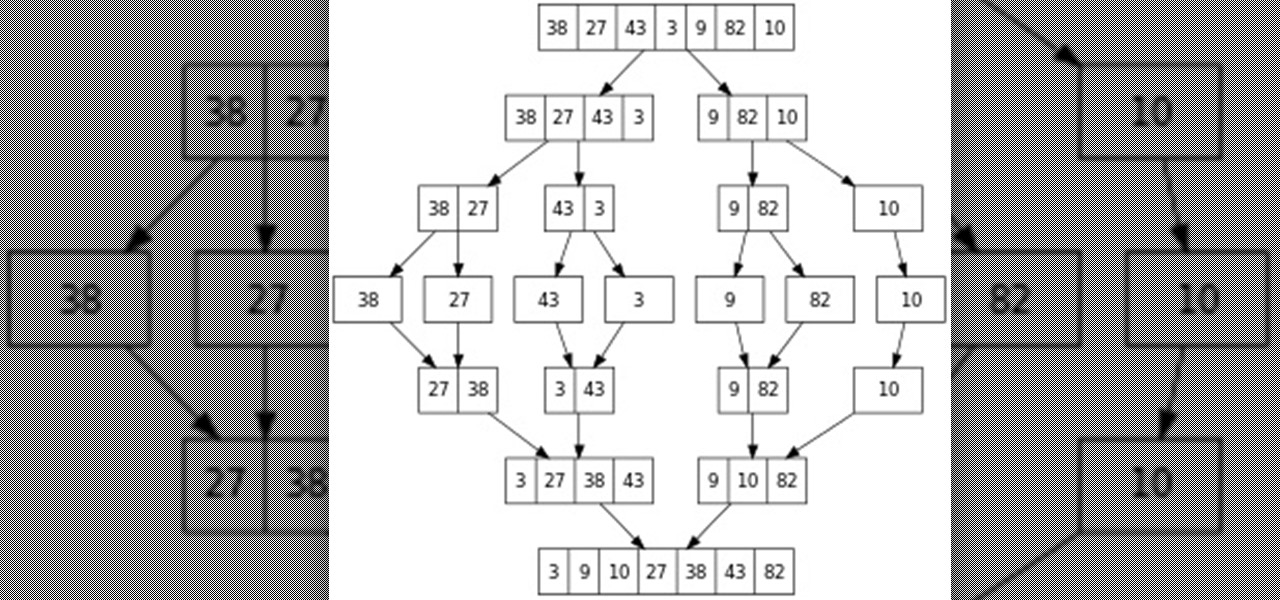
Sorting (Part 7.0): Merge Sort
Hello everyone! This is part 7.0 of my Sorting series. I know, I said last time that there would be a 6.1, but not just yet!


Hello everyone! This is part 7.0 of my Sorting series. I know, I said last time that there would be a 6.1, but not just yet!

Welcome back, my neophyte hackers! Metasploit is such a powerful tool that I can only scratch the surface of its capabilities here. As it has developed over the years, it is now possible to use Metasploit for nearly everything from recon to post exploitation to covering your tracks. Given its versatility, every aspiring hacker should have at least a tentative grasp of Metasploit.

Welcome to another C tutorial. We will be looking at arrays, discussing what they are, when they are used and their special relationship with the char variable. Let's begin.

Greetings all. Before I get into the tutorial, I would like to mention that I am fairly new to Null Byte (been lurking for some time though), and what really appeals to me about this place is its tight, family-like community where everyone is always willing to help each other and the constant search for knowledge that inhabits this subdomain is a driving motivator for me to join in. I'm glad I arrived at the right time. Anyway, wipes tears (not really)...

Ahh, coffee. That first sip of hot goodness in the morning is glorious, isn't it? There are days when you need it straight up: No extras, please. But what about those moments when you need a little something else? When that flavored French vanilla, hazelnut mocha, blah blah blend just doesn't cut it and you want a truly special flavor in your morning joe?

Hi everyone! In the previous part of this series we introduced remote code arbitrary execution via buffer overflows using all of our past experiences.

Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers with over 60% of the market. In addition, Linux and Unix servers are the operating system of choice for major international corporations (including almost all the major banks) throughout the world.
This how-to is for everybody who faced the problem of intercepting personal data sending through the Internet and is looking for fast and secure method to protect his activity in the global network.

Welcome back, my neophyte hackers! I have already done a few tutorials on password cracking, including ones for Linux and Windows, WEP and WPA2, and even online passwords using THC Hydra. Now, I thought it might be worthwhile to begin a series on password cracking in general. Password cracking is both an art and a science, and I hope to show you the many ways and subtleties involved.

United Arab Emirates is the cosmopolitan country that offers various attractions for tourists across the world. This country has buildup its image as one the fastest growing country of this region. Besides visiting worth seeing places, travelers can also enjoy tasty traditional food of UAE across the country. Whether you have chosen Dubai, Abu Dhabi, Ajman or Ras Al Khaimah, you will get the chance to enjoy best traditional food everywhere.

In this video Jennie shows us how to make a perfect spiral paper rose. All you need for this is a piece of 6X6 inches of paper, scissors, some glue and, if you really want to be creative, some ink. For starters you're going to need a 6X6 inch piece of card stock. Jennie chose a double-sided card stock because she thinks it will look more interesting but you can also use a plain piece of paper. The first step in creating your rose is making a spiral patterned cut alongside the paper. The ideal...

Nothing says you care like a hand-made card. Show that special someone what they mean to you or just have fun with this cute arts and crafts project. Get your markers and colored pencils. Get your glitter and glue. Get creative.

There are plenty of films out there with baseball bats, but if you want your bat to explode on impact, you'll have to make it yourself. A smashable baseball bat is perfect for any gangster flick or sports movie. Watch this video tutorial to learn how to make a breakable baseball bat movie prop.

Whether you’re headed for a half-pipe or your driveway, always be safe. Wearing protective gear and taking a few precautions can help prevent you from landing in the ER. Watch this video to learn how to practice skateboarding safety.

Need a way to keep the kids busy on a rainy day? Making a pop-up card is quick, easy, and will entertain them for hours! Watch this video to learn how to make a pop-up card.

Getting a good break in life is always nice. But when you're playing pool, it's essential. You Will Need

Puris are such a treat to the eyes and to the taste buds. The sight of a well puffed up puri excites everyone (not just kids). Some great combinations are ‘Aloo-Puri’, Chole-Puri’ or ‘Halwa-Puri’. It is made on special occasions from religious functions to weddings to birthdays. Enjoy this awesome South Asian unleavend bread that will take your breath away! Watch this how-to video to learn how it is prepared.

Let our expert show you how to do super scary Vampire Halloween makeup! A vampire Halloween costume is easy, but getting the makeup right is key. Our expert will show you how to apply the various layers of vampire makeup, how to add gray shadows, how to add creepy bite marks on your neck and even how to add fake blood special effects to your lips and chin. This is great makeup for a fun Halloween party or even a Haunted House!

A bouquet of fresh roses is wonderful but real roses soon fade and die. Make a rose that will last forever, or at least a lot longer that a freshly cut one. Give your rose to someone special or use it as a decoration.

Impress everyone by bringing a beautiful homemade tart to the next celebration. You can use seasonal berries or even other fruits to create a colorful and flavorful dessert that will make any occasion seem extra special. With its rich pastry cream and tangy fruit wrapped in a flaky, buttery shell, the fruit tart is a classic dessert. Make this version with one or more of your favorites berries.

You don't have to wait for the carnival to come around. You can make this special treat any time you like at home. It takes a little bit more time than at the fair but will be worth the look on party guests’ faces when they realize you've just made this counterintuitive dessert.

The makeup artist Julia presents this tutorial in partnership with VSP vision care in order to demonstrate makeup tips for people wearing glasses or contact lens.

A hand-decorated cake makes any occasion more special. This series has expert Karen Weismen showing you how to decorate a cake like a "gift box".

A side effect of the COVID-19 pandemic is that small businesses are suffering from forced closures and social distancing, but game developer Niantic has a solution.
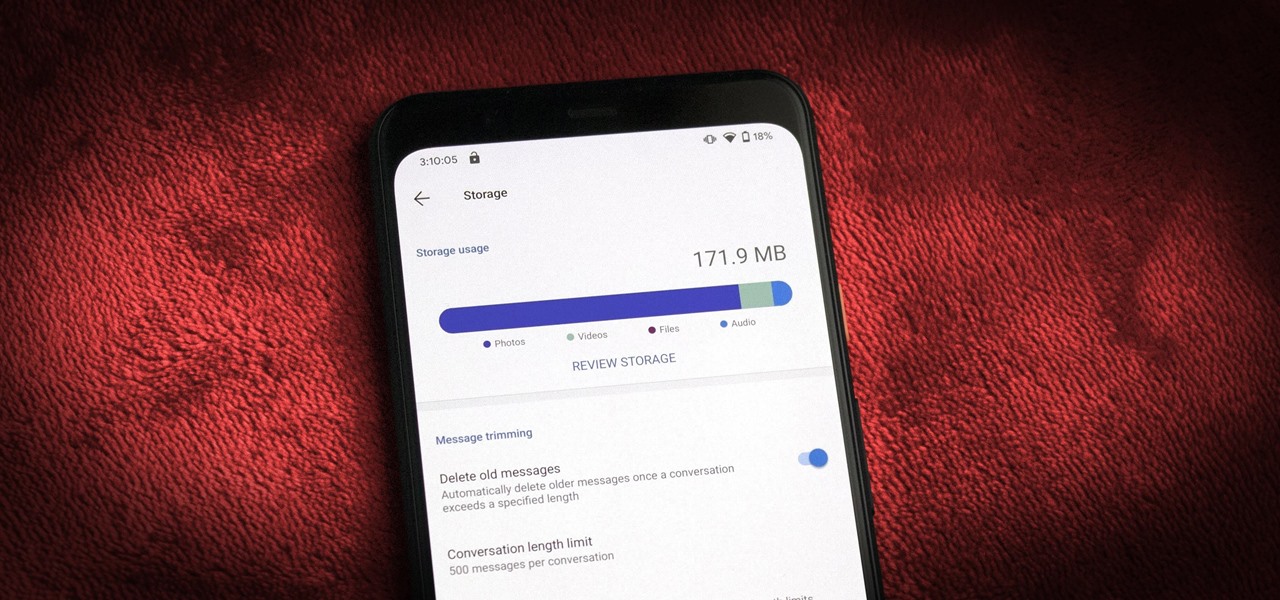
Thanks to backups, Signal conversations can span over multiple years and multiple phones. These archives can get rather large as you share photos, videos, and other files with friends. But between the other apps and large files on your phone, you might not be able to afford to keep all those messages.

Alternate US history is the go-to move for hot new cable and streaming shows, from HBO's Watchmen to Hulu's The Handmaid's Tale, reimagining how things might have turned out is an endless well of narrative inspiration.
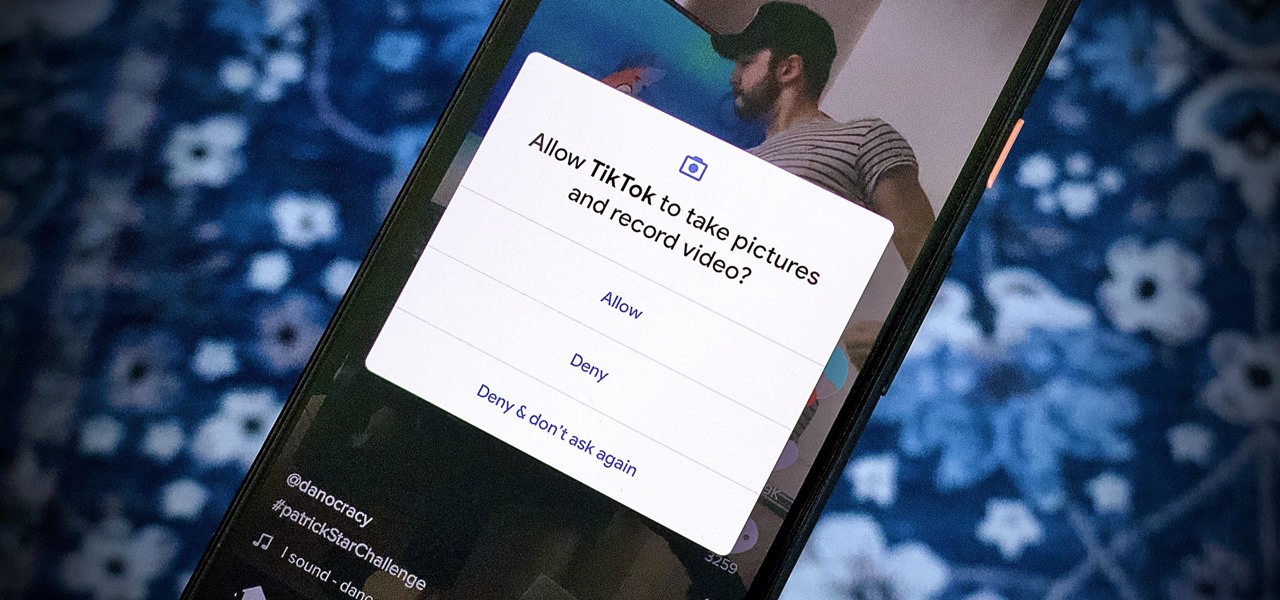
We're thinking more and more about our digital privacy these days. When we first started using smartphones, we'd download apps with reckless abandon, allowing permissions lists as long as novels in order to play free games. Now, we know that apps have access to things like our cameras and microphones, even when they shouldn't. Luckily, taking away these permissions is easy.

Snapchat is probably used to Facebook copying its features by now, but Apple borrowing a page out of its playbook is likely a bit more surprising.
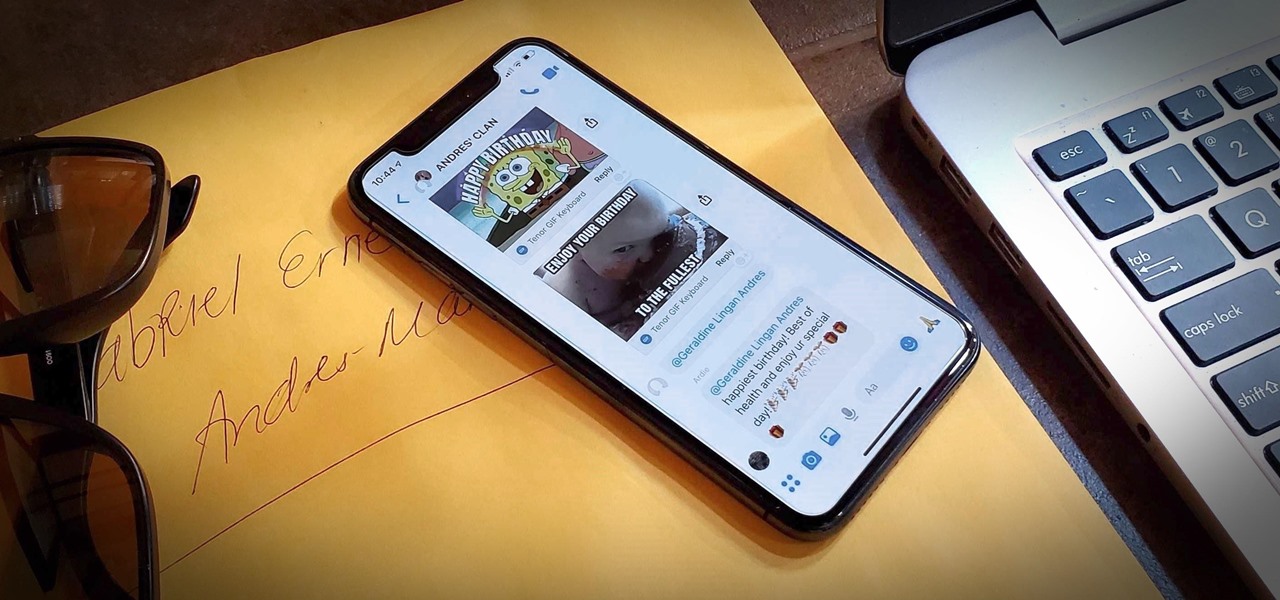
Group chats in Facebook Messenger can devolve into outright noise pollution as people chit chat randomly and bombard you with distracting notifications. Unfortunately, leaving the group outright alerts everyone inside, so if you want to get out of the thread unnoticed, what exactly can you do?
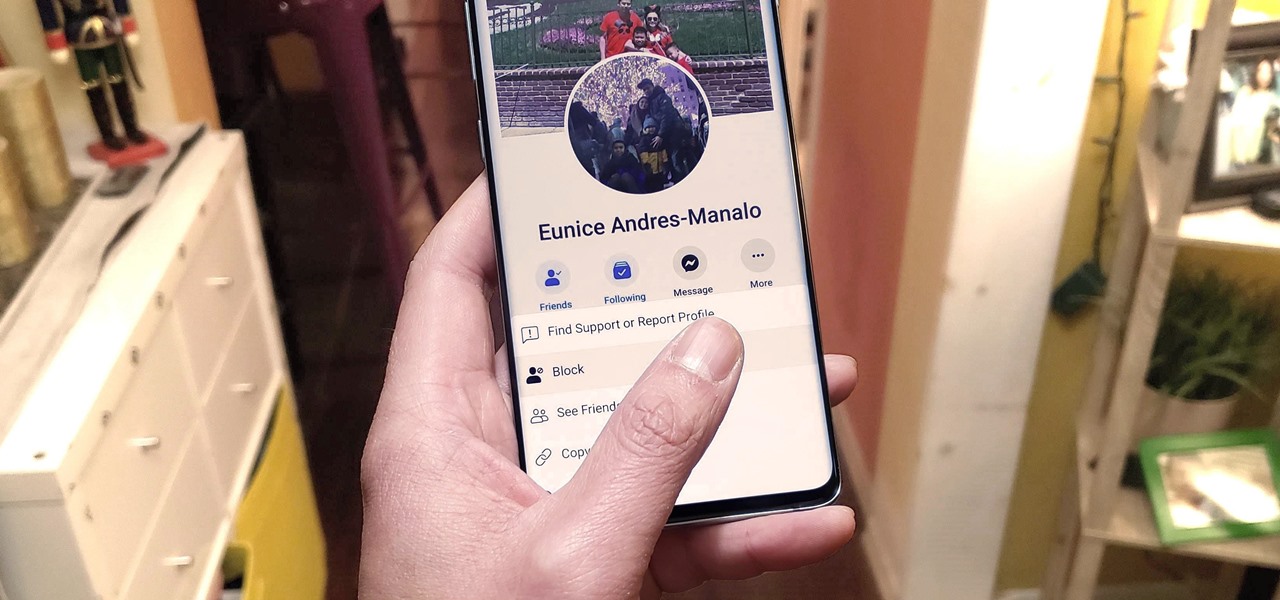
It's easy to block a person or a website from appearing in your Facebook feed, but it isn't as easy to undo that. Thankfully, there are still ways to unblock people directly from your phone.

With No Time to Die, the 25th installment in the James Bond saga, arriving in April and Black Widow, the first solo film for the Marvel Cinematic Universe's own secret agent, following a month later, what better way to get in the espionage mood than some augmented reality spy gaming?
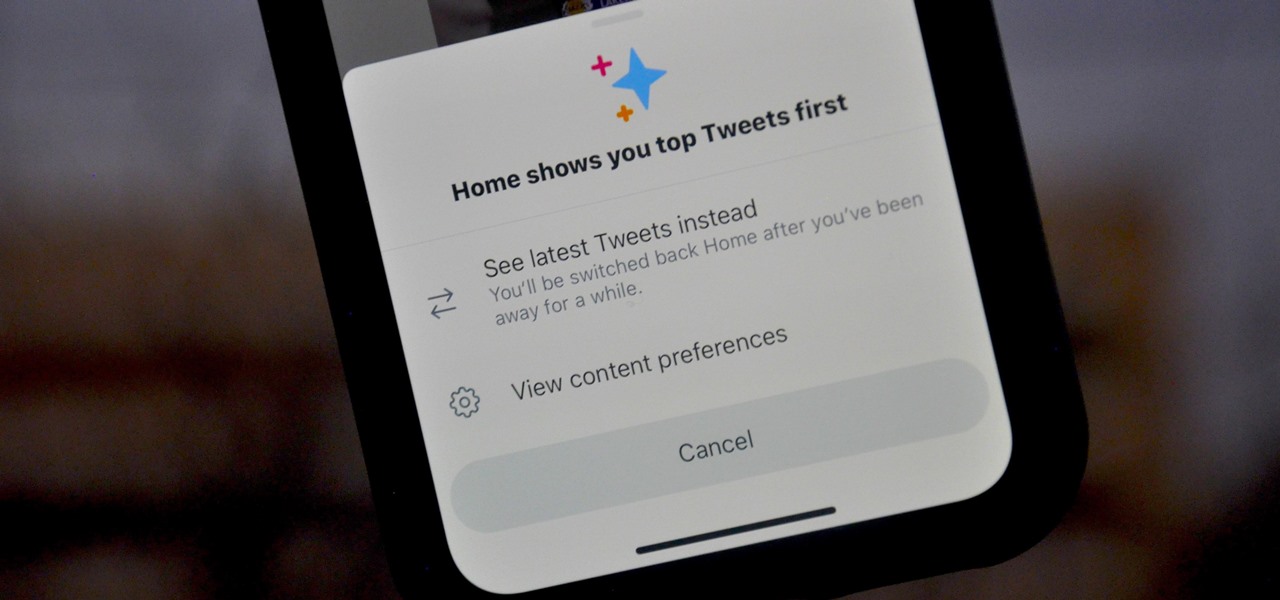
If you're tired of the so-called "top" tweets appearing first in your Twitter timeline instead of only the latest from the people, companies, and bots you follow, there's a way to get rid of them.
The Google Pixel's camera is a status symbol of sorts. When someone sees you with one, you become the photographer of choice for social events. And where do those photos end up? Social media, of course. It's how we share our lives now, and the smartphone camera defines how we approach that.
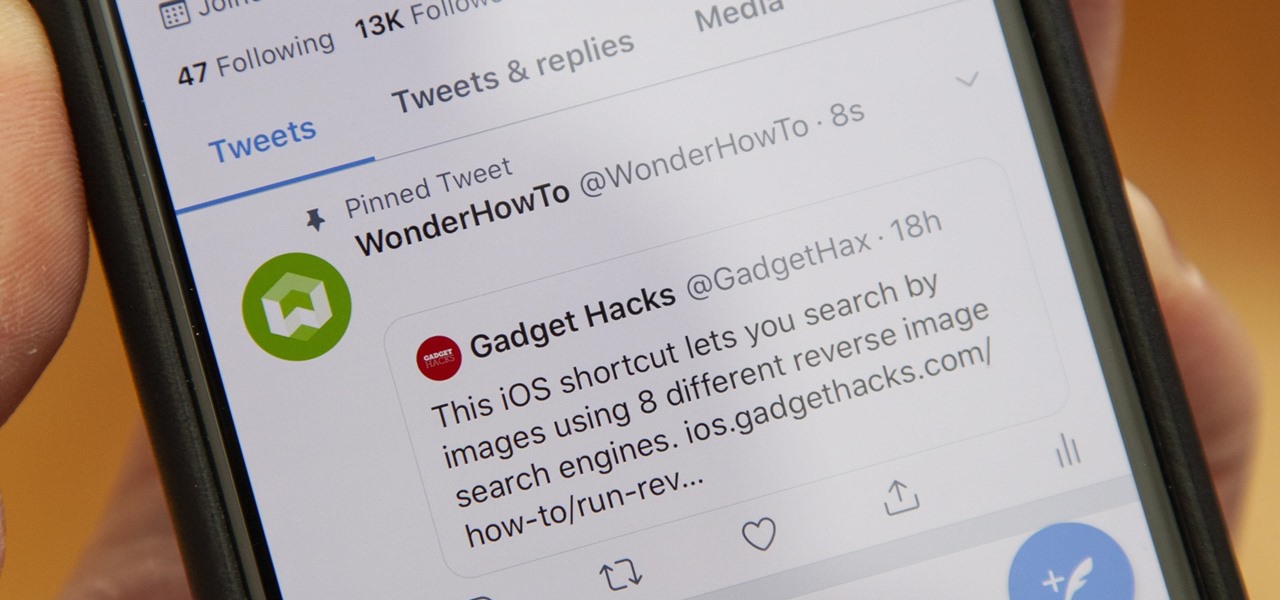
On Twitter, you can pin one of your tweets or replies to your profile, so it's the first post people see when they visit your page. However, Twitter prevents you from pinning someone else's tweet. You can't even pin something you retweet. There is a clever workaround, though, and it also works for posting empty tweets.

There's definitely some malware-ridden apps on the Play Store. When it comes to the third-party apps you've connected to your Google Fit account, some have a crazy amount of permissions they have no business accessing. For example, you probably don't want a heart monitor app having access to your personal location data.
Every iPhone since the 5S has come equipped with a microchip called a motion coprocessor, which collects data from integrated accelerometers, gyroscopes and compasses, and can then transfer that information to fitness apps that track physical activity. Essentially, the chip knows whether you're running, walking, sleeping, or driving — but what if you don't want it to?

The HoloLens 2 hasn't even reached most of the market, but it's already a big-time TV star. Microsoft's augmented reality device made its primetime debut on FOX TV last night on an episode of the hospital drama The Resident.
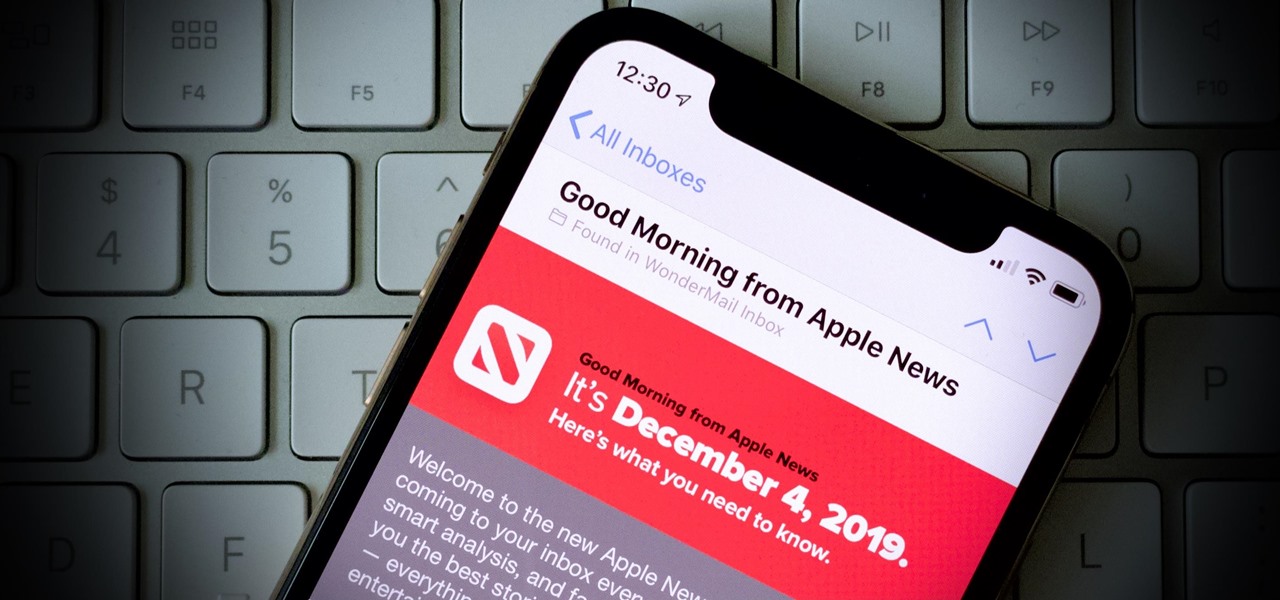
While the App Store is filled with news aggregators, Apple News is a solid choice when it comes to keeping up with current events. Apple recently made it easier than ever to stay informed, thanks to a daily newsletter sent straight to your inbox. The problem? It's unclear how to sign up for this newsletter, and it's equally unclear how to unsubscribe.

Pokémon, Google, and augmented reality go together like wasabi, soy, and ginger, and the trio has come together again for the release of the latest game from the Pokémon universe.

Starbucks is spicing things up ahead of this holiday season with a little augmented reality joy. This week the company launched its first Instagram filter, called Holijoy, delivered like an early Christmas gift and packing four seasonal lenses.