
How To: End a letter
Not sure how to close an important letter? Convey a powerful meaning to readers by choosing the right sign-off. In this video, proper etiquette to close a letter is gone over.


Not sure how to close an important letter? Convey a powerful meaning to readers by choosing the right sign-off. In this video, proper etiquette to close a letter is gone over.

Our national month-long celebration of all things creepy and crawly comes to a climax on Wednesday with Halloween and will end with Día de Muertos on Friday, so now is the ideal time for the The New York Times to publish a mildly chilling augmented reality story for children.

Once a hacker has created a PowerShell payload to evade antivirus software and set up msfconsole on their attack system, they can then move onto disguising their executable to make it appear as a regular text file. This is how they will get a Windows 10 users to actually open the payload without knowing they are doing so.
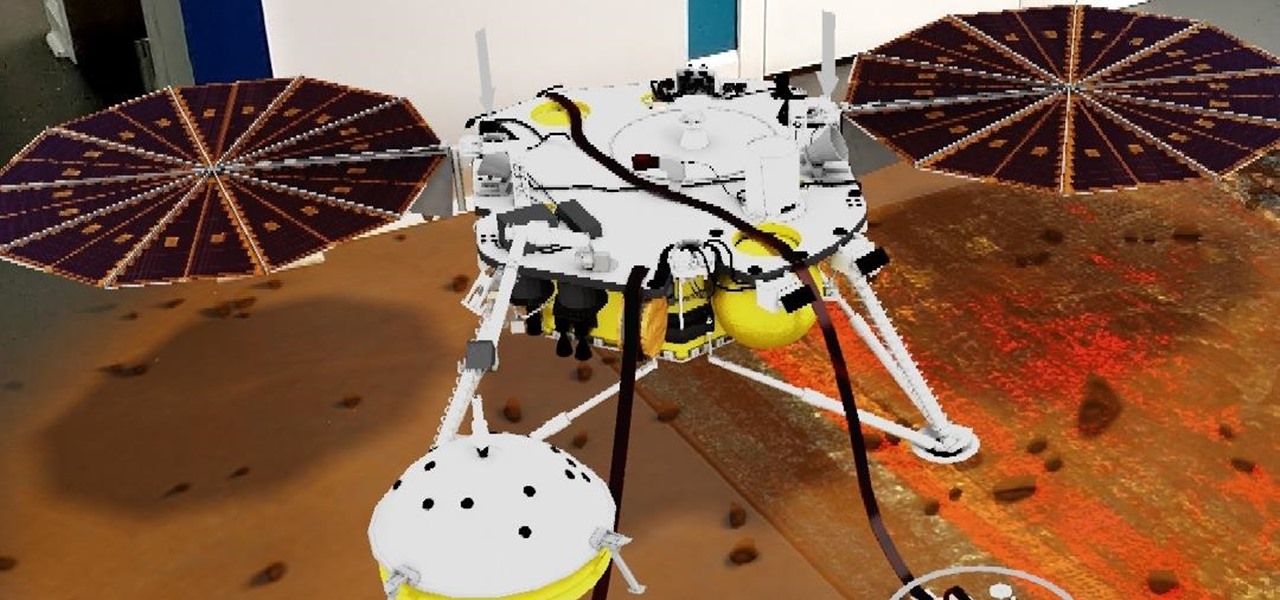
In the latest installment in its burgeoning augmented reality journalism practice, The New York Times is bringing its readers closer to Mars and NASA's latest spacecraft set to travel to the red planet.

Okay, so you've decided to take the plunge, and participate in our Love. Earn program with a how-to article. But, for whatever reason, your article keeps getting rejected by WonderHowTo, and you're wondering, well, where's the love?

In its latest feature with an assist from augmented reality in storytelling, the New York Times shows readers the virtual crime scene it constructed to prove that the Syrian military conducted chemical warfare against its citizens.

While a new museum to house the original torch of the Statue of Liberty is under construction on Liberty Island and scheduled to open in May 2019, New York Times readers can now view the sculpture in their own space through augmented reality.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

Although it's impossible (at least for now) to travel back in time to see the Big Bang, The New York Times has provided its readers the closest simulation of the experience via its latest augmented reality feature.

It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

If you've blocked out your calendar to watch the NHL All-Star Game this weekend, then you might be excited to know that USA Today has given its readers the opportunity to meet Washington Capital's John Carlson in augmented reality.

Before The New York Times brought augmented reality to its iPhone app, the only way Winter Olympics fans could get this close a view to the world's best athletes would be to acquire a press pass.

We've all been there: facing a lengthy, complex word that ignores the phonics we were taught in elementary school, unsure of not only its pronunciation, but also its meaning. These words, from autochthonous to esquamulose, are both terrifying and impressive. After all, if someone knows how to use them—and even say them—they must be quite smart. Yet before you begin stuffing every email and presentation with verbose prose, you might want to reconsider what others perceive to be intelligent.

The augmented reality team at USA Today closed out a prolific year of immersive storytelling with a hard-hitting companion piece exploring the controversial conflict in Afghanistan.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

Usually paper beats rock. With augmented reality, The Rock beats paper. Using the Life VR app for iOS or Android, Entertainment Weekly readers can point their smartphones at the cover of the Dec. 8 edition to view a holiday greeting from Dwayne "The Rock" Johnson, star of the forthcoming reboot, Jumanji: Welcome to the Jungle.

The Augmented World Expo or AWE — if you are a big fan of AR/MR technology, that is a very fitting acronym — is the world's largest conferences dedicated to all things augmented, mixed and virtual reality. AWE is in its 8th year, and with the massive growth we have seen in the space over the last year, promises to be its biggest year yet.
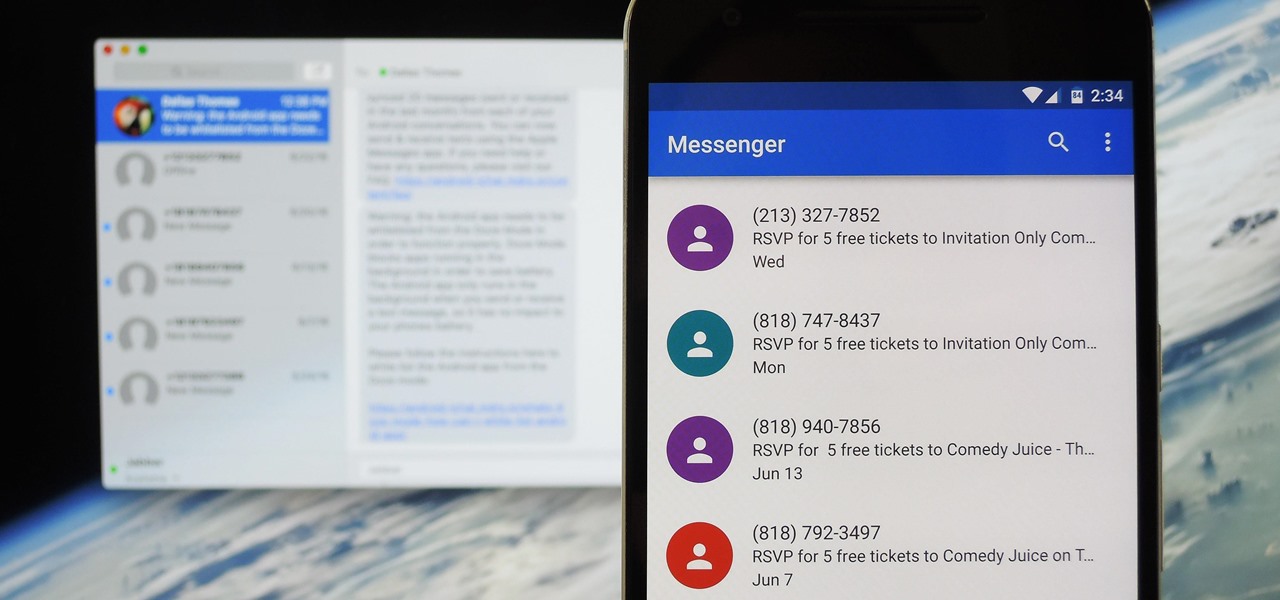
Prior to this year's WWDC, there were lots of rumors that Apple might finally be making a version of iMessage for Android. While that never came to fruition, a few big updates to a very useful app have now ensured that we can seamlessly send and receive Android texts in Apple Messages on our Macs.

The newest version of macOS has arrived. While everyone's mind is being blown by Mojave's groundbreaking new Dark Mode, we'll be taking advantage of its insecure file permissions to establish a persistent backdoor with a self-destructing payload that leaves little evidence for forensics.

No matter what kind of business you have, small or big, online-based or not, when you're dealing with email marketing, the number one things your targets will see is the subject line, and if your subject line looks spammy or uninteresting, it's not going to help you one bit.

In order to use ThermaPure heat system to eradicate bedbugs, you will need a professional, with the appropriate equipment, including surface temperature readers.

Having a well written executive summary is an essential tool for you to have when you are presenting a report. The executive summary serves as an introduction to let readers know what your report is going to discuss in detail.
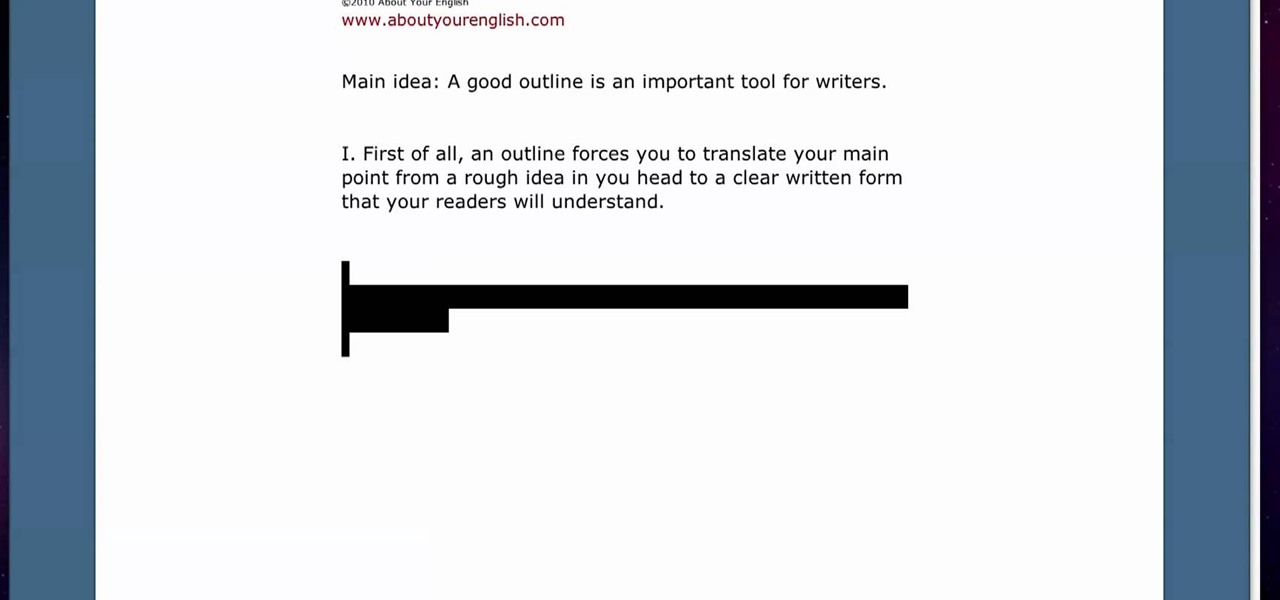
This technique can be used to write answers for a question asked in the exam or can be used to write a paragraph while applying for a scholarship or while writing a brief letter. The main thing to be considered while writing the paragraph is having an outline, all we need to do is prepare an outline before starting the paragraph. First write the "main idea" that is to be delivered, then the main idea should be supported with additional details, there can be two to three additional points to s...

After winning the 2015 FIFA Women's World Cup, the USA Women's National Soccer Team is ready to defend its title in the 2019 tournament.

While The New York Times' augmented reality section has largely been dormant in 2019 (so far), USA Today has continued to crank out AR news stories.

In most macOS hacks, a non-root terminal is used to create a backdoor into the device. A lot of damage can be done as a low-privileged user, but it has its limitations. Think twice before granting a file permission to execute — an attacker might be able to convert your harmless scripts into persistent root backdoors.

Most users don't realize how much valuable data is in their network traffic. With a few simple tools, an attacker can quickly pick out cookies, passwords, and DNS queries from a macOS device as it covertly streams the victim's network traffic to the attacker's system. Here, we will cover two methods for analyzing packets flowing from a Mac.

Passwords and data stored in web browsers are extremely valuable to hackers. If not for financial gain, black hat hackers may still leak your passwords and personal information for amusement. Never undervalue what you're worth to a hacker.

In the previous article, we learned how to set up our VPS, configure our PHP server, and developed an in-depth understanding of how the payload works. With all that taken care of, we can get into disguising our payload to appear as an image and crafting the note in the greeting card being delivered to our intended target.

After devoting a number of resources toward developing VR content to modernize the delivery of its news content in recent years, The New York Times is expanding its capabilities to include augmented reality as well, a mission outlined in a manifesto published on Thursday.
Starting your morning right is an essential first step to a productive day. Whether you're running late, rushing to catch up on the day's news, or lagging behind with early emails, little hiccups like these can have a trickle-down effect and ultimately ruin your day. Like with many problems, though, your smartphone can help.

The first teaser for Jurassic World: Fallen Kingdom just hit computer screens on Sunday, but now plans for an augmented reality book for the film have also emerged.

If you need a little inspiration for tonight's Halloween festivities, this augmented reality magazine cover featuring the Dark Knight himself, Batman, may do the trick.

The Washington Post believes augmented reality adds an extra layer to stories, and they're doubling down on that belief by adding in new AR features into their already popular "rainbow" news (iOS and Android) and Classic (iOS and Android) news apps.

Aaron Betsky, director of the Cincinnati Art Museum and previous director of the Netherlands Institute of Architecture, reports on the world's first postage stamp to employ augmented reality. Dutch advertising agency Gummo, the NIA and the Dutch postal service teamed up to present five unbuilt models by different Dutch architecture studios in 3D form. When held in front of a webcam, the illusion of a 3D building is projected in your hand. By slowly moving the stamp, you can experience the vir...

Whether you are sharing an internet connection, working together or just playing group video games, you will need to network your computers. Check out this tutorial and learn just how easy it is to create a home network.

1. To start a blog pick a topic on which you want to create your blog. 2. Select a blog software or platform where you can work like word press.

While I am a writer with a degree in Creative Writing, I haven't published any Steampunk fiction. However, as a panelist and track director, I've been on panels with many well-known Steampunk writers and have gleaned insight from the things they've said. I've compiled some of those things into this post, which will hopefully be helpful to all of the writers out there!

Lenovo, the company that now owns Motorola, just announced two new entries in their wildly successful midrange Moto G series. The Moto G5, and its bigger brother, the Moto G5 Plus, were both shown off in detail at Mobile World Congress 2017 in Barcelona, Spain.