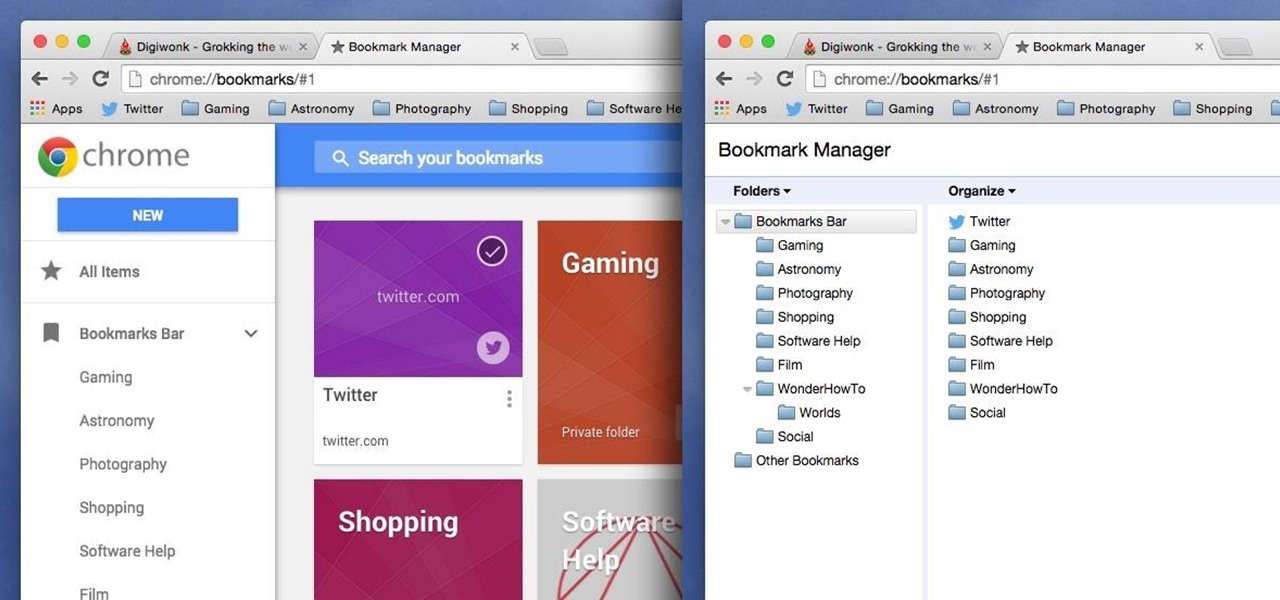
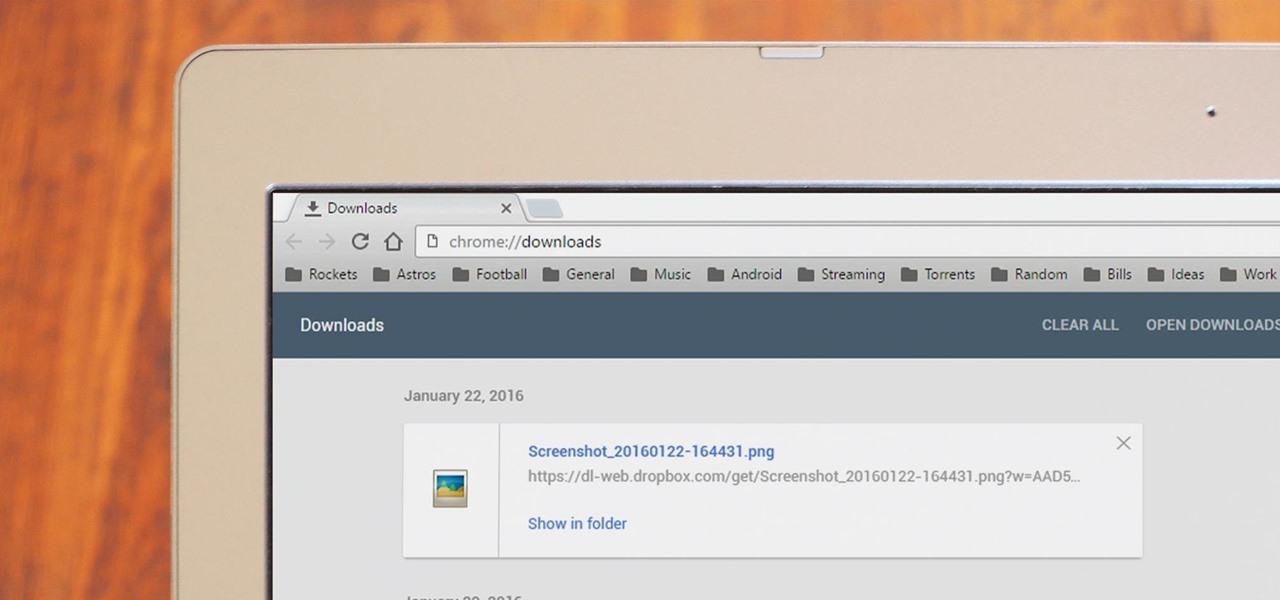
Chrome has been pushing out a lot of new changes lately, but not all of them are as good as they think they are. Earlier this year, there was an update that changed how user profiles worked, which made it harder to actually switch profiles. Luckily, there was a way to get back the old profile management interface, but now there's another "improvement" that you might want to change—Chrome's new Bookmarks Manager interface.
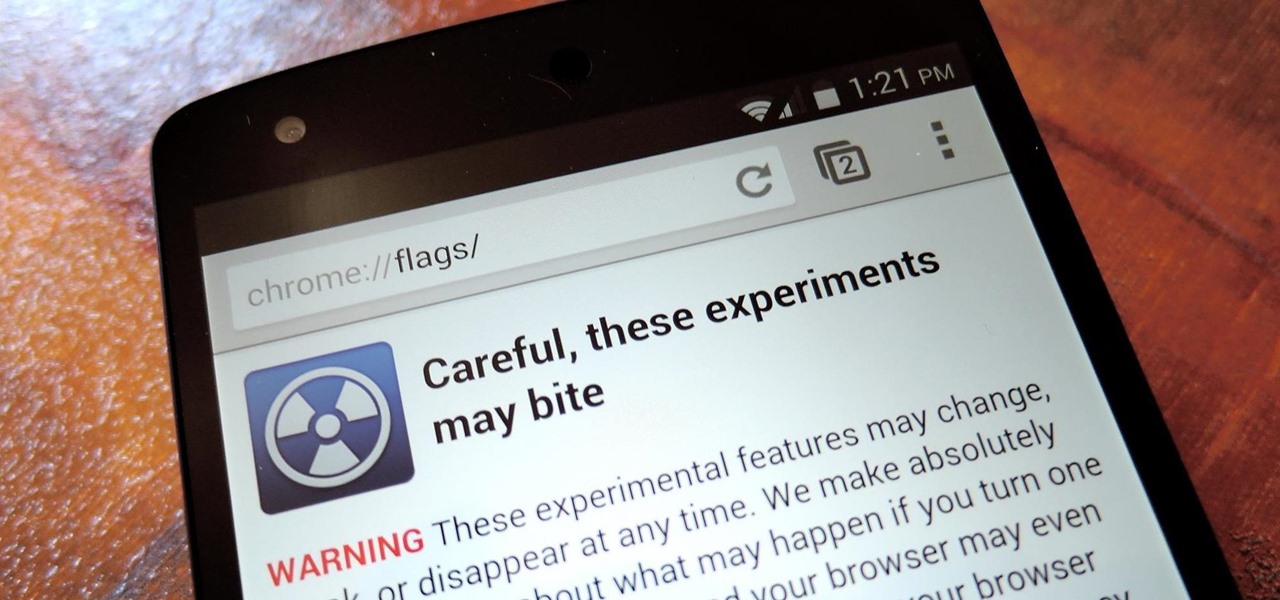
With the release of Jelly Bean, Chrome became the default web browser on Android. The wildly successful desktop browser was now fully entrenched in the world's largest mobile operating system.

One of the lesser known features brought along by the roll-out of Android 4.4 KitKat is the ability to screen record from within the device. This features isn't overtly obvious, nor is its implementation the most streamlined, but if you were ever looking for a way to capture video of what's happening on your screen, this is now the best way to do it.

Dark themes are all the rage these days, and both Android and iOS have system-wide versions. Many big-name apps and device manufacturers have already jumped on board the night train, and Google Chrome is no different. But the Chrome mobile browser offers various ways to enable its dark theme.

Alright so last time I gave you a homework assignment. This week we're gonna look at my version of the UDP-Flooder.

Knowing if your meat is cooked properly is both the difference between a delicious meal and an inedible one... and the difference between making your guests sick and keeping them safe.

Macs are generally highly power efficient due to, in part, the optimized sleeping schedule with OS X. Yet in certain scenarios, you might not want your Mac to go to sleep: downloading a huge file, reading a book, reviewing a spreadsheet, analyzing some content on the screen... the list goes on. To resolve this, you can go to System Preferences and mess with the settings, but this can be an annoying process if you need to do it often.

Welcome back, my novice hackers! I have tried to emphasize throughout this "Hack Like a Pro" series that good reconnaissance is critical to effective hacking. As you have seen in many of these hacks, the techniques that we use are VERY specific to the:

Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.