This is chemistry at its best! Europium is the chemical element (Eu) which was named after Europe. Dysprosium (Dy) is a rare earth element of a metallic silver luster. Watch this science video tutorial from Nurd Rage on how to make europium and dysprosium nitrate salts with Dr. Lithium.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.
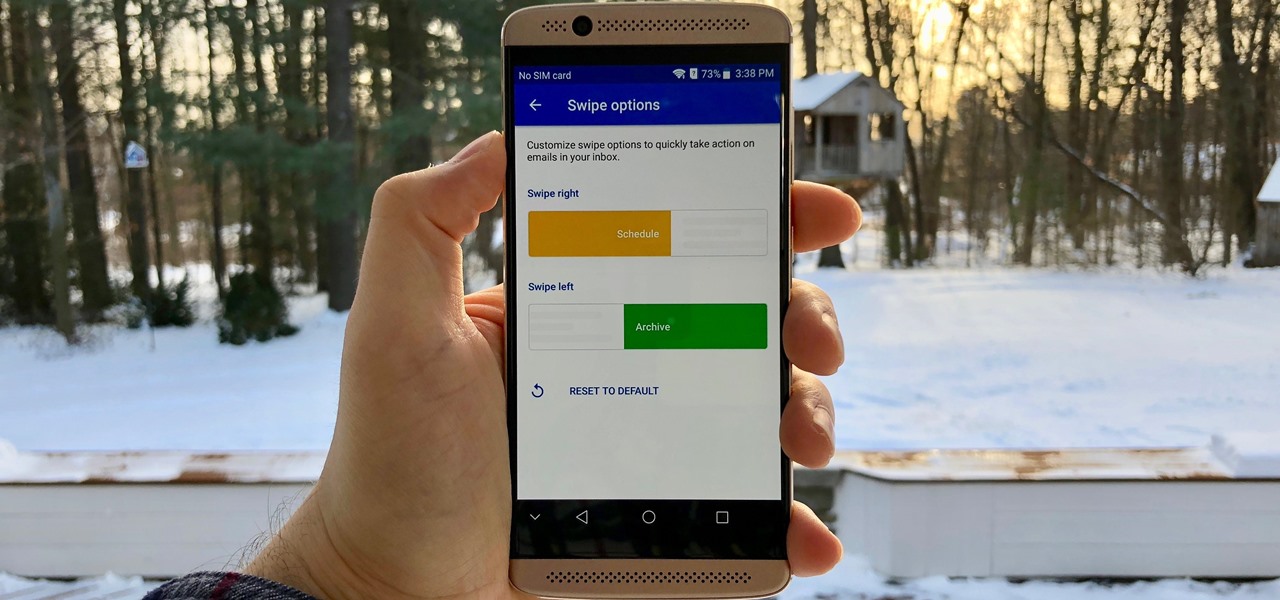
Swipe actions are an integral multitasking feature of any good email client, and Outlook is no exception. The application allows for two swipe actions at a time, but offers seven total options for those actions. We'll show you how to choose which actions go with which swipes to best tailor the app to your needs.

An attacker with shell access to a Linux server can manipulate, or perhaps even ruin, anything they have access to. While many more subtle attacks could provide significant value to a hacker, most attacks also leave traces. These traces, of course, can also be manipulated and avoided through methods such as shell scripting.

Ever wanted to communicate with another driver on the road, but just didn't know how? Sure, you could flag them down by waving or honking at them, but that assumes that they're in close proximity, that you have a unobscured path, and that they're paying attention. And if you're in a fit of road rage, flagging them down probably isn't the best idea for either of you.
Google continues to be the most commonly-used search engine for a reason. While continuing to stay ahead of the pack with advanced semantic search functions, Google even introduced Knowledge Graph results that offer key information without ever having to click a search result.

Being politically correct on social media sites is super boring. I've had my fair share of rage tweets and angry Facebook posts with some colorful wording, but sometimes using and F-bomb just gets the point across better. Now that Facebook is pushing out their new Graph Search, it might be time to clean up your profile. FaceWash is a web app that searches your Facebook profile for common bad words. You will need to give the app permission to access all of your wall posts (or course). Once acc...

Summer is coming so start saving your popsicle sticks (or more conveniently buy them from a craft store) to make your very own mini American flag. This is a great activity to take into the class room or just to pass the time on a summer’s afternoon.

Cloth is an essential part of almost any 3D modeling project involving people. This video will show you how to properly use the cloth modifier in 3D Studio MAX to create the waving, tarnished American flag shown in the thumbnail. This tutorial does NOT feature Reactor, the in-program physics engine included with 3DS MAX, only the actual 3D Studio MAX cloth modifier.

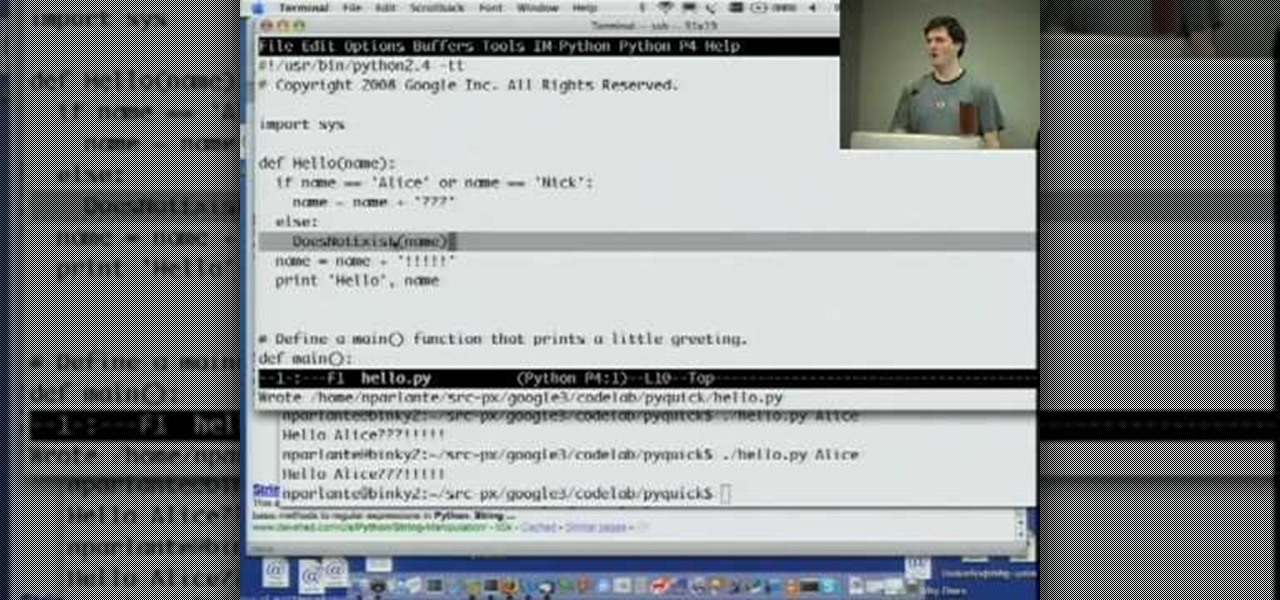
Welcome to Google's Python Class – a seven-segment, two-part free virtual class for people with a little bit of programming experience who want to learn Python. The class includes written materials, lecture videos, and lots of code exercises to practice Python coding. The first exercises work on basic Python concepts like strings and lists, building up to the later exercises which are full programs dealing with text files, processes, and http connections. The class is geared for people who ha...

Catching sight of a hummingbird floating from flower to flower is one of those rare gifts from nature. In this quick and easy guide, use a little bit of science and learn how to make a hummingbird feeder that will attract all the birds in the yard.

Mr. Paul Righetti teaches us a Santa Maria BBQ tritip lesson. The beauty of Santa Maria Style barbecue is that it delivers big flavors while being relatively easy to prepare. You can even take some flavorful shortcuts with Santa Maria Style Barbecue products by Susie Q,s Brand and Cowboy Flavor, among others. So fire up the grill and let'€™s get started!

If you've ever needed to prove you have remote access to a device, or simply want a way to convince someone their computer is haunted, SSH can be used to make a device begin to show signs of being possessed.

EternalBlue was a devastating exploit that targeted Microsoft's implementation of the SMB protocol. Metasploit contains a useful module that will automatically exploit a target, as long as it's vulnerable. But what if we wanted to exploit this vulnerability without Metasploit holding our hand? It can be done using a Python file to exploit EternalBlue manually.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

Battery drain is a major pain point for Android users, though that promises to change thanks to Android Pie's new Adaptive Battery feature. But Google hasn't said much about the inner workings of this feature, only publicly stating that it uses AI to boost battery life. So we dug in to find out what's really going on under the hood.

Market boxes are an integral part of the player experience in Animal Crossing: Pocket Camp, but using them effectively can be a tricky task. The item-trading tool between human friends is the locale for both junk and diamond-in-the-rough deals, and it can greatly increase the number of bells you earn if you play your cards right.

In the US, ticks can spread several pathogens in one bite. A new test offers physicians the ability to identify what infections ticks are carrying and can detect if one of the pathogens could be the spreading Powassan virus.

The culprit probably wasn't what doctors were expecting when a 57-year-old man in Hong Kong came to the hospital. The patient was admitted to the intensive care unit in critical condition. A clue to the cause of the infection would lie in the man's profession—he was a butcher.

Where in the world did it come from? All of a sudden, one day, someone had an infection with flesh-eating bacteria. It captured headlines and worldwide attention because it was such a severe, strange, uncontrollable, and really disgusting condition.

In this video Dave shows his unique way to grill fillet mignon. Dave begins the video with a brief history of fillet mignon. Dave says his unique way is easy as long as you follow his simple steps: 1) Allow steak to come to room temperature before putting it on the grill. This allows the cooking time to be a lot more consistent, and you won’t have a very cold middle with an overcooked outside. 2) With a great fillet mignon cut, do not over season. He adds just a little salt and coarse groun...

Check out this episode of Brian Brushwood's Scam School from Revision3 to find out how to pull the best cons, bar scams and magic tricks. It's rare to find a trick that you can actually fool yourself with...and that's exactly what you get with this episode!

Micro misters allow for low volume of water over a wide area. They give good moisture coverage. Systems can be pulled up, changed and made into what you need it to be. Keep potted plants separate from other plants. They should have their own system. There is a system to encourage growth of root systems of various plants. Shrubs get two emitters in case one clogs up, the plant still has moisture. Having the water at the base of the plant limits weed growth. There is a temporary system to get t...

Fourth of July is near, which means we'll soon be seeing an influx of red, white, and blue flags, banner, and of course patriotic sweets for those who indulge in the foodie side of the holiday.

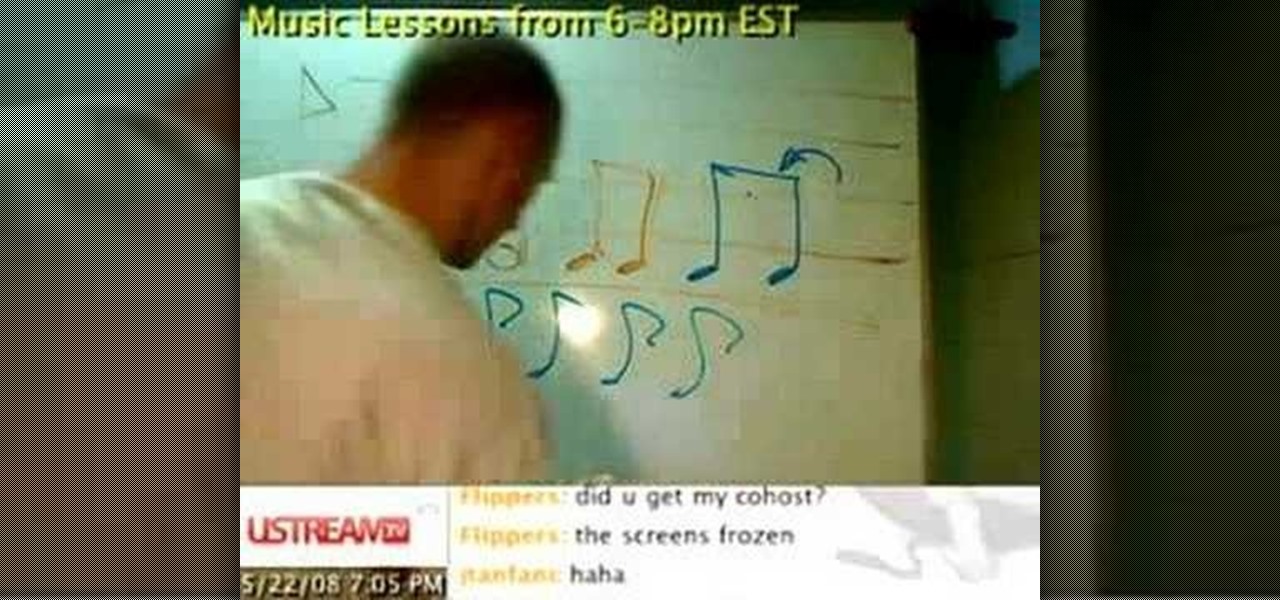
Connecting the flags on eighth notes, sixteenth notes, etcetera, is very important to neat, legible music. This how to video teaches you when to connect the flags in the music notes. Learn how to read and write music better with this music theory tutorial.

Dr. Aaron Katz explains what red flags men need to watch out for that could indicate prostate cancer and also explains what the PIN test is and how it relates to prostate health.

White is the traditional American wedding gown color, so why not match your makeup with your dress? Many brides go with a natural, flatteringly neutral makeup look when walking down the aisle, but silvery white eyeshadow is a steely yet gorgeous alternative.

Sunny Anderson from the Food Network creates a dish that spans the gap between winter and spring and combines comfort food with fresh, bright, and spring-like flavors. The main attraction is sliced herb-crusted roast beef with horseradish cream sauce. To begin, preheat your skillet, add olive oil to barely cover the bottom, and season the roast with salt and pepper. Sear on all sides. In the meantime, make the herb crust in the food processor. Combine 5 cloves of garlic, handful of parsley to...

In this video, Steven Raichen demonstrates how to make a quick and delicious meal of Argentine "gaucho grilled" filet mignon with grilled eggplant and peppers. In his travels around the world, Raichen became fascinated with the rich, slightly smoky flavor of steak cooked in the traditonal Argentine method, and decided to find a way to replicate that flavor quickly and easily. To do this , Raichen uses a traditional wood-burning grill from Grillworks (to purchase, contact Grillworks at 202-758...

Curtis Smith, Extension Horticulturist, and Jeff Hart of the Albuquerque Parks Department discuss the types of trees that grow in Albuquerque.

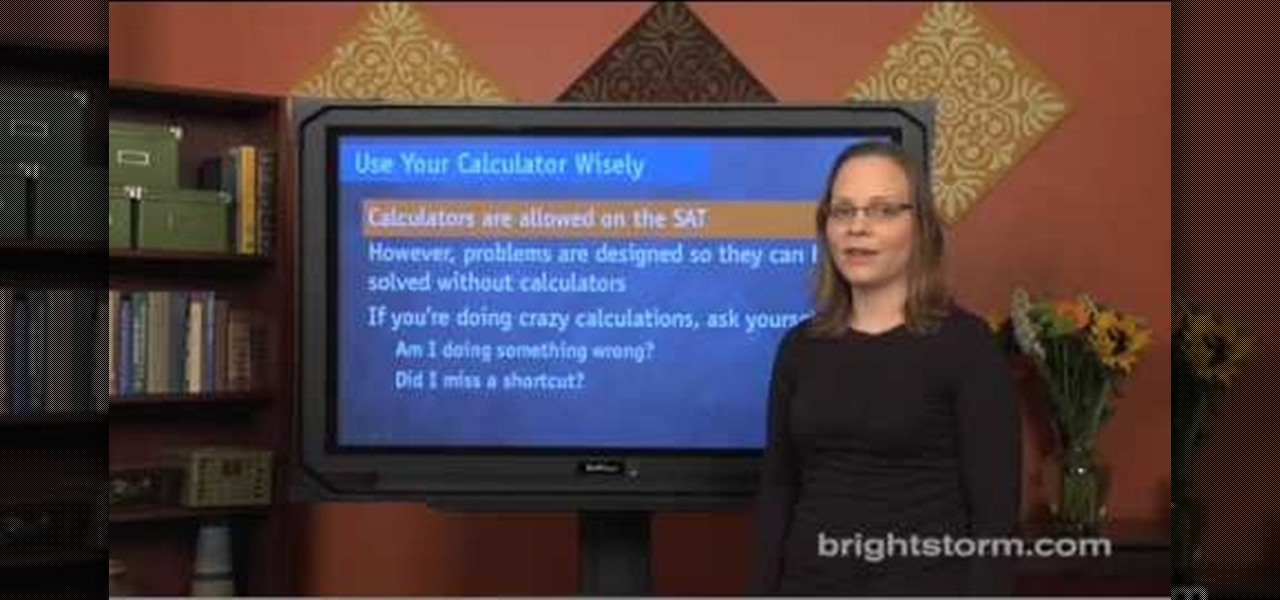
How to prepare for the math section of SAT:Eva for brightstorm2 gives us a few quick tips to solve the math section in the SAT test. They are simple, easy yet crucial to help you get through the math section. Let us begin with the basics. Basic are simple tips like read carefully, use your calculator wisely, use all the information given, do not worry about formulae and symbols, tackle the “always”, “never”, “must and “could and “can” problems. To explain them in detail; you should pay attent...

Coarsely crush peppercorns in mortar with pestle. Season steaks with salt. Sprinkle peppercorns over both sides of steaks, pressing to adhere. Heat oil in heavy large skillet over medium-high heat. Add steaks and cook to desired doneness, about 3 minutes per side for medium-rare.

Make London broil grilled steak by following these easy steps! Enjoy cooking! London broil is a preparation, not a cut of meat. It is a steak that is pan-fried (and therefore not grilled) over high heat only to medium rare, beyond which point it becomes inedibly tough. It is a useful preparation for lean, tough cuts of meat, such as flank steak, shoulder, and round. To the less pure, London broil is a preparation that involves marinating a flank steak, then grilling, broiling, or pan-frying i...

Set the packaged roast on the kitchen counter. Let the roast warm to room temperature for an hour or more. This helps it to cook evenly.

Where the coin goes, nobody knows. Except you! You Will Need

Death by stingray is extremely rare, but getting hit with their barb still hurts like hell – which is why you need to learn how to play footsie safely with these sea creatures.

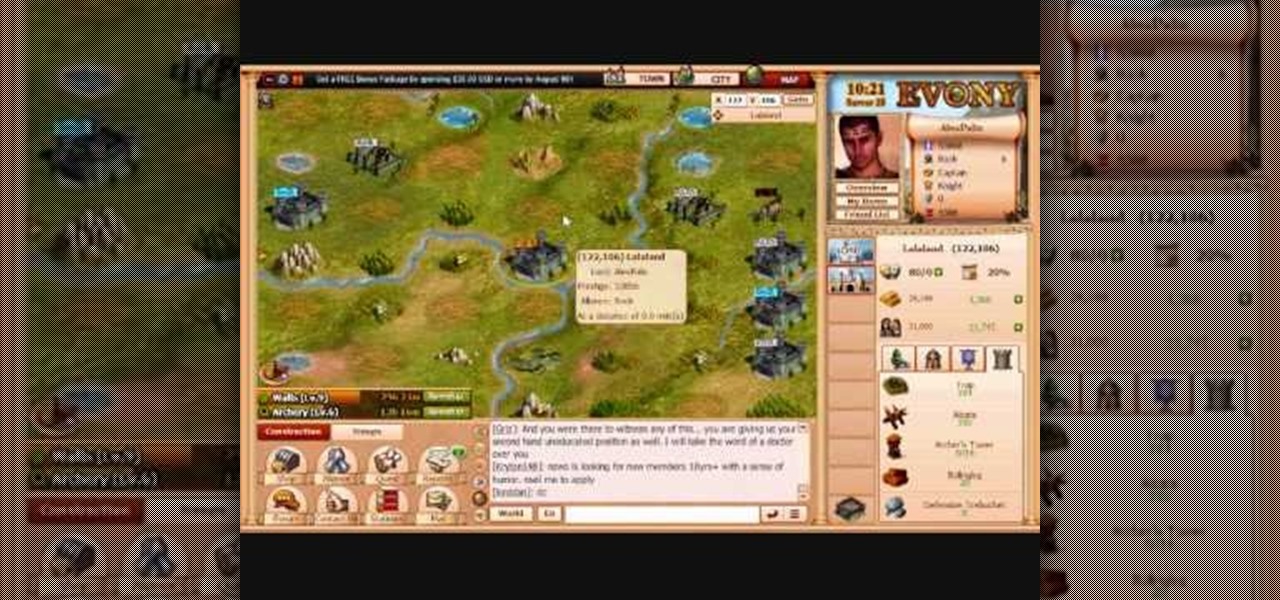
Learn everything you could possibly want to know about the internet, multiplayer game Evony with help from alexstewart2. Watch this video tutorial to learn how to farm rose, lion, cross, and nation medals in Evony.

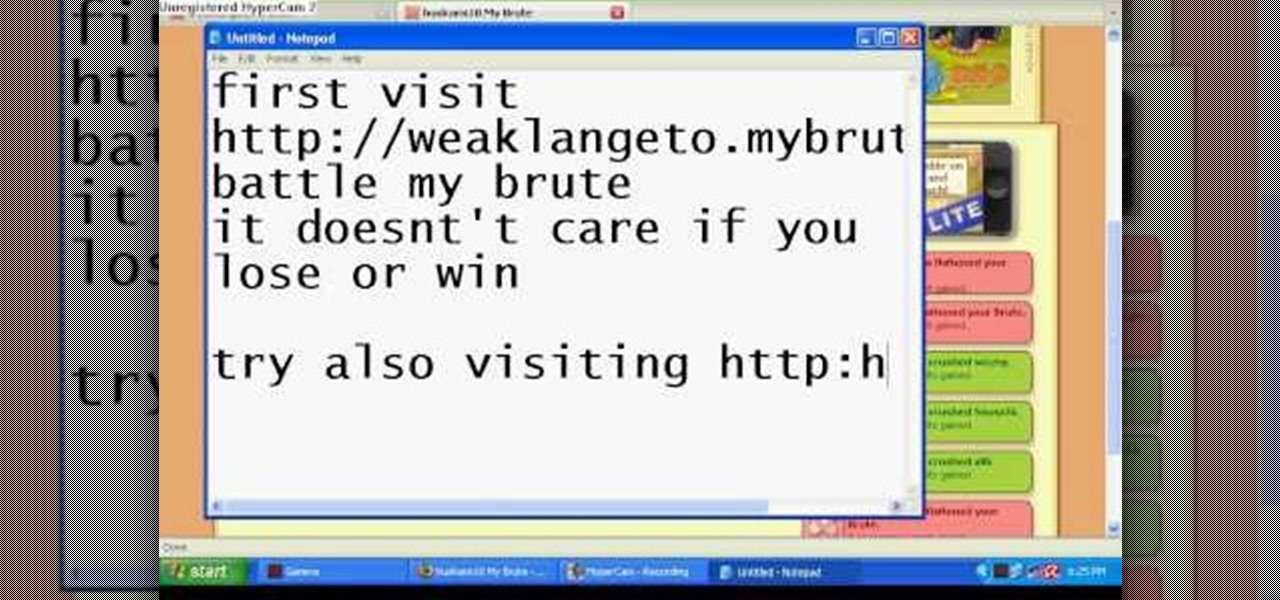
Hack mybrute with this mybrute cheat. MyBrute hacks, cheats, tricks. Watch this video tutorial to learn how to hack a wolf or bear in MyBrute (07/26/09). Without Cheat Engine!

Summertime is grilling time! For all you kebob/kebab/cabob lovers, watch this how to video on how to make delicious grilled spiced lamb kabobs. Perfect for your summer backyard BBQ!

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.