Humanity is standing on an infection precipice. As antibacterial resistant grows, we're running out of options, and a recent scary case of total antibiotic resistance is a frighting view of our potential future. In the end, it was septic shock that took the life of a 70-year old woman with an incurable infection. One of few such cases in the US, her death could nonetheless be the shape of things to come.

The presence of certain bacteria can indicate whether the vaginal tract is healthy or not. It could also impact the likelihood of acquiring certain sexually transmitted diseases, like HIV, a new study suggests.

Super Mario Run has been one of the most insidiously addicting iOS games to come out in recent years for iPhone. And now, as of March 22, Android users can get in on the fun, too.

Many new parents will tell you how hard it is to name a baby. Some have stories of how they knew what the name of their child would be from before conception, only to change their mind when they were born. Sometimes new babies can go weeks without a name since there is an endless selection to choose from.

Whenever I went to the grocery store on a mission for blueberries, I'd inevitably find myself staring at these weird little tomato-looking berries... and wondering what the hell they really were. Tomatoes? Berries? A weird science experiment? Then, I'd set a pint of blueberries in my cart and carry on, forgetting about them for the time being.

An average user's smartphone tinkering doesn't go much further than taking their phones out of the box, signing into their account, and installing apps. But some of us want more functionality and customizability than the basic experience provided by Android and iOS.

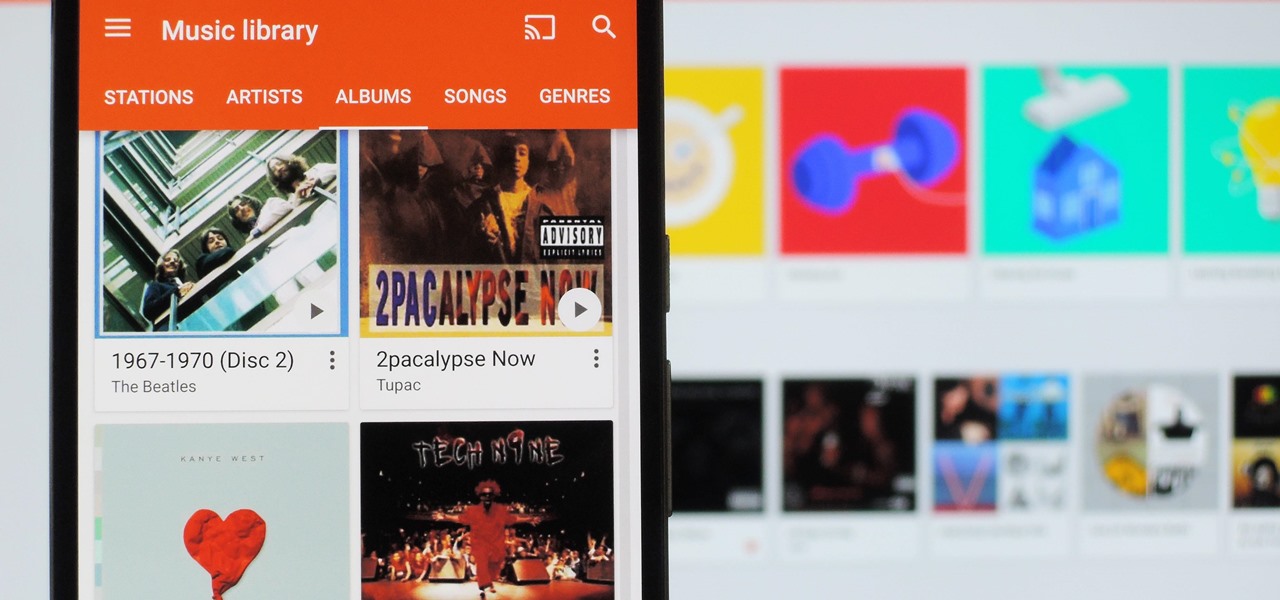
It's always a pain to make sure you have enough storage on your smartphone. Pictures and videos occupy a lot of space, so your music library has to take a back seat—otherwise, you might see that pesky "Storage Full" notification at any time.
Most of you lot would be aware what WPA/WPA2 is so I won't bang on about the encryption or protocols a great deal. In short WPA and WPA2 both have a maximum of 256bit encrypted with a maximum of 64 characters in the password. The encryption is really only 64bit but x 4 because of the way the authentication functions as a 4 way handshake.

I was on our new #nullbyte IRC channel when someone told me how tedious it is to install an OSX Virtual Machine on Virtual Box (I think it was wawa). We all know Linux rocks (gets acknowledgement from the crowd), but there are morons out there, multiplying at a never before seen rate, who use OSX. We at nullbyte should be prepared for anything and everything. So, in this guide I take you step by step to creating your OSX Yogemite VM.

If you think that "pawpaw" is just an affectionate name for your grandfather or a cute way of talking about your cat's feet, you're missing out on one of the most interesting fruits out there.

Welcome back my networking geeks. In this part we are going to keep discussing about IP Addressing and I hope after you finish reading it you will become an IP wizzard.

Social engineering is a pretty important item in a hacker's toolkit. In Mr robot there was a time, we saw Elliot using social engineering to gain access to his therapist's boyfriend's email and bank accounts by calling him and pretending to be someone from his bank, then Elliot asked him for some info that were really useful to gain access to his account, the target believed to be someone from the bank and gave him the info Elliot was looking for. But How Is It in the Real World?

Yes, screen savers are fun to look at for a few seconds, but those animations actually used to serve a purpose beyond simple entertainment.

Developing GUI apps in python is really cool. I ask those who understand the language to help convert some of the command-line or console programs or apps ( I mean programs that are useful to a hacker ) to GUI. I know GUI makes us lazy and not wanna learn but we should all know its fast. Today's tutorial is on p2p chat app I developed last week and decided to share it with the community since its kinda cool.

With the amount of time we spend glued to our smartphones, they could be considered a second job (if only we got paid). I spend a large part of my day scrolling through Reddit, Facebook, Instagram, and countless other apps, and burn through hours and hours without even noticing.

Barbecue season: it's the perfect time to play with fire, produce your best burger ever (until next year, that is), and find even more ways to make beer a part of your daily life. However, even a grilling badass occasionally gets stumped by minor BBQ problems. No worries: We've got solutions!

For some odd reason, the Netflix app likes to disable the Nexus Player's built-in screensaver. It doesn't use its own, it simply keeps your screen on indefinitely, which of course can lead to screen burn-in. This is not just an Android TV issue, as the Netflix app does the same thing on Roku and smart TVs.

Lemons and limes might be among the most useful fruits in the kitchen and even beyond. Their bright, tart flavor livens up just about any dish, while their mildly acidic nature makes them incredibly useful when you want to clean your house safely. We already knew lemons were great for keeping fruits and vegetables from turning brown, deodorizing garbage disposals, disinfecting cutting boards, and neutralizing odors. But just when we thought we knew all the ways that lemons can be used around ...

We've all been there. You can't decide what you want to eat and, even more confusingly, you want two distinctly different things, whether it's sweet and salty, Chinese and, well, cheese. Chances are when you're in this state of indecision, you also want to make this mythically satisfying meal really, really fast.

Hard as it is to imagine, there are people out there who loathe garlic and onions. Some might have allergies or medical conditions like IBS, or are supertasters (i.e. people who carry a certain gene that makes them extremely sensitive to how certain foods taste). Others might just be picky eaters.

Many people drink green tea for health reasons, and it's no wonder. This beverage is a superstar when it comes to antioxidant levels, and is being studied for its potentially curative properties on multiple health concerns, whether it's staving off the aging process or fighting cancer.

Welcome back, my novice hackers! There are SOOOO many ways to hack a system or network, which means you need to think creatively in order to be successful.

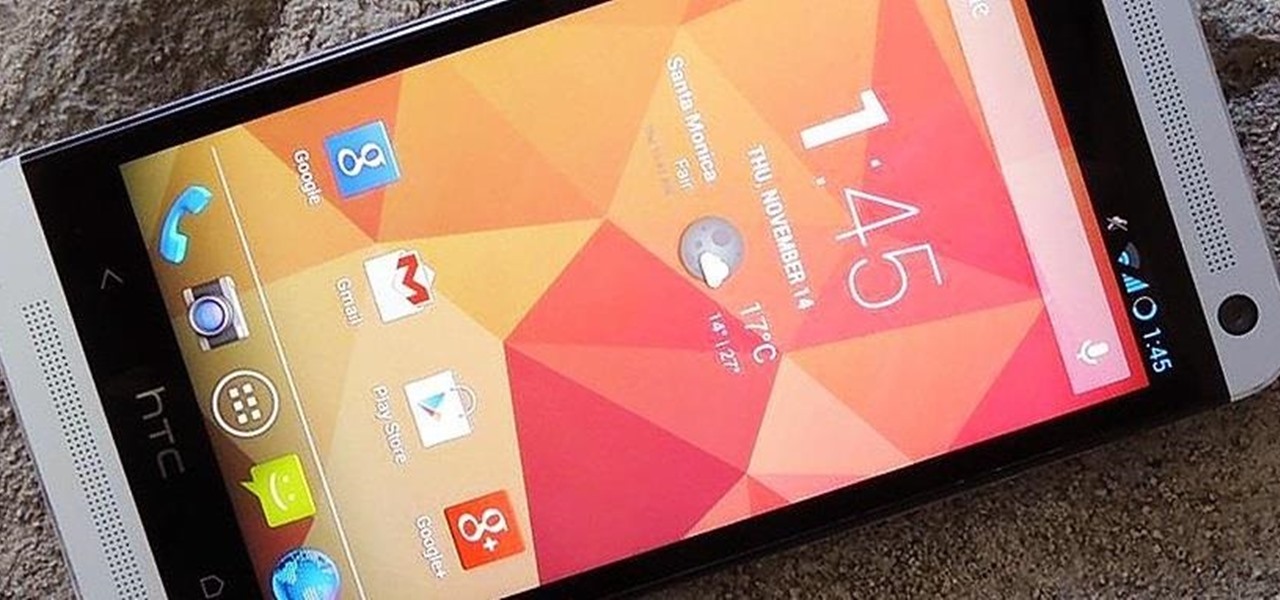
It's rare that a developer listens to the wishes of the masses, but that's exactly what CyanogenMod has done with their new CyanogenMod Installer, which automates the entire ROM installation process on your HTC One or other Android device. Previously, upgrading from the stock HTC One ROM to CyanogenMod required an unlocked bootloader, a custom recovery, the latest CM version, and Gapps. Let's be honest—unlocking the bootloader is a pain the ass, and probably the only reason stopping most peop...

Unless you're a pretty avid home cook, you probably don't know a lot about sous vide. Sous vide is a low-temperature cooking method where food is cooked in vacuum-sealed plastic bags in a water bath for a prolonged period of time.

No matter what device you have, Android lag will get you down. It's our little green robot's only major downside, and you've probably noticed it quite a bit on your Nexus 7 tablet. Apps open slowly, actions stutter or pause, and loading files takes forever.

Deep in the crevasses of the Songshan mountain range, an Indian dhyana master established the first Shaolin Monastery in 477 AD, seeking to spread the relatively new teachings of Buddha at the time. This monastery then bred the Shaolin monks, who are now popular for their incredible feats with Chinese martial arts, particularly with Shaolin Kung Fu.

Tea has been around for thousands of years, and as a result, tons of customs and ceremonies have sprung up around its consumption. Some cultures take their tea plain, while others put things in it. Sometimes there are special tea-holding vessels, other times not. Maybe there will even be special foods meant to be eaten with tea. However, in America, our appreciation of tea has waned. For many, iced tea is their biggest source of tea consumption, and it's imbibed with no ceremony whatsoever in...

There's something special about Laika Inc.'s Paranorman... Hey! Did you love Coraline? Are you interested at all in stop-motion animation? Well, watch this feature on Laika Inc.’s new film, Paranorman.

This video shows you how to add some smoke and muzzle type flash effects to video footage of a gun being shot. The video says it's using After Effects, but the software is really Adobe Premiere Pro.

I drop my smartphone a lot. Like an absurd amount of times. Practically multiple times a day. So it's surprising that my iPhone 12 Pro has lasted nine months without a cracked screen yet. Part of that has to do with the late-2020 model's durability, and the other part is thanks to my protective case.

Over the past few months, Google has prioritized the development of its video communications products as the demand for social distancing solutions continues to increase in response to the COVID-19 pandemic.

The worldwide health crisis around the coronavirus has gripped the live events industry, particularly in the tech sector, with the cancellations of Mobile World Congress, the Game Developers Conference, Facebook's F8, Google I/O and now South by Southwest.

While holographic Whitney Houston is hitting the road, a new mobile app is bringing volumetric captures of up and coming performers directly to the iPhones and iPads of fans.

As a native of Alabama, Apple CEO Tim Cook has a special place in his heart for the state. He also empathizes with the struggles that African-Americans have historically faced in the state, particularly during the 1950s and '60s civil rights era.

The camera system on the iPhone has never been better. Apple's iPhone 11, 11 Pro, and 11 Pro Max sport some of the best shooters on the market. But no level of quality makes up for the fact that shady apps can access your cameras for nefarious reasons. You can take control of the situation, however, and block any app you want from using your rear and front-facing cameras.

The "what (blank) are you" augmented reality filters on Instagram have become so popular that more and more Hollywood giants are following the augmented reality-powered social media meme train, with the latest example coming via Snapchat.

Spreading your reach to new audiences on Instagram takes time and effort. It's not only about taking unique photos and curating an exciting feed. You should choose the time of day wisely, connect with popular brands, and take advantage of hashtags. Unfortunately, hashtags can make it seem like you're trying too hard, but you can make them invisible — in stories, at least.

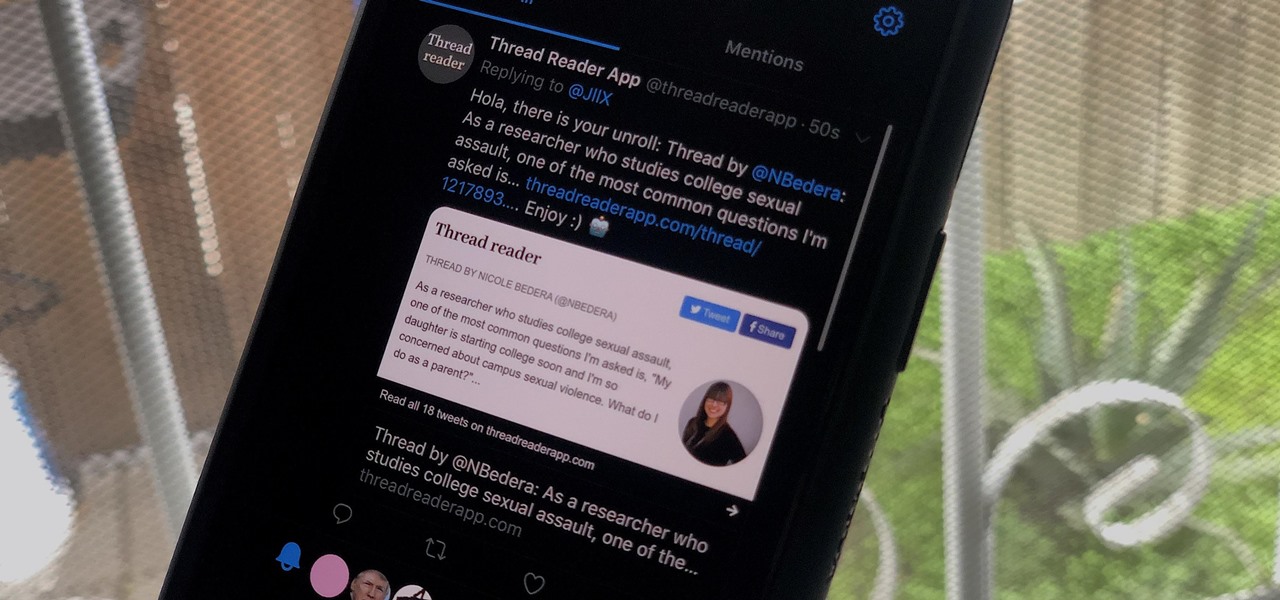
While tweetstorms were a part of Twitter since the beginning, threads, which makes tweetstorms more viable, didn't show up until late-2017. Still, threading multiple tweets at once to create long-form stories, opinions, tirades, and other lengthy Twitter posts, can be hard to digest. However, you can make reading them easier with just a single message.

While Snapchat is no stranger to location-based AR scavenger hunts, the app's new world-facing game adds some environmental understanding to the mix.

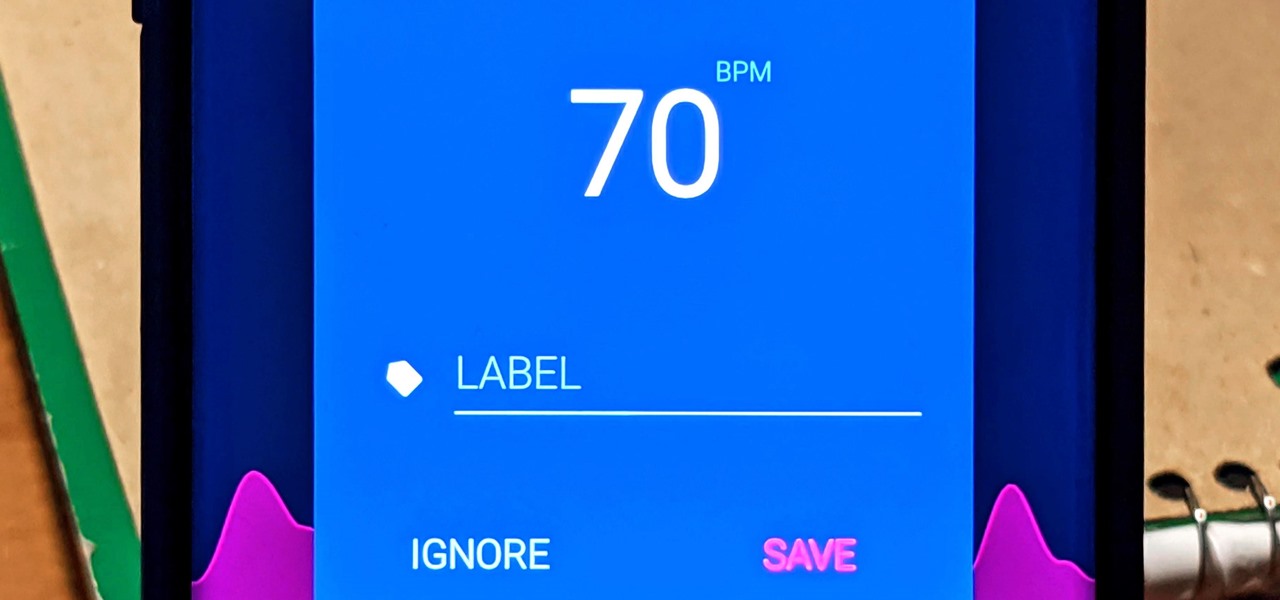
With the rise of smartwatches and wearables, you'd almost expect to need one to get a heart rate reading. While these devices can be helpful, not everyone has or wants to wear a gadget all the time to track their BPM. Luckily, when you combine Google Fit with a popular third-party heart rate measuring app, it will make things easy for you.