Link shortening is the process of cleaning up the URL link which is long and converting it into a short URL. You can use bit.ly to do link shortening. Using bit.ly you can not only shorten the link but also track the users who are using those links. To use this service go to the http://www.bit.ly website. There in the home page you are provided with a text box. Enter your long link in the text box and submit it. Now the website converts the long URL and provides you with a short link which ca...

In this video, you'll see how and why wax can be a deadly. This is how it works,When the test tube is submerged in cold water, the glass forms tiny cracks. The Water enters gets into the tube and vaporizes causing a micro explosion. The hot wax is then ejected from the tube quickly as oxygen is displaced from the tube itself. Be careful, and make sure to be as safe as possible when trying this experiment at home.

This video shows you how to do a mathematical representation on computing the nCr function using a TI-89 calculator. You can write the nCr notation in different forms. It can be simplified from nCr to C(n,r). The symbol can either be read "n choose r" or "n taken r at a time" which are from it's probability applications. On the example to find "26 choose 17", go to the Home screen of the TI-89 calculator and then go 2nd 5 which is Math. Go choose probability and then to nCr to type in (26,17)...

Installing a peephole in your home's front door can give you and your family a sense of security knowing who comes to your door before they enter. In this video Barbara K will show us exactly how to install a peephole on your door.
Learn how to create shiny, reflective and vector text in Adobe Ilustrator. Open a new file in Illustrator. Select pixel dimensions and orientation. Select the text tool and enter desired text. Ungroup the text. Select a portion of the text. Use the gradient editor to select a swatch and change the angle. Adjust the drop shadow. Create a reflection of the text using the horizontal reflect command.

By using the mirror glitch, it's possible for Link to enter the Dark World earlier than the game intended. Take a look at this instructional video and learn where and how to perform the mirror glitch to travel to the Dark World early on in Zelda: A Link to the Past. Note that this glitch works on the Game Boy Advanced and the SNES emulator, but doesn't work on the Super Nintendo console.

The BBC Focus magazine team enter the 2008 Woolacombe International Sandcastle competition applying the laws of science to build the ultimate sand castle. This tutorial video will give you some tips and tricks on applying science to sandcastles.

Watch this electronics tutorial video to learn how to enter a secret code and see a lot of interesting info on how your iPhone connects to the network. Field testing your iPhone is easy with the tips in this how-to video.

This video is a how-to demonstration of Eastern European Knitting, the purl stitch. Please note, this is not continental knitting, as here we enter through the back of the loop in both the knit and purl stitch. The resulting fabric appears exactly the same as both English and Continental knitting styles. As a note to the purl stitch, notice that the yarn is still held at the back of the work.

This video is a how-to demonstration of Eastern European Knitting. Please note, this is not continental knitting, as here we enter through the back of the loop in both the knit and purl stitch. The resulting fabric appears exactly the same as both English and Continental knitting styles. Great thing to love about ribbing using this method is that the yarn is held at the back of the work the whole time.

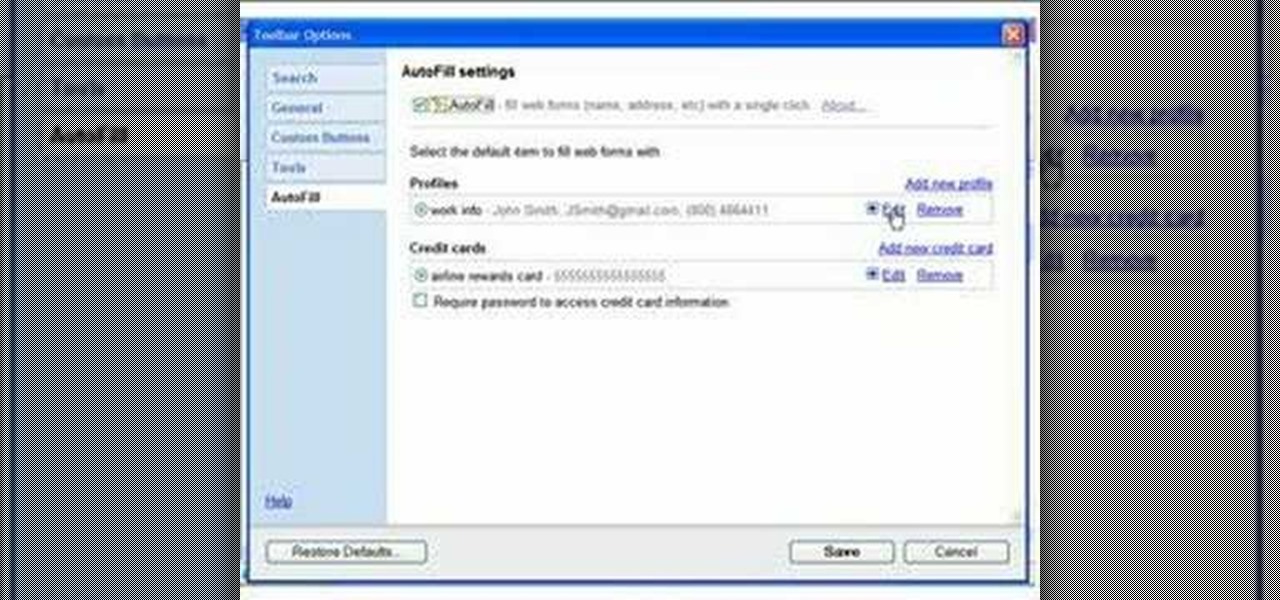
A simple video showing how to add an auto fill profile so that when you have to enter all your contact information it will do it automatically using auto fill.

If you've ever entered a lot of data into an Excel spreadsheet before, then you know that putting together even one spreadsheet is a pain in the butt. So if you are required to place all the data on one spreadsheet onto another spreadsheet, don't slave away for hours copying and pasting.

The move order 1.d4 d5 2.e3 Nf6 3.Bd3 e6 4.Nd2 c5 5.c3 Bd6 is very annoying because it discourages the key move f2-f4. Instead, White should play a different opening. He can enter a reversed Meran Defense with 6.dxc5, or a Colle System with 6.Ngf3.

This tutorial gives tips on how to properly enter corners when go-karting for the fastest times possible and while being safe.

This video demonstrates an easy way to create natural transitions. The key is to have the subject enter and exit the frame during different shots. This keeps a level of continuity that makes your movie easier to follow and easier to edit!

Male instructor explains how to create new contacts in the BlackBerry 8700 mobile device. Going to the BlackBerry's address book, it is a matter of entering in all the information for a new contact to be created. Step-by-step process makes it very easy to understand and complete the contact.

In Numbers '08 you can enter data dynamically with interactive buttons and sliders known as cell controls. This tutorial goes over using check boxes and sliders.

This simple technique to creating a bang when people open a door is sure to scare the daylights out of your friends. Using party poppers, you can take them apart and tie them across a door entry. When a person enters, the poppers explode. There are great reaction shots on this video as welll.

The iPhone's autocorrect feature is wonderful and convenient, but it doesn't always work with informal language like profanity. If you've ever used the F-word, there's a good chance you've had your curse words "corrected" to other words that don't ducking make sense. And with the release of iOS 13, swearing in your messages and on social media could get a little harder.

With new iPhone models out, you'll have updated cameras to try out, a faster processor, and new colors to choose from. The only thing that could stop you from picking one up yourself is, well, your current iPhone. Here's how to check if you're eligible to upgrade to iPhone 11, iPhone 11 Pro, iPhone 11 Pro Max, or any other iPhone still being sold.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.

NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of last year, they've really out done themselves.

It has been a while since my last Raspberry Pi tutorial , but now I am back with another tutorial. This one I should note isn't your typical tutorial, but as always lets boot up our Pi and wreck havoc.

Social Engineering was mentioned a few times here on Null Byte, but not very many explained what it is, or how to do it. I love this quote because it's true: Social Engineering is the key to carrying out client side attacks, and all you need is a little creativity!

Master Lock combination padlocks have been known to be vulnerable to an attack that reduces their 64,000 possible combinations down to 100. I've devised a new attack for cracking any Master combo lock that simplifies the process and reduces the amount of work down to only 8 combinations.

When Google Play Music launched a few years ago, I ditched iTunes and began using the service as my one and only source for listening to my personal music library. While All Access is great, I still prefer the radio feature on Spotify, so I still use that to discover new music.

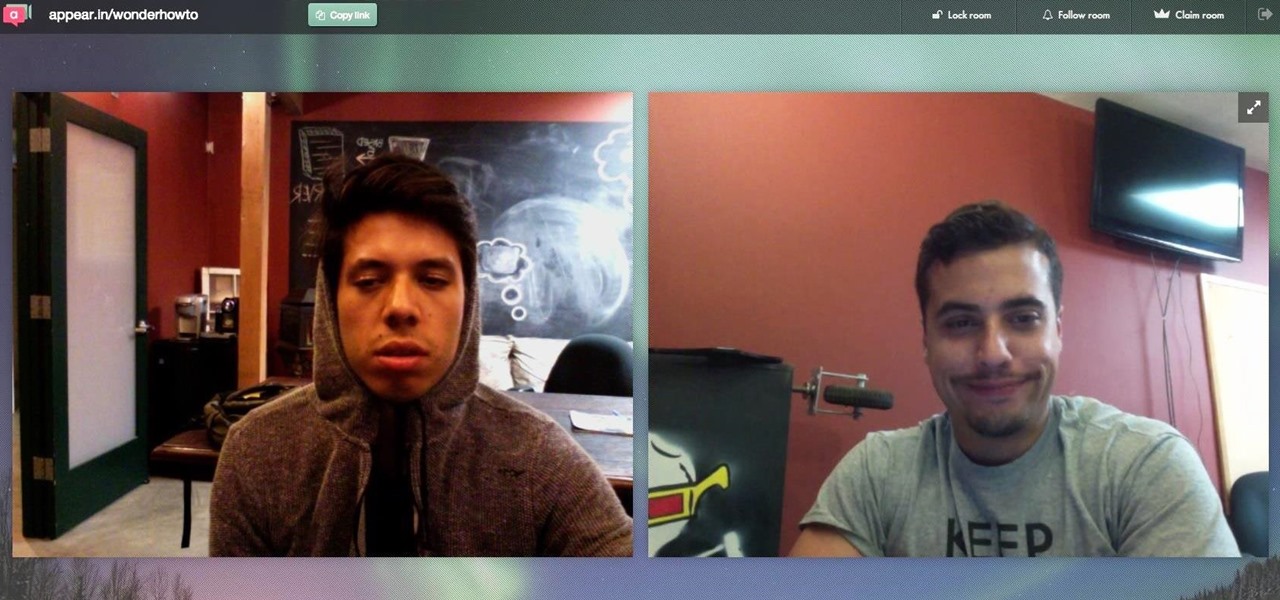
These days, phone calls aren't always the best way to communicate with others. Maybe you need to reach people out of the country, or you simply want to have a more visual conversation. Either way, there's a reason why video calling has become so popular.

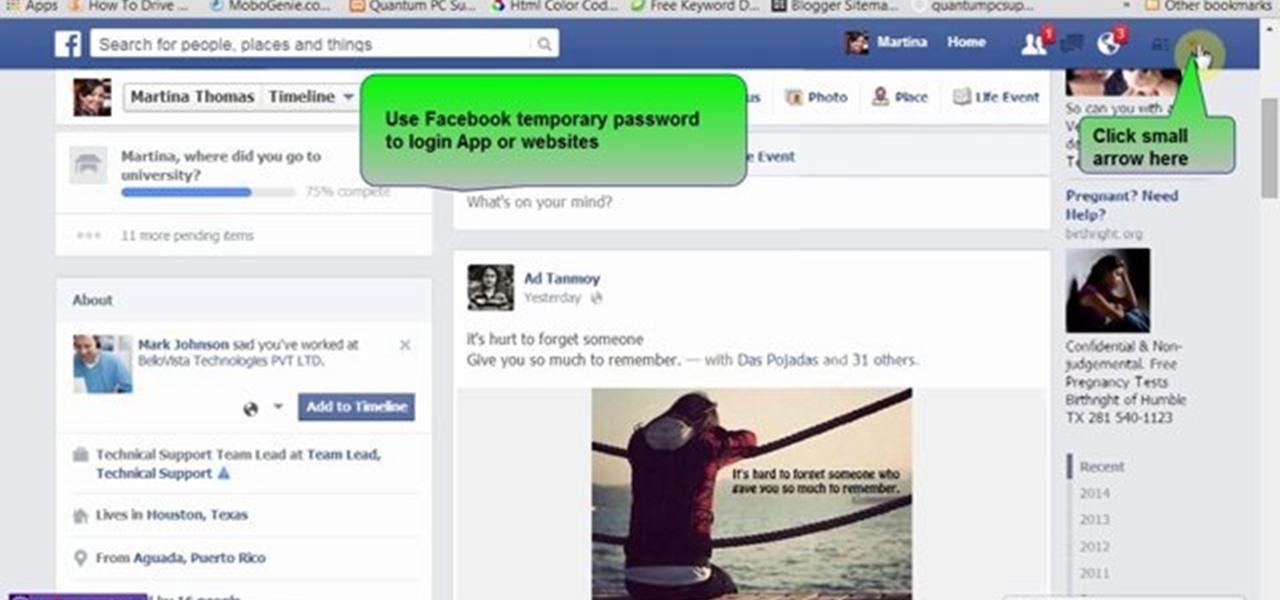
Many people use Facebook login detail to enter different apps or websites. This is somehow dangerous because unethical websites or apps may use your Facebook detail. So to avoid this warning Facebook is generating a temporary password for you. Now you could use this detail to login app or websites. You don't have to use your Facebook original login detail.

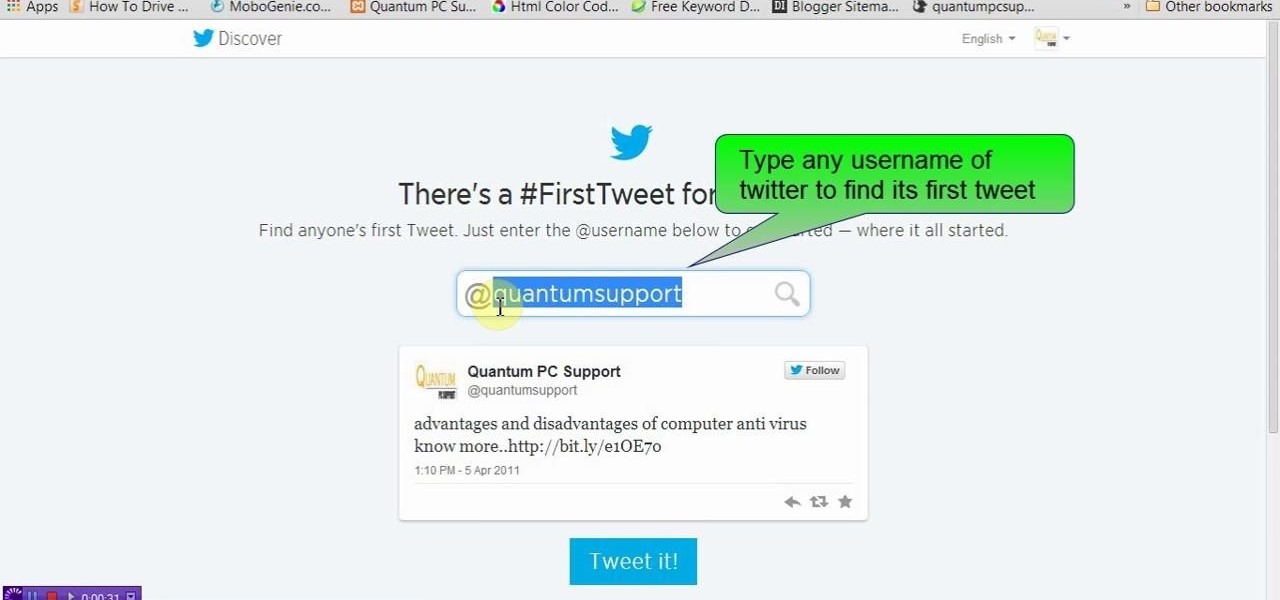
This video will show you how to see first twit of any user in twitter. You could type https://www.first-tweets.com in address bar and the site will be redirected to another place https://www.discover.twitter.com/first -tweet page. You have to enter the user name and twitter will fetch the first twit of that user. Watch the video and employ it yourself.

You probably use your smartphone to mostly surf the web, play games, and communicate with others, but there's so much more it can do. Thanks to integrated features and third-party apps, you can seamlessly control things around your home, including your TV, tablet, Bluetooth speakers, and even lighting fixtures.

If you've had the pleasure of owning both an iOS and Android device, you may have noticed one subtle difference on each one's PIN unlock screen. Android's lock screen requires you to press "OK" after entering the PIN, whereas iOS's simply unlocks the screen right after the last digit.

If you just got a new Android mobile phone, then chances are, the first thing you're going to want to set up is your email account, so you have instant access to your emails all the time, everywhere and anywhere. Setting up your specific email account or accounts is actually not hard. Best Buy has answers. The Best Buy Mobile team explains how simple it is to set up an email account on an Android cell phone.

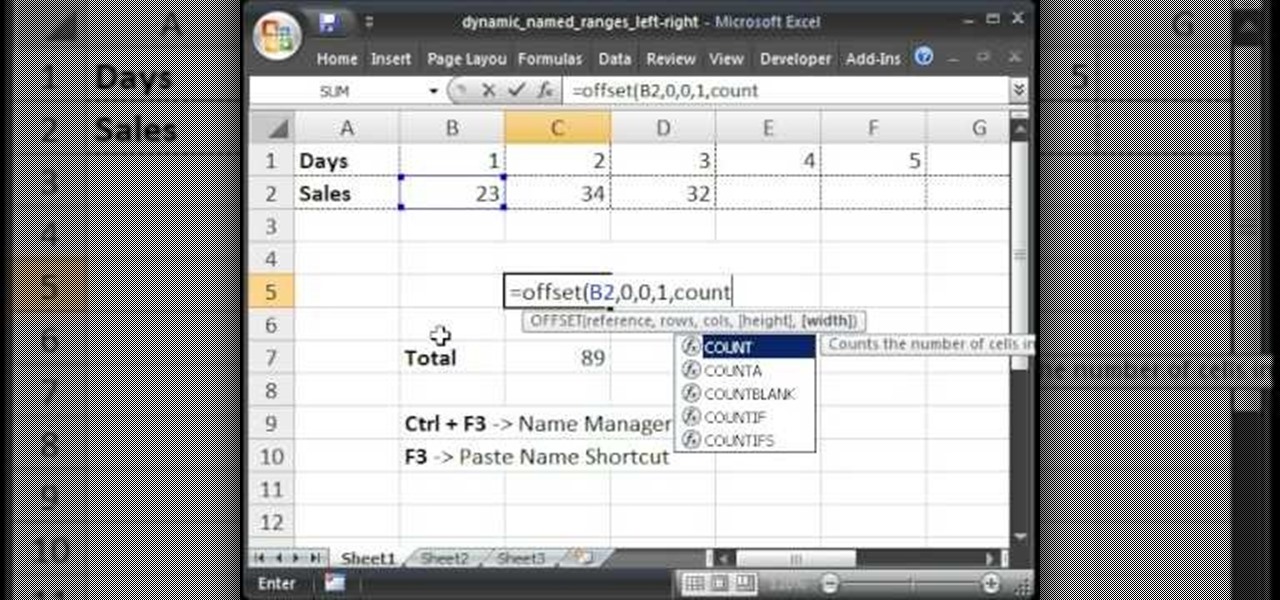
Teach Excel describes how to create a dynamically updating named range that goes from left to right using Excel. First, you define the named range by highlighting the cells containing numbers in a certain row. In the name box to the left of the formula bar, type the name of the data. In this example, the numbers correspond to sales, so type "sales." To check if the named range works, click on an empty cell and enter =sum(sales). That should return the sum of the highlighted cells. However, as...

Advance Photoshop shows viewers how to make the Photoshop CS3 icon in Photoshop. First in Photoshop go to File and then click New. Make a new blank at 500 x 500 pixels. Go to your layer button and create a new layer. Next, go to your rectangular marquee tool, hold down shift, and make the rectangle slightly smaller than the canvas itself. Set it from foreground to background and change the background color to a dark blue, enter 15396F for the color. Click on foreground color and enter 3070CA ...

This video explains how to add a bulleted or numbered list in Microsoft Word 2007. The shortcut to create a bullet-list is simple holding Shift and pressing the "A" key. After you hit the space bar or type a character the bullet will appear, and when you hit the Enter key it will continue the bulleted list. For numbering you just need to type the number you want and a dot after it and it should begin a numbered list. The list will continue if you press enter just like a bullet-list will. If y...

Want to forget about always pulling out your credit card to purchase something on your BlackBerry? There's a little application that can do it all for you? But how? Best Buy has answers. The Best Buy Mobile team explains how to use the BlackBerry Wallet application. This application can store personal information such as credit card information and shipping addresses on a secure website for easy access when shopping online.

This is a great playthrough of The Saboteur for the Xbox 360. In the fourth mission in Act 2: Jailbreak, you will need to do the obvious… jailbreak. Once you acquire the papers to enter Area 2, you'll be able to start this mission by visiting the resistance in the Western District. They will charge you with freeing a man named Bryman from a Nazi prison. Grab a car and follow the GPS to the destination. Here you'll find a heavily occupied Nazi area. Bryman's cell is within the courtyard surrou...

Check out this L4D2 walkthrough for some tips on Campaign 5: The Parish - Park. Stock up on items and exit via the door right next to the one you entered. Clear out any zombies and work your way up the large staircase into the park. Be prepared to deal with a likely Crescendo event in the plaza here. Pick a one of the staircases to climb up and enter the park. The restrooms near the entrance of the park usually contain a throwable item or two. For more info, watch the whole gameplay.

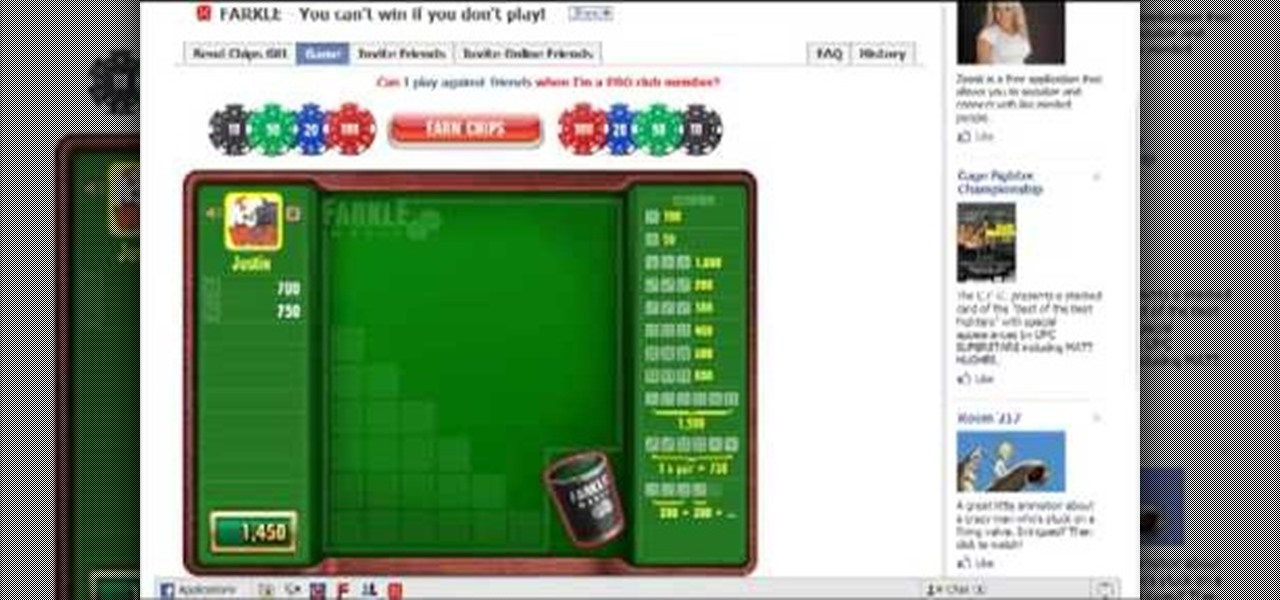
Farkle hacks, cheats, glitches. How to hack Farkle. Watch this video tutorial to learn how to hack Farkle with Cheat Engine (09/12/09).

Have you ever gotten the error message, "BOOTMGR is missing" on your PC? Well, if you have check out this video. In this tutorial, learn how to remedy and fix this problem in no time.