When you were younger, you probably had your parents bugging you not to have your cassette player headphones up too loud. For all you younger readers out there, it was probably a CD player. The even younger readers likely had an iPod or other MP3 player. Either way, your parents didn't want you to mess up your hearing, blasting that Limp Bizkit in your ears (wow, I'm showing my age here).

Hackers can be notoriously difficult to buy gifts for, so we've curated a list of the top 20 most popular items Null Byte readers are buying during their ethical-hacking studies. Whether you're buying a gift for a friend or have been dying to share this list with someone shopping for you, we've got you covered with our 2017 selection of hacker holiday gifts — just in time for Christmas.

Apple Pay has been available to use in stores, as well as in select apps and websites, ever since its first appearance in iOS 8.1. Now, with iOS 12, there are currently 13 different iPhone models that support Apple Pay functionality without the use of an Apple Watch, and the list of partnered stores that accept Apple Pay has only grown. Here's our always-up-to-date list to keep you in the know.

No matter what age you are or what kind of life you've lived you can put your story out there by writing an autobiography. Every life can be interesting if written about in a well formulated, and honest manner.

Kali Linux is probably the most well-known hacking distribution among penetration testers. However, there are alternative distros which offer versatility and advanced package management systems that are absolutely worth considering.

The augmented reality industry has a bright future built on innovation and growth, but that doesn't mean we can't look back at the close of the year to see what the industry has accomplished from a business perspective.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

Transferring hundreds of screenshots, webcam recordings, keystroke logs, and audio recordings between your VPS and a local Kali machine can be tricky. Services like Dropbox don't always have the best privacy policies and suffer data breaches just like any other website. To mitigate these risks, we'll use a secure, open source, and decentralized alternative.

Backdooring a powered-off MacBook is easy when a few minutes of physical access is allowed. That attack works well if the hacker also shares a Wi-Fi network with the victim, but this time, I'll show how to remotely establish a connection to the backdoored MacBook as it moves between different Wi-Fi networks.

The default Camera app got a few more tricks up its sleeves when iOS 11 was released, and the best addition by far was the inclusion of a built-in QR code reader since that meant no more third-party apps just for QR code scanning. However, Apple's built-in QR code scanner did have a vulnerability at one point that would let hackers direct you to a compromised website without you even noticing it.

The year is 2018. You just received your own Magic Leap One: Creator Edition. What now? Rewinding back to today, we know of one specific app that will be available for Magic Leap's device, along with two others that could be tagged as highly likely. Paired with Magic Leap's own experiments and demonstrations, we can get a sense of what the playground for this new toy will offer.

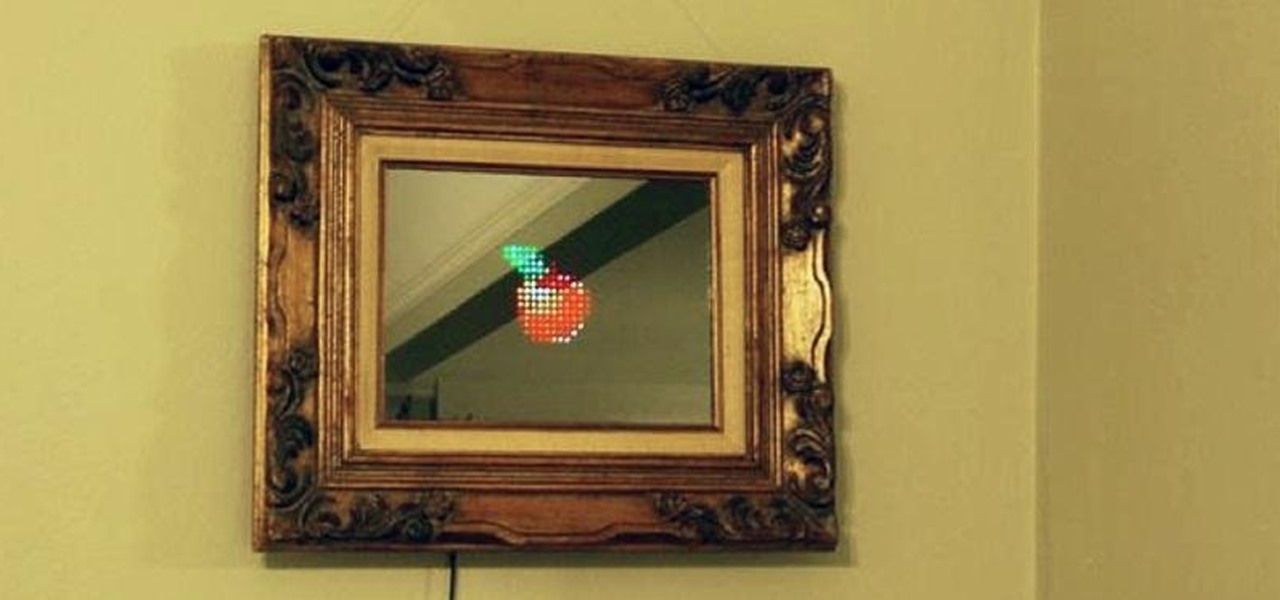
Fool your friends, scare your cat, play a game while also admiring your physique! This "magic" mirror lets you do all that and more by letting you display words, pictures, videos, and even some games—all controllable through a mobile phone.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

Edit: Some of the methods I show you may be difficult, or not work at famous or high quality hotels.

Welcome back, my future hackers! After my first tutorial about doxing, I decided I would dive a little bit deeper into the world of social engineering. In this tutorial we will learn some basic social engineering techniques to get into a company building, find out more information about the company's security, and maybe even exploit the company's computers if you get the chance.

It's a common misconception that iPhones are impervious to cyberattacks and "more secure" than Android. And when an iPhone does get hacked, it's nearly impossible to tell that it happened.

It's no secret that the vast majority of Null Byte readers range from beginner to seasoned coding pros and developers. Regardless of whether you're interested primarily in building websites or creating best-selling apps and games, working with a wide variety of programming languages remains one of the best ways to make serious money in an increasingly app-driven world.

We know our Null Byte readers would like to see some iPhone-hacking scenarios on the site soon, but until we get some of those up, we understand that some of you actually use an iPhone as your primary phone. If that's you, and you would like an easier way to get information from point A (your iPhone) to point B (your computer) and vice versa, there's an all-in-one tool that can help.

Null Byte readers are no strangers to the powers and benefits that come from learning how to code. By knowing only a handful of programming languages and platforms, an intrepid developer can create everything from best-selling apps to spyware in the comfort of his or her own home.

The Files app received a big update in iOS 13. Before, it was limited to local and cloud-based files, but now you can access data from external storage devices, including SD cards and USB drives. But before you try to connect your favorite card or drive to your iPhone, there are a few things you need to know.

A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.

The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already built into macOS.

Hashes containing login passwords are transmitted between Windows computers on local Wi-Fi networks. By intercepting and decrypting these hashes using Responder and John the Ripper, respectively, we can learn a target's login credentials which can be later used to gain physical access to their computer.

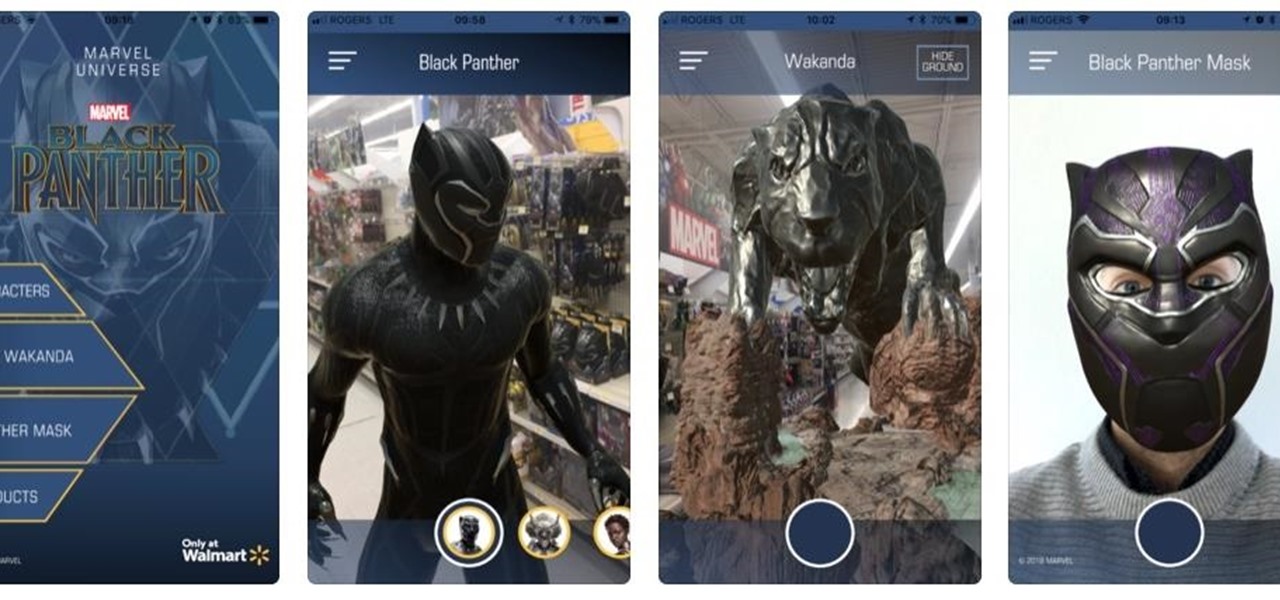
Marvel and Walmart are looking to capitalize on the uber-successful Black Panther film with a mobile augmented reality app designed to push the franchise's merchandise.

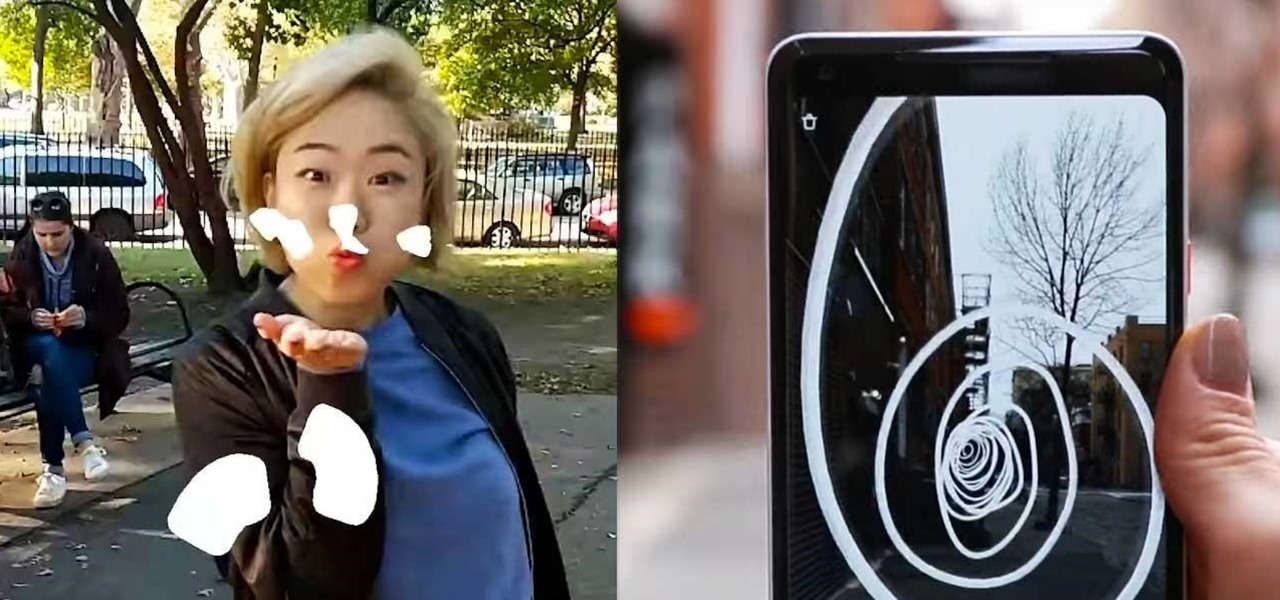
As part of its ARCore push this week, Google has promoted Just a Line from one-time AR experiment to a full-fledged app.

In a huge surprise, Verizon is the first US carrier to push out the Samsung Galaxy S8/S8+ Android Oreo update. The update has been available in international markets for some time now, but this is the first report of a rollout in the United States. We've already ran down all the new features available in Android Oreo, so check out our full coverage if you're interested in those.

While The Walking Dead has brand recognition for its AR game, ARZombi has ARKit.

On Oct. 19-20, the MOC Exhibition Center in Munich, Germany will play host to the Augmented World Expo (AWE) Europe 2017.

While not specifically an augmented reality conference, IFA 2017 packed a plethora of presentations with AR themes, including devices with AR features from Sony and Motorola, a smartphone-based AR headset from Lenovo, and a new processor from Huawei that will facilitate AR experiences.

Following the most recent election, some argue that increasing political polarization is dividing Americans. A new app, called Read Across the Aisle, is aiming to combat this by encouraging users to read news from media outlets on both sides of the political spectrum.

Hello there learners and readers! I figured I'd show you guys my problem and how I solved it, hoping that it would help people who are facing the same issue. Today, we'll be talking about the solution of

A new leak from GSM Israel on March 6th shows some telling screenshots of the U.S. variant of the upcoming Samsung Galaxy S4, some of which confirm features seen in the leaked 4.2.1 ROM for the Galaxy S3.

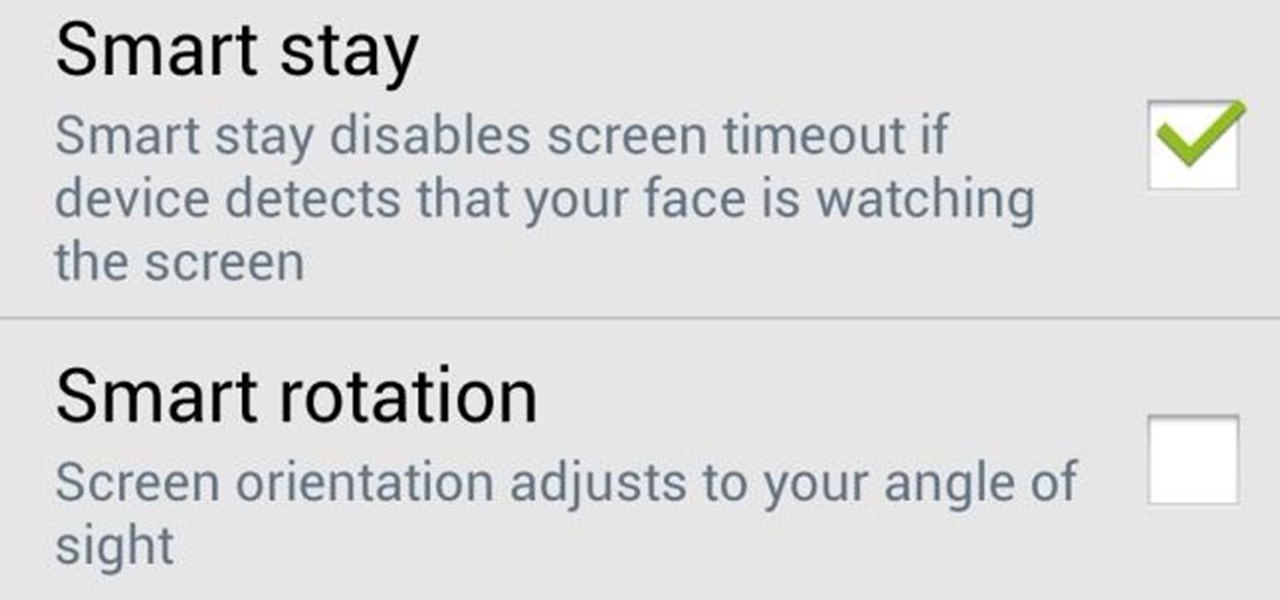
One of the coolest things for readers using the Samsung Galaxy Note 2 is the stock Smart Rotation feature. While most smartphones use the accelerometer to adjust the screen orientation, Smart Rotation actually uses the camera to detect your face-to-screen angle and adjusts accordingly. Now, if only there was a way that all Android users can continue reading an article or text without sporadic and unexpected 90-degree turns of their screen. Wait, there is!

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

The latest Star Wars movie, Solo: A Star Wars Story, has grossed almost $350 million worldwide during its first month in theaters. This is a good opportunity to discuss how hackers can use media hype (in this case, Hollywood movie hype) to disarm an unsuspecting Windows user into inserting an evil USB stick into their computer.

The holidays are stressful. Between traveling, family, and dinner, Thanksgiving weekend can feel like weeks. Many families have traditions that make the days long, but some of us would rather curl up somewhere and watch our favorite shows. But all is not lost — our phones do so much for us now that they can help make the long stressful weekend much more bearable.

Knowing just one or two programming languages is no longer sufficient if you want to make serious money in the lucrative world of web design and development. But the good news is that you don't need to spend an excessive amount of time or money on a traditional coding education to get the skills you need to thrive.

While the airline, casino, cruise, and hotel industries are asking for government bailouts during the COVID-19 pandemic, companies around the US are giving away its apps and services for a limited time. So while you're stuck at home, keep your mind off of coronavirus with free movies, TV, music apps, concerts, internet, fitness sessions, classes, and more.

The sky is the limit when it comes to augmented reality, but Snapchat's latest innovation is keeping its AR platform grounded.

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.