It's exciting to get that reverse shell or execute a payload, but sometimes these things don't work as expected when there are certain defenses in play. One way to get around that issue is by obfuscating the payload, and encoding it using different techniques will usually bring varying degrees of success. Graffiti can make that happen.

Password cracking is a specialty of some hackers, and it's often thought that raw computing power trumps everything else. That is true in some cases, but sometimes it's more about the wordlist. Making a custom, targeted wordlist can cut down cracking time considerably, and Wordlister can help with that.

After months of back and forth, ZTE is finally making their return to the United States. The last phone the Chinese company released here was the Axon 7 Pro, a low priced flagship phone that competed well against the OnePlus 3 and 3T at the time. Its successor is the Axon 10 Pro, which adopts the same strategy.

For the first time in a while, the battle between Samsung and Apple is really interesting. Unlike previous years where the choice for smaller hands was limited to the Galaxy S series, this year, there's an option for Galaxy Note users. Both sides of the aisle have their best options in years with minimal sacrifices.

One of the first steps in attacking a web application is enumerating hidden directories and files. Doing so can often yield valuable information that makes it easier to execute a precise attack, leaving less room for errors and wasted time. There are many tools available to do this, but not all of them are created equally. Gobuster, a directory scanner written in Go, is definitely worth exploring.

The art of privilege escalation is a skill that any competent hacker should possess. It's an entire field unto itself, and while it's good to know how to perform the techniques involved manually, it's often more efficient to have a script automate the process. LinEnum is one such script that can be incredibly useful for privilege escalation on Linux systems.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

In 2019, Sony is mixing up its design, attempting to stand out among the sea of familiarity. Instead of emulating Samsung with punch hole cameras, they decided to target a rare section of the market, content consumers. There's the Xperia 1 for those who want the best, and the Xperia 10 and 10 Plus for the budget crowd.

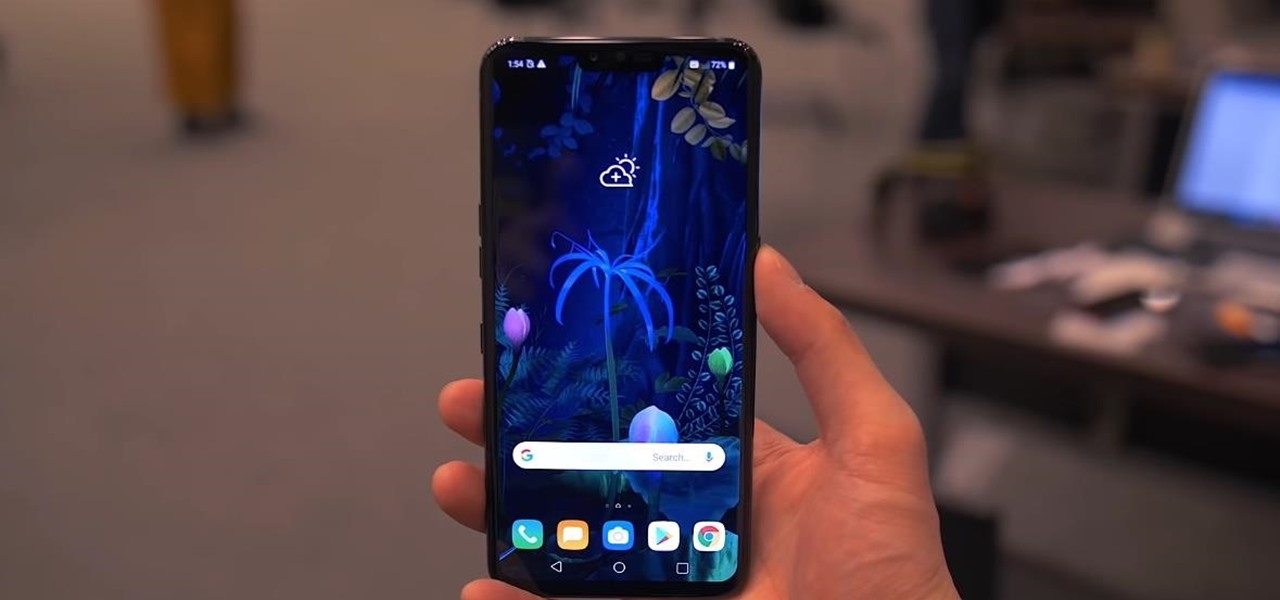
Similar to last year, LG is mixing up its releases. Instead of the G series in the first half of the year and the V series in the second half, LG is releasing both heavy hitters together. However, unlike last year, this is a true upgrade from its predecessor, the LG V50 ThinQ 5G.

For 2019, Sony is trying to shake its failures of the past and start fresh. Following the unsuccessful Xperia XZ series, Sony is changing the name of their flagship to a single number: Xperia 1. With the name change comes a few upgrades, one of which is its new look. Secondly, its new display is unmatched in the mobile space.

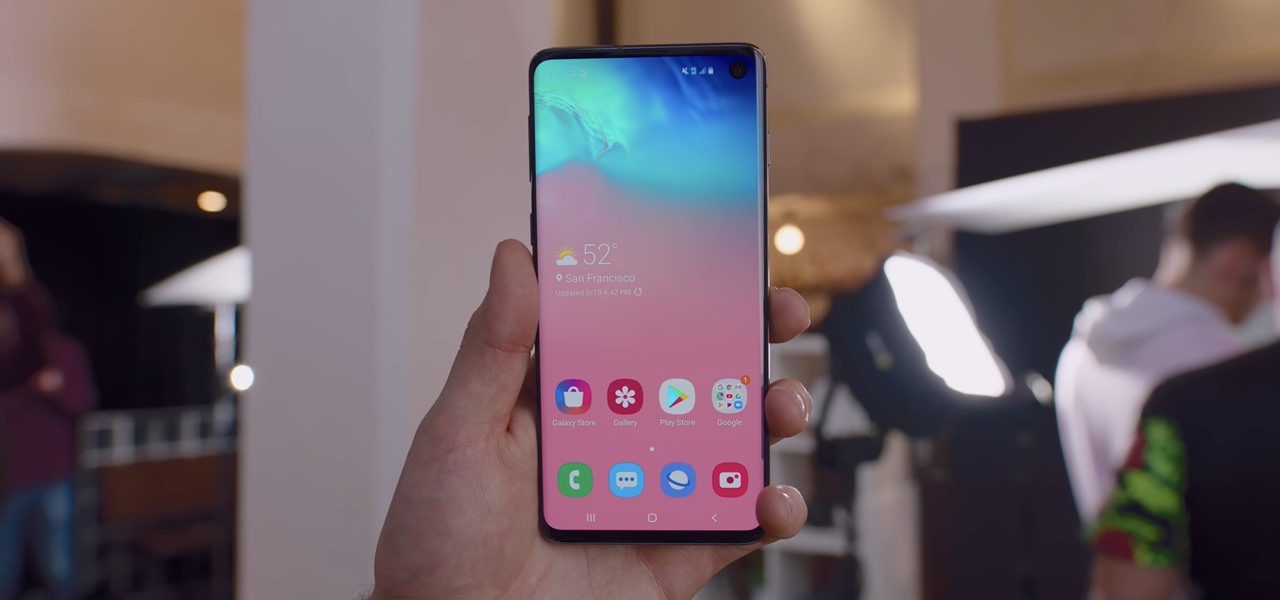
The Galaxy S10 has finally been revealed to the masses, and it certainly doesn't disappoint. As the flagship to herald the tenth anniversary of the venerable Galaxy S line, the S10 has kept popular and familiar design elements like the immersive Infinity Display while employing new features like more advanced cameras to set a new standard for other OEMs to follow.

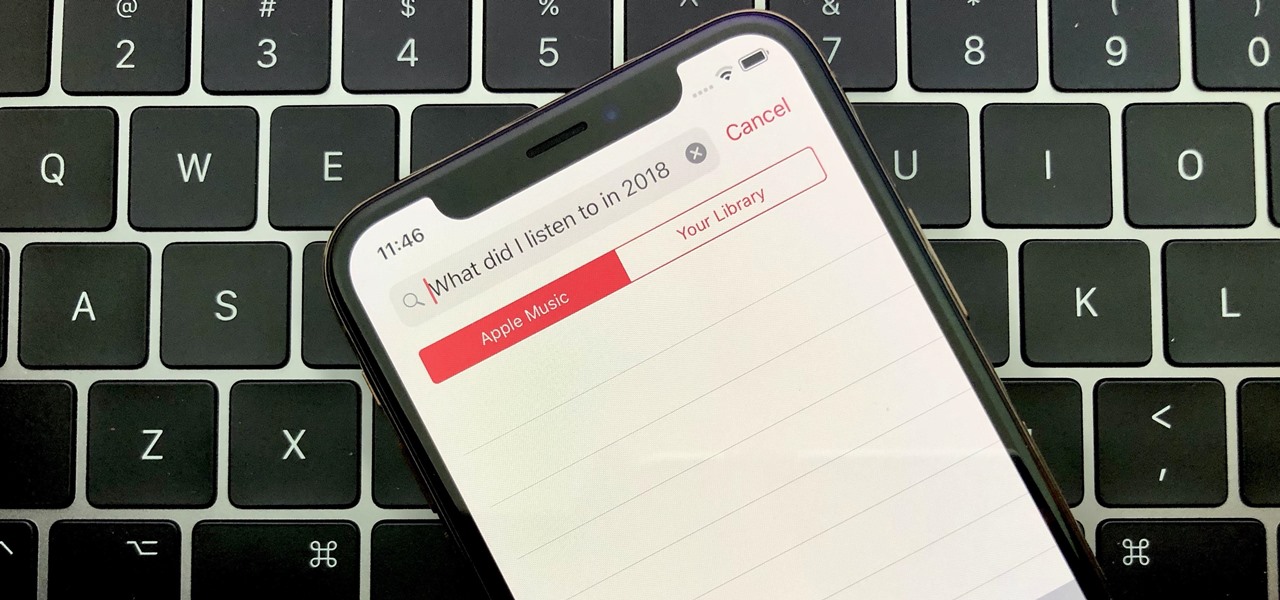
Around the end of each year, Spotify offers a year-in-review service so its users can see what they listened to the past year and share their listening histories in fun infographics. Apple Music does not have such a feature, unfortunately, but there is a way to curb that FOMO feeling this holiday season by downloading your listening history not just for 2018, but for the entire lifespan of your account.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

One of the things that sets a seasoned hacker apart from the script kiddies is the ability to effectively sneak past antivirus defenses when executing an attack. One way to do this is to use custom shellcode in an exploit. Not everyone is an expert at writing shellcode, but luckily there's an easy way to do this that is both quick and effective.

By now, you already know that the Magic Leap One ships with an array of apps to immediately get you accustomed to operating in your new spatial computing reality. The first one we're going to focus on is Screens, an app we told you about previously, but only now have managed to try for ourselves.

In its latest feature with an assist from augmented reality in storytelling, the New York Times shows readers the virtual crime scene it constructed to prove that the Syrian military conducted chemical warfare against its citizens.

As manufacturers try to differentiate their smartphones from the sea of Android devices, a new genre of smartphone has emerged: gaming phones. Razer Phone was the first to gain traction, but the likes of Xiaomi, Asus, and ZTE have all announced gaming-first phones coming soon. Still, you don't really need to buy a "gaming phone" to play games like a pro on your smartphone.

Kali Linux is known as being the de facto penetration-testing Linux distribution but can be a pain to use as an everyday OS — even more of a pain if that means carrying around a second laptop or the constant frustration of using the finicky Wi-Fi on virtual machines. But there's another option: installing a Kali subsystem on your Windows computer as a convenient compromise.

You may have noticed improved photo quality in the Android Snapchat app in recent months. Believe it or not, this is because Snapchat only just recently started using a decade-old camera API that predates every Android phone in existence.

Preserving battery life has become one of the biggest problems for the average user. Whether you're on Android or iPhone, your battery is probably a massive concern. While there are a ton of battery-saving tips out there, they mainly rely on you manually performing actions yourself. This isn't the case if you use IFTTT to take care of your battery automatically.

Apple has been in hot water ever since the news that the company slows down iPhones with older batteries. The iPhone maker is now in damage control, offering customers a large, $50 discount on battery replacements. The question for you, though, is does your iPhone need a battery replacement in the first place?

"I'm Rey." That's what a lot of people will be saying again this Halloween, as Rey costumes are sure to be another favorite of trick-or-treaters and cosplayers. Yes, on Oct. 31 we all have a chance to be the scavenger of Jakku who just so happens to be the "new hope" for a Jedi renaissance.

Deadly rat lungworm parasites have found their way into Florida. The parasitic worm relies on snails and rats to complete its life cycle, but don't let this nematode's name fool you. This worm can cause meningitis and death in humans who inadvertently consume snails, frogs, or crustaceans harboring the infective parasite.

The noses of kids who live in areas of intense pig farming may harbor antibiotic-resistant bacteria, presumably acquired from the animals, according to a new study by scientists at the Johns Hopkins Bloomberg School of Public Health, UNC Gillings School of Global Public Health, and Statens Serum Institut in Denmark, published in Environmental Health Perspectives.

Antibiotics used to prevent diseases in livestock are creating a world of hurt for humans and the soil we depend on for food. Bacterial resistance to antibiotics is a global health issue. The overuse, underuse, and poor use of these life-saving drugs is rapidly removing them as a treatment option for serious infections in humans—plus bacteria are naturally adaptive.

Have you ever had the stomach flu, aka the 24-hour flu? Well, chances are high that you never had influenza, but an intestinal infection called gastroenteritis.

Somewhere around 600–800 million people in the world are infected with whipworm (Trichuris trichiura), an infection they got from ingesting soil or water contaminated with feces of infected animals or people containing the parasite's eggs.

Marijuana is legal to use for medical purposes in 28 states and the District of Columbia, but the quick development of this new industry could have left some regulation issues in the lurch.

BlackBerry has formally announced the arrival of its flagship, the KeyOne, during Mobile World Congress 2017 in Barcelona. The all-Android KeyOne looks distinctly BlackBerry, with its 4.5" screen and physical QWERTY keyboard. Here's the lowdown on this elegant handset that hearkens back to BlackBerry's heyday, which had previously been known by its code name, the BlackBerry Mercury. Aluminum Unibody with Physical Keyboard

All day I dream of eggs: scrambled, poached, over easy, hard-boiled, fried, baked, raw... Okay, the last one is a joke (unless you're Gaston, which means that you eat five dozen of them and you're roughly the size of a barge). But eggs are freaking good in just about any cooking prep, and more often than not are the foundation of your favorite baked goods.

I used to brag that I could make a swan out of an apple, but chicks don't dig swans—they dig roses. So now I'm going to brag about making apple roses, because you would, too, if you could get them to look like this: Now that's an apple tart that will win the ladies over. (And definitely 100% tastier than the usual bouquet of roses, and 100% less greasy than a bouquet of bacon.)

Wheat toast. White toast. Sweet potato toast. Okay, one of these things is not like the others... Don't Miss:

Summer means watermelon. Juicy, pink-fleshed, and ever-so-tasty, this pepo is a seasonal sensation. But while cost effective, purchasing a whole, large watermelon can lead to melon monotony and maybe even a rotting rind in the fridge. To keep that from ever happening, here are 15 creative ways to use up that wondrous watermelon. Waste not, want not!

Though the word "pie" may conjure up images of a dessert made of dough with various fillings, the famous Frito Pie is, in fact, something of an entirely different nature. Absurdly simple in its construction, this pile of Fritos and chili is served in the actual chip bag and more closely resembles nachos than it does a traditional pie.

If you love sitting poolside with a slice of watermelon, then I've got a real treat for you. Picture yourself cooling off with a slice of juicy watermelon topped with fresh ingredients like soft cheeses, herbs, and fresh summer fruits. Watermelon pizza is a wondrous thing—a creative take on the classic watermelon salad, only pizza-fied!

The octopus is famous for its bulbous head, enormous eyes, and four pairs of long arms. The stuff of legends and nightmares, octopi have been featured in stories, artwork, and meals galore. But how do you eat this distinctive looking, bilaterally symmetrical sea creature?

You can put spices in a scramble or fry an egg in bacon fat, so why poach eggs in just plain water? Water doesn't add any flavor whatsoever, so you're wasting a valuable opportunity to give your poached eggs more oomph—an extra important step if you're not frying your poached eggs afterward.

Plastic wrap is, arguably, man's greatest invention—or at least, the 2000 Year Old Man thought so. Its primary use is to protect food from getting dried out in the fridge or on the counter; but if that's all you're only using it for, you're missing out.

Alright so last time I gave you a homework assignment. This week we're gonna look at my version of the UDP-Flooder.

Uh-oh: you wake up one morning with the telltale signs that you are coming down with something. Your throat is sore, you can barely breathe out of your nose, and you have a nagging cough.