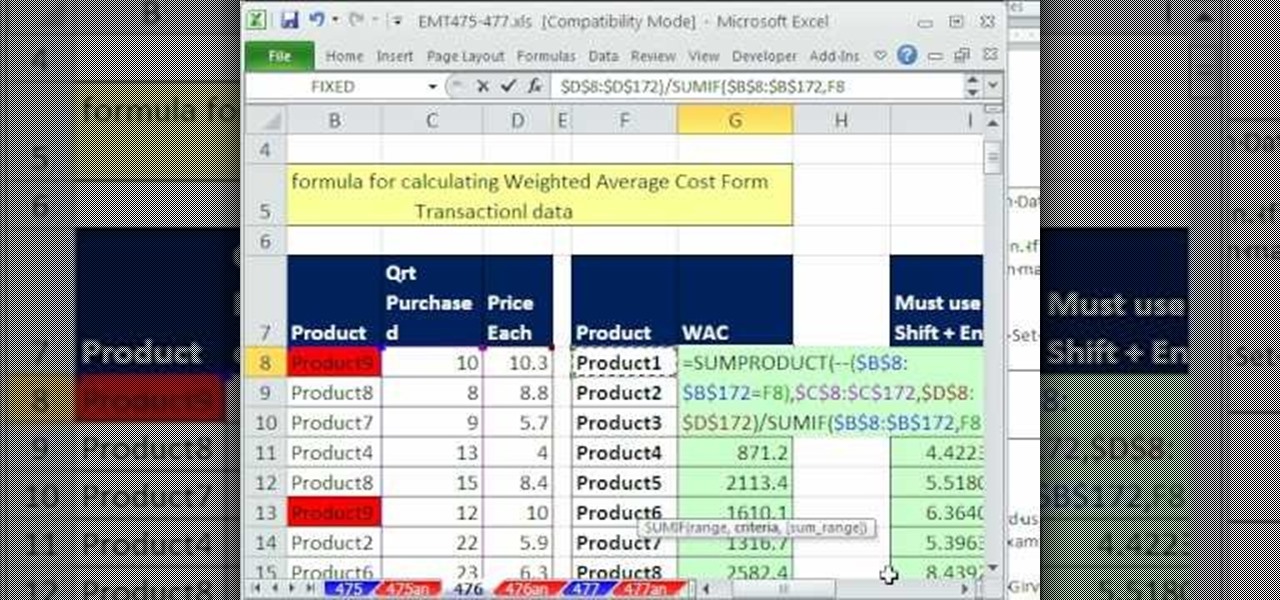
This video shows you how to calculate weighted average cost from a transactional data set using SUMPRODUCT function. It explains things very clearly. If you're working with a very large database transactions the SUMPRODUCT function makes it. It works as text if you do the formatting first and then type the number. We put the number in first and then format as text, then press F2 and ENTER.

Studying to be a nurse? Then follow along with this how-to video to learn how to start an IV on a live person. IVs are an important part of a nurse's everyday routine. When inserting an IV needle, be sure to enter at a 30 degree angle. The nursing students in this video, Moe and Drew, insert the needle at 10 to 20 degrees.

Sometimes you don't want people to see what you've entered into Excel. Use this tutorial video to learn how to hide that information in Excel to keep it safe.
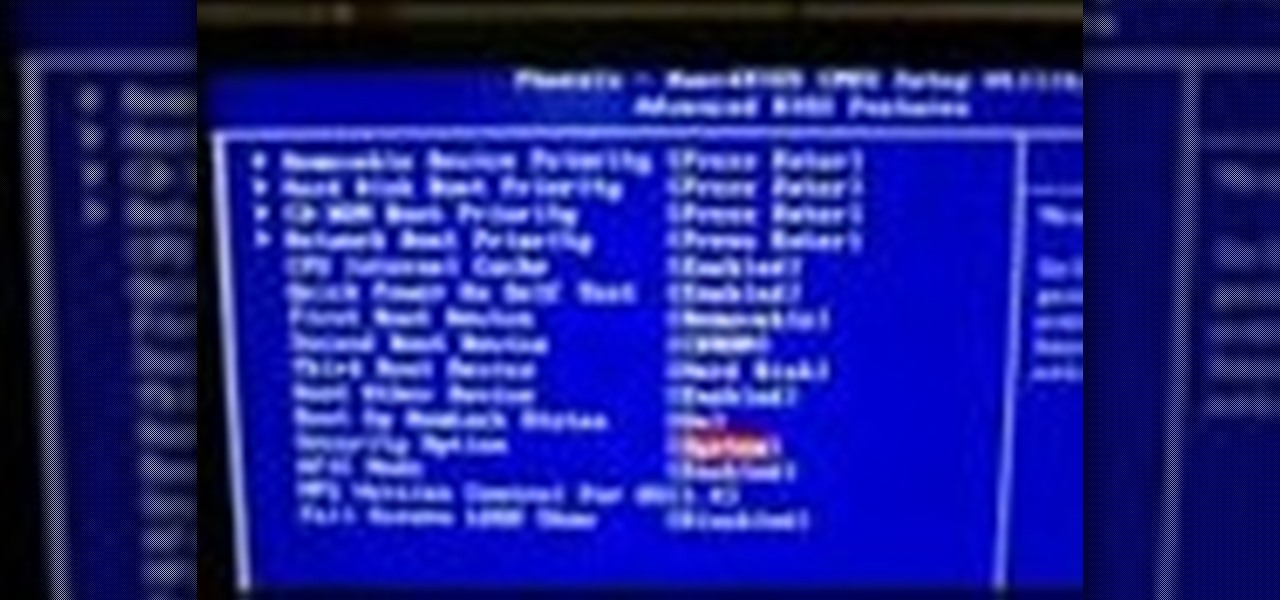
What you need to do is press a certain button when your computer boots (it should say something like press this key to enter setup). Press the specified key and inside the bios find the option that allows you to set a password. Once you create a password then you have to set it so the computer requires the password on boot. Please rate and comment this video.

Shogi is Japanese chess. It is a unique game of strategy. Captured pieces can be replayed and most pieces can be promoted when entering the opponent's territory.

Want to crack Ninja Gaiden Sigma for the PS3? Let a hot chick help you! In the regular version of this game, you can unlock the five additional missions that come on the collector's edition. After you've solved the game, go to the mission mode screen and enter: Up, Down, Left, Down, Right, Up, Square.

Get closer to God with a hot chick.

Try some gender bending in Elder Scrolls IV (4): Oblivion and flip the sex of your character. To do so, enter the code ~sexchange.

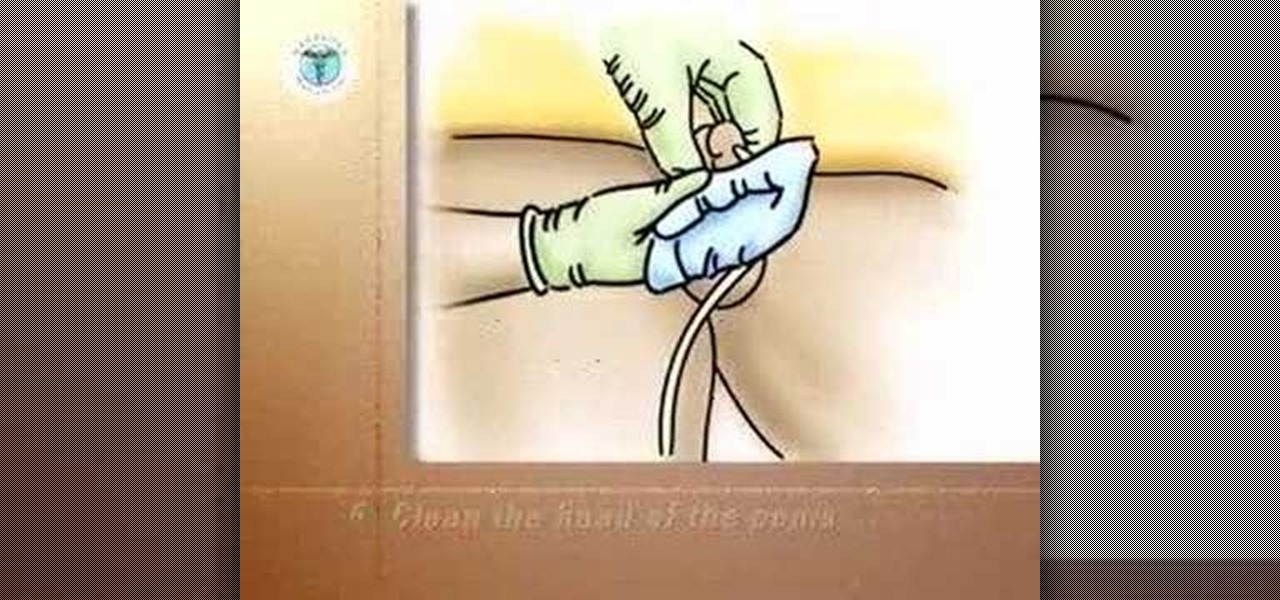
Once each day, or according to your doctor's instructions, you will need to clean the urethral meatus - the opening where the catheter enters the body. This video shows you how to give a proper male perineal wash.

This video shows you step by step how to choose the aperture to produce drastically different effects. The is the opening by which light enters your camera.

Many people tend to focus on decorating and tidying up their house, often forgetting to care for their patio. This makes little sense to us because the doorway and patio is the first thing all your guests will see as they enter your house. So spruce your patio up by building a patio and walkway out of flagstone.

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

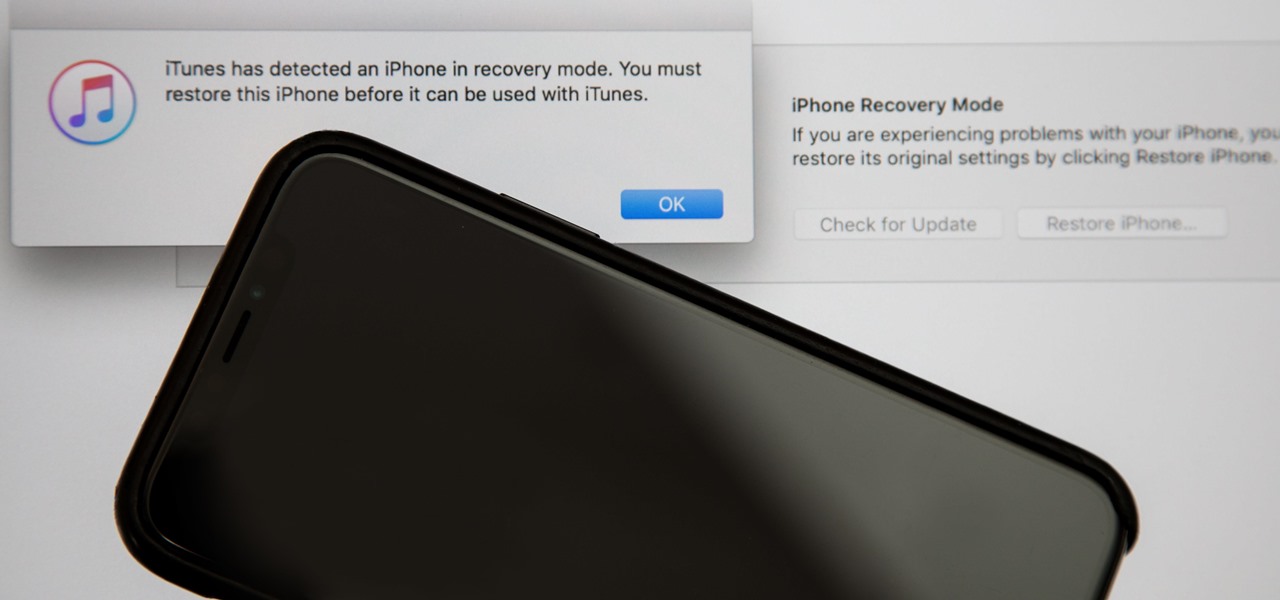
Apple's innovations often involve more taking away than adding on. The company has released seven iPhones that omit the home button, the latest batch including the iPhone 11, 11 Pro, and 11 Pro Max. If you recently picked up one of these devices for the first time, you might be a little confused on how to enter DFU mode when your iPhone acts up.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!

Spotlight, Apple's selection-based search system, received a major facelift on Mac OS X Yosemite. Packed with dozens of new features, such as a central search window and increased app suggestions, the reworked Spotlight was a breath of fresh air.

Voicemails are like chores for me. I have to listen to them, but never really feel like doing it. When I finally do, most of them get deleted right away, but every so often they'll be one I save and listen to over and over again, whether it's a cute birthday wish from grandma or a hilarious joke from my friend.

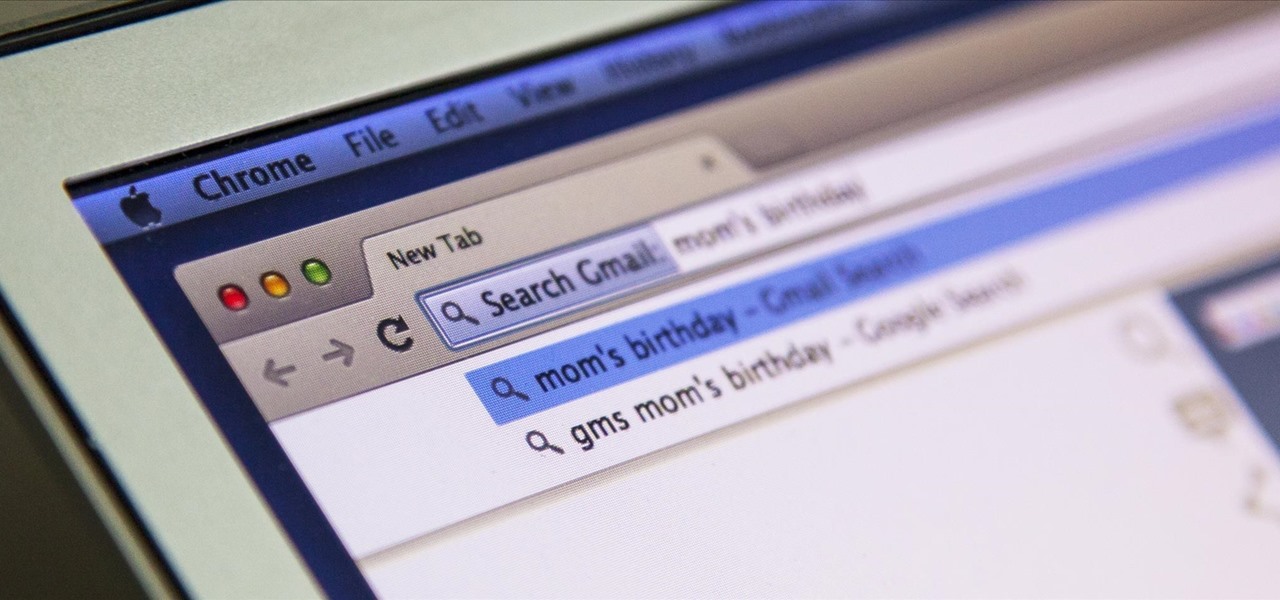
I'm all about saving time. If there's a quicker way to do something, I'm going to find it. For this reason, whenever I need to search through old emails or compose new ones in Gmail, I do it directly from Chrome's address bar, or as Google likes to call it, the omnibox—and you can, too.

Want to learn how to make your own comic book? This instructional video will teach you how to take your created character and their powers and enter them into a comic book world. The first step, is to decide whether your character will be acting as a hero or villain. Next, you must create the setting. This is followed by the conflict of the story. Finally, the resolution. The hero must defeat the villain and everything is back to normal. The video then takes you through a sample comic book an...

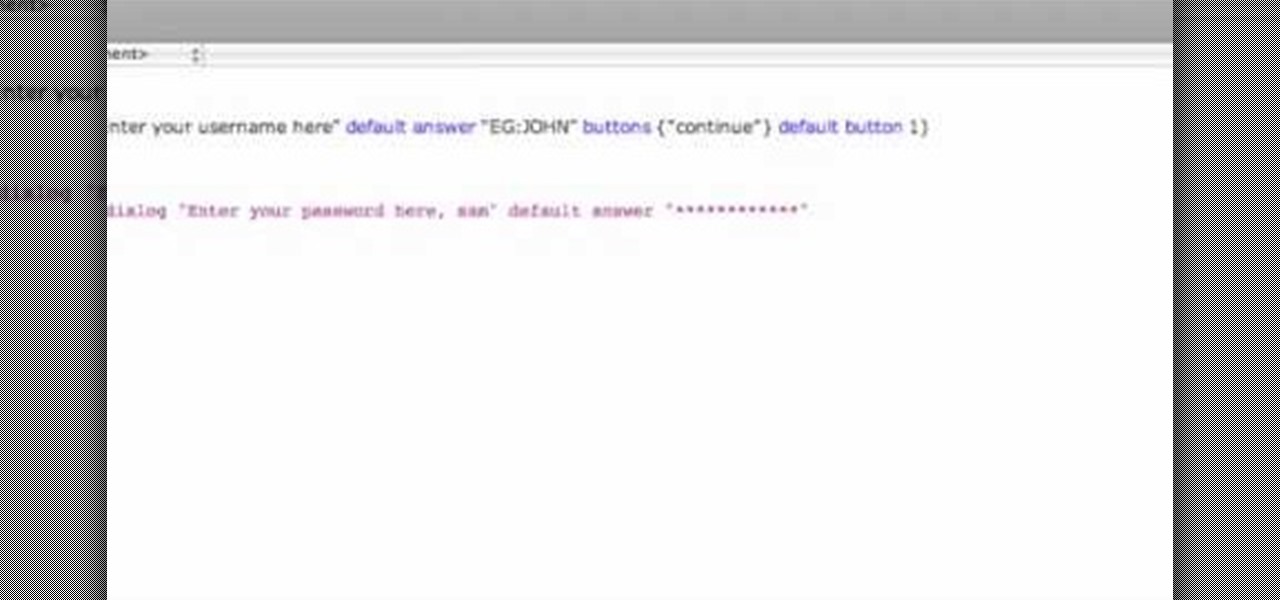
This video shows how to program a password and user protected application in AppleScript.

If you've ever received an email from a sketchy address purporting to be Uber, asking you to sign in with your credentials, you might be a phishing target. Hackers use a fake login page from real-looking domains to trick you into giving up your account information, and while it's been an issue in the past, Uber is making it more difficult on cyber thieves with the addition of two-step verification.

Following in the iPhone X's footsteps, the iPhone XS and XS Max, as well as the iPhone XR, have all ditched the iconic Home button last seen on the iPhone 8 and 8 Plus, which is one giant leap toward Jony Ive's ultimate vision of an iPhone that's a clean slab of glass. However, without the Home button, a lot of tasks have changed, most notably, entering and exiting DFU mode in iTunes.

Excessive cell phone use was issue that Apple decided to tackle with iOS 12. Starting with the iPhone's 2018 update, a new "Screen Time" feature give you the ability to set App Limits to encourage more balanced usage, and there's another setting that gives you control over when certain apps can be accessed.

Buying an unlocked phone is usually the correct move. By doing so, you bypass a lot of bloat that carriers put on your phone, and you can also use that phone with another carrier should you decide to switch to a new one. However, a lot of carriers won't give unlocked devices access to their visual voicemail apps. For that, there's Google Voice.

Following in iOS 11's footsteps, Android 9.0 Pie will include a security feature that lets you immediately disable the fingerprint scanner as well as extended Smart Lock features. After initiating the feature, you will be required to insert your PIN, pattern, or password before any other unlock methods will work again.

Netflix currently lets parents block content based on maturity rating, but it isn't a perfect system. Not all titles rated PG-13 are equal, for instance. That's why it's good news that Netflix is adding more controls for parents, by allowing account holders to bar individual movies and TV shows they deem inappropriate.

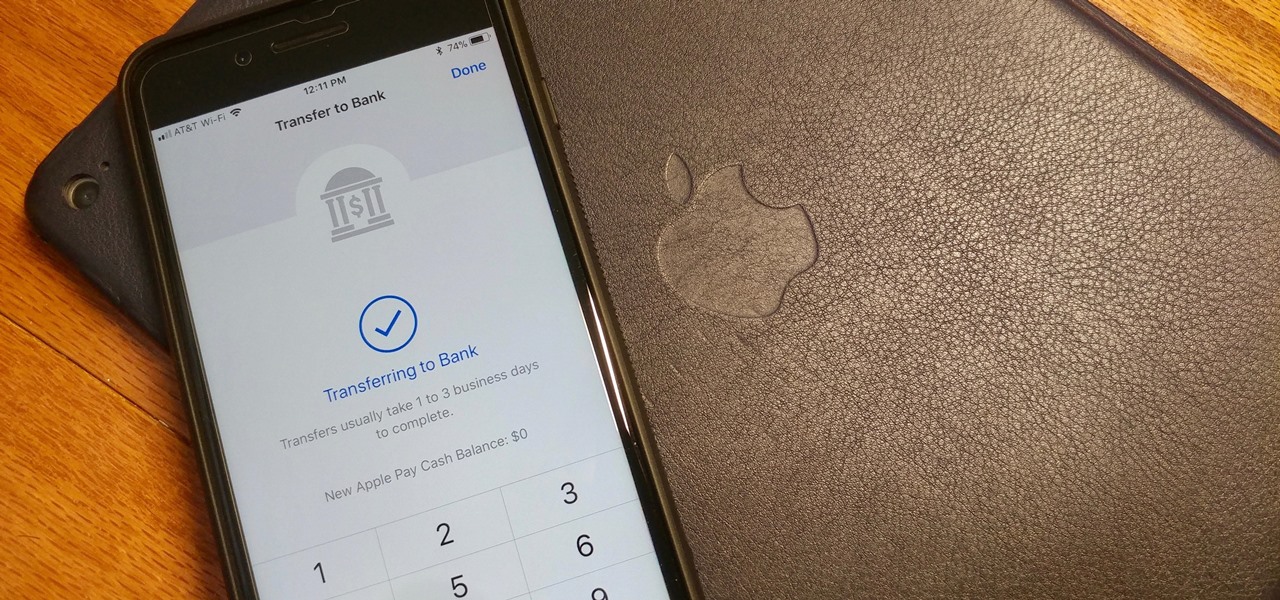
Let's say you receive $10 from a friend through Apple Pay Cash via an iMessage. You could spend that money in the App Store or at any retailer that supports Apple Pay using your Apple Pay Cash card. If you'd rather save it or use it for bills, it's easy to transfer that money to your bank account in iOS 11.2.

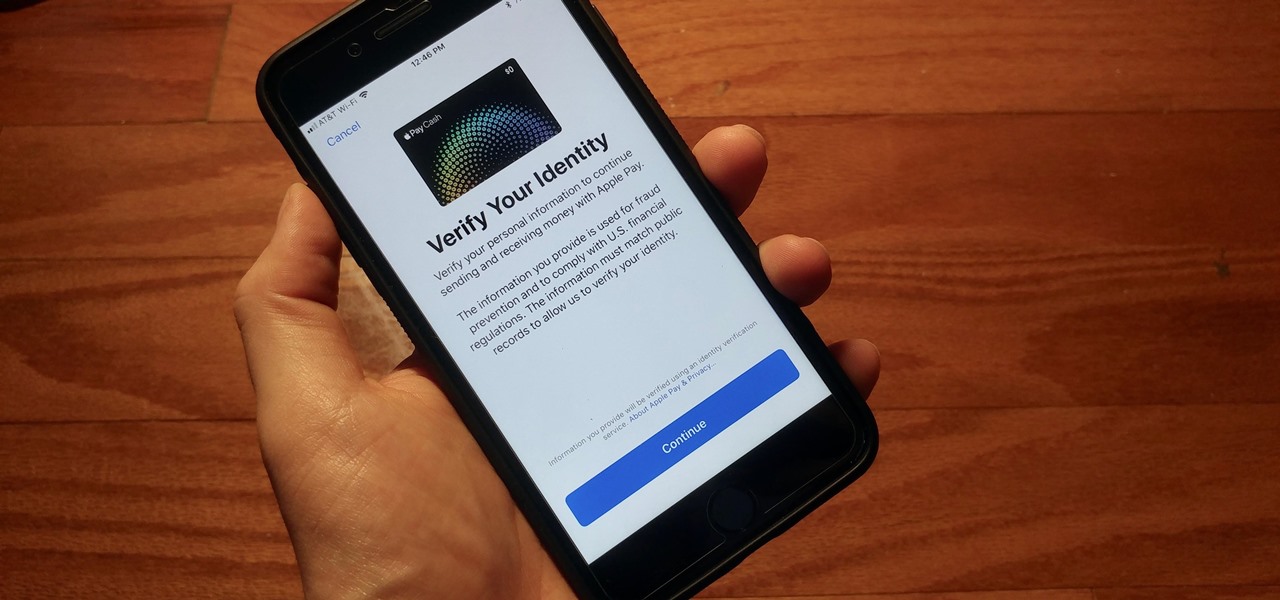
With iOS 11.2's introduction of Apple Pay Cash, you can send and receive money to others directly through iMessage, using the convenience and security Apple Pay is known for. However, if you want to make sure your efforts go uninterrupted, you'll want to make sure you verify your identity with Apple.

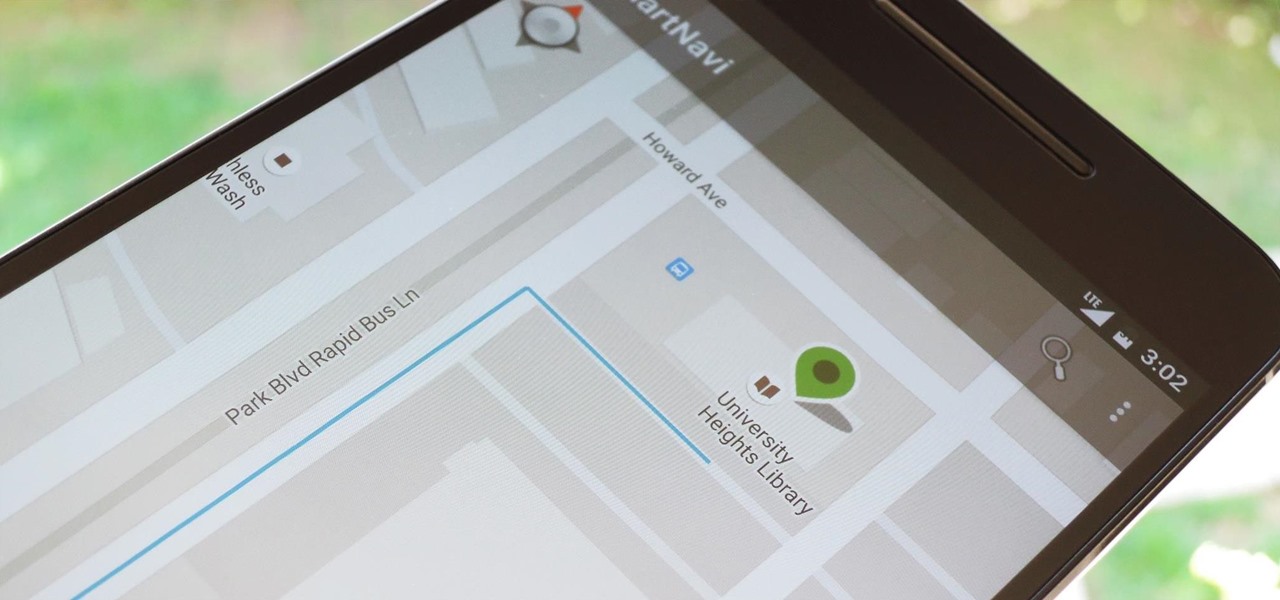
Modern smartphones are packed to the brim with low-power sensors like accelerometers and gyroscopes, which means they're capable of precisely measuring almost any type of movement. So why is it that when you just want to get walking directions somewhere, your device still uses its battery-sucking GPS connection to track your progress?

Windows 10 definitely has a sleek and modern look to it, but some of these visual changes have been made at the expense of functionality. For instance, the slider that appears when you click the volume icon in your notification tray now sports a completely minimalist look that lacks the quick link to the full volume mixer from past Windows versions.

While password cracking and WPS setup PIN attacks get a lot of attention, social engineering attacks are by far the fastest way of obtaining a Wi-Fi password. One of the most potent Wi-Fi social engineering attacks is Wifiphisher, a tool that blocks the internet until desperate users enter the Wi-Fi password to enable a fake router firmware update.

One of the most exciting things about a major iOS update is the discovery of new glitches, or even just finding ways to replicated the old ones that we've come to love so much. One of these is the glitch that lets you nest folders within folders on the home screen, which can save some major screen real estate. While this glitch was available in both iOS 7 and iOS 8, the process is slightly different in iOS 9, but you still have a couple options to choose from.

You would think that with each major iOS update, there'd be fewer ways to bypass the lock screen. Unfortunately, Apple's developers have consistently failed every year since 2013 in this department, leaving open lock screen exploits for iOS 7, iOS 8, and now the latest iOS version, iOS 9, with each exploit being discovered within days of the OS release.

Hello all! In this tutorial, I'd like to show you one way of getting root on OS X. Check out this GitHub page for a recent privilege escalation exploit that was recently discovered. I've tested it and it works on both OS X 10.9 Mavericks and OS X 10.10 Yosemite, but appears to have been patched with OS X 10.11 El Capitan. If you check out the file main.m you can see where most of the magic is happening. This source code can very easily be changed to make it do more than just the system("/bin/...

Hackers have stolen over 225,000 Apple user's account information from countries all over the world—including the United States, China, and France—in what many are reporting to be the biggest known Apple hack in history.

This tutorial is for those who've purchased an account with Private Internet Access to hide your VPN and would like to set it up in Kali. Please note, you can chose to run your PIA service from your Windows computer without configuring it in linux as long as you'll be using a NAT connection. Using a NAT connection will allow your Windows machine and Kali Virtual Machine to use the same IP address, hence if your IP is hidden on one, it will be hidden on the other.

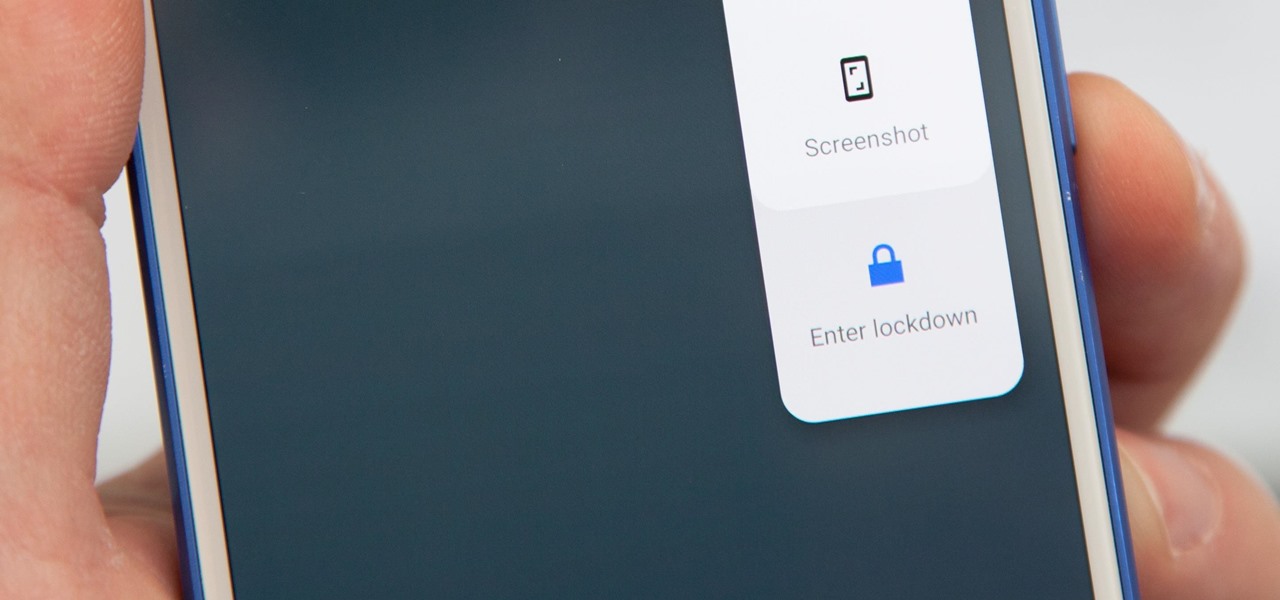
When it comes to security, there are usually only a handful of things that you want protected from prying eyes on your iPhone—private photos, scandalous videos, and important text, such as credit card and social security numbers.

After you have registered to this site,sign in then to start missions. Basic Missions

As you're probably well aware by now, the Apple Watch isn't just for sending text messages and checking Instagram—you can also use it as your wallet. With Apple Pay compatibility, you can use your Watch to make purchases at any retailer that accepts the payment service.

Google recently rolled out a new Smart Lock option labeled "On-body detection" for Android Lollipop via an update to Google Play Services. As I'm sure you can gather from the name, this new function keeps your phone or tablet unlocked using the built-in accelerometer to determine whether or not your device is being carried on your body, allowing you to set it down and walk away carefree knowing that's it's locked again.

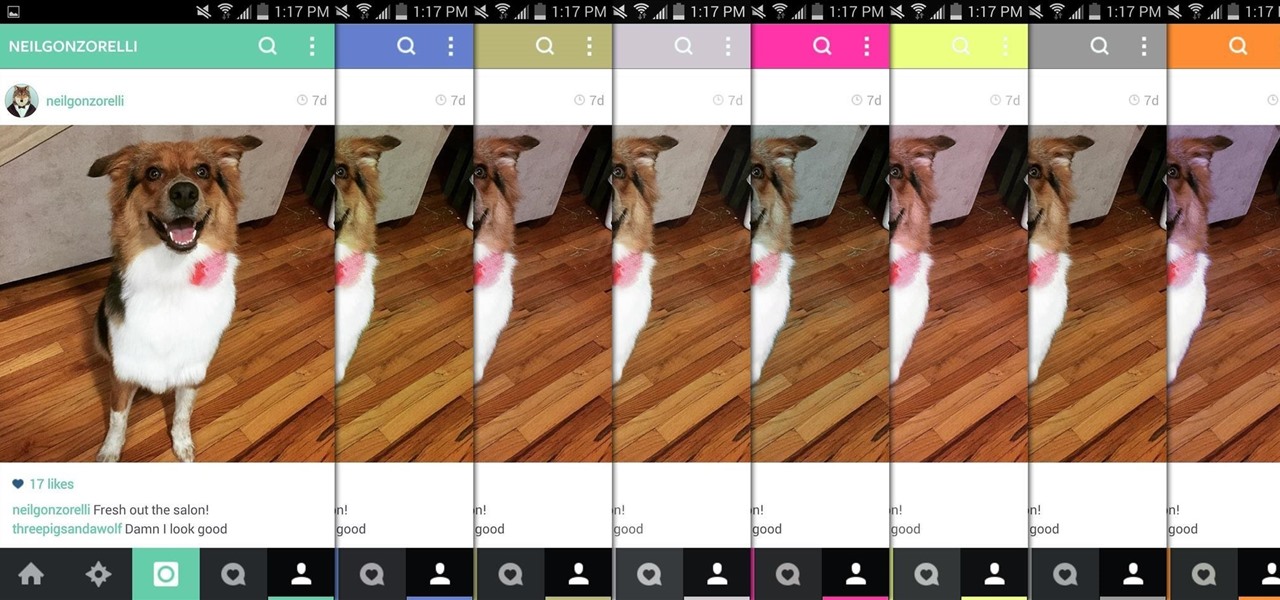
There aren't many complaints I can think of when it comes to the Instagram interface, and finding one would just be nitpicking. But like with most things in life, if given the opportunity, why not take advantage? "When in Rome," as they say.